官方wp:CTFtime.org / Square CTF 2023 tasks and writeups
sandbox
Description:
I “made” “a” “python” “sandbox” “”“”
nc 184.72.87.9 8008
先nc连上看看,只允许一个单词,空格之后的直接无效了。
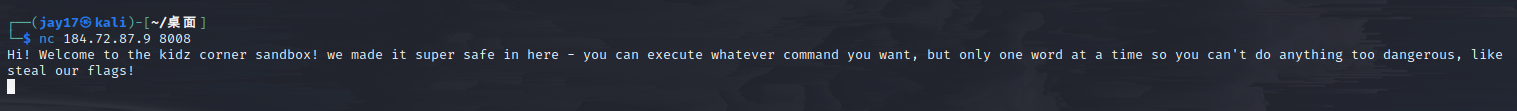
flag就在当前目录下的flag.txt文件中,我们用<来代替空格
cat<flag.txt
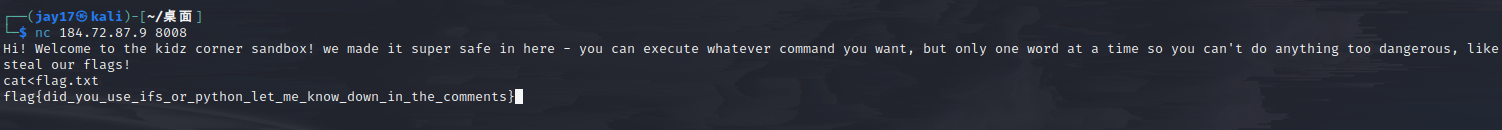
There’s plenty of ways to break the sandbox, the two easiest that come to mind are cat${IFS}flag or python3 -> open(“flag.txt”, “r”).read()
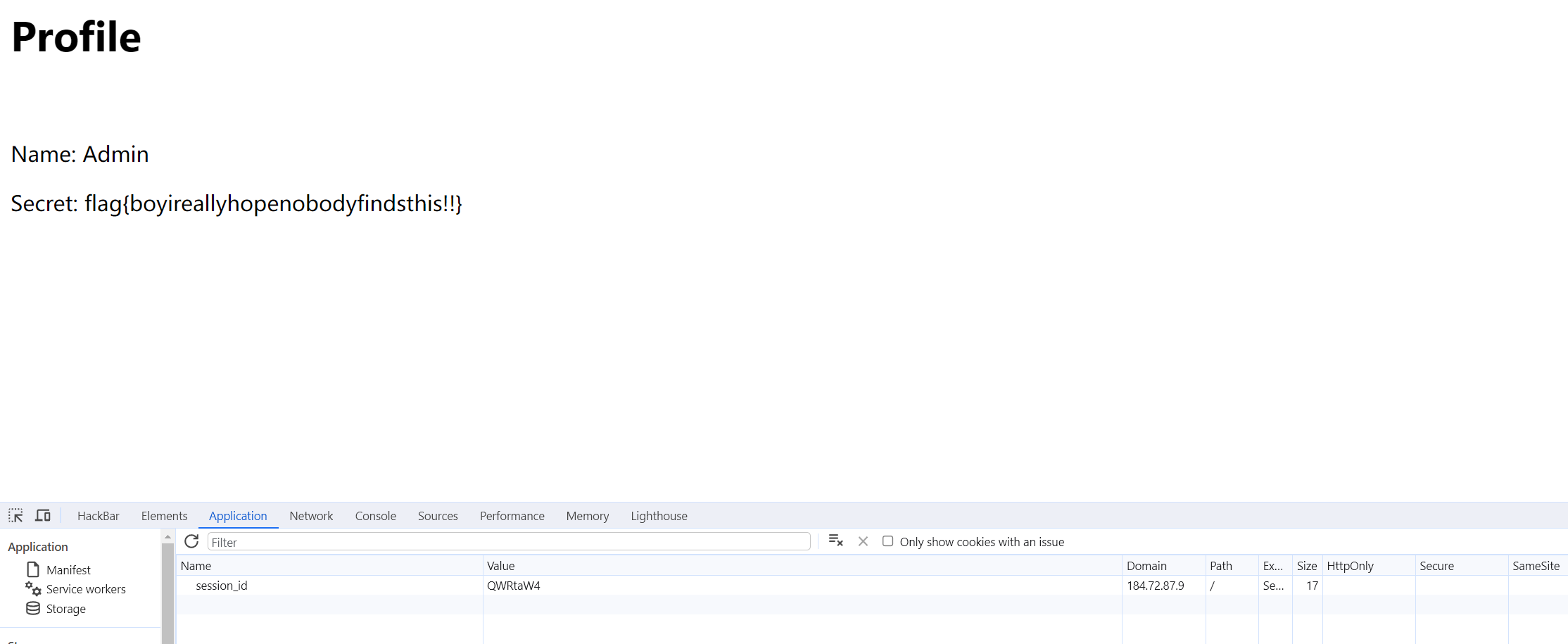
Be The Admin
Description:
This is a very basic website where you can view other user’s profiles, but you can only see your own secret. I’ll bet other users’ secrets have something of interest
用户身份是通过Cookie认证的,Cookie就是用户名的base64编码(暂且认为)
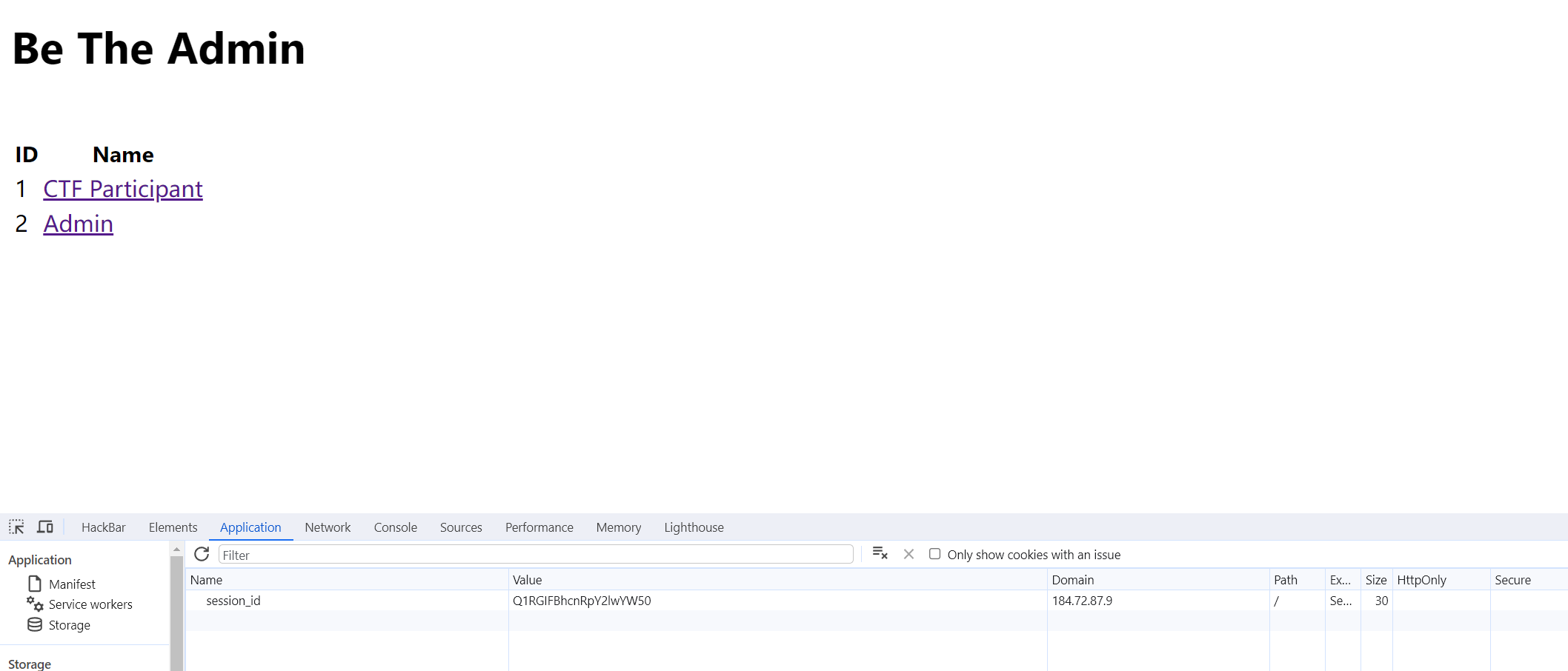
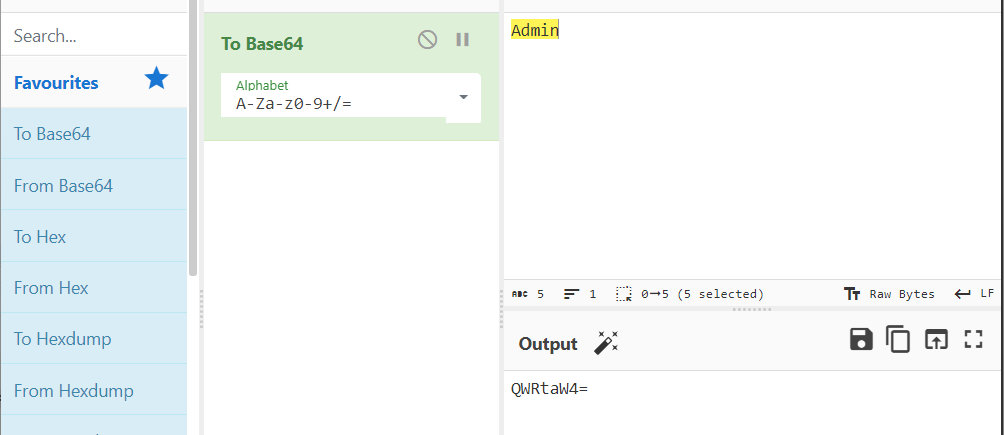
那我们把session改成Admin的base64编码QWRtaW4=就好啦,删掉一个等号,最后是QWRtaW4。为什么要删掉最后一个等号呢?因为出于安全性考虑,在cookie的名或值中不能使用分号(;)、逗号(,)、等号(=)以及空格。而且等号在base64编码中起到补位作用,去掉也不影响解码后的数据。
Just Go Around
Description: This website is a forum where people can make posts, though it’s so broken right now that you can probably only search them. It turns out that someone posted something top secret and later deleted it, but was it truly deleted?
**Hints: ** Have you heard of “soft deletes”?
官方wp:
The index page of the website provides a search feature that performs fuzzy text search, which should indicate that it uses a modern NoSQL DB. There’s also a commented out link to the post page where you can attempt to create a new post, but when you submit the post, you are redirected to another page that says this feature no longer works. However, you can look at the HTTP requests used in that workflow and see that the post is serialized into XML before submitting, which should prompt you to try an XXE attack. Once you get that working, your goal is to use the XXE as an SSRF to query the backend elasticsearch db and get the “deleted” post. You can get the DB host name “db” by guessing/brute forcing or using the XXE for LFI and reading source/config files (or the env file)
翻译后:
网站的索引页提供了一个搜索功能,执行模糊文本搜索,这应该表明它使用了现代NoSQL数据库。还有一个评论链接到帖子页面,在那里你可以尝试创建一个新的帖子,但是当你提交帖子时,你被重定向到另一个页面,上面说这个功能不再有效。但是,您可以查看该工作流中使用的HTTP请求,并看到文章在提交之前被序列化为XML,这应该提示您尝试XXE攻击。一旦您使其工作,您的目标是使用XXE作为SSRF来查询后端elasticsearch数据库并获取“已删除”的帖子。您可以通过猜测/暴力强制或使用LFI的XXE和读取源/配置文件(或env文件)来获得DB主机名“DB”。
一些题2)
)

)



数据库实验(数据库需求分析):音乐软件数据管理系统)




)






