1,基本概念
- 为了方便管理和集成jenkins,k8s、harbor、jenkins均使用openLDAP统一认证。
2,部署openLDAP
- 根据之前的文档,openLDAP使用GFS进行数据持久化。
- 下载对应的openLDAP文件
git clone https://github.com/xiaoqshuo/k8s-cluster.git
2.1 创建openLDAP
[root@k8s-master01 k8s-cluster]# kubectl apply -f openldap/
deployment.extensions/ldap created
persistentvolumeclaim/openldap-data created
secret/ldap-secret created
service/ldap-service created
deployment.extensions/phpldapadmin created
service/phpldapadmin created
- 此处参考的是:https://github.com/osixia/docker-openldap,更新DN可以更改environment下的yaml文件,默认的example.org
2.2 创建ldap-ui-ingress
[root@k8s-master01 openldap]# kubectl create -f traefik-ldap.yaml
ingress.extensions/ldap-ui created[root@k8s-master01 openldap]# cat traefik-ldap.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:name: ldap-uinamespace: public-serviceannotations:kubernetes.io/ingress.class: traefik
spec:rules:- host: ldap.k8s.nethttp:paths:- backend:serviceName: phpldapadminservicePort: 8080
3, 查看验证
[root@k8s-master01 openldap]# kubectl get po,svc,pvc -n public-service | grep ldap
pod/ldap-6c9fcc7446-r52r7 1/1 Running 0 4m19s
pod/phpldapadmin-6784bf8db-gxqw2 1/1 Running 0 4m16sservice/glusterfs-dynamic-openldap-data ClusterIP 10.96.177.154 <none> 1/TCP 3m29s
service/ldap-service ClusterIP 10.111.36.109 <none> 389/TCP,636/TCP 4m16s
service/phpldapadmin ClusterIP 10.103.142.162 <none> 8080/TCP 4m11spersistentvolumeclaim/openldap-data Bound pvc-252ac771-01da-11e9-b0c8-000c2927a0d0 1Gi RWX gluster-heketi 4m20s
3.1 访问web
- 访问phpldapadmin:ldap.k8s.net
- 登录
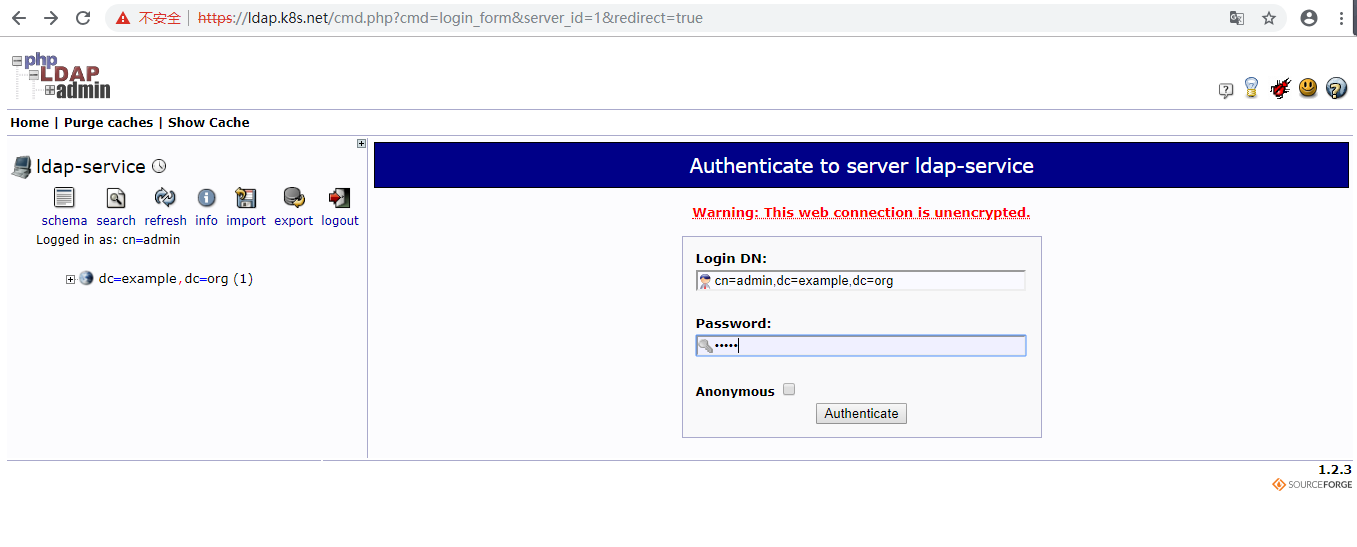
- 默认DN:cn=admin,dc=example,dc=org,默认Password:admin(线上系统需自定义修改)
4, 添加用户和组
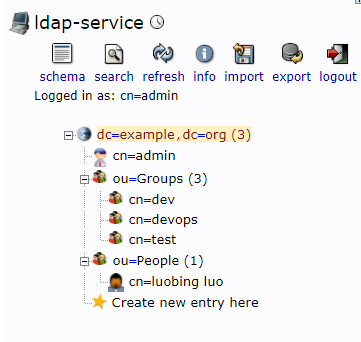
4.1 创建Groups和People OU
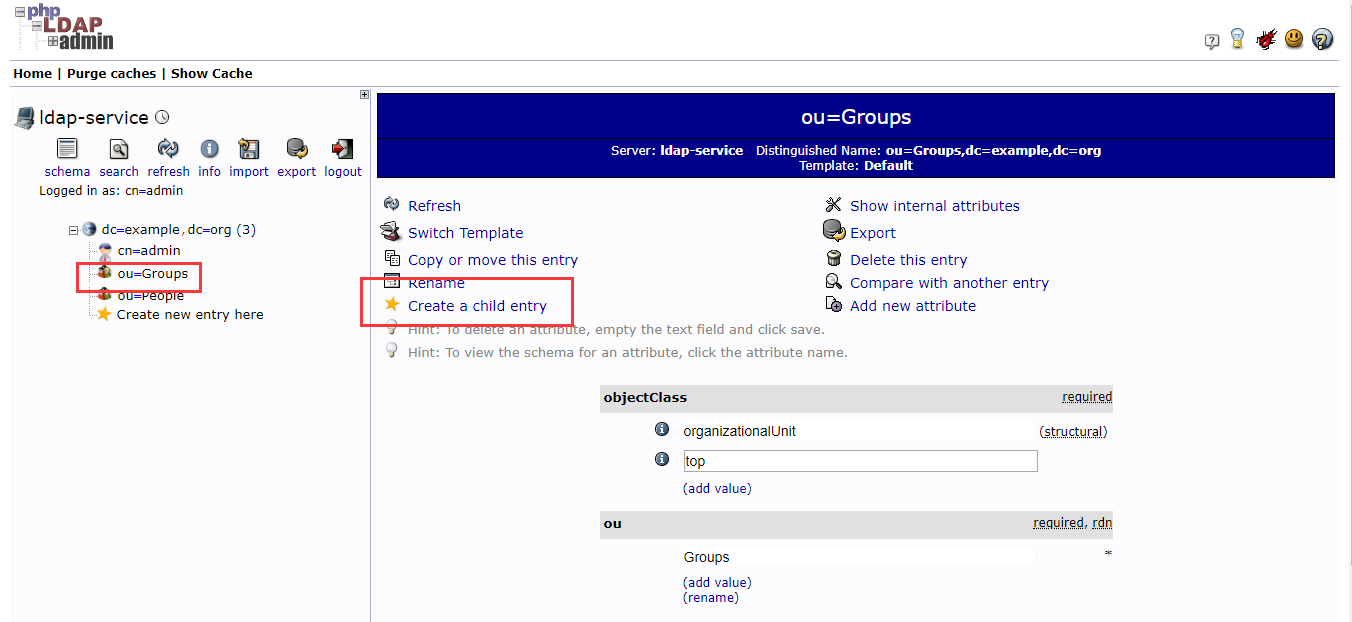
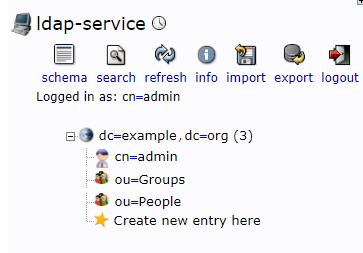
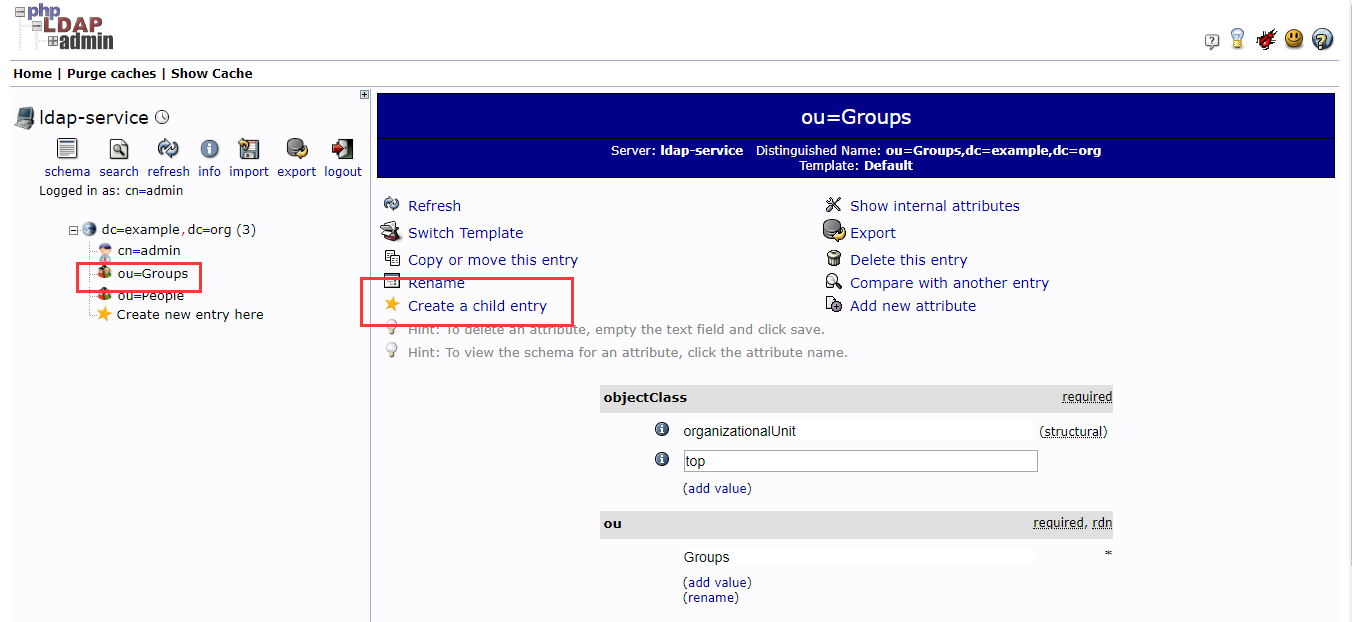
4.2 创建组和用户
4.2.1 组 dev devops test
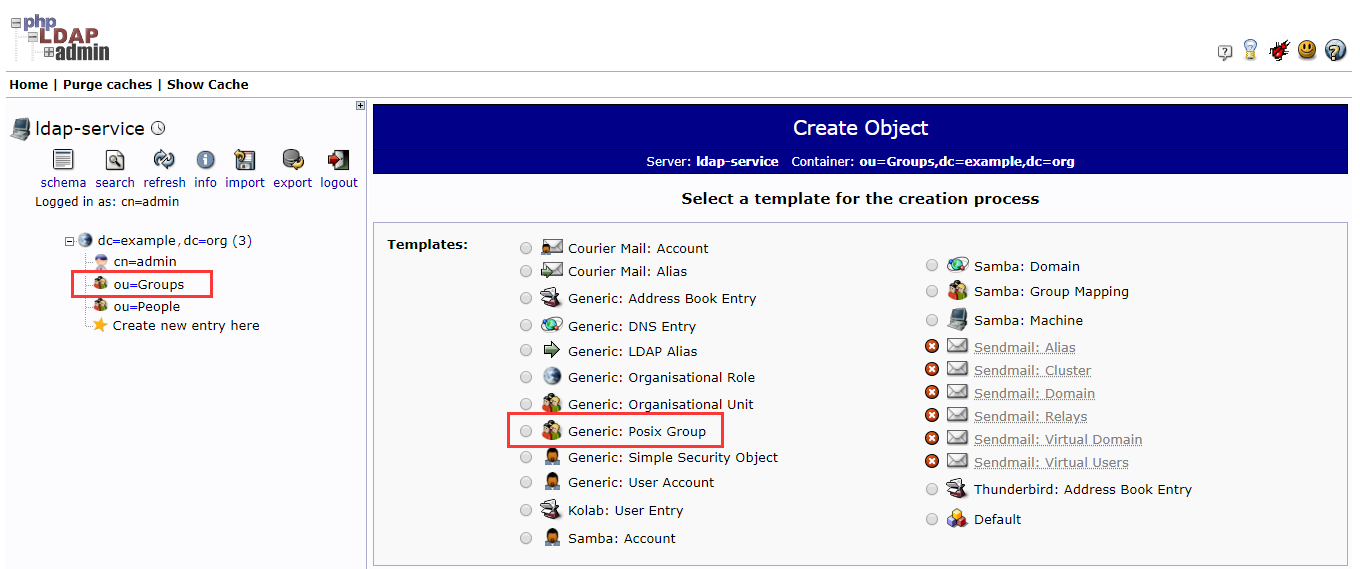
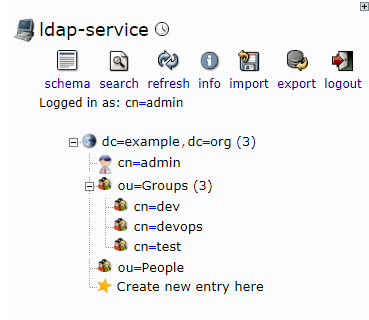
4.2.2 用户
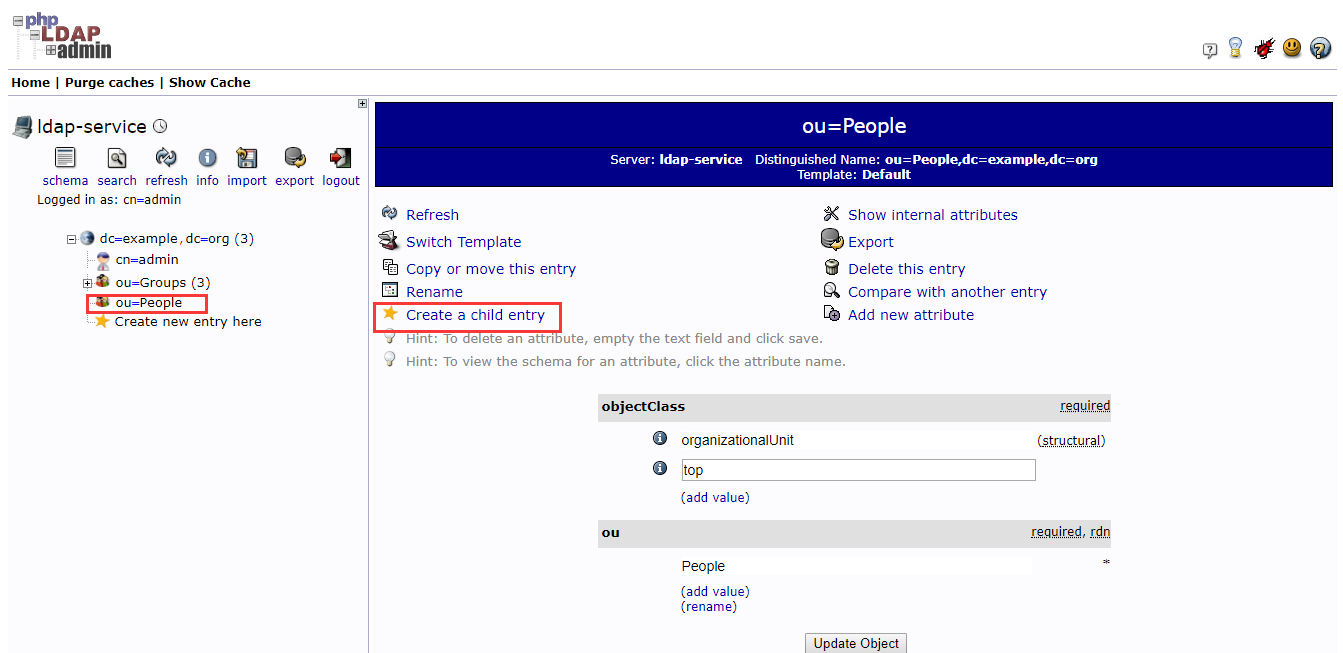
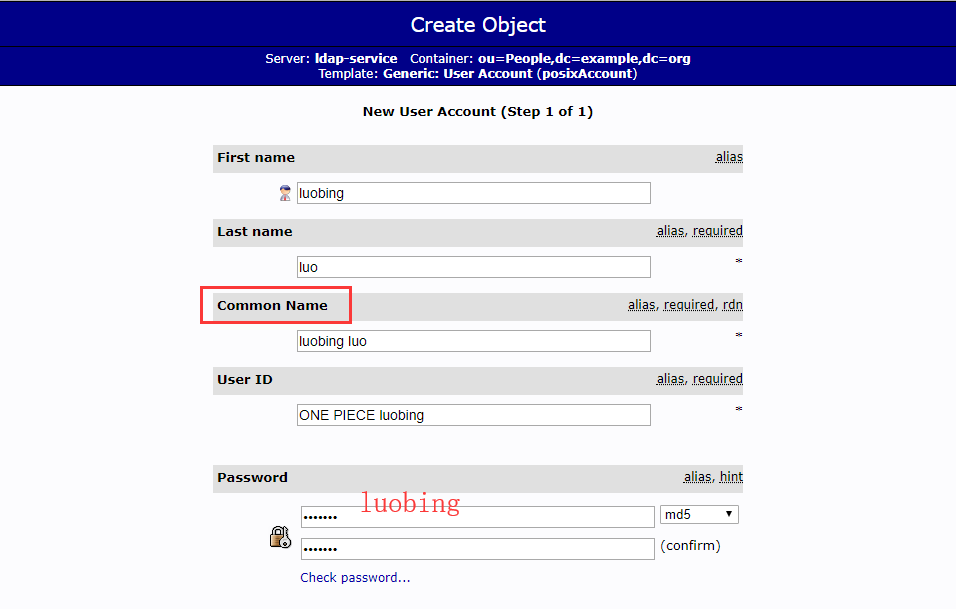
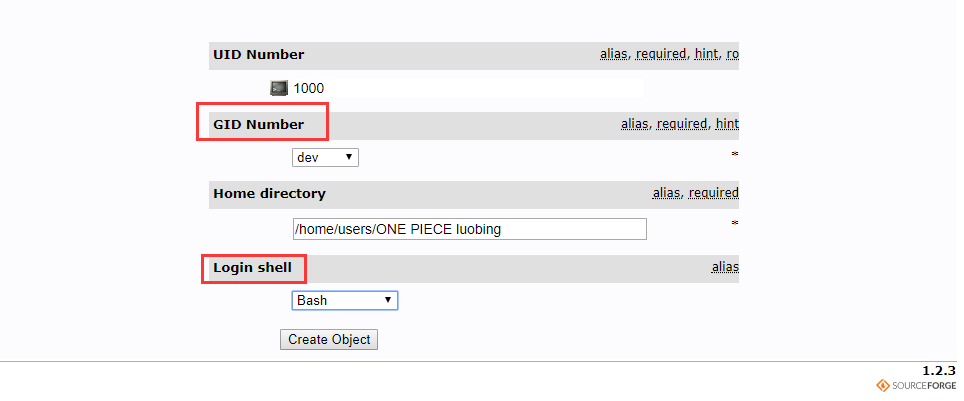
- 填写基本信息,选择组和Login Shell
- 注意修改Common Name
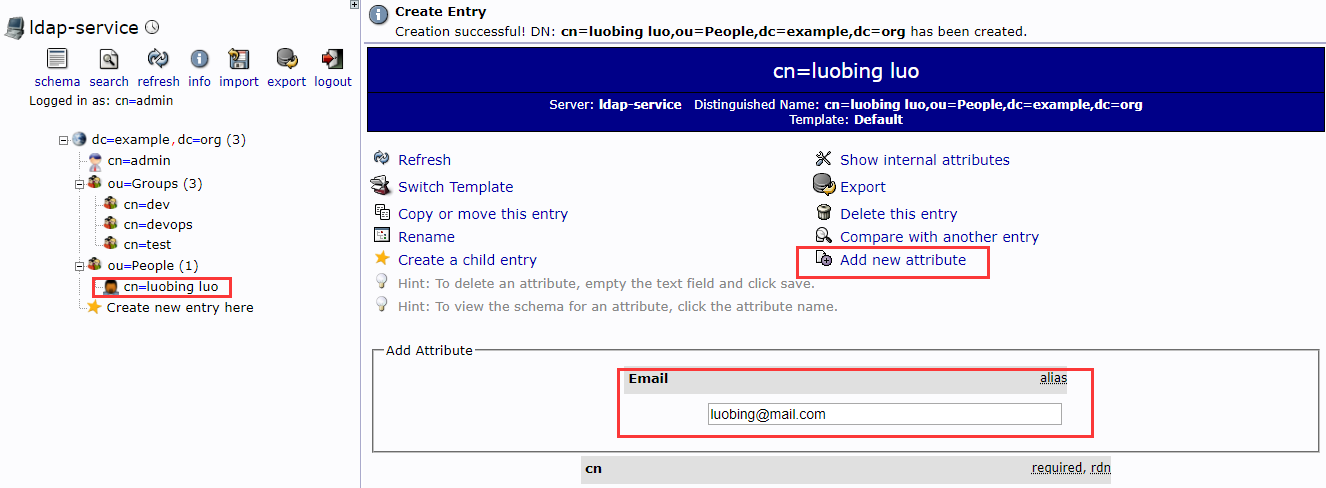
4.3 为每个用户添加Email,没有Email无法登陆gitlab
5,配置k8s使用ldap登录
未完待续
- 参考:
- https://www.cnblogs.com/dukuan/p/9983899.html
- https://github.com/osixia/
- https://icicimov.github.io/blog/virtualization/Kubernetes-LDAP-Authentication/
- https://github.com/nginxinc/nginx-ldap-auth.git















![[Egret][文档]遮罩](http://pic.xiahunao.cn/[Egret][文档]遮罩)








![【洛谷】P1641 [SCOI2010]生成字符串(思维+组合+逆元)](http://pic.xiahunao.cn/【洛谷】P1641 [SCOI2010]生成字符串(思维+组合+逆元))

暑期集训--二进制(BZOJ5294)【线段树】)


![[Python设计模式] 第17章 程序中的翻译官——适配器模式](http://pic.xiahunao.cn/[Python设计模式] 第17章 程序中的翻译官——适配器模式)


