题目链接:
https://adworld.xctf.org.cn/challenges/list
elf是一种对可执行文件,目标文件和库使用的文件格式,跟window下的PE文件格式类似。载入IDA后如果需要对此文件进行远程调试,需要用linux系统,比如说Ubuntu,kali等
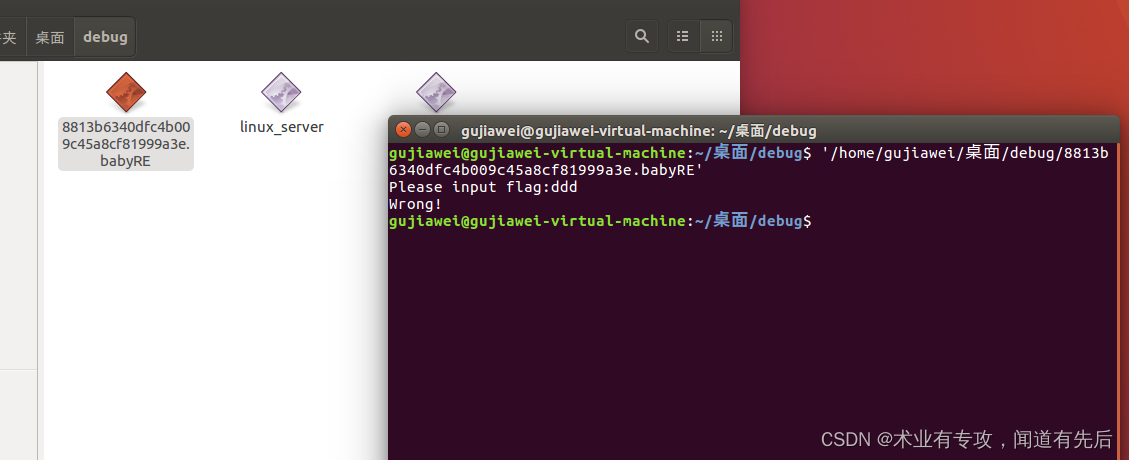
一般应对策略:使用按键U,告诉IDA,这是一个数据(通常是一个字节就够了),然后在下一个位置,点击C告诉IDA又可以开始按照代码来解释
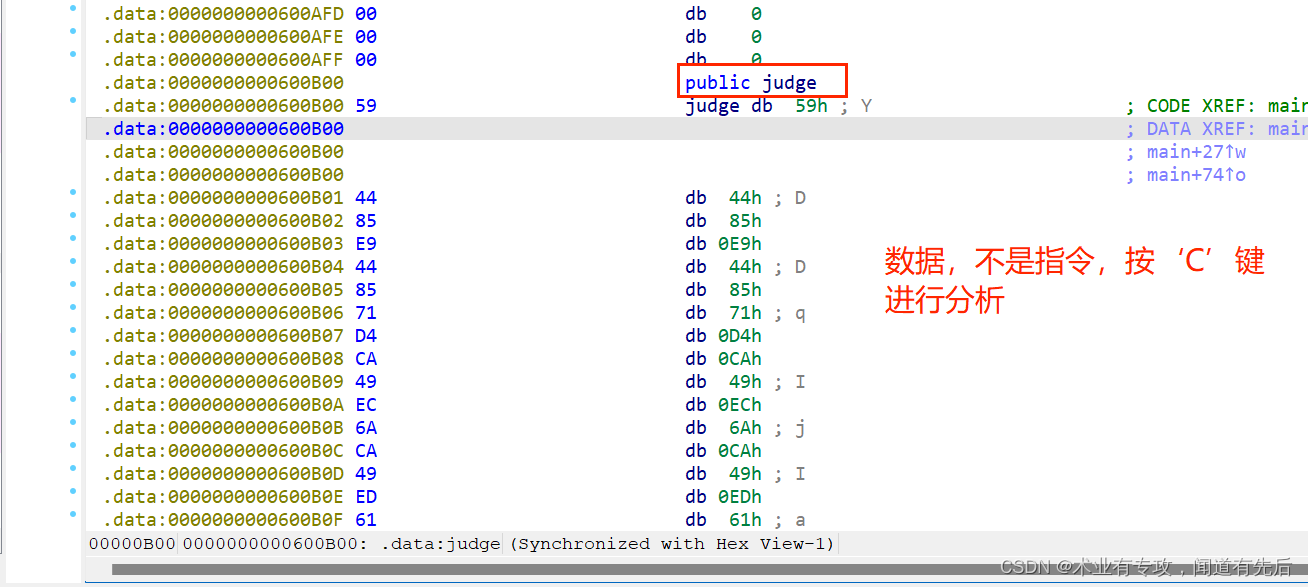
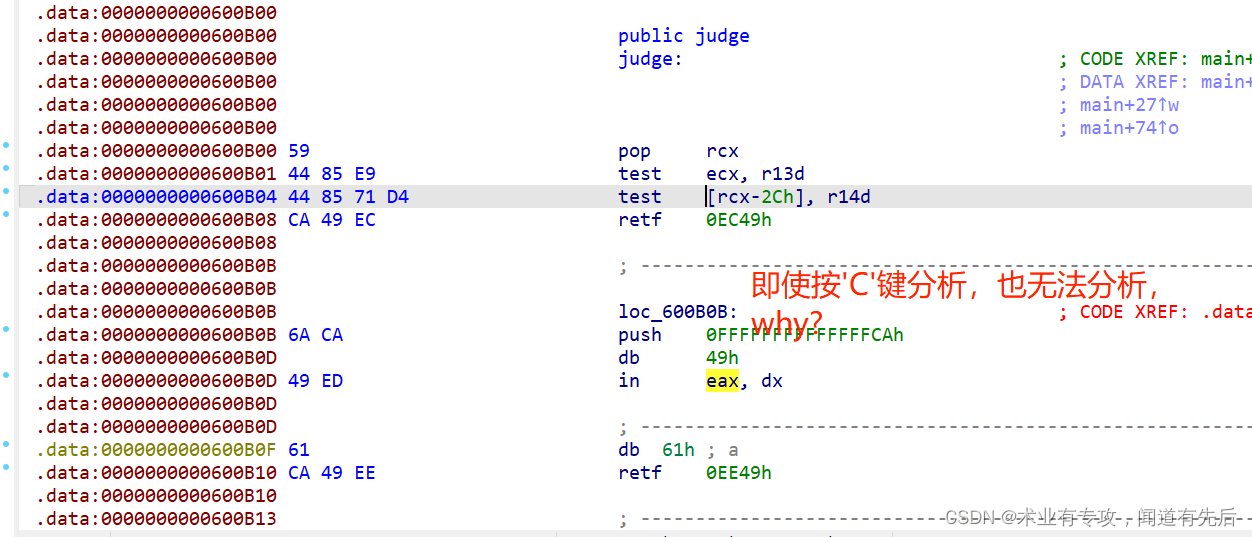
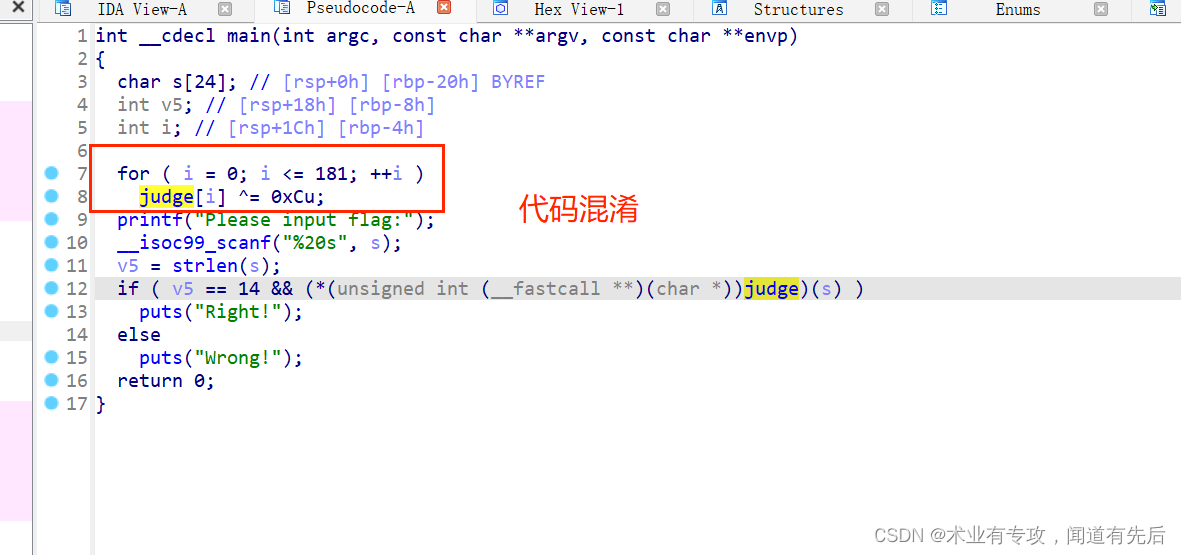
然后下面就是看汇编代码了:
先恶补一下汇编知识吧(要不真的看不懂汇编指令......)
'rbp'寄存器是一个基址指针寄存器,用于指向函数的栈帧。栈帧是函数在执行时在栈上所创建的一块内存区域,用于存储局部变量,函数参数,返回地址等信息。在函数调用过程中,‘rbp‘用于维护栈帧的指针,以便在函数执行结束后能够恢复调用者的上下文。
在函数调用过程中,通常会先将返回地址和其他寄存器的值(如’rbx‘,'rdi','rsi','rdx'等)压入栈中,然后将’rbp‘的值压入栈中
汇编代码分析:输入值循环与i进行异或,然后与str进行比较,如果相等则成功!
public judge
.data:0000000000600B00 judge: ; CODE XREF: main+80↑p
.data:0000000000600B00 ; DATA XREF: main+16↑r
.data:0000000000600B00 ; main+27↑w
.data:0000000000600B00 ; main+74↑o
.data:0000000000600B00 push rbp
.data:0000000000600B01 mov rbp, rsp
.data:0000000000600B04 mov [rbp-28h], rdi
.data:0000000000600B08 mov byte ptr [rbp-20h], 66h ; 'f'
.data:0000000000600B0C mov byte ptr [rbp-1Fh], 6Dh ; 'm'
.data:0000000000600B10 mov byte ptr [rbp-1Eh], 63h ; 'c'
.data:0000000000600B14 mov byte ptr [rbp-1Dh], 64h ; 'd'
.data:0000000000600B18 mov byte ptr [rbp-1Ch], 7Fh
.data:0000000000600B1C mov byte ptr [rbp-1Bh], 6Bh ; 'k'
.data:0000000000600B20 mov byte ptr [rbp-1Ah], 37h ; '7'
.data:0000000000600B24 mov byte ptr [rbp-19h], 64h ; 'd'
.data:0000000000600B28 mov byte ptr [rbp-18h], 3Bh ; ';'
.data:0000000000600B2C mov byte ptr [rbp-17h], 56h ; 'V'
.data:0000000000600B30 mov byte ptr [rbp-16h], 60h ; '`'
.data:0000000000600B34 mov byte ptr [rbp-15h], 3Bh ; ';'
.data:0000000000600B38 mov byte ptr [rbp-14h], 6Eh ; 'n'
.data:0000000000600B3C mov byte ptr [rbp-13h], 70h ; 'p'
.data:0000000000600B40 mov dword ptr [rbp-4], 0
.data:0000000000600B47 jmp short loc_600B71
.data:0000000000600B47
.data:0000000000600B49 ; ---------------------------------------------------------------------------
.data:0000000000600B49
.data:0000000000600B49 loc_600B49: ; CODE XREF: .data:0000000000600B75↓j
.data:0000000000600B49 mov eax, [rbp-4]
.data:0000000000600B4C movsxd rdx, eax
.data:0000000000600B4F mov rax, [rbp-28h]
.data:0000000000600B53 add rax, rdx
.data:0000000000600B56 mov edx, [rbp-4]
.data:0000000000600B59 movsxd rcx, edx
.data:0000000000600B5C mov rdx, [rbp-28h]
.data:0000000000600B60 add rdx, rcx
.data:0000000000600B63 movzx edx, byte ptr [rdx]
.data:0000000000600B66 mov ecx, [rbp-4] ; ecx=i
.data:0000000000600B69 xor edx, ecx ; input[i]^i
.data:0000000000600B6B mov [rax], dl
.data:0000000000600B6D add dword ptr [rbp-4], 1 ; i++
.data:0000000000600B6D
.data:0000000000600B71
.data:0000000000600B71 loc_600B71: ; CODE XREF: .data:0000000000600B47↑j
.data:0000000000600B71 cmp dword ptr [rbp-4], 0Dh
.data:0000000000600B75 jle short loc_600B49
.data:0000000000600B75
.data:0000000000600B77 mov dword ptr [rbp-4], 0
.data:0000000000600B7E jmp short loc_600BA9
.data:0000000000600B7E
.data:0000000000600B80 ; ---------------------------------------------------------------------------
.data:0000000000600B80
.data:0000000000600B80 loc_600B80: ; CODE XREF: .data:0000000000600BAD↓j
.data:0000000000600B80 mov eax, [rbp-4]
.data:0000000000600B83 movsxd rdx, eax
.data:0000000000600B86 mov rax, [rbp-28h]
.data:0000000000600B8A add rax, rdx
.data:0000000000600B8D movzx edx, byte ptr [rax]
.data:0000000000600B90 mov eax, [rbp-4]
.data:0000000000600B93 cdqe
.data:0000000000600B95 movzx eax, byte ptr [rbp+rax-20h]
.data:0000000000600B9A cmp dl, al
.data:0000000000600B9C jz short loc_600BA5
.data:0000000000600B9C
.data:0000000000600B9E mov eax, 0
.data:0000000000600BA3 jmp short loc_600BB4
.data:0000000000600BA3
.data:0000000000600BA5 ; ---------------------------------------------------------------------------
.data:0000000000600BA5
.data:0000000000600BA5 loc_600BA5: ; CODE XREF: .data:0000000000600B9C↑j
.data:0000000000600BA5 add dword ptr [rbp-4], 1
.data:0000000000600BA5
.data:0000000000600BA9
.data:0000000000600BA9 loc_600BA9: ; CODE XREF: .data:0000000000600B7E↑j
.data:0000000000600BA9 cmp dword ptr [rbp-4], 0Dh
.data:0000000000600BAD jle short loc_600B80
.data:0000000000600BAD
.data:0000000000600BAF mov eax, 1
.data:0000000000600BAF
.data:0000000000600BB4
.data:0000000000600BB4 loc_600BB4: ; CODE XREF: .data:0000000000600BA3↑j
.data:0000000000600BB4 pop rbp
.data:0000000000600BB5 retn
.data:0000000000600BB5编写脚本:
ff=[0x66,0x6D,0x63,0x64,0x7F,0x6B,0x37,0x64,0x3B,0x56,0x60,0x3B,0x6E,0x70]
flag=''
for i in range(0xE):ff[i]=ff[i]^iflag+=chr(ff[i])#chr()函数与ord()函数用于ASCII与字符之间的转换
print(flag)
#flag{n1c3_j0b}





)

)
)









