实验11 无线网设备配置.......................................................... - 97 -
实验12 单臂路由器配置........................................................ - 106 -
实验13 防火墙配置................................................................. - 113 -
实验11 无线网设备配置
一、实验目的与要求:
1.掌握无线网设备的配置命令。
2.掌握无线AC和AP配置的步骤和方法。
二、实验内容:
1.掌握无线网设备的配置命令。
2.掌握无线AC和AP配置的步骤。
三、实验器材:
计算机 + 网络设备(华为路由器)
四、实验步骤:
以下是最简单的拓扑图及需求:
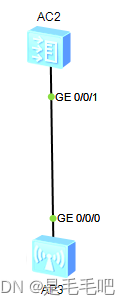
使用VLAN1作为AP管理VLAN,使用VLAN100作为用户业务VLAN,ssid为wlan-lab,密码为123456789,以下是配置:
配置VLAN及三层接口
[AC]int vlan 1
[AC-Vlanif1]ip address 192.168.1.254 24
[AC]vlan 100
[AC-vlan100]interface vlan 100
[AC-Vlanif100]ip address 192.168.100.254 24
配置DHCP地址池
[AC]dhcp enable
[AC]ip poo vlan1
[AC-ip-pool-vlan1]network 192.168.1.0 mask 24
[AC-ip-pool-vlan1]gateway 192.168.1.254
[AC-ip-pool-vlan1]option 43 sub-option 2 ip-address 192.168.1.254
[AC]ip poo vlan100
[AC-ip-pool-vlan100]network 192.168.100.0 mask 24
[AC-ip-pool-vlan100]gateway-list 192.168.100.254
引用DHCP地址池
[AC]interface vlan 1
[AC-Vlanif1]dhcp select global
[AC]interface vlan 100
[AC-Vlanif100]dhcp select global
在开始无线部分配置前,你需要知道这种图,先耐下性子把这张图看完,你才能看得懂我接下来的配置:
无线配置
[AC]capwap source interface Vlanif 1
##先配置CAPWAP隧道的管理接口地址
[AC-wlan-view]ap auth-mode mac-auth
[AC-wlan-view]ap whitelist mac 00e0-fc1e-4960
##配置AP白名单,默认情况下是MAC认证,所以要将AP的MAC地址添加到白名单中,完成这一步之后,要确保AP已经正常上线,如果上线失败,则说明前面的步骤肯定是少了,只有当AP正常上线了之后,才能开始后面的配置
[AC-wlan-view]ssid
[AC-wlan-view]ssid-profile name wlan-lab
[AC-wlan-ssid-prof-wlan-lab]ssid wlan-lab
##配置SSID模版,设置SSID
[AC-wlan-view]security-profile name wlan-lab
[AC-wlan-sec-prof-wlan-lab]security wpa2 psk pass-phrase 123456789 aes
##配置认证模版,设置无线密码
[AC-wlan-view]vap-profile name default
[AC-wlan-vap-prof-default]security-profile wlan-lab
[AC-wlan-vap-prof-default]ssid-profile wlan-lab
[AC-wlan-vap-prof-default]service-vlan vlan-id 100
##配置VAP模版,绑定SSID模版,认证模版,配置用户业务VLAN(连接至此VAP的STA将会被划入该VLAN)
[AC-wlan-view]ap-group name default
[AC-wlan-ap-group-default]vap-profile default wlan 1 radio 0 ##开启2.4g频段射频
[AC-wlan-ap-group-default]vap-profile default wlan 1 radio 1 ##开启5.8g频段射频
##开启该VAP的射频功能,发射无线信号
此练习总结:我建议是你将这个实验多做几遍,可以加深你对这个无线配置框架的印象,看着表从右往左配置,因为右边总是被左边包含,一层一层的包含关系,分的非常明细,不会搞混,刚开始接触时会觉得很麻烦,但是熟练之后会发现,一个模块一个模块之间,互不干扰,互相配合,互相包含,这个关系会使配置变得非常的简单

##使用VLAN1作为AP管理VLAN,使用VLAN100作为用户业务VLAN,SSID为wlan-lab,密码为wlan-lab123,认证方式为wpa2,AP1负责2.4g频段射频,AP2负责5.8g频段射频
VLAN及端口配置
[AC6005]vlan 100
[AC6005]interface g0/0/1
[AC6005-GigabitEthernet0/0/1]port link-type trunk
[AC6005-GigabitEthernet0/0/1]port trunk allow-pass vlan all
[AC6005-GigabitEthernet0/0/1]
[AC6005]interface g0/0/2
[AC6005-GigabitEthernet0/0/2]port link-type trunk
[AC6005-GigabitEthernet0/0/2]port trunk allow-pass vlan all
[AC6005]interface vlan 1
[AC6005-Vlanif1]ip address 192.168.1.254 24
[AC6005]interface vlan 100
[AC6005-Vlanif100]ip add 192.168.100.254 24
DHCP地址池及关联接口配置
[AC6005]dhcp enable
[AC6005]ip pool vlan1
[AC6005-ip-pool-vlan1]network 192.168.1.0 mask 24
[AC6005-ip-pool-vlan1]gateway 192.168.1.254
[AC6005-ip-pool-vlan1]option 43 sub-option 2 ip-address 192.168.1.254
[AC6005]ip pool vlan100
[AC6005-ip-pool-vlan100]network 192.168.100.0 mask 24
[AC6005-ip-pool-vlan100]gateway 192.168.100.254
[AC6005]interface vlan 1
[AC6005-Vlanif1]dhcp select global
[AC6005-Vlanif1]int vlan 100
[AC6005-Vlanif100]dhcp select global
无线配置
[AC6605-wlan-view]capwap source interface vlanif1
AP认证配置
[AC6605-wlan-view]ap auth-mode mac-auth
[AC6605-wlan-view] ap whitelist mac 00e0-fc0d-7770
[AC6605-wlan-view] ap whitelist mac 00e0-fccd-3a90
SSID模版配置
[AC6605-wlan-view]ssid-profile name wlan-lab
[AC6605-wlan-ssid-prof-wlan-lab]ssid wlan-lab
安全模版配置
[AC6605-wlan-view]security-profile name wlan-lab
[AC6605-wlan-sec-prof-wlan-lab]security wpa2 psk pass-phrase wlan-lab123 aes
VAP模版配置
[AC6605-wlan-view]vap-profile name wlan-lab
[AC6605-wlan-vap-prof-wlan-lab]service-vlan vlan-id 100
[AC6605-wlan-vap-prof-wlan-lab]security-profile wlan-lan
[AC6605-wlan-vap-prof-wlan-lab]ssid-profile wlan-lab
射频配置
[AC6605-wlan-view]ap-id 0 ##因为我这里AP1上线之后自动关联到了ap-id0,所以这里请根据你的情况灵活变化
[AC6605-wlan-ap-0]vap-profile wlan-lab wlan 1 radio 0 ##激活ap1的2.4g频段
[AC6605-wlan-view]ap-id 1 ##因为我这里AP2上线之后自动关联到了ap-id0,所以这里请根据你的情况灵活变化
[AC6605-wlan-ap-1]vap-profile wlan-lab wlan 1 radio 1 ##激活ap1的5.8g频段
这个实验需要在第一个实验完成并且熟练之后,才能完成并理解这个实验,否则,你根本不知道我在配什么,下图就是配置完成之后的无线射频

企业网中最常见的是多个SSID,比如一个Guest,一个Internet,连接到Guest的外来用户只能访问内部业务,连接到Internet的用户可以访问互联网,我们这里就来做一下这个实验,要求:Guest连接的用户归纳到VLAN100,Internet连接的用户归纳到VLAN200,Guest为开放式认证,Internet为WPA2认证,密钥为123456789, 两个AP分别发送一个SSID的两个频段,其中AP1负责SSID:Guest的下发,AP2负责SSID:Internet的下发,以下是拓扑图及配置:
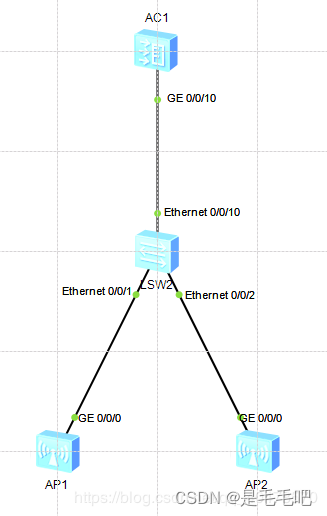
VLAN及端口配置
[AC6605]vlan batch 100 200
[AC6605]interface g0/0/10
[AC6605-GigabitEthernet0/0/10]port link-type trunk
[AC6605-GigabitEthernet0/0/10]port trunk allow vlan all
接口地址配置
[AC6605]interface vlan 1
[AC6605-Vlanif1]ip address 192.168.1.254 24
[AC6605]interface vlan 100
[AC6605-Vlanif100]ip address 192.168.100.254 24
[AC6605]interface vlan 200
[AC6605-Vlanif200]ip address 192.168.200.254 24
DHCP地址池及关联接口配置
[AC6605]dhcp enable
[AC6605]ip pool vlan1
[AC6605-ip-pool-vlan1]network 192.168.1.0 mask 24
[AC6605-ip-pool-vlan1]gateway 192.168.1.254
[AC6605-ip-pool-vlan1]option 43 sub-option 2 ip-address 192.168.1.254
[AC6605]ip pool vlan100
[AC6605-ip-pool-vlan100]network 192.168.100.0 mask 24
[AC6605-ip-pool-vlan100]gateway 192.168.100.254
[AC6605]ip pool vlan200
[AC6605-ip-pool-vlan200]network 192.168.200.0 mask 24
[AC6605-ip-pool-vlan200]gateway 192.168.200.254
[AC6605]interface vlan 1
[AC6605-Vlanif1]dhcp select global
[AC6605]interface vlan 100
[AC6605-Vlanif100]dhcp select global
[[AC6605]interface vlan 200
[AC6605-Vlanif200]dhcp select global
WLAN无线配置
[AC6605]capwap source interface vlan 1
##设置CAPWAP隧道地址
[AC6605]wlan
[AC6605-wlan-view]ap whitelist mac 00e0-fc22-24b0
[AC6605-wlan-view]ap whitelist mac 00e0-fcd3-49b0
##设置AP白名单,在做任何配置之前,先确保AP成功上线
[AC6605-wlan-view]ssid-profile name Guest
[AC6605-wlan-ssid-prof-Guest]ssid Guest
[AC6605-wlan-view]ssid-profile name Internet
[AC6605-wlan-ssid-prof-Internet]ssid Internet
##配置SSID模版
[AC6605-wlan-view]security-profile name Guest
[AC6605-wlan-sec-prof-Guest]security open
[AC6605-wlan-view]security-profile name Internet
[AC6605-wlan-sec-prof-Internet]security wpa2 psk pass-phrase 123456789 aes
##配置认证模版
[AC6605-wlan-view]vap-profile name Guest
[AC6605-wlan-vap-prof-Guest]ssid-profile Guest
[AC6605-wlan-vap-prof-Guest]security-profile Guest
[AC6605-wlan-vap-prof-Guest]service-vlan vlan-id 100
[AC6605-wlan-vap-prof-Guest]forward-mode direct-forward
##创建名为Guest的VAP模版,并分别调用SSID模版,安全模版,设置转发状态,以及关联VLAN
[AC6605-wlan-view]vap-profile name Internet
[AC6605-wlan-vap-prof-Internet]ssid Internet
[AC6605-wlan-vap-prof-Internet]security-profile Internet
[AC6605-wlan-vap-prof-Internet]service-vlan vlan-id 200
[AC6605-wlan-vap-prof-Internet]forward-mode direct-forward
##创建名为Internet的VAP模版,并分别调用SSID模版,安全模版,设置转发状态,以及关联VLAN
[AC6605-wlan-view]ap-id 0
[AC6605-wlan-ap-0]vap-profile Guest wlan 1 radio 0
[AC6605-wlan-ap-0]vap-profile Guest wlan 1 radio 1
[AC6605-wlan-view]ap-id 1
[AC6605-wlan-ap-1]vap-profile Internet wlan 1 radio 0
[AC6605-wlan-ap-1]vap-profile Internet wlan 1 radio 1
##分别在AP1调用名为Guest的VAP模板,在AP2调用名为Internet的VAP模板
下图是完成之后射频拓扑图:
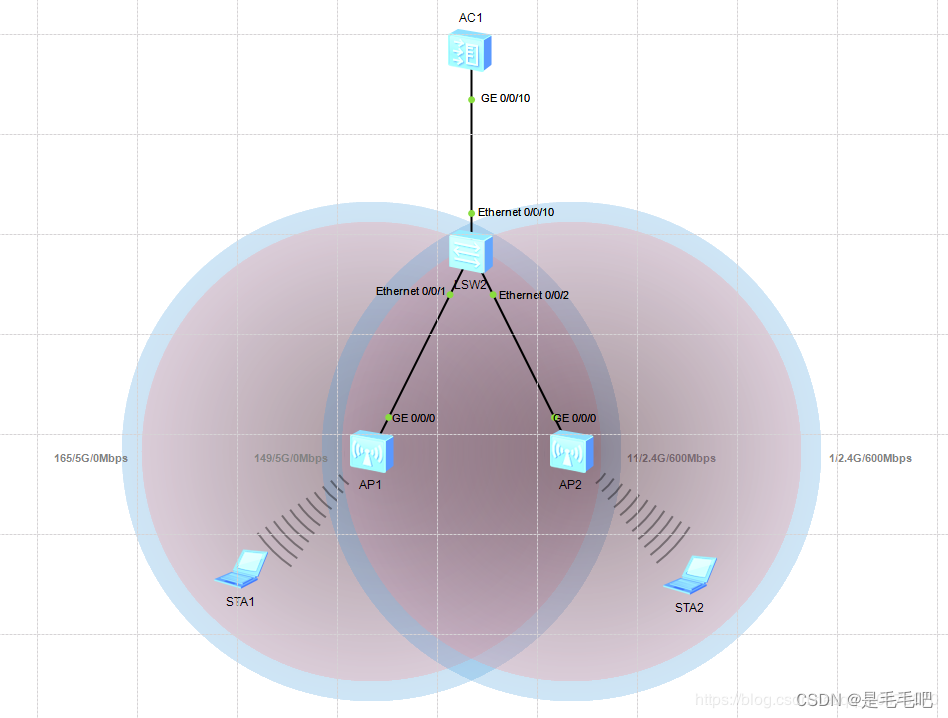
总结:华为的这个无线配置架构刚开始学的时候会觉得很杂乱,所以我的建议是,看着他的架构图,在做配置,这样会清晰很多,其次就是多练习,以上的三个拓扑每个都多做几遍也就差不多熟练了,然后再回过头来看这个架构图就觉得很清楚了
实验12 单臂路由器配置
一、实验目的与要求:
1.掌握单臂路由器的配置命令。
2.掌握单臂路由器的过程
二、实验内容:
1.掌握单臂路由器的配置命令。
2.掌握单臂路由器的过程
三、实验器材:
计算机 + 网络设备(华为路由器)
单臂路由配置
1、单臂路由实现VLAN间路由
(1)实验拓扑

(2)实验IP
| 设备 | 接口 | IP 地址 | 子网掩码 | 默认网关 |
| R1 | GE0/0/1 | 192.168.1.254 | 255.255.255.0 | N/A |
| GE0/0/2 | 192.168.2.254 | 255.255.255.0 | N/A | |
| GE0/0/3 | 192.168.3.254 | 255.255.255.0 | N/A | |
| PC1 | Ethernet0/0/1 | 192.168.1.1 | 255.255.255.0 | 192.168.1.254 |
| PC2 | Ethernet0/0/1 | 192.168.2.1 | 255.255.255.0 | 192.168.2.254 |
| PC3 | Ethernet0/0/1 | 192.168.3.1 | 255.255.255.0 | 192.168.3.254 |
(3)实验步骤
基本配置
PC1到PC3 主机设置IP地址。如下

<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname S1
[S1]
配置两台交换机
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname S2
[S2]
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname S3
[S3]
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname R1
[R1]
- 创建VLAN ,配置ACCESS接口
[S2]vlan 10
[S2-vlan10]
Dec 7 2017 21:31:15-08:00 S1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 5, the change loop count is 0, and the maximum number of records is 4095.
[S2-vlan10] description HR //描述经理
[S2-vlan10]vlan 20
[S2-vlan20]
Dec 7 2017 21:31:45-08:00 S1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 6, the ch
ange loop count is 0, and the maximum number of records is 4095.
[S2-vlan20]description market //描述市场部
[S2-vlan20]
[S3]vlan 30
[S2-vlan30]
Dec 7 2017 21:31:15-08:00 S1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 5, the change loop count is 0, and the maximum number of records is 4095.
[S1-vlan30] description Manager //描述人事部
使用display vlan 命令查看VLAN 的相关信息
[S2]dis vlan
The total number of vlans is : 3
--------------------------------------------------------------------------------
U: Up; D: Down; TG: Tagged; UT: Untagged;
MP: Vlan-mapping; ST: Vlan-stacking;
#: ProtocolTransparent-vlan; *: Management-vlan;
--------------------------------------------------------------------------------
VID Type Ports
--------------------------------------------------------------------------------
1 common UT:Eth0/0/1(U) Eth0/0/2(U) Eth0/0/3(D) Eth0/0/4(D)
Eth0/0/5(D) Eth0/0/6(D) Eth0/0/7(D) Eth0/0/8(D)
Eth0/0/9(D) Eth0/0/10(D) Eth0/0/11(D) Eth0/0/12(D)
Eth0/0/13(D) Eth0/0/14(D) Eth0/0/15(D) Eth0/0/16(D)
Eth0/0/17(D) Eth0/0/18(D) Eth0/0/19(D) Eth0/0/20(D)
Eth0/0/21(D) Eth0/0/22(D) GE0/0/1(D) GE0/0/2(U)
10 common
20 common
VID Status Property MAC-LRN Statistics Description
--------------------------------------------------------------------------------
1 enable default enable disable VLAN 0001
10 enable default enable disable HR
20 enable default enable disable Market
[S2]
配置ACCESS 接口
在S2 h E0/0/1和E0/0/2接口类型配置为ACCESS类型接口,对应的VLAN
[S2]int eth 0/0/1
[S2-Ethernet0/0/1]port link-type access //定义交换机连接PC 机的ACCESS 接口
[S2-Ethernet0/0/1]port default vlan 10 //接口默认为VLAN 10
[S2-Ethernet0/0/2]int eth 0/0/2
[S2-Ethernet0/0/2]port link-type access //定义交换机连接PC 机的ACCESS 接口
[S2-Ethernet0/0/2]port default vlan 20 //接口默认为VLAN 20
在S3 h E0/0/1接口类型配置为ACCESS类型接口,对应的VLAN
[S3]int eth 0/0/1
[S3-Ethernet0/0/1]port link-type access //定义交换机连接PC 机的ACCESS 接口
[S2-Ethernet0/0/1]port default vlan 30 //接口默认为VLAN 30
配置Trunk接口
在S2和S3上配置GE0/0/2接口配置为trunk 接口,允许所有VLAN 通过
[S2]int G 0/0/2
[S2-GigabitEthernet0/0/2]port link-type trunk
Dec 11 2017 14:06:12-08:00 S1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 6, the ch
ange loop count is 0, and the maximum number of records is 4095.psys
Error: Unrecognized command found at '^' position.
[S2-GigabitEthernet0/0/2]port trunk allow-pass vlan all
[S3]int G 0/0/2
[S3-GigabitEthernet0/0/2]port link-type trunk
Dec 11 2017 14:06:12-08:00 S1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 6, the ch
ange loop count is 0, and the maximum number of records is 4095.psys
Error: Unrecognized command found at '^' position.
[S3-GigabitEthernet0/0/2]port trunk allow-pass vlan all
在S1上创建VLAN 10、VLAN 20和VLAN 30,并配置交换机与路由器相连的接口为trunk 接口,允许所有VLAN 通过
[S1]VLAN 10
[S1-vlan10]Vlan 20
[S1-vlan20]Vlan 30
[S1-vlan10]int g 0/0/2
[S1-GigabitEthernet0/0/2]port link-type trunk
[S1-GigabitEthernet0/0/2]port trunk allow-pass vlan all
[S1-GigabitEthernet0/0/2]int g 0/0/3
[S1-GigabitEthernet0/0/3]port link-type trunk
Dec 11 2017 14:29:11-08:00 S3 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 5, the ch
ange loop count is 0, and the maximum number of records is 4095.
[S1-GigabitEthernet0/0/3]port trunk allow-pass vlan all
[S1-GigabitEthernet0/0/3]int g 0/0/1
[S1-GigabitEthernet0/0/1]port link-type trunk
Dec 11 2017 14:29:11-08:00 S3 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 5, the ch
ange loop count is 0, and the maximum number of records is 4095.
[S1-GigabitEthernet0/0/1]port trunk allow-pass vlan all
配置路由器子接口和IP 地址
在R1创建子接口GE0/0/1.1,配置IP为192.168.1.254/24,作为人事部网关地址。
[R1]int g 0/0/1.1
[R1-GigabitEthernet0/0/1.1]ip add 192.168.1.254 24
在R1创建子接口GE0/0/1.2,配置IP为192.168.2.254/24,作为市场部网关地址。
[R1]int g 0/0/1.2
[R1-GigabitEthernet0/0/1.2]ip add 192.168.2.254 24
在R1创建子接口GE0/0/1.3,配置IP为192.168.3.254/24,作为经理网关地址。
[R1]int g 0/0/1.3
[R1-GigabitEthernet0/0/1.3]ip add 192.168.3.254 24
测试PC1上测试 与PC2和PC3间的连通性
PC>ping 192.168.2.1
From 192.168.2.1: Destination host unreachable
From 192.168.2.1: Destination host unreachable
From 192.168.2.1: Destination host unreachable
From 192.168.2.1: Destination host unreachable
From 192.168.2.1: Destination host unreachable
PC>ping 192.168.3.1
From 192.168.3.1: Destination host unreachable
From 192.168.3.1: Destination host unreachable
From 192.168.3.1: Destination host unreachable
From 192.168.3.1: Destination host unreachable
From 192.168.3.1: Destination host unreachable
配置路由器子接口封装VLAN
在R1创建子接口GE0/0/1.1上封装VLAN 10,同样在GE0/0/1.2和GE0/0/1.3分别封装VLAN 20和VLAN 30,并开启子接口的ARP 广播功能。
[R1-GigabitEthernet0/0/1.1]dotlq termination Vid 10 //配置子接口对一层TAG 报文的终结功能
[R1-GigabitEthernet0/0/1.1]arp broadcast enable //开启子接口的ARP广播功能
[R1-GigabitEthernet0/0/1.1]int g 0/0/1.2
[R1-GigabitEthernet0/0/1.2]dotlq termination Vid 20 //配置子接口对一层TAG 报文的终结功能
[R1-GigabitEthernet0/0/1.2]arp broadcast enable //开启子接口的ARP广播功能
[R1-GigabitEthernet0/0/1.2]int g 0/0/1.3
[R1-GigabitEthernet0/0/1.3]dotlq termination Vid 30 //配置子接口对一层TAG 报文的终结功能
[R1-GigabitEthernet0/0/1.3]arp broadcast enable //开启子接口的ARP广播功能
[R1] dis ip int brief //查看路由器接口状态
[R1] dis ip routing-table //查看路由表
在PC1分别测试与网关地址192.168.1.254 和PC2 间的连通性
PC>ping 192.168.1.254
Ping 192.168.1.254: 32 data bytes, Press Ctrl_C to break
From 192.168.1.254: bytes=32 seq=1 ttl=128 time=31 ms
From 192.168.1.254: bytes=32 seq=2 ttl=128 time=47 ms
From 192.168.1.254: bytes=32 seq=3 ttl=128 time=46 ms
From 192.168.1.254: bytes=32 seq=4 ttl=128 time=31 ms
From 192.168.1.254: bytes=32 seq=5 ttl=128 time=47 ms
PC>ping 192.168.2.1
Ping 192.168.2.1: 32 data bytes, Press Ctrl_C to break
From 192.168.2.1: bytes=32 seq=1 ttl=128 time=31 ms
From 192.168.2.1: bytes=32 seq=2 ttl=128 time=47 ms
From 192.168.2.1: bytes=32 seq=3 ttl=128 time=46 ms
From 192.168.2.1: bytes=32 seq=4 ttl=128 time=31 ms
From 192.168.2.1: bytes=32 seq=5 ttl=128 time=47 ms
可以观察到。通信正常,在PC1上Tracert PC2
PC>tracert 192.168.2.1 //跟踪路由
五、实验结果:
完成VLAN划分。
六、实验小结:
能熟练完成VLAN划分的方法。
实验13 防火墙配置
一、实验目的与要求:
1.掌握网络安全管理方法;
2.掌握防火墙配置方法。
二、实验内容:
1.掌握网络安全管理方法;
2.掌握防火墙配置方法。
三、实验器材:
计算机+华为模拟器+防火墙
四、实验步骤:
防火墙默认的管理接口为g0/0/0,默认的ip地址为192.168.0.1/24,默认g0/0/0接口开启了dhcp server,默认用户名为admin,默认密码为Admin@123
配置案例
1.1 拓扑图
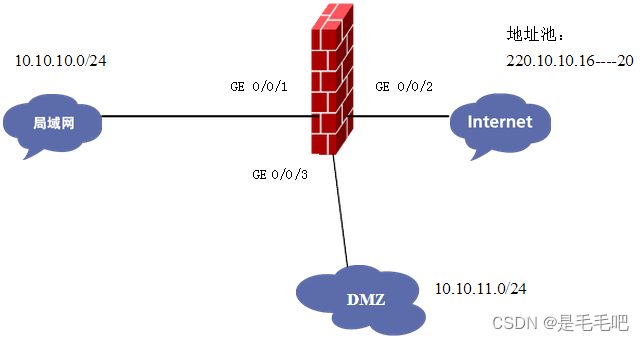 GE 0/0/1:10.10.10.1/24
GE 0/0/1:10.10.10.1/24
GE 0/0/2:220.10.10.16/24
GE 0/0/3:10.10.11.1/24
WWW服务器:10.10.11.2/24(DMZ区域)
FTP服务器:10.10.11.3/24(DMZ区域)
1.2 Telnet配置
配置VTY 的优先级为3,基于密码验证。
# 进入系统视图。
<USG5300> system-view
# 进入用户界面视图
[USG5300] user-interface vty 0 4
# 设置用户界面能够访问的命令级别为level 3
[USG5300-ui-vty0-4] user privilege level 3
配置Password验证
# 配置验证方式为Password验证
[USG5300-ui-vty0-4] authentication-mode password
# 配置验证密码为lantian
[USG5300-ui-vty0-4] set authentication password simple lantian ###最新版本的命令是authentication-mode password cipher huawei@123
配置空闲断开连接时间
# 设置超时为30分钟
[USG5300-ui-vty0-4] idle-timeout 30
[USG5300] firewall packet-filter default permit interzone untrust local direction inbound //不加这个从公网不能telnet防火墙。
基于用户名和密码验证
user-interface vty 0 4
authentication-mode aaa
aaa
local-user admin password cipher ]MQ;4\]B+4Z,YWX*NZ55OA!!
local-user admin service-type telnet
local-user admin level 3
firewall packet-filter default permit interzone untrust local direction inbound
如果不开放trust域到local域的缺省包过滤,那么从内网也不能telnet的防火墙,但是默认情况下已经开放了trust域到local域的缺省包过滤。
1.3 地址配置
内网:
进入GigabitEthernet 0/0/1视图
[USG5300] interface GigabitEthernet 0/0/1
配置GigabitEthernet 0/0/1的IP地址
[USG5300-GigabitEthernet0/0/1] ip address 10.10.10.1 255.255.255.0
配置GigabitEthernet 0/0/1加入Trust区域
[USG5300] firewall zone trust
[USG5300-zone-untrust] add interface GigabitEthernet 0/0/1
[USG5300-zone-untrust] quit
外网:
进入GigabitEthernet 0/0/2视图
[USG5300] interface GigabitEthernet 0/0/2
配置GigabitEthernet 0/0/2的IP地址
[USG5300-GigabitEthernet0/0/2] ip address 220.10.10.16 255.255.255.0
配置GigabitEthernet 0/0/2加入Untrust区域
[USG5300] firewall zone untrust
[USG5300-zone-untrust] add interface GigabitEthernet 0/0/2
[USG5300-zone-untrust] quit
DMZ:
进入GigabitEthernet 0/0/3视图
[USG5300] interface GigabitEthernet 0/0/3
配置GigabitEthernet 0/0/3的IP地址。
[USG5300-GigabitEthernet0/0/3] ip address 10.10.11.1 255.255.255.0
[USG5300] firewall zone dmz
[USG5300-zone-untrust] add interface GigabitEthernet 0/0/3
[USG5300-zone-untrust] quit
五、实验结果:
完成网络安全管理。
六、实验小结:
能熟练完成网络安全管理的方法。


另一个项目)


)












-- 缓存cache用法总结)
