目录
- 脚本源码
- 用法
- 效果及示例
- SSH 端口
- FTP 端口
版本:Grey Hack v0.7.3618 - Alpha
适用于SSH (22) 端口、FTP (21) 端口、HTTP (80) 端口、SMTP (25) 端口及3306/3307 端口 。
脚本源码
if params.len != 2 or params[0] == "-h" or params[0] == "--help" then exit("<b>Usage: "+program_path.split("/")[-1]+" [ip_address] [port]</b>")
metaxploit = include_lib("/lib/metaxploit.so")
if not metaxploit thenmetaxploit = include_lib(current_path + "/metaxploit.so")
end if
if not metaxploit then exit("Error: Can't find metaxploit library in the /lib path or the current folder")
address = params[0]
port = params[1].to_intnet_session = metaxploit.net_use( address, port )
if not net_session then exit("Error: can't connect to net session")
metaLib = net_session.dump_libprint("Founded " + metaLib.lib_name + " "+ metaLib.version)if not metaLib then exit("Error: TargetLib not found.")exploits = metaxploit.scan(metaLib)
for exploit in exploitsprint(exploit)result_lists = metaxploit.scan_address(metaLib, exploit).split("Unsafe check: ")[1:]for result_list in result_liststarget_str = result_list.split(".")[0]target_key = target_str.split(" ")[-1]result = metaLib.overflow(exploit, target_key[3:-4])print(target_key + ": " + typeof(result))print(result_list)end for
end for
用法
【脚本名】 【公网IP】 【端口号】
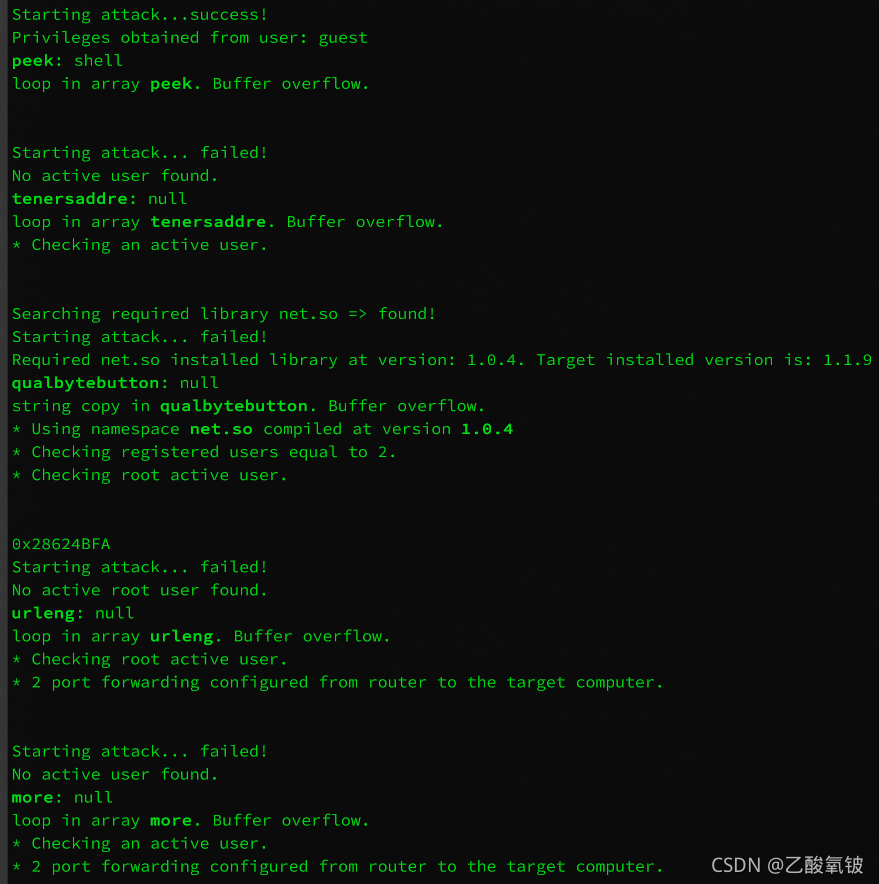
效果及示例
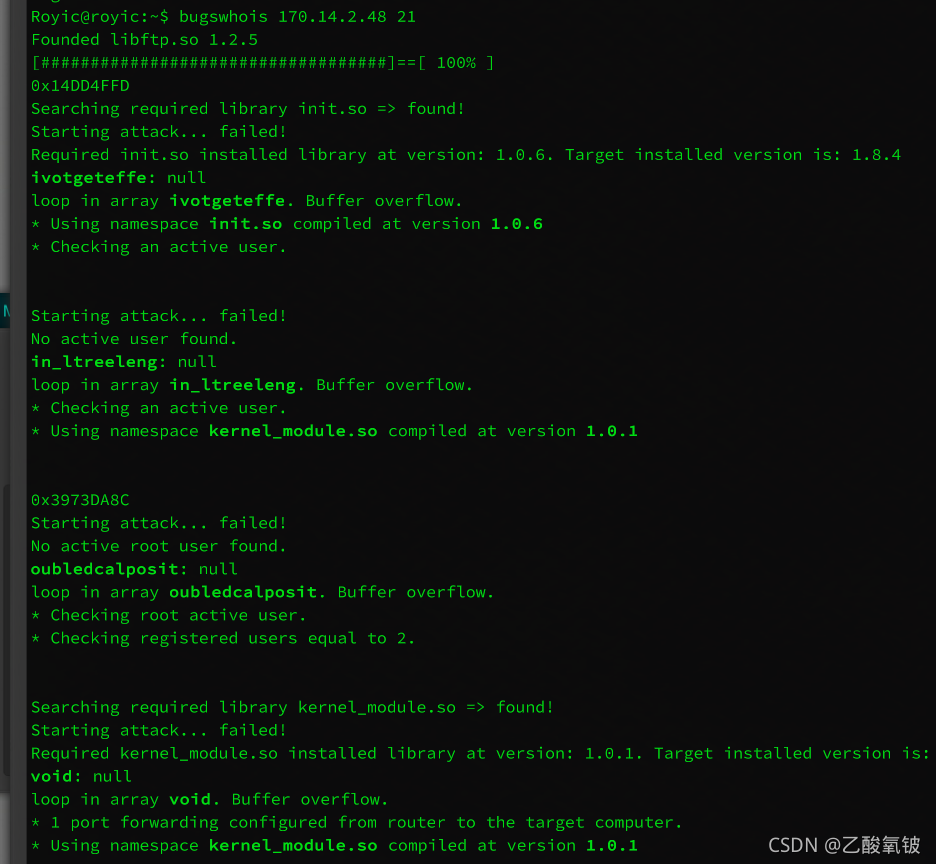
先检测目标端口库版本
再尝试遍历检测对应漏洞的内存地址、关键字和漏洞类型
并打印触发条件、所获得的权限或失败原因
SSH 端口
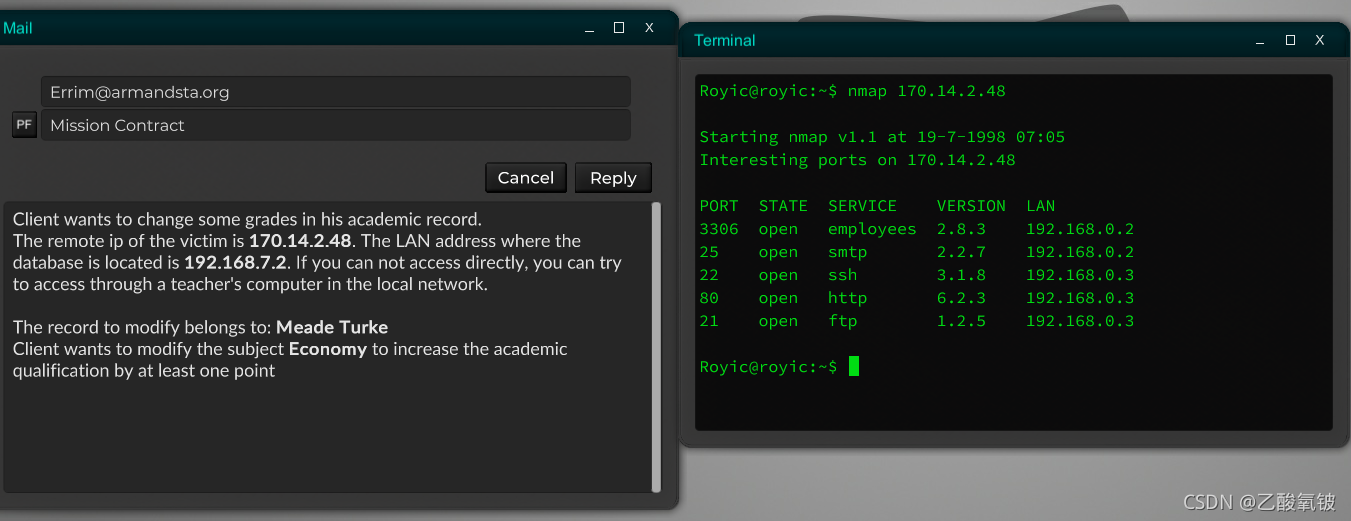
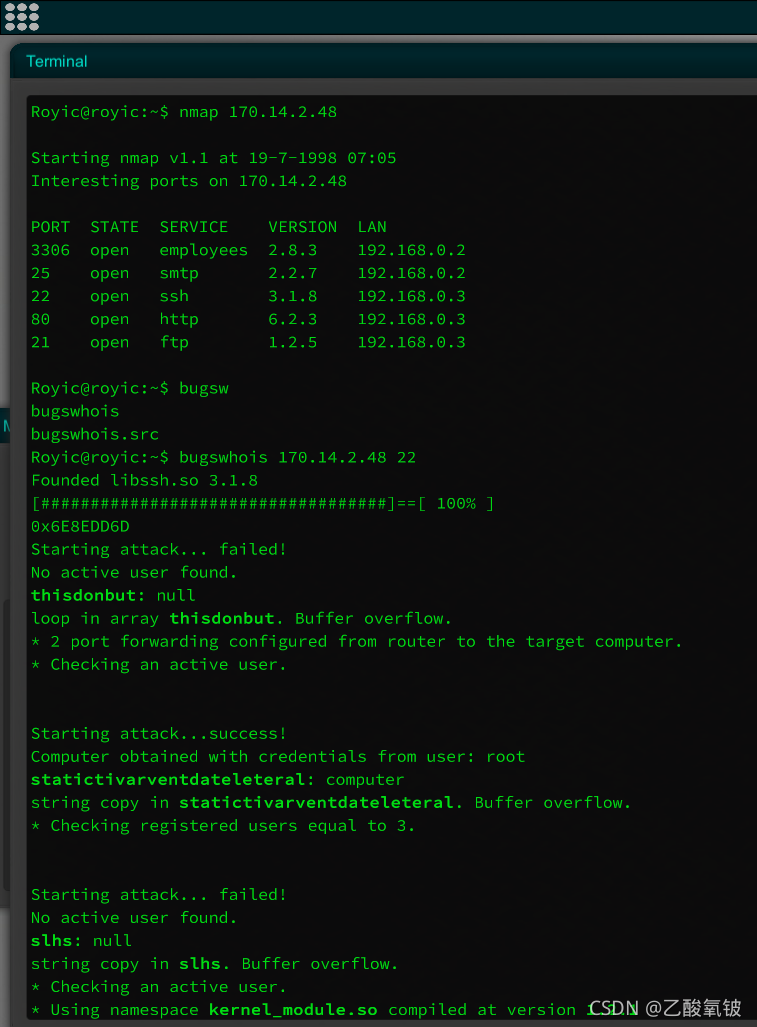
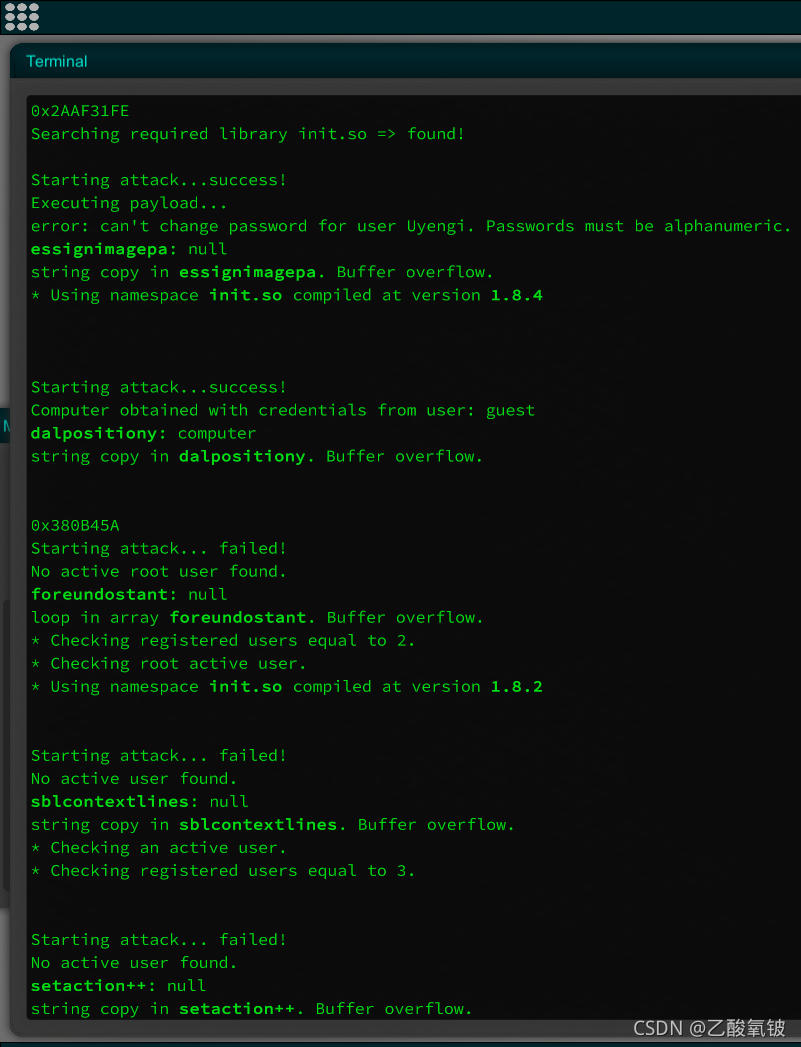
FTP 端口

















----基于注解开发bean作用范围与生命周期管理)

-POJ-2533)