
r5上直接导入直连路由
r3和r2进行双点双向路由重分布
查看R3去往R5产生了次优路径:
因为是R2先互相引入的isis和ospf,所以R3会产生次优路径,如果是R3先相互引入ospf和isis,那就是R2去R5会产生次优路径,而R3本身不会。
通过终极解决方案:可以实现无论如何在R5上后来再发布什么路由都不会产生次优路径和环路产生了。
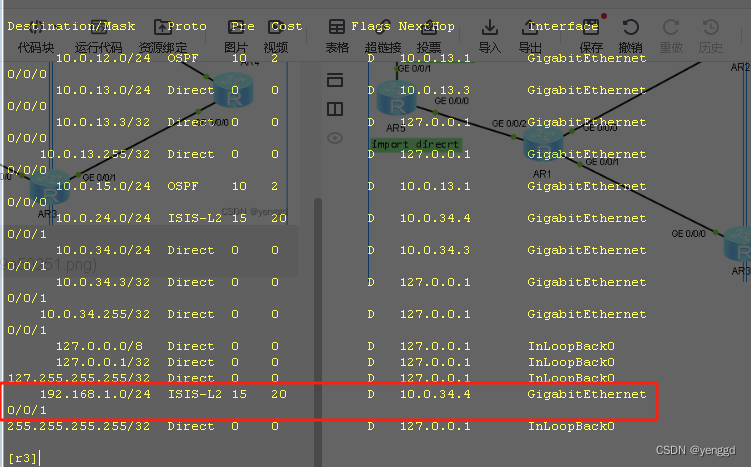
终极解决方案:
R2关键配置:
[Huawei]dis route-policy //下面2条路由策略是用于解决环路的
Route-policy : ospf-to-isisdeny : 10 (matched counts: 0)Match clauses : if-match tag 100 //和R3对标,这边禁掉R3已打过标签的包permit : 20 (matched counts: 0)Apply clauses : apply tag 200 Route-policy : isis-to-ospfdeny : 10 (matched counts: 0)Match clauses : if-match tag 300 //和R3对标,这边禁掉R3已打过标签的包permit : 20 (matched counts: 0)Apply clauses : apply tag 400 route-policy test permit node 10 //这个策略是用于解决次优路径的if-match tag 100 apply preference 150 ospf 1 import-route isis 1 route-policy isis-to-ospf //导入isis时加策略isis-to-ospfpreference ase 12 route-policy test //改ospf外部路由的协议优先级为12,改的时候顺便调用test策略把isis学到的打的tag 100 的协议优先级为150area 0.0.0.0 isis 1is-level level-2cost-style wide //必须为宽度量才能打tagnetwork-entity 49.0001.0000.0000.0002.00is-name R2import-route ospf 1 level-2 route-policy ospf-to-isis //导入ospf时加策略ospf-to-isis
R3关键配置:
[r3]dis route-policy //下面2条路由策略是用于解决环路的
Route-policy : isis-to-ospfdeny : 10 (matched counts: 0)Match clauses : if-match tag 200permit : 20 (matched counts: 0)Apply clauses : apply tag 100 Route-policy : ospf-to-isisdeny : 10 (matched counts: 0)Match clauses : if-match tag 400permit : 20 (matched counts: 0)Apply clauses : apply tag 300route-policy test permit node 10 //这个策略是用于解决次优路径的if-match tag 400apply preference 150 ospf 1 import-route isis 1 route-policy isis-to-ospf //导入isis时加策略isis-to-ospfpreference ase 12 route-policy test//改ospf外部路由的协议优先级为12,改的时候顺便调用test策略把isis 学到的打了tag 400 的协议优先级为150area 0.0.0.0 isis 1is-level level-2cost-style widenetwork-entity 49.0001.0000.0000.0003.00is-name R3import-route ospf 1 levle-2 route-policy ospf-to-isis //导入ospf时加策略ospf-to-isis
最终查看:
R2
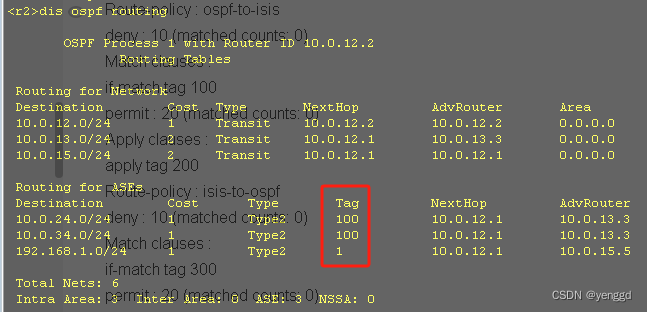
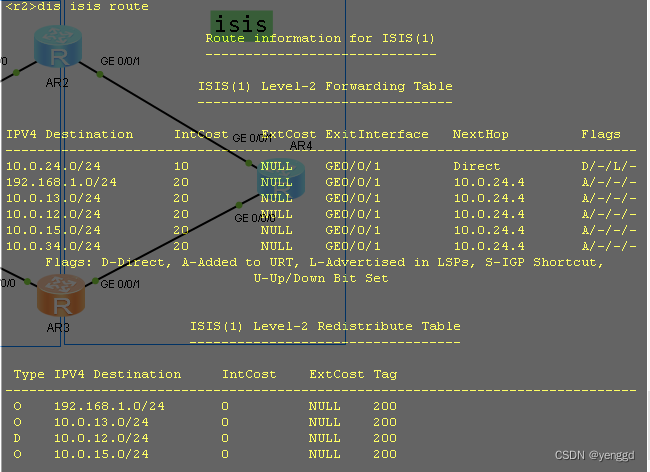
R3上查看:
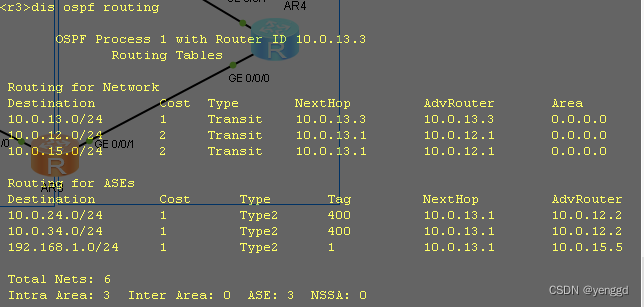
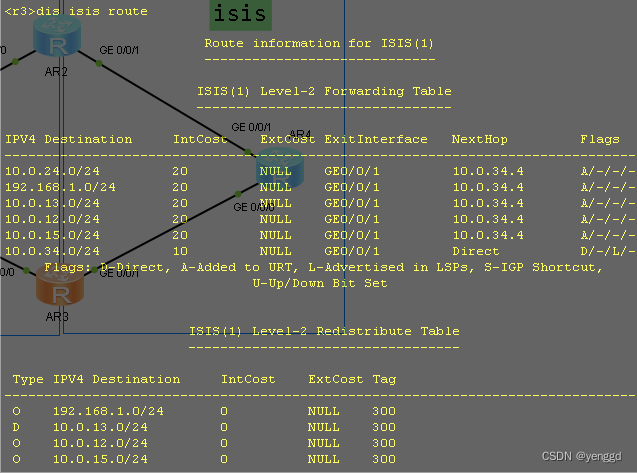
)


)





C++ 用Qt5实现一个工具箱(增加一个进制转换器功能)- 示例代码拆分讲解)









