目录
- 实验条件
- 网络拓朴
- 实验目的
- 开始配置
- 1. R2 Ping R3确定基础网络是通的
- 2. 配置R2
- 3. 配置R3
- 4. 测试
实验条件
网络拓朴
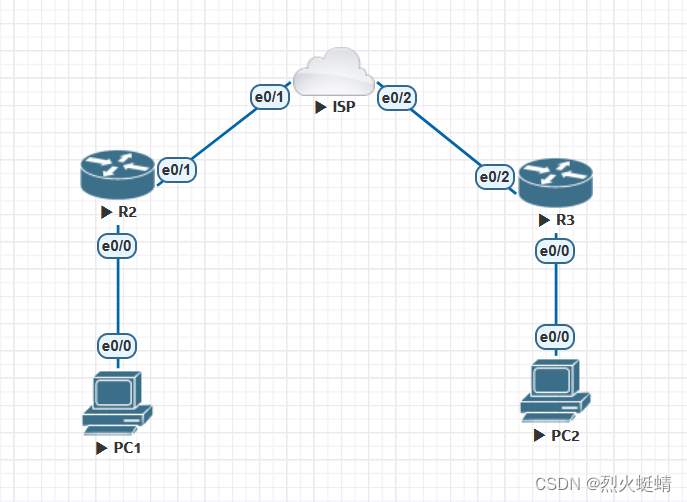
实验目的
为PC1和PC2建立IPSec VPN
PC1可以ping通PC2
开始配置
1. R2 Ping R3确定基础网络是通的
R2#show ip int br
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 192.168.1.254 YES TFTP up up
Ethernet0/1 12.1.1.2 YES TFTP up up
Ethernet0/2 unassigned YES TFTP administratively down down
Ethernet0/3 unassigned YES TFTP administratively down down
NVI0 192.168.1.254 YES unset up up
R2#ping 13.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 13.1.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R2#ping 13.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 13.1.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R2#ping 192.168.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 ms
R2#ping 192.168.2.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.254, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
基本网络可以
2. 配置R2
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#crypto isakmp policy 10
R2(config-isakmp)#encryption aes 256
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#hash sha512
R2(config-isakmp)#group 5
R2(config-isakmp)#lifetime 3600
R2(config-isakmp)#crypto isakmp key CISCO address 13.1.1.3
R2(config)#crypto ipsec transform-set mySET esp-aes 256 esp-sha512-hmac
R2(cfg-crypto-trans)#mode tunnel
R2(cfg-crypto-trans)#crypto map myMAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peerand a valid access list have been configured.
R2(config-crypto-map)#set peer 13.1.1.3
R2(config-crypto-map)#match address 101
R2(config-crypto-map)#access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.$
R2(config)#int e0/1
R2(config-if)#crypto map myMAP
R2(config-if)#
*Mar 31 13:21:50.243: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
3. 配置R3
R3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#crypto isakmp policy 10
R3(config-isakmp)#encryption aes 256
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#hash sha512
R3(config-isakmp)#group 5
R3(config-isakmp)#lifetime 3600
R3(config-isakmp)#crypto isakmp key CISCO address 12.1.1.2
R3(config)#crypto ipsec transform-set mySET esp-aes 256 esp-sha512-hmac
R3(cfg-crypto-trans)#mode tunnel
R3(cfg-crypto-trans)#crypto map myMAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peerand a valid access list have been configured.
R3(config-crypto-map)#set peer 12.1.1.2
R3(config-crypto-map)#match address 101
R3(config-crypto-map)#access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.$
R3(config)#int e0/2
R3(config-if)#crypto map myMAP
R3(config-if)#
*Mar 31 13:26:16.710: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R3(config-if)#
4. 测试
R4#ping 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
..!!!
Success rate is 60 percent (3/5), round-trip min/avg/max = 1/1/1 ms
R4#ping 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R4#

实验完成







函数 用法详解)

)


)






