1、环境
操作系统:龙蜥os 7.9
sshpiper:1.3.1
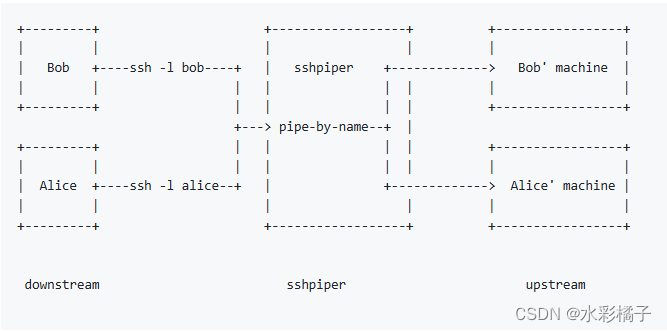
2、下载软件
https://github.com/tg123/sshpiper/releases
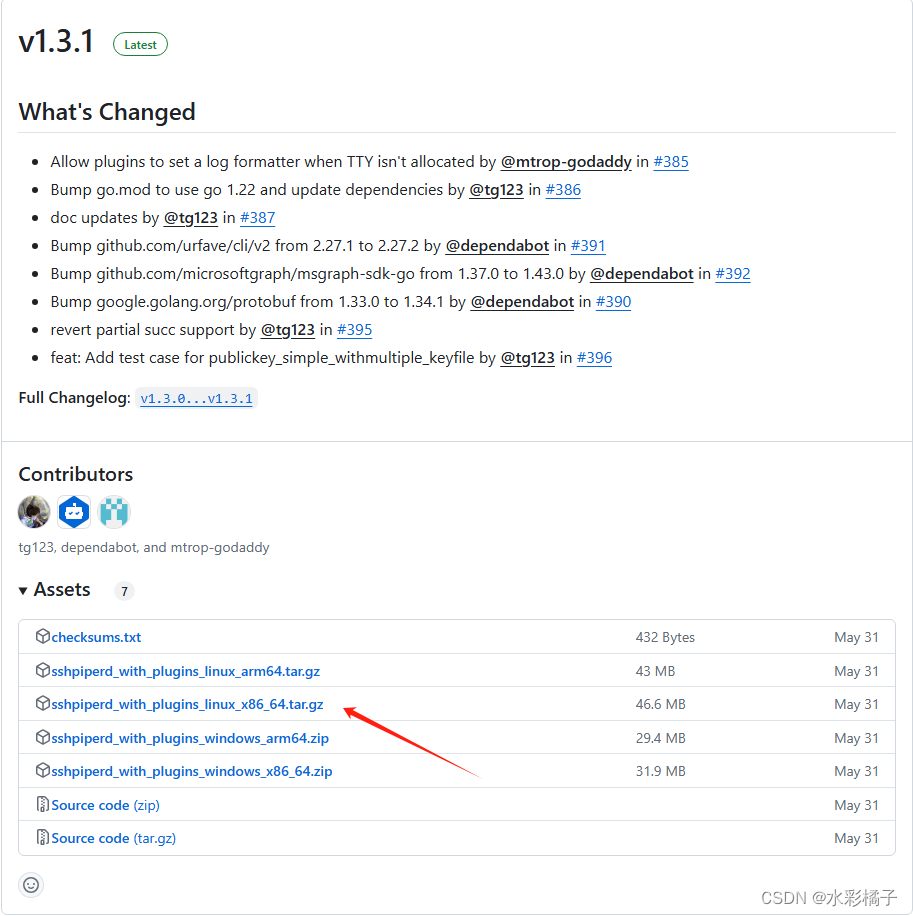
3、解压到指定目录
mkdir /opt/sshpiper
tar -xvf sshpiperd_with_plugins_linux_x86_64.tar.gz -C /opt/sshpipe
4、添加执行权限
chmod +x /opt/sshpiper/sshpiperd
chmod +x /opt/sshpiper/plugins/*
5、创建配置文件(使用yaml模块)
模块说明
https://github.com/tg123/sshpiper/tree/master/plugin/yaml
mkdir /opt/sshpiper/conf
vi /opt/sshpiper/conf/config.yaml
添加如下,需要符合yaml语法
version: "1.0"
pipes:
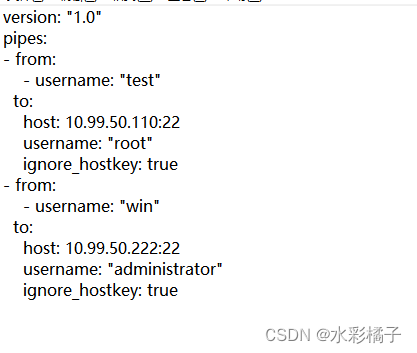
- from:- username: "test"to:host: 10.99.50.110:22username: "root"ignore_hostkey: true
说明:通过from 的username 来区分登录到不同的服务器,例子中使用test 用户连接sshpiper的时候会代理到10.99.50.110:22,并使用root用户登录
更改配置文件权限
chmod 600 /opt/sshpiper/conf/config.yaml
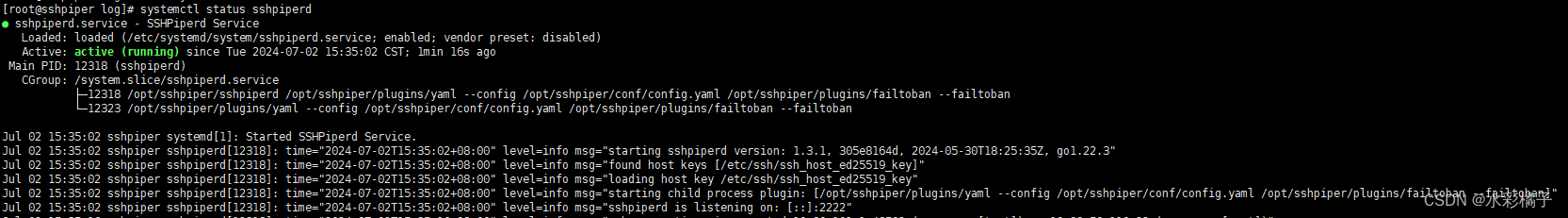
6、创建守护进程(这里加入了failtoban模块)
vi /etc/systemd/system/sshpiperd.service
添加如下:
[Unit]
Description=SSHPiperd Service
After=network.target[Service]
Type=simple
ExecStart=/opt/sshpiper/sshpiperd /opt/sshpiper/plugins/yaml --config /opt/sshpiper/conf/config.yaml /opt/sshpiper/plugins/failtoban --failtoban
Restart=on-failure
User=root
Group=root[Install]
WantedBy=multi-user.target设置权限
chmod 644 /etc/systemd/system/sshpiperd.service
重新加载 Systemd 守护进程:
systemctl daemon-reload
启动服务
systemctl start sshpiperd
systemctl enable sshpiperd
7、添加防火墙规则限制访问
firewall-cmd --permanent --zone=public --remove-service=ssh
firewall-cmd --permanent --zone=public --add-rich-rule='rule family=ipv4 source address=10.90.101.1 port port=22 protocol=tcp accept'
firewall-cmd --permanent --zone=public --add-rich-rule='rule family=ipv4 source address=10.90.101.0/24 port port=2222 protocol=tcp accept'
firewall-cmd --permanent --zone=public --add-rich-rule='rule family=ipv4 source address=10.99.17.65 port port=2222 protocol=tcp accept'
firewall-cmd --reload
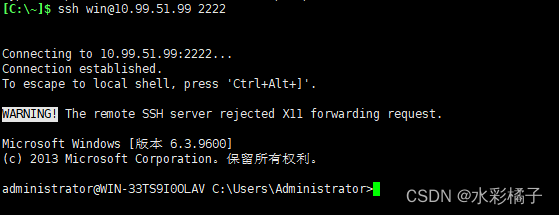
8、linux访问
用xshell 登录目标机器
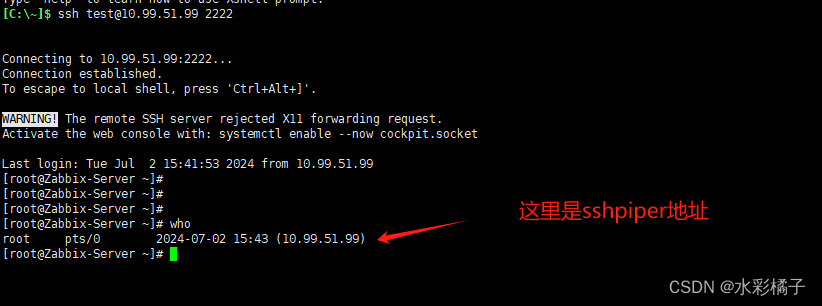
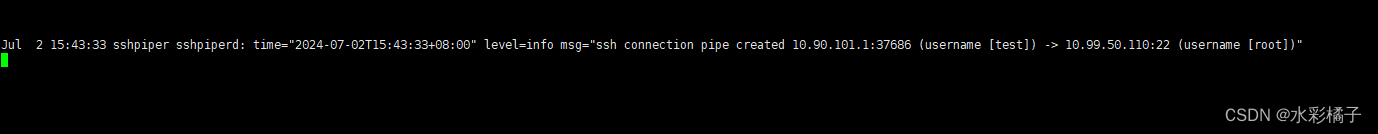
日志里有类似如下信息
9、windows 配置ssh
https://github.com/PowerShell/Win32-OpenSSH/releases
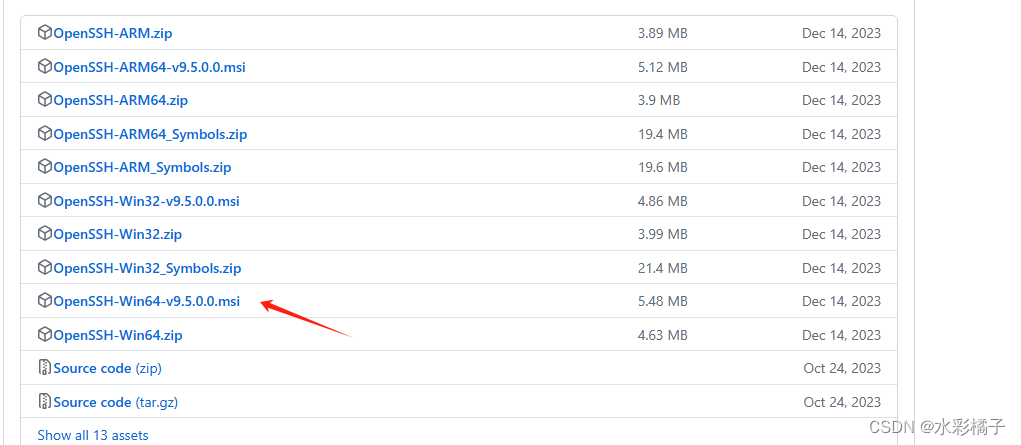
安装到windows 服务器 同时配置防火墙规则
sshpiper 配置windows
- from:- username: "win"to:host: 10.99.50.222:22username: "administrator"ignore_hostkey: true
![[开源软件] 支持链接汇总](http://pic.xiahunao.cn/[开源软件] 支持链接汇总)








 SPI 应用编程基础)

)
![[AIGC] Java HashMap原理解析:深入探索键值对存储和检索的内部机制](http://pic.xiahunao.cn/[AIGC] Java HashMap原理解析:深入探索键值对存储和检索的内部机制)



)


)