Android native报错有时候只有一句 signal 11 (SIGSEGV),这种情况仅通过log是很难定位到问题的。不过Android 在/data/tombstones目录保存了错误的堆栈信息,为定位bug提供了路径。不过一般这里的log都无法像java一样直接定位的出错的行数。如下图:
--------- beginning of crash
11-21 11:31:40.633 F/libc ( 1127): Fatal signal 11 (SIGSEGV), code 1, fault addr 0xcbb45812 in tid 1260 (RenderThread)
11-21 11:31:40.633 W/ ( 203): debuggerd: handling request: pid=1127 uid=1000 gid=1000 tid=1260
11-21 11:31:40.646 E/JNI_MANAGER( 1127): WebRtcAecm_BufferFarend
11-21 11:31:40.647 E/JNI_MANAGER( 1127): WebRtcAecm_BufferFarend
11-21 11:31:40.731 F/DEBUG ( 2352): *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
11-21 11:31:40.732 F/DEBUG ( 2352): Build fingerprint: 'Android/rk3288/rk3288:7.1.2/NHG47K/zoeyli08041021:userdebug/test-keys'
11-21 11:31:40.732 F/DEBUG ( 2352): Revision: '0'
11-21 11:31:40.733 F/DEBUG ( 2352): ABI: 'arm'
11-21 11:31:40.734 F/DEBUG ( 2352): pid: 1127, tid: 1260, name: RenderThread >>> com.intercom.supervisor <<<
11-21 11:31:40.734 F/DEBUG ( 2352): signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0xcbb45812
11-21 11:31:40.735 F/DEBUG ( 2352): r0 7f1d9fc0 r1 900f4ef8 r2 cbb457f2 r3 01000000
11-21 11:31:40.735 F/DEBUG ( 2352): r4 900f4f20 r5 7ed04880 r6 00000004 r7 00000001
11-21 11:31:40.736 F/DEBUG ( 2352): r8 7ed04830 r9 900f4f60 sl 900f4f20 fp 00000001
11-21 11:31:40.736 F/DEBUG ( 2352): ip a358dba8 sp 900f4ef0 lr a1d558b0 pc a1d5f518 cpsr 20070010
11-21 11:31:40.750 W/AudioFlinger( 234): RecordThread: buffer overflow
11-21 11:31:40.794 F/DEBUG ( 2352):
11-21 11:31:40.794 F/DEBUG ( 2352): backtrace:
11-21 11:31:40.794 F/DEBUG ( 2352): #00 pc 0043e518 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.794 F/DEBUG ( 2352): #01 pc 004348ac /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.794 F/DEBUG ( 2352): #02 pc 00326090 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.794 F/DEBUG ( 2352): #03 pc 00323b1c /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.794 F/DEBUG ( 2352): #04 pc 00447a60 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.794 F/DEBUG ( 2352): #05 pc 00455750 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #06 pc 004503dc /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #07 pc 0044e8b8 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #08 pc 0044f18c /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #09 pc 0044f260 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #10 pc 003ab1ac /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #11 pc 0038664c /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.795 F/DEBUG ( 2352): #12 pc 00695288 /vendor/lib/egl/libGLES_mali.so
11-21 11:31:40.796 F/DEBUG ( 2352): #13 pc 0069e3bc /vendor/lib/egl/libGLES_mali.so (eglMakeCurrent+1488)
11-21 11:31:40.796 F/DEBUG ( 2352): #14 pc 0000ac41 /system/lib/libEGL.so (_ZN7android13egl_display_t11makeCurrentEPNS_13egl_context_tES2_PvS3_S3_S3_S3_S3_+192)
11-21 11:31:40.796 F/DEBUG ( 2352): #15 pc 0000d497 /system/lib/libEGL.so (eglMakeCurrent+290)
11-21 11:31:40.796 F/DEBUG ( 2352): #16 pc 000263e9 /system/lib/libhwui.so
11-21 11:31:40.796 F/DEBUG ( 2352): #17 pc 0002667d /system/lib/libhwui.so
11-21 11:31:40.796 F/DEBUG ( 2352): #18 pc 0002344b /system/lib/libhwui.so
11-21 11:31:40.796 F/DEBUG ( 2352): #19 pc 00023339 /system/lib/libhwui.so
11-21 11:31:40.796 F/DEBUG ( 2352): #20 pc 000272e5 /system/lib/libhwui.so
11-21 11:31:40.797 F/DEBUG ( 2352): #21 pc 00028117 /system/lib/libhwui.so
11-21 11:31:40.797 F/DEBUG ( 2352): #22 pc 00028857 /system/lib/libhwui.so
11-21 11:31:40.797 F/DEBUG ( 2352): #23 pc 00029139 /system/lib/libhwui.so (_ZN7android10uirenderer12renderthread12RenderThread10threadLoopEv+80)
11-21 11:31:40.797 F/DEBUG ( 2352): #24 pc 0000e325 /system/lib/libutils.so (_ZN7android6Thread11_threadLoopEPv+144)
11-21 11:31:40.797 F/DEBUG ( 2352): #25 pc 00067f29 /system/lib/libandroid_runtime.so (_ZN7android14AndroidRuntime15javaThreadShellEPv+80)
11-21 11:31:40.797 F/DEBUG ( 2352): #26 pc 00047323 /system/lib/libc.so (_ZL15__pthread_startPv+22)
11-21 11:31:40.797 F/DEBUG ( 2352): #27 pc 00019e5d /system/lib/libc.so (__start_thread+6)
11-21 11:31:41.277 I/AudioFlinger( 234): BUFFER TIMEOUT: remove(4098) from active list on thread 0xad983d00
11-21 11:31:41.742 E/ ( 2352): debuggerd: failed to kill process 1127: No such process
11-21 11:31:41.748 W/ ( 203): debuggerd: resuming target 1127
11-21 11:31:41.750 I/BootReceiver( 485): Copying /data/tombstones/tombstone_05 to DropBox (SYSTEM_TOMBSTONE)
- 先看崩溃的tid:1260,不是主线程,说明是子线程。
- 最后一行/data/tombstones/tombstone_05提示异常日志保存在了tombstone_05文件里面
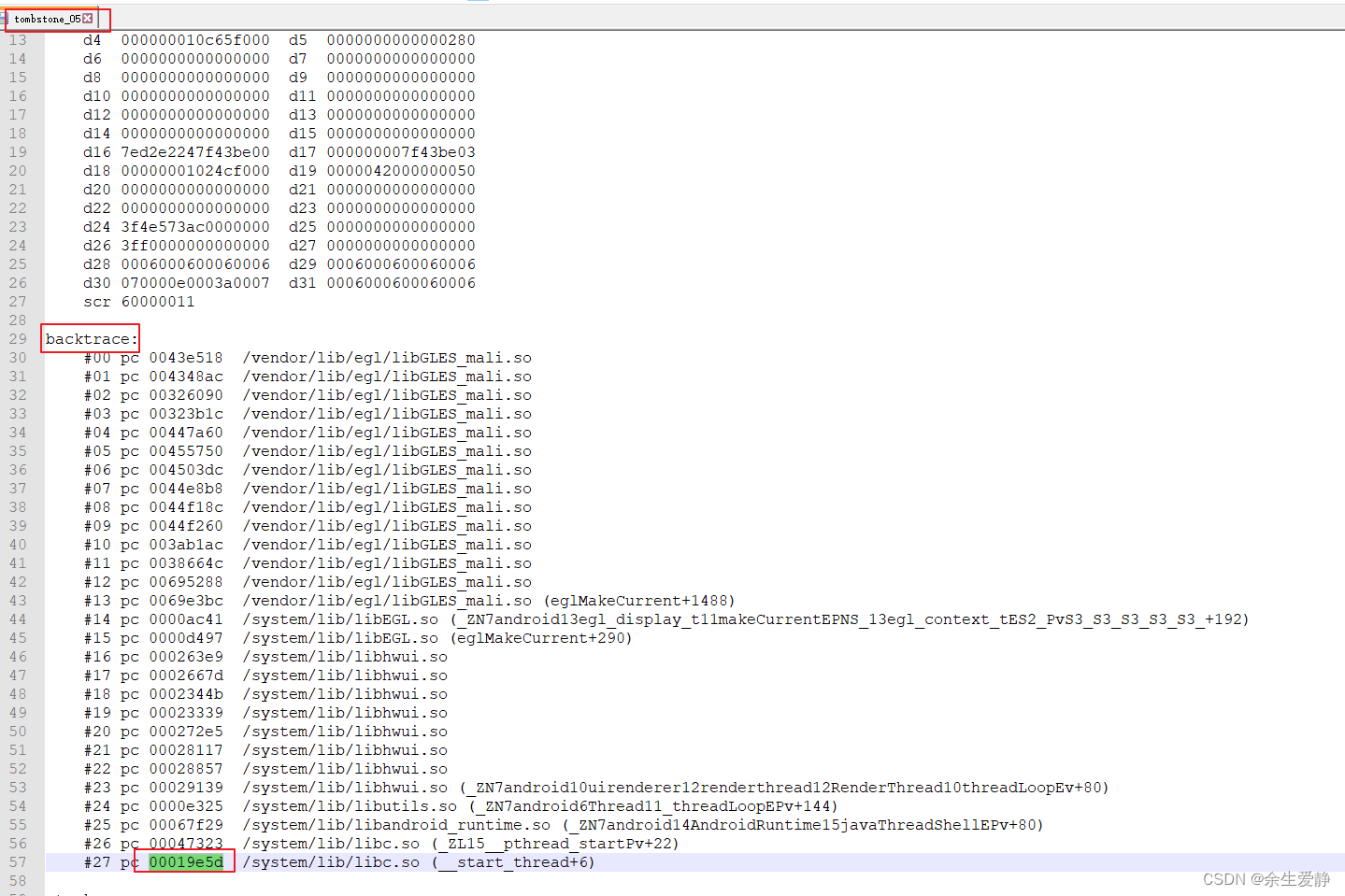
backtrace需要借助Android ndk提供的addr2line工具来分析,从工具的名字就能看出来,这个东西可以帮我们把报错的地址指向代码行,以协助我们排查问题。
看工具的使用方式:
1.找到本地ndk路径下的addr2line的程序
我的路径“D:\Android\ndk\android-ndk-r10e\toolchains\aarch64-linux-android-4.9\prebuilt\windows-x86_64\bin”
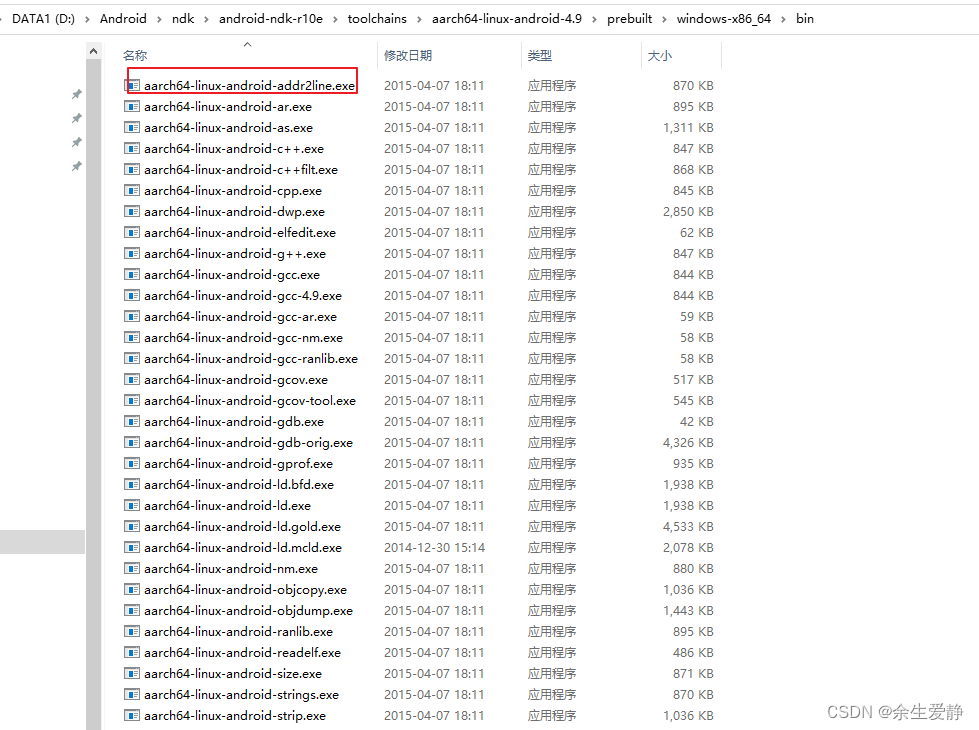
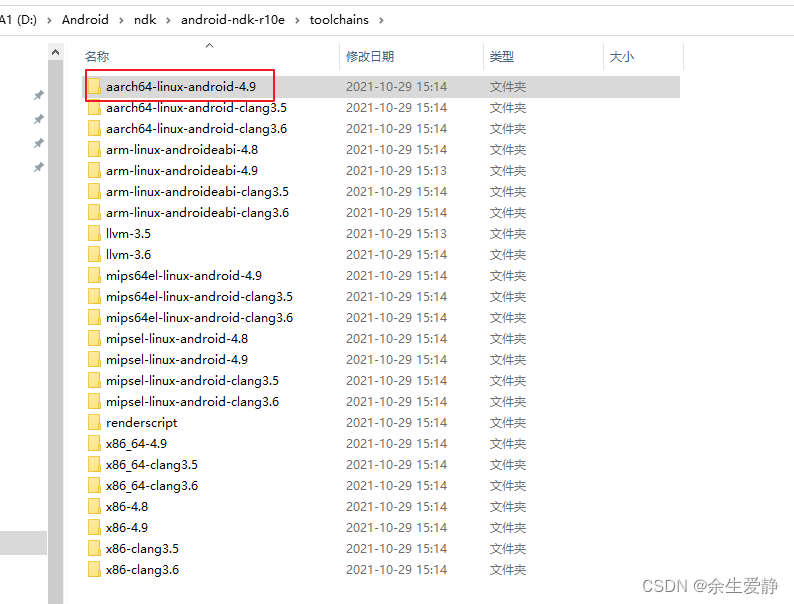
这里需要注意toolchains下根据系统架构区分多个目录,需要根据自己运行的系统进行区分,否则会报File format not recognized 错误。我的是64位系统,所以选了图示目录
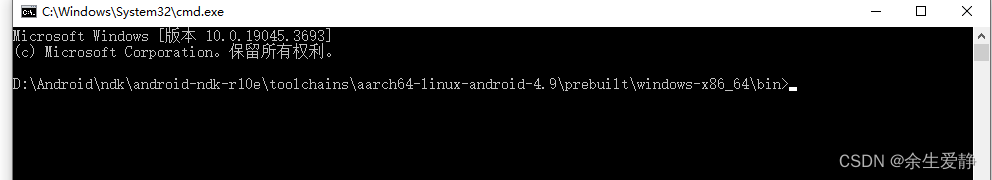
2.打开命令行跳转至该目录
2.1、直接在路径下输入cmd,然后按enter键,就可以直接打开命令行窗口,并且跳转到该路径下面

3.使用addr2line -e命令
aarch64-linux-android-addr2line -e D:\Android\AndroidStudio\Project\ManagerJni\obj\local\armeabi\intercomManager.so 00019e5d
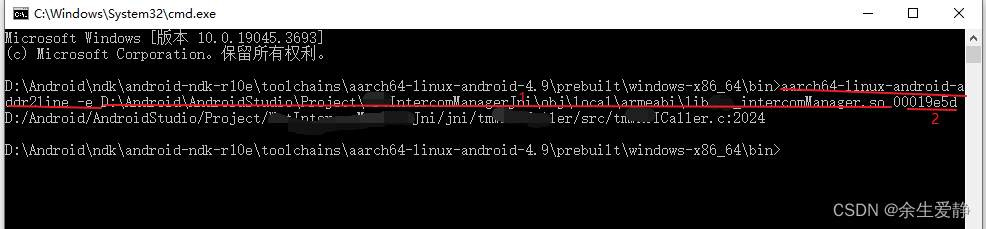
- 红色1、so库必须是带有符号表的
- 红色2、为异常的地址
- 最后一行就转换出了异常所在的行



)


 第十一章: 软件编程课后习题及其答案解析)
或者数组(Array))
)










