REVERSE-PRACTICE-BUUCTF-11
- [FlareOn4]IgniteMe
- [MRCTF2020]Xor
- [GKCTF2020]BabyDriver
- [MRCTF2020]hello_world_go
[FlareOn4]IgniteMe
exe程序,运行后提示输入flag,无壳,ida分析
主逻辑在start函数中,读取输入后check,验证输入成功则输出“G00d j0b!”
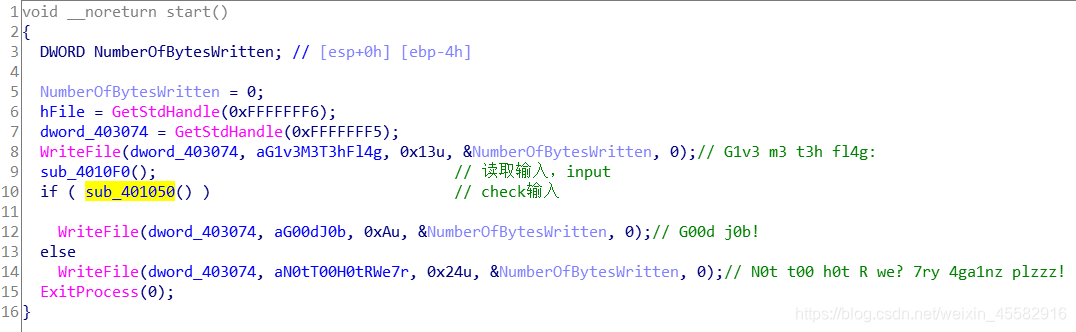
分析sub_401050函数,input和v4异或后放入byte_403180,v4有一个初始值,且在循环中不断变化,实际上的运算效果为
当i==input_len-1时,byte[i]=v4^input[i],
当i等于从input_len-2到0时,byte[i]=input[i]^input[i+1]
运算完毕后byte_403180数组和byte_403000数组比较,验证输入
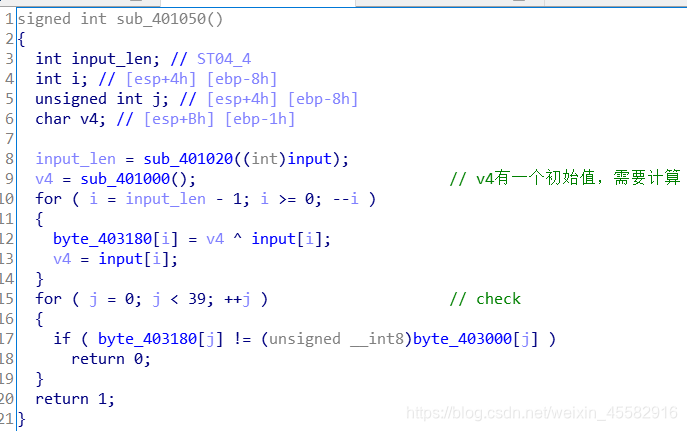
写脚本前需要先得到v4的那个初始值,直接查函数或者调试得到v4的初始值为4,写脚本即可得到flag
[MRCTF2020]Xor
exe程序,运行后提示输入flag,输入错误打印“Wrong”,无壳,ida分析
字符串交叉引用来到主逻辑函数部分,不能F5反编译,直接看汇编
主要就是将输入与对应的下标异或,input[i]^i
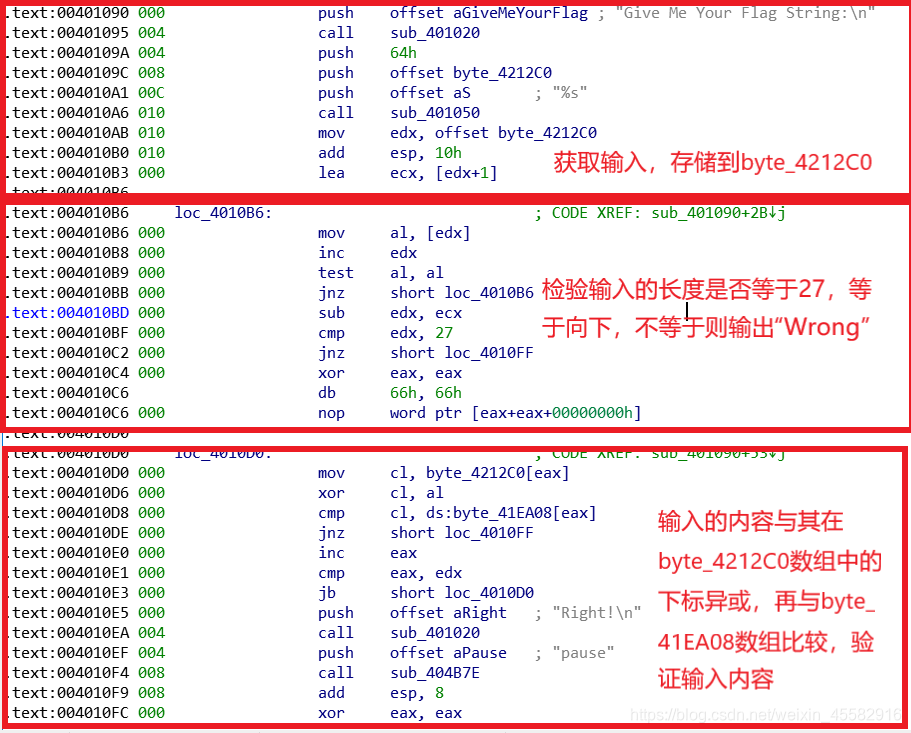
写脚本即可得到flag
[GKCTF2020]BabyDriver
sys文件,ida分析
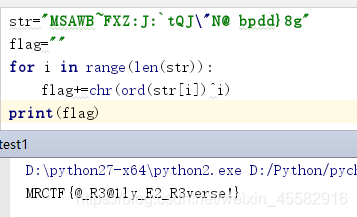
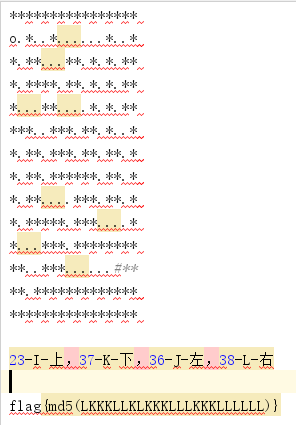
字符串交叉引用来到sub_140001380函数,分析可知是个走迷宫的题目,map的长度为224,具体分析可知map为14x16,即14行16列的地图,起始点为o,终止点为#,不能碰到*,23-上,37-下,36-左,38-右
__int64 __fastcall sub_140001380(__int64 a1, __int64 a2)
{__int64 v2; // rbx__int64 v3; // rdi__int64 v4; // raxint v5; // ecx__int16 *v6; // rsi__int64 v7; // rbp__int16 v8; // dxchar v9; // dlCHAR *v10; // rcxv2 = a2;if ( *(_DWORD *)(a2 + 48) >= 0 ){v3 = *(_QWORD *)(a2 + 24);v4 = *(_QWORD *)(a2 + 56) >> 3;if ( (_DWORD)v4 ){v5 = index; // v5=10v6 = (__int16 *)(v3 + 2);v7 = (unsigned int)v4;while ( *(_WORD *)(v3 + 4) ){
LABEL_28:v6 += 6;if ( !--v7 )goto LABEL_29;}map[v5] = '.';v8 = *v6;if ( *v6 == 23 ) // 23-上{if ( v5 & 0xFFFFFFF0 ){v5 -= 16;goto LABEL_21;}v5 += 208;index = v5;}if ( v8 == 37 ) // 37-下{if ( (v5 & 0xFFFFFFF0) != 208 ){v5 += 16;goto LABEL_21;}v5 -= 208;index = v5;}if ( v8 == 36 ) // 36-左{if ( v5 & 0xF ){--v5;goto LABEL_21;}v5 += 15;index = v5;}if ( v8 != 38 ) // 38-右goto LABEL_22;if ( (v5 & 0xF) == 15 )v5 -= 15;else++v5;
LABEL_21:index = v5;
LABEL_22:v9 = map[v5];if ( v9 == '*' ) // 不能碰到*{v10 = "failed!\n";}else{if ( v9 != '#' ) // 起始点为o,终止点为#{
LABEL_27:map[v5] = 'o';goto LABEL_28;}v10 = "success! flag is flag{md5(input)}\n";}index = 16;DbgPrint(v10);v5 = index;goto LABEL_27;}}
LABEL_29:if ( *(_BYTE *)(v2 + 65) )*(_BYTE *)(*(_QWORD *)(v2 + 184) + 3i64) |= 1u;return *(unsigned int *)(v2 + 48);
}
由于是sys文件,其使用的不是ascii码,而是键盘码,可知23-I-上,37-K-下,36-J-左,38-L-右
走完迷宫,再md5散列路线即可得到flag
[MRCTF2020]hello_world_go
elf文件,无壳,ida分析
左侧函数窗最后一个main_main函数,内容很乱,在runtime_memequal函数的一个参数unk_4D3C58中找到了flag
__int64 __fastcall main_main(__int64 a1, __int64 a2)
{__int64 v2; // r8__int64 v3; // r9__int64 v4; // r8__int64 v5; // r9__int64 v6; // rdx__int64 v7; // r8__int64 v8; // rcx__int64 v9; // rdx__int64 v10; // r9signed __int64 v11; // rax__int64 result; // rax__int64 v13; // ST58_8__int64 *v14; // [rsp+8h] [rbp-A8h]char v15; // [rsp+18h] [rbp-98h]__int64 *v16; // [rsp+60h] [rbp-50h]__int128 v17; // [rsp+68h] [rbp-48h]__int128 v18; // [rsp+78h] [rbp-38h]__int128 v19; // [rsp+88h] [rbp-28h]__int128 v20; // [rsp+98h] [rbp-18h]if ( (unsigned __int64)&v18 + 8 <= *(_QWORD *)(__readfsqword(0xFFFFFFF8) + 16) )runtime_morestack_noctxt();runtime_newobject(a1, a2);v16 = v14;*(_QWORD *)&v20 = &unk_4AC9C0;*((_QWORD *)&v20 + 1) = &off_4EA530;fmt_Fprint(a1, a2, (__int64)&v20, (__int64)&unk_4AC9C0, v2, v3, (__int64)&go_itab__os_File_io_Writer, os_Stdout);*(_QWORD *)&v19 = &unk_4A96A0;*((_QWORD *)&v19 + 1) = v16;fmt_Fscanf(a1,a2,(__int64)&go_itab__os_File_io_Reader,(__int64)&v19,v4,v5,(__int64)&go_itab__os_File_io_Reader,os_Stdin,(__int64)&unk_4D07C9,2LL);v8 = v16[1];if ( v8 != 24 )goto LABEL_3;v13 = *v16;runtime_memequal(a1, a2, v6, (unsigned __int64)&unk_4D3C58);// flag{hello_world_gogogo}if ( !v15 ){v8 = 24LL;
LABEL_3:runtime_cmpstring(a1, a2, (__int64)&unk_4D3C58, v8, v7);if ( (signed __int64)&v19 >= 0 )v11 = 1LL;elsev11 = -1LL;goto LABEL_5;}v11 = 0LL;
LABEL_5:if ( v11 ){*(_QWORD *)&v17 = &unk_4AC9C0;*((_QWORD *)&v17 + 1) = &off_4EA550; // Wrongresult = fmt_Fprintln(a1,a2,v9,(__int64)&go_itab__os_File_io_Writer,v7,v10,(__int64)&go_itab__os_File_io_Writer,os_Stdout);}else{*(_QWORD *)&v18 = &unk_4AC9C0;*((_QWORD *)&v18 + 1) = &off_4EA540; // OK!You are right!result = fmt_Fprintln(a1,a2,v9,(__int64)&go_itab__os_File_io_Writer,v7,v10,(__int64)&go_itab__os_File_io_Writer,os_Stdout);}return result;
}
 简单易上手)


















