补充:
用010hex打开zip文件。
把504B0304后的第3、4个byte改成0000
即将0900改为0000
而504B0102后的第5、6个byte不需改成0000即可破解伪加密。
解题
下载,解压
文件有hint.txt,king.jpg,kinglet.jpg,Poke.zip
通过binwalk -e 和foremost分别分离king.jpg与kinglet.jpg
从king.jpg分离得到:
加密压缩包,加密了code.txt

尝试爆破无果后,尝试伪加密,成功
解压得到code.txt

很明显得base64转图片,在线工具转一下
https://tool.jisuapi.com/base642pic.html
得到另一半二维码

再看kinglet.jpg,分离得到:

7z压缩包,打开发现文件错误,010分析,尾部是png文件尾
分离出png文件,得到

或者foremost直接分离出此图片
通过window系统的作图工具合成
组合起来发现缺少定位符,手动补齐一下

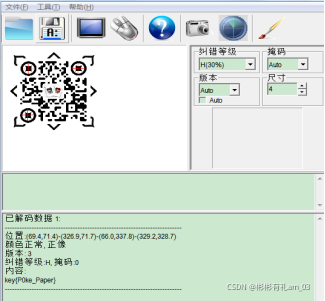
扫码得到 key{P0ke_Paper}
得到第一步Poke.zip加密压缩包得解压密码
解压Poke.zip
老K(K.jpg)明显有问题,打不开。010分析下,头部为504B0304
发现是zip文件
修改后缀,解压发现是加密压缩包
寻找解压密码
其他图片暂没看出什么异样
分析David’s words.txt
先看David’s words.txt,注意到里面有一句:“Only A is 1”
再观察一下密文的结构,所以把2345678910替换成0,把A替换成1,然后把替换得到的二进制转为字符。
import base64
s="2345678910A2345678910A23456789102345678910AA2345678910A234567891023456789102345678910AAA2345678910A234567891023456789102345678910AA23456789102345678910AAA2345678910AAA2345678910AA234567891023456789102345678910AA2345678910A23456789102345678910A2345678910234567891023456789102345678910AA2345678910A2345678910AA2345678910AA23456789102345678910AAA2345678910AA23456789102345678910A234567891023456789102345678910A234567891023456789102345678910AAA23456789102345678910AAA2345678910234567891023456789102345678910AA23456789102345678910AAA2345678910AA23456789102345678910A234567891023456789102345678910A234567891023456789102345678910AAA2345678910A2345678910A2345678910AA23456789102345678910AAA23456789102345678910AA2345678910AA234567891023456789102345678910A23456789102345678910A2345678910234567891023456789102345678910AA2345678910A2345678910234567891023456789102345678910A234567891023456789102345678910AA2345678910A2345678910A2345678910AA234567891023456789102345678910A234567891023456789102345678910AA23456789102345678910AA2345678910A2345678910A2345678910A2345678910A2345678910AA23456789102345678910AAA2345678910AA2345678910234567891023456789102345678910A23456789102345678910AA23456789102345678910A23456789102345678910A2345678910A2345678910AA234567891023456789102345678910AA2345678910A2345678910A2345678910A23456789102345678910A23456789102345678910A2345678910A234567891023456789102345678910AAA2345678910AA2345678910AA234567891023456789102345678910AAAA2345678910A23456789102345678910A23456789102345678910A23456789102345678910A2345678910A234567891023456789102345678910A2345678910A2345678910AAA2345678910A234567891023456789102345678910AA2345678910AA234567891023456789102345678910AA23456789102345678910A2345678910A2345678910A2345678910AA2345678910234567891023456789102345678910AAA2345678910A234567891023456789102345678910A2345678910A23456789102345678910234567891023456789102345678910A2345678910A2345678910A234567891023456789102345678910A2345678910A2345678910A2345678910A2345678910AA23456789102345678910A234567891023456789102345678910AA23456789102345678910AA23456789102345678910A2345678910A2345678910AAA2345678910A2345678910A2345678910AAA23456789102345678910AAA23456789102345678910A23456789102345678910AA234567891023456789102345678910A2345678910A2345678910AA2345678910A23456789102345678910A234567891023456789102345678910AAA23456789102345678910AAA23456789102345678910A2345678910AAA23456789102345678910234567891023456789102345678910AA23456789102345678910A234567891023456789102345678910A23456789102345678910A23456789102345678910234567891023456789102345678910AA234567891023456789102345678910234567891023456789102345678910AAAA2345678910A"
s=s.replace("2345678910","0")
s=s.replace("A","1")
print(s)
for i in range(0,len(s),8):print(chr(int(s[i:i+8],2)),end="")
print("\n")am = "SGFwcHkgdG8gdGVsbCB5b3Uga2V5IGlzIEtleXtPTUdfWW91ZG9pdH0="
print(base64.b64decode(am))
得到的结果再base64解码一次得到Happy to tell you key is Key{OMG_Youdoit}
所以k.zip的密码就是OMG_Youdoit,得到的Ancient spells.txt里给出了提示
As long as you help me to fix, I’ll give you what you want.
(It Is Reverse Flag)
要修好它,得到的flag还是反向的
很明显,老K的下面缺少一部分,那就拉高
这里跟V3师傅学了一招,修改jpg文件的宽高,在详细信息里查看宽高数字,直接将其宽高值转为16进制去010里搜
查看老K详细信息。得到宽高为730×550
转为16进制就是 2DA×226
010搜索 02 26

将其改为05 DC(高位1500)
修改高度
得到

Stegsolve打开

可以把图片旋转一下,然后硬看,结合出题人说的图里的0当o、 @ 和 a 不要看混了、flag错了多试几遍,慢慢看
flag{Poker_F@ce}
)


![PWN题[强网先锋]no_output](http://pic.xiahunao.cn/PWN题[强网先锋]no_output)

)













