MDH
源题:
from hashlib import sha256
from secret import flagr = 128
c = 96
p = 308955606868885551120230861462612873078105583047156930179459717798715109629
Fp = GF(p)def gen():a1 = random_matrix(Fp, r, c)a2 = random_matrix(Fp, r, c)A = a1 * a2.Treturn (a1, a2), Ask_alice, pk_alice = gen()
sk_bob, pk_bob = gen()
shared = (sk_alice[0].T * pk_bob * sk_alice[1]).trace()
ct = int(sha256(str(int(shared)).encode()).hexdigest(), 16) ^^ int.from_bytes(flag, 'big')with open('output.txt', 'wb') as f:f.write(str(ct).encode() + b'\n')f.write(str(list(pk_alice)).encode() + b'\n')f.write(str(list(pk_bob)).encode() + b'\n')
思路:本题思路很简单,高等代数,sk_alice[0].T * pk_bob * sk_alice[1]和pk_bob*pk_alice.T的迹的大小是相等的。
exp:
from hashlib import sha256
from Crypto.Util.number import*r = 128
c = 96
p = 308955606868885551120230861462612873078105583047156930179459717798715109629
Fp = GF(p)f = open('output.txt','r')
ct = eval(f.readline())
a1 = eval(f.readline())
a2 = eval(f.readline())pk_alice = matrix(Fp,a1)
pk_bob = matrix(Fp,a2)
# print(pk_alice)
# print(pk_bob)
shared = (pk_bob*pk_alice.T).trace()
m = int(sha256(str(int(shared)).encode()).hexdigest(), 16) ^^ ct
print(long_to_bytes(m))claw crane
源码:
!/usr/bin/env python3
from Crypto.Util.number import (bytes_to_long, long_to_bytes
)
from hashlib import md5
import os, signal
import sys
import randomBITS = 128class ClawCrane(object):def __init__(self) -> None:self.seed = bytes_to_long(os.urandom(BITS//8))self.bless = 0self.score = 0def get_input(self, prompt="> "):print(prompt, end="")sys.stdout.flush()return input()def check_pos(self, pos, moves):col, row = 0, 0for move in moves:if move == "W":if row < 15: row += 1elif move == "S":if row > 0: row -= 1elif move == "A":if col > 0: col -= 1elif move == "D":if col < 15: col += 1else:return -1print(col, row)return pos == [col, row]def gen_chaos(self, inp):def mapping(x):if x=='W': return "0"if x=='S': return "1"if x=='A': return "2"if x=='D': return "3"vs = int("".join(map(mapping, inp)), 4)chaos = bytes_to_long(md5(long_to_bytes((self.seed + vs) % pow(2,BITS))).digest())self.seed = (self.seed + chaos + 1) % pow(2,BITS)return chaosdef destiny_claw(self, delta):bits = bin(delta)[2:]if len(bits) < 128+self.bless:bits += "0"*(128+self.bless - len(bits))c = random.choice(bits)if c=='0': return Trueelse: return Falsedef run(self):pos = [random.randrange(1,16), random.randrange(1,16)]moves = self.get_input(f"i am at {pos}, claw me.\nYour moves: ")if len(moves) > 100:print("too many steps")returnif not self.check_pos(pos, moves):print("sorry, clawed nothing")returnr = self.gen_chaos(moves[:64])print(f"choas: {r}")p, q = map(int, self.get_input(f"give me your claw using p,q and p,q in [0, 18446744073709551615] (e.g.: 1,1): ").split(","))if not (p>0 and p<pow(2,BITS//2) and q>0 and q<pow(2,BITS//2)):print("not in range")returndelta = abs(r*q - p*pow(2,BITS))if self.destiny_claw(delta):self.score += 10self.bless = 0print("you clawed it")else:self.bless += 16print("sorry, clawed nothing")def main():signal.alarm(600)cc = ClawCrane()for _ in range(256):try:cc.run()print(f"your score: {cc.score}")except:print(f"abort")breakif cc.score >= 2220:print(f"flag: {open('/flag.txt').read()}")if __name__ == "__main__":main()思路:在本题目中我们需要绕过proof验证、check_pos的位置验证和以下
chaos = bytes_to_long(md5(long_to_bytes((self.seed + vs) % pow(2,BITS))).digest()) self.seed = (self.seed + chaos + 1) % pow(2,BITS)
首先:
proof验证:我们知道是将十六进制数输入,进行sha1操作与已知输出对比,相同即可通过,我们在输入的十六进制数的前六位未知,直接爆破即可。
check_pos的位置验证:我们观察源码,源码是通过构造的输入序列(‘A’,'B','C','D'),对此时在(0,0)的点进行位移输入到随机确认的pos位置上,若最终移动的位置相同,即可通过。
由于 r = self.gen_chaos(moves[:64]),moves是我们自己输入的,此时函数仅仅需要前64位进行运算获得r的值,我们需要固定r的值的大小,所以此时便在seed上做文章,令每次输入的vs都在上一个vs的基础上减去(chaos + 1),此时,输出的chaos值固定。
于是,check_pos的位置验证中,我们输入序列的前64位由上述r取值中确认,我们需要计算出64次移动后的位置,再寻找到pos点的移动所需里程。
完成上述操作后,开始运算,当cc.score >= 2220时,我们即可得到flag的值
exp:
import itertools
from Crypto.Util.number import *
from hashlib import md5
import gmpy2
from pwn import *
from tqdm import tqdm
from hashlib import *
from time import *BITS = 128def proof():sh.recvuntil(b'sha1(prefix+"')k = sh.recvuntil(b'"')[:-1]sh.recvuntil(b')==')cc = sh.recvuntil(b'\n')[:-1]sh.recvuntil(b'prefix = ?\n')String = b'0123456789abcdef'# print(k,cc)start = time()for i1, i2, i3, i4, i5, i6 in tqdm(itertools.product(String, String, String, String, String, String)):kk = str(chr(i1)) + str(chr(i2)) + str(chr(i3)) + str(chr(i4)) + str(chr(i5)) + str(chr(i6)) + k.decode()# print(kk,k.decode())# print(sha1(kk.encode()).hexdigest(),cc.decode())if sha1(kk.encode()).hexdigest() == cc.decode():print(kk[:6])sh.sendline(kk[:6].encode())breakend = time()print(f"consume {end - start} time")def check_pos(pos, moves):col, row = int(pos[0]), int(pos[1])for move in moves:if move == "W":if row < 15: row += 1elif move == "S":if row > 0: row -= 1elif move == "A":if col > 0: col -= 1elif move == "D":if col < 15: col += 1else:return -1print(col, row)return [col, row]def solve_chaos(la_chaos, idx):def mapping(x):if x == '0': return "W"if x == '1': return "S"if x == '2': return "A"if x == '3': return "D"New_vs = (-la_chaos - 1) * (idx - 1) % (2 ^ 128)target = New_vs % 4new_vs = ''while New_vs:if target == 0:new_vs += 'W'New_vs = New_vs // 4if target == 1:new_vs += 'S'New_vs = New_vs // 4if target == 2:new_vs += 'A'New_vs = New_vs // 4if target == 3:new_vs += 'D'New_vs = New_vs // 4target = New_vs % 4# print(new_vs)new_vs = new_vs[::-1]if len(new_vs) != 64:new_vs = mapping("0") * (64 - len(new_vs)) + new_vsprint('solve_chaos:', new_vs)return new_vsdef solve_pos(cu_pos, new_pos, sol):x0, y0 = cu_posx1, y1 = new_posif x0 < x1:sol += 'D' * ((x1 - x0) % 16)else:sol += 'A' * ((x0 - x1) % 16)if y0 < y1:sol += 'W' * ((y1 - y0) % 16)else:sol += 'S' * ((y0 - y1) % 16)return soldef solve_pq(chaos):K = matrix(ZZ, [[2 ^ 128, 0], [chaos, 1]])KK = K.LLL()# print(num)v = K.solve_left(KK[0])p, q = v[0], v[1]return abs(p), abs(q)for i in range(1, 10000):print(f'Try {i} times')sh = process(['python3', 'server.py'])proof()Assert, chaos, idx, failure, success = 0, -1, 0, 0, 0p, q = 0, 0try:while idx < 256:idx += 1print(f'----------The {idx} quarters---------')sh.recvuntil(b'i am at ')pos = eval(sh.recvuntil(b']'))sh.recvuntil(b'Your moves: ')x1, y1 = int(pos[0]), int(pos[1])# print(pos,x1,y1,chaos)vs = solve_chaos(chaos, idx)# print(vs)x0, y0 = check_pos((0, 0), vs)moves = solve_pos((x0, y0), (x1, y1), vs)sh.sendline(moves.encode())sh.recvuntil(b'choas: ')chaos = int(sh.recvuntil(b'\n')[:-1])if not p and not q:p, q = solve_pq(chaos)x = abs(chaos * q - p * pow(2, 128))print(bin(x)[2:].count('1'))print(bin(x)[2:])if bin(x)[2:].count('1') > 23:breakprint(abs(chaos * q - p * pow(2, 128)))sh.recvuntil(b'give me your claw using p,q and p,q in [0, 18446744073709551615] (e.g.: 1,1): ')sh.sendline(f'{p},{q}'.encode())ding = sh.recvline()# print(ding)sh.recvuntil(b'your score: ')score = sh.recvuntil(b'\n')[:-1]print('Your score: ', score)sh.interactive()except:continueEazyRSA
源码:
from secret import flag
from Crypto.Util.number import *def genKey(nbits, dbits):bbits = (nbits // 2 - dbits) // 2while True:a = getRandomNBitInteger(dbits)b = getRandomNBitInteger(bbits)c = getRandomNBitInteger(bbits)p1 = a * b * c + 1if isPrime(p1):# print("p1 =", p1)breakwhile True:d = getRandomNBitInteger(dbits)p2 = b * c * d + 1if isPrime(p2):# print("p2 =", p2)breakwhile True:e = getRandomNBitInteger(bbits)f = getRandomNBitInteger(bbits)q1 = e * d * f + 1p3 = a * e * f + 1if isPrime(q1) and isPrime(p3):# print("p3 =", p3)# print("q1 =", q1)breakwhile True:d_ = getRandomNBitInteger(dbits)if GCD(a * b * c * d * e * f, d_) != 1:continuee_ = inverse(d_, a * b * c * d * e * f)k1 = (e_ * d_ - 1) // (a * b * c * d * e * f)assert e_ * d_ == (a * b * c * d * e * f) * k1 + 1q2 = k1 * e * f + 1q3 = k1 * b * c + 1if isPrime(q2) and isPrime(q3):# print("q2 =", q2)# print("q3 =", q3)# print("e =", e_)# print("d =", d_)breakn1 = p1 * q1n2 = p2 * q2n3 = p3 * q3assert pow(pow(0xdeadbeef, e_, n1), d_, n1) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n2), d_, n2) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n3), d_, n3) == 0xdeadbeefreturn(e_, n1, n2, n3)nbits = 0x600
dbits = 0x210m = bytes_to_long(flag)
e, n1, n2, n3 = genKey(nbits, dbits)
c = pow(m, e, n1)print("c =", c)
print("e =", e)
print("n1 =", n1)
print("n2 =", n2)
print("n3 =", n3)# c = 63442255298812942222810837512019302954917822996915527697525497640413662503768308023517128481053593562877494934841788054865410798751447333551319775025362132176942795107214528962480350398519459474033659025815248579631003928932688495682277210240277909527931445899728273182691941548330126199931886748296031014210795428593631253184315074234352536885430181103986084755140024577780815130067722355861473639612699372152970688687877075365330095265612016350599320999156644
# e = 272785315258275494478303901715994595013215169713087273945370833673873860340153367010424559026764907254821416435761617347240970711252213646287464416524071944646705551816941437389777294159359383356817408302841561284559712640940354294840597133394851851877857751302209309529938795265777557840238332937938235024502686737802184255165075195042860413556866222562167425361146312096189555572705076252573222261842045286782816083933952875990572937346408235562417656218440227
# n1 = 473173031410877037287927970398347001343136400938581274026578368211539730987889738033351265663756061524526288423355193643110804217683860550767181983527932872361546531994961481442866335447011683462904976896894011884907968495626837219900141842587071512040734664898328709989285205714628355052565784162841441867556282849760230635164284802614010844226671736675222842060257156860013384955769045790763119616939897544697150710631300004180868397245728064351907334273953201
# n2 = 327163771871802208683424470007561712270872666244394076667663345333853591836596054597471607916850284565474732679392694515656845653581599800514388800663813830528483334021178531162556250468743461443904645773493383915711571062775922446922917130005772040139744330987272549252540089872170217864935146429898458644025927741607569303966038195226388964722300472005107075179204987774627759625183739199425329481632596633992804636690274844290983438078815836605603147141262181
# n3 = 442893163857502334109676162774199722362644200933618691728267162172376730137502879609506615568680508257973678725536472848428042122350184530077765734033425406055810373669798840851851090476687785235612051747082232947418290952863499263547598032467577778461061567081620676910480684540883879257518083587862219344609851852177109722186714811329766477552794034774928983660538381764930765795290189612024799300768559485810526074992569676241537503405494203262336327709010421
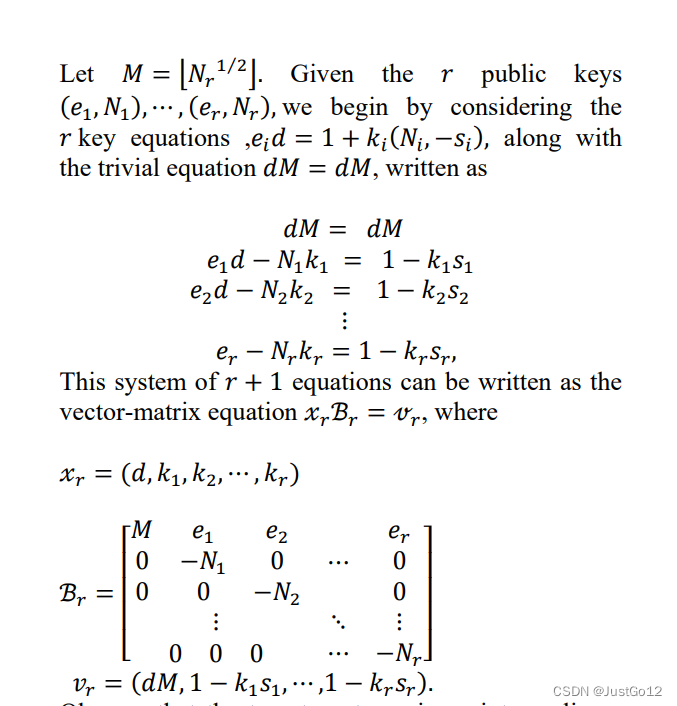
思路:造格即可
exp:
from sage.all import *
from Crypto.Util.number import *
import randomc = 63442255298812942222810837512019302954917822996915527697525497640413662503768308023517128481053593562877494934841788054865410798751447333551319775025362132176942795107214528962480350398519459474033659025815248579631003928932688495682277210240277909527931445899728273182691941548330126199931886748296031014210795428593631253184315074234352536885430181103986084755140024577780815130067722355861473639612699372152970688687877075365330095265612016350599320999156644
e = 272785315258275494478303901715994595013215169713087273945370833673873860340153367010424559026764907254821416435761617347240970711252213646287464416524071944646705551816941437389777294159359383356817408302841561284559712640940354294840597133394851851877857751302209309529938795265777557840238332937938235024502686737802184255165075195042860413556866222562167425361146312096189555572705076252573222261842045286782816083933952875990572937346408235562417656218440227
n1 = 473173031410877037287927970398347001343136400938581274026578368211539730987889738033351265663756061524526288423355193643110804217683860550767181983527932872361546531994961481442866335447011683462904976896894011884907968495626837219900141842587071512040734664898328709989285205714628355052565784162841441867556282849760230635164284802614010844226671736675222842060257156860013384955769045790763119616939897544697150710631300004180868397245728064351907334273953201
n2 = 327163771871802208683424470007561712270872666244394076667663345333853591836596054597471607916850284565474732679392694515656845653581599800514388800663813830528483334021178531162556250468743461443904645773493383915711571062775922446922917130005772040139744330987272549252540089872170217864935146429898458644025927741607569303966038195226388964722300472005107075179204987774627759625183739199425329481632596633992804636690274844290983438078815836605603147141262181
n3 = 442893163857502334109676162774199722362644200933618691728267162172376730137502879609506615568680508257973678725536472848428042122350184530077765734033425406055810373669798840851851090476687785235612051747082232947418290952863499263547598032467577778461061567081620676910480684540883879257518083587862219344609851852177109722186714811329766477552794034774928983660538381764930765795290189612024799300768559485810526074992569676241537503405494203262336327709010421M = int(random.randint(n1,2*n2) ** 0.5)
K = matrix([[M,e,e,e],[0,-n1,0,0],[0,0,-n2,0],[0,0,0,-n3]])
KK = K.LLL()
d = int(KK[0][0]/M)
m = pow(c,d,n1)
print(long_to_bytes(int(m)))MidRSA
源码:
from secret import flag
from Crypto.Util.number import *def genKey(nbits, dbits):bbits = (nbits // 2 - dbits) // 2while True:a = getRandomNBitInteger(dbits)b = getRandomNBitInteger(bbits)c = getRandomNBitInteger(bbits)p1 = a * b * c + 1if isPrime(p1):# print("p1 =", p1)breakwhile True:d = getRandomNBitInteger(dbits)p2 = b * c * d + 1if isPrime(p2):# print("p2 =", p2)breakwhile True:e = getRandomNBitInteger(bbits)f = getRandomNBitInteger(bbits)q1 = e * d * f + 1p3 = a * e * f + 1if isPrime(q1) and isPrime(p3):# print("p3 =", p3)# print("q1 =", q1)breakwhile True:d_ = getRandomNBitInteger(dbits)if GCD(a * b * c * d * e * f, d_) != 1:continuee_ = inverse(d_, a * b * c * d * e * f)k1 = (e_ * d_ - 1) // (a * b * c * d * e * f)assert e_ * d_ == (a * b * c * d * e * f) * k1 + 1q2 = k1 * e * f + 1q3 = k1 * b * c + 1if isPrime(q2) and isPrime(q3):# print("q2 =", q2)# print("q3 =", q3)# print("e =", e_)print("d =", d_)breakn1 = p1 * q1n2 = p2 * q2n3 = p3 * q3assert pow(pow(0xdeadbeef, e_, n1), d_, n1) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n2), d_, n2) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n3), d_, n3) == 0xdeadbeefreturn(e_, n1, n2, n3)nbits = 0x600
dbits = 0x240m = bytes_to_long(flag)
e, n1, n2, n3 = genKey(nbits, dbits)
c = pow(m, e, n1)print("c =", c)
print("e =", e)
print("n1 =", n1)
print("n2 =", n2)
print("n3 =", n3)# c = 598823083137858565473505718525815255620672892612784824187302545127574115000325539999824374357957135208478070797113625659118825530731575573239221853507638809719397849963861367352055486212696958923800593172417262351719477530809870735637329898331854130533160020420263724619225174940214193740379571953951059401685115164634005411478583529751890781498407518739069969017597521632392997743956791839564573371955246955738575593780508817401390102856295102225132502636316844
# e = 334726528702628887205076146544909357751287869200972341824248480332256143541098971600873722567713812425364296038771650383962046800505086167635487091757206238206029361844181642521606953049529231154613145553220809927001722518303114599682529196697410089598230645579658906203453435640824934159645602447676974027474924465177723434855318446073578465621382859962701578350462059764095163424218813852195709023435581237538699769359084386399099644884006684995755938605201771
# n1 = 621786427956510577894657745225233425730501124908354697121702414978035232119311662357181409283130180887720760732555757426221953950475736078765267856308595870951635246720750862259255389006679454647170476427262240270915881126875224574474706572728931213060252787326765271752969318854360970801540289807965575654629288558728966771231501959974533484678236051025940684114262451777094234017210230731492336480895879764397821363102224085859281971513276968559080593778873231
# n2 = 335133378611627373902246132362791381335635839627660359611198202073307340179794138179041524058800936207811546752188713855950891460382258433727589232119735602364790267515558352318957355100518427499530387075144776790492766973547088838586041648900788325902589777445641895775357091753360428198189998860317775077739054298868885308909495601041757108114540069950359802851809227248145281594107487276003206931533768902437356652676341735882783415106786497390475670647453821
# n3 = 220290953009399899705676642623181513318918775662713704923101352853965768389363281894663344270979715555659079125651553079702318700200824118622766698792556506368153467944348604006011828780474050012010677204862020009069971864222175380878120025727369117819196954091417740367068284457817961773989542151049465711430065838517386380261817772422927774945414543880659243592749932727798690742051285364898081188510009069286094647222933710799481899960520270189522155672272451
思路:相比于EazyRSA题目,提高了dbits的比特数,使得无法计算,此时我们需要爆破一定的高位即可。
exp:
from sage.all import *
from Crypto.Util.number import *
import random
from tqdm import tqdmc = 598823083137858565473505718525815255620672892612784824187302545127574115000325539999824374357957135208478070797113625659118825530731575573239221853507638809719397849963861367352055486212696958923800593172417262351719477530809870735637329898331854130533160020420263724619225174940214193740379571953951059401685115164634005411478583529751890781498407518739069969017597521632392997743956791839564573371955246955738575593780508817401390102856295102225132502636316844
e = 334726528702628887205076146544909357751287869200972341824248480332256143541098971600873722567713812425364296038771650383962046800505086167635487091757206238206029361844181642521606953049529231154613145553220809927001722518303114599682529196697410089598230645579658906203453435640824934159645602447676974027474924465177723434855318446073578465621382859962701578350462059764095163424218813852195709023435581237538699769359084386399099644884006684995755938605201771
n1 = 621786427956510577894657745225233425730501124908354697121702414978035232119311662357181409283130180887720760732555757426221953950475736078765267856308595870951635246720750862259255389006679454647170476427262240270915881126875224574474706572728931213060252787326765271752969318854360970801540289807965575654629288558728966771231501959974533484678236051025940684114262451777094234017210230731492336480895879764397821363102224085859281971513276968559080593778873231
n2 = 335133378611627373902246132362791381335635839627660359611198202073307340179794138179041524058800936207811546752188713855950891460382258433727589232119735602364790267515558352318957355100518427499530387075144776790492766973547088838586041648900788325902589777445641895775357091753360428198189998860317775077739054298868885308909495601041757108114540069950359802851809227248145281594107487276003206931533768902437356652676341735882783415106786497390475670647453821
n3 = 220290953009399899705676642623181513318918775662713704923101352853965768389363281894663344270979715555659079125651553079702318700200824118622766698792556506368153467944348604006011828780474050012010677204862020009069971864222175380878120025727369117819196954091417740367068284457817961773989542151049465711430065838517386380261817772422927774945414543880659243592749932727798690742051285364898081188510009069286094647222933710799481899960520270189522155672272451for i in tqdm(range(70000,2^20)):t1 = bin(i)[2:].zfill(21)h = int('1'+t1[:3],2) << 0x23ch1 = int(t1[3:9],2) << 1338h2 = int(t1[9:15],2) << 1338h3 = int(t1[15:21],2) << 1338M = Matrix(QQ,[[-e,-e,-e,2^766,0,0,0,0],[n1,0,0,0,0,0,0,0],[0,n2,0,0,0,0,0,0],[0,0,n3,0,0,0,0,0],[-h*e,-h*e,-h*e,0,2^(1338),0,0,0],[-h1,0,0,0,0,2^1338,0,0],[0,-h2,0,0,0,0,2^1338,0],[0,0,-h3,0,0,0,0,2^1338]])
# e_*d_-k1*n1,n1res = M.LLL()d = int(res[0][3]//2^766) + hif b'ACTF' in long_to_bytes(ZZ(pow(c,d,n1))):print(long_to_bytes(ZZ(pow(c,d,n1))))


![[Machine Learning][Part 7]神经网络的基本组成结构](http://pic.xiahunao.cn/[Machine Learning][Part 7]神经网络的基本组成结构)
:EcShop添加商品功能)



)



相机与图像实践:OpenCV处理图像与图像拼接(点云))





)

