requestedExecutionLevel level="asInvoker" uiAccess="false" 可以修改这一行来启用禁用原程序的盾牌图标,似乎作用不大。以前没事写的一个小玩意,记录一下。
等同于这里的设置:
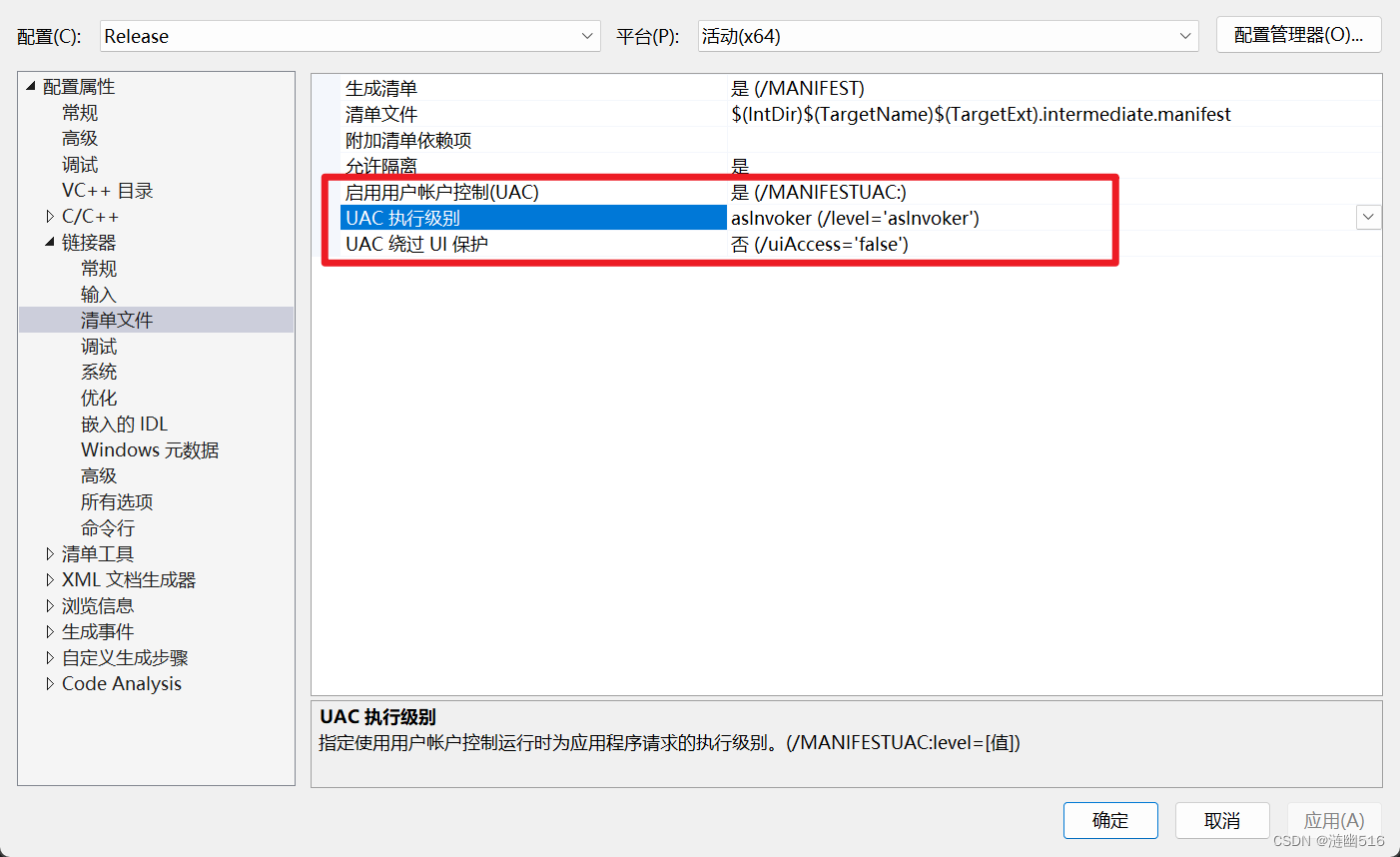
代码如下:
#include <iostream>
#include <Windows.h>
#include <iomanip>
#include <fstream>
#include<cstdlib>
#include<string>using namespace std;char HEX[16] = { '0','1','2','3','4','5','6','7','8','9','A','B','C','D','E','F' };
void setIndex(int num, char* hexNumber)
{// 清空行下标for (int i = 0; i < 8; i++) {hexNumber[i] = '0';}// 设置新的行下标int index = 7;while (num != 0 && index >= 0){hexNumber[index--] = HEX[num % 16];num = num / 16;}
}int codeArr_kipetl_102[] = {0x72, 0x65, 0x71, 0x75, 0x65, 0x73, 0x74, 0x65, 0x64, 0x45, 0x78, 0x65, 0x63, 0x75, 0x74, 0x69, 0x6F, 0x6E, 0x4C, 0x65, 0x76, 0x65, 0x6C// requestedExecutionLevel
};
int codeCtrl_kipetl_102[] = {1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1
};int inline get_PE_feature_rof(string path_r, // PE 文件全路径。我这里是:"C:\\Windows\\SysNative\\ntoskrnl.exe"int codeArr[], // 上面提到的第一个数组int codeCtrl[], // 上面提到的第二个数组int len // 数组的长度
) {// 打开文件ifstream in = ifstream(path_r, ios::binary);if (!in.is_open()) {cout << "文件打开失败:" << GetLastError() << endl;in.close();return 0;}// 获取文件大小、文件名long long Beg = in.tellg();in.seekg(0, ios::end);long long End = in.tellg();long long fileSize = End - Beg;in.seekg(0, ios::beg);// 读文件(每次循环读取 1 字节)int byteBeenRead = 0; // 已经读取的字节数unsigned char temp; // 存放读取内容的缓冲区 int rof_feature = 0; // 特征 ROFint codeArrSub = 0; // 要对比的 codeArr[] 下标BOOL isFound = FALSE; // 是否找到特征while (in.read((char*)&temp, 1) && isFound == FALSE) {byteBeenRead++;// 读 1 字节int hex = (unsigned)temp;// 比较特征for (int i = 0; i < len; i++) {// 需要匹配if (codeCtrl[codeArrSub] == 1) {// 匹配到特征if (hex == codeArr[codeArrSub]) {codeArrSub++;// 匹配完成if (codeArrSub == len) {rof_feature = byteBeenRead - len;isFound = TRUE;break;}else { break; }}else { codeArrSub = 0; break; }}else { codeArrSub++; break; }}}//cout << "rof_feature = " << hex << rof_feature << endl;in.close();return rof_feature;
}int main(int argc, char* argv[])
{// 打开文件string path_r = "CGnetsw.exe";//根据特征码定位UIAccess属性位置int ROF = get_PE_feature_rof(path_r, codeArr_kipetl_102, codeCtrl_kipetl_102, 23);cout << ROF << endl;fstream fs("XXXX.exe", ios::binary | ios::out | ios::in);//跳转到ROF位置进行写入,写入新的UIAccess属性。从而去除启动权限fs.seekp(ROF, ios::beg);//requestedExecutionLevel level="asInvoker" uiAccess="false"/>//0D 0A 换行//11个空格(0x20)fs.write("\x72\x65\x71\x75\x65\x73\x74\x65\x64\x45\x78\x65", 12);fs.write("\x63\x75\x74\x69\x6F\x6E\x4C\x65\x76\x65\x6C\x20", 12);fs.write("\x6C\x65\x76\x65\x6C\x3D\x22\x61\x73\x49\x6E\x76", 12);fs.write("\x6F\x6B\x65\x72\x22\x20\x75\x69\x41\x63\x63\x65", 12);fs.write("\x73\x73\x3D\x22\x66\x61\x6C\x73\x65\x22\x2F\x3E", 12);fs.write("\x0D\x0A\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20", 13);fs.close();cin.get();return 0;
}可以搜索 requestedExecutionLevel 位置,并关闭 PE 文件的自动 UAC 请求。
发布于:2024.02.11



)
)






Vue routes的 children使用(小白来看,包会!))

)


)


