文章目录
- [HNCTF 2022 Week1]超级签到
- [HNCTF 2022 Week1]贝斯是什么乐器啊?
- [HNCTF 2022 Week1]X0r
- [HNCTF 2022 Week1]你知道什么是Py嘛?
- [HNCTF 2022 Week1]CrackMe
- [HNCTF 2022 Week1]给阿姨倒一杯Jvav
- [HNCTF 2022 Week1]Little Endian
- NSSCTF{Littl3_Endiannnn}
[HNCTF 2022 Week1]超级签到
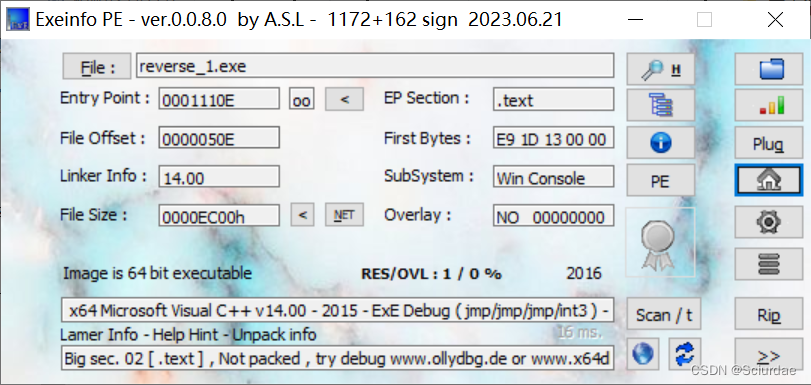
64bit文件,
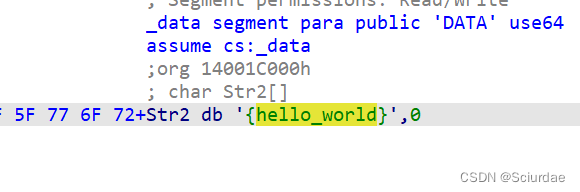
IDA打开就是,{hello_world}
[HNCTF 2022 Week1]贝斯是什么乐器啊?
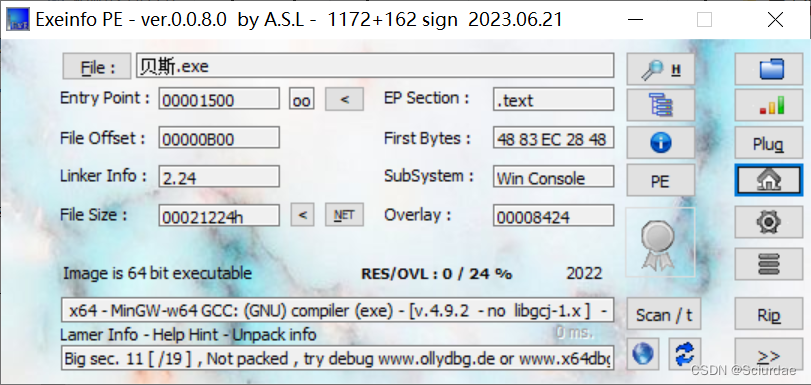
64bit文件。
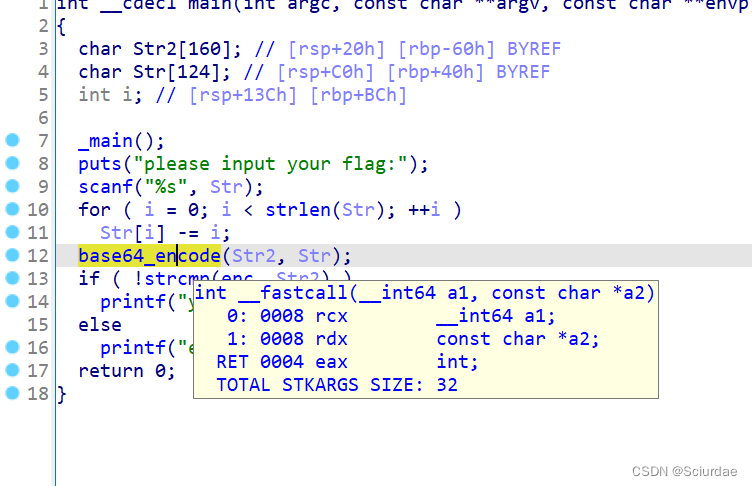
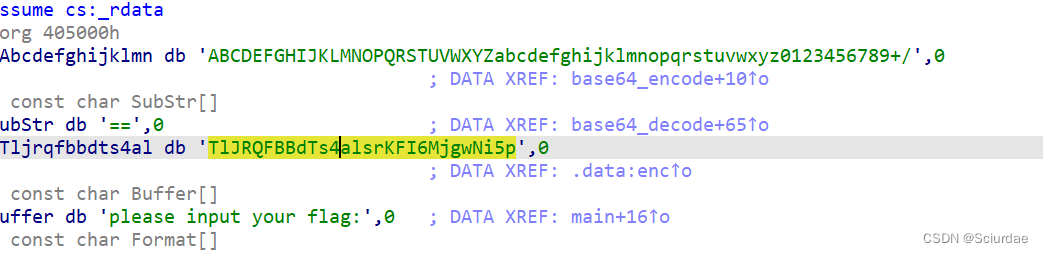
base64解码。
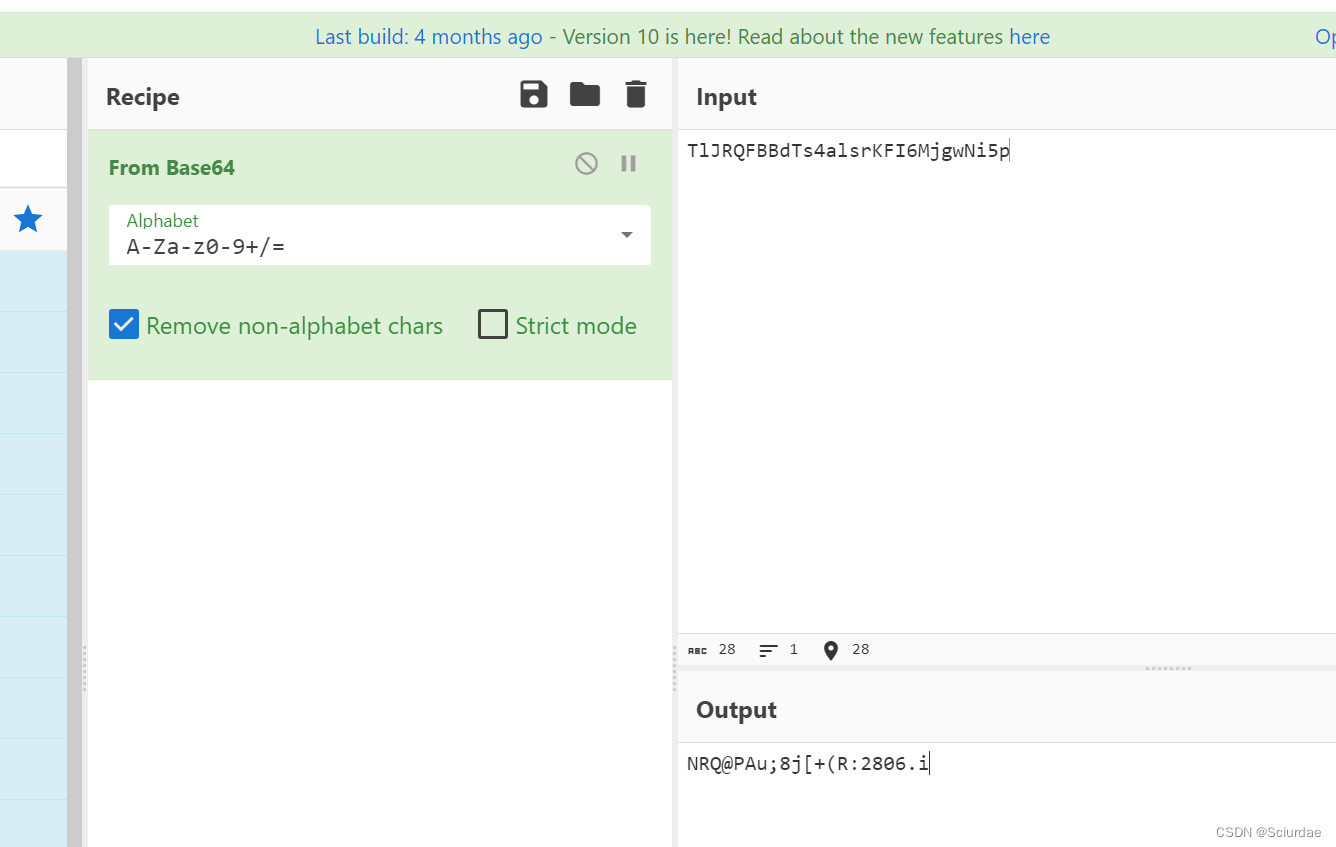
解码之后,再做一个加法。依次加 i
EXP:
enc = 'NRQ@PAu;8j[+(R:2806.i'
flag = []
for i in range(len(enc)):flag.append(chr(ord(enc[i]) + i))
print(''.join(flag))# NSSCTF{B@se64_HAHAHA}
[HNCTF 2022 Week1]X0r
64bit文件
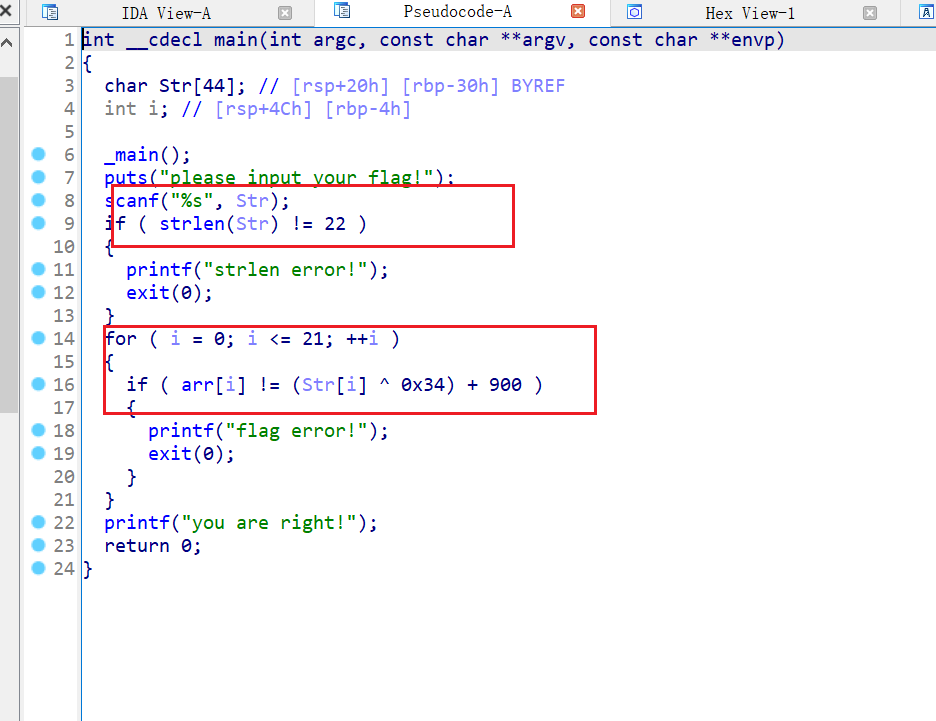
输入flag,检验长度,循环异或(和0x34异或再加900)
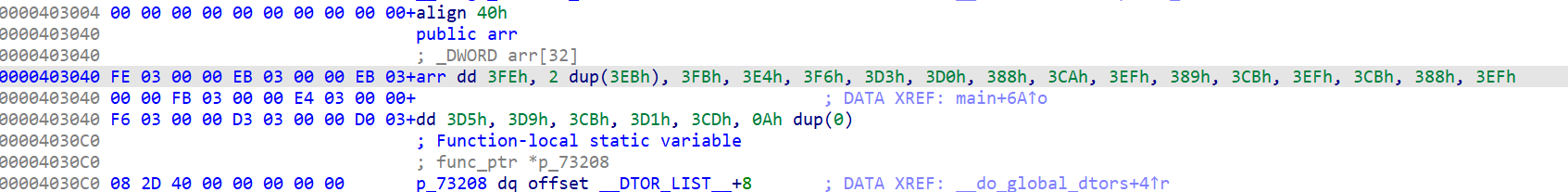
可以写个idapython提取数据
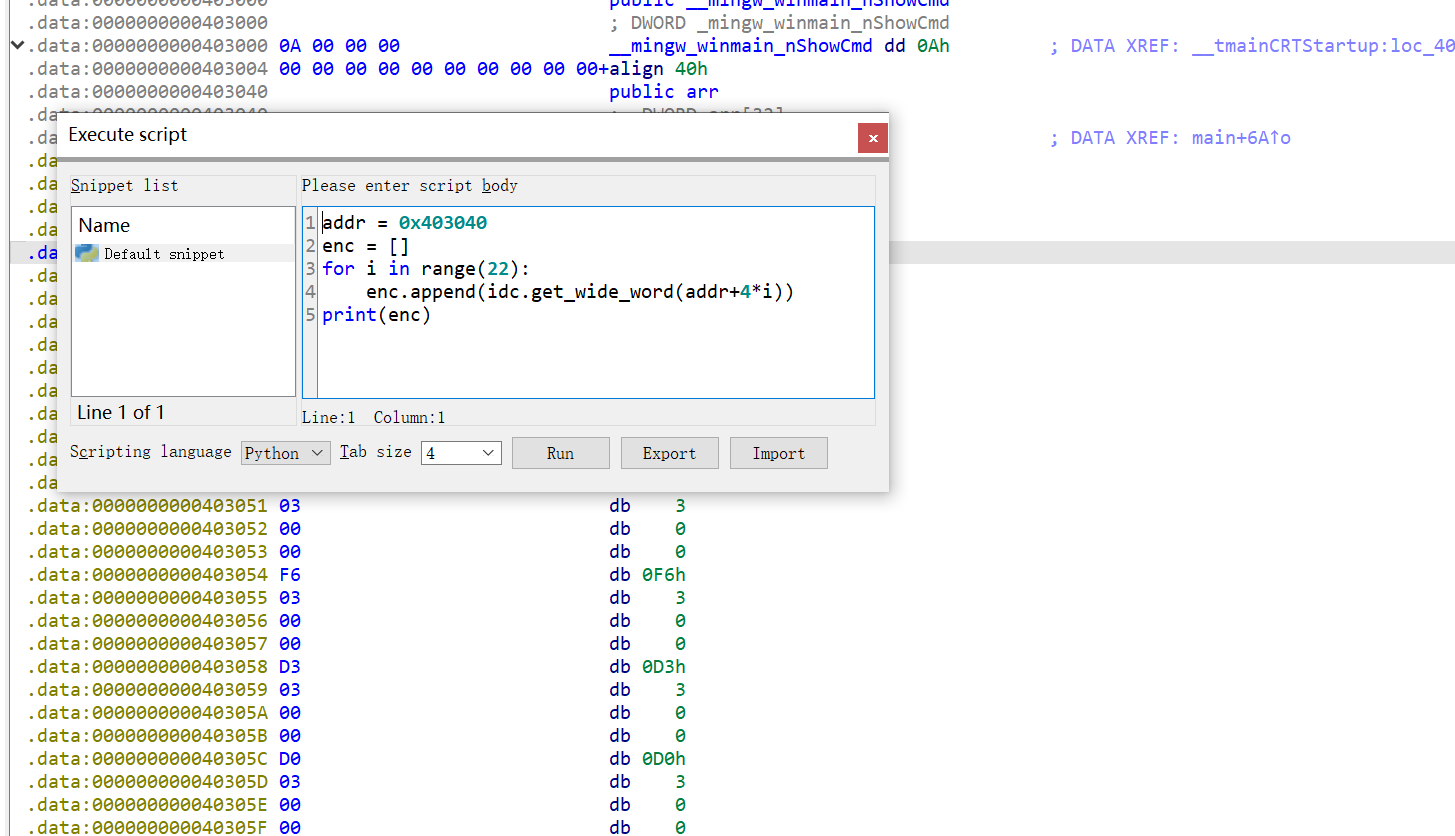
逆向一下,-900再异或0x34
EXP:
enc = [1022, 1003, 1003, 1019, 996, 1014, 979, 976, 904, 970, 1007, 905, 971, 1007, 971, 904, 1007, 981, 985, 971, 977, 973]
flag = [chr((enc[i]-900)^0x34) for i in range(len(enc))]
print(''.join(flag))# NSSCTF{x0r_1s_s0_easy}
[HNCTF 2022 Week1]你知道什么是Py嘛?
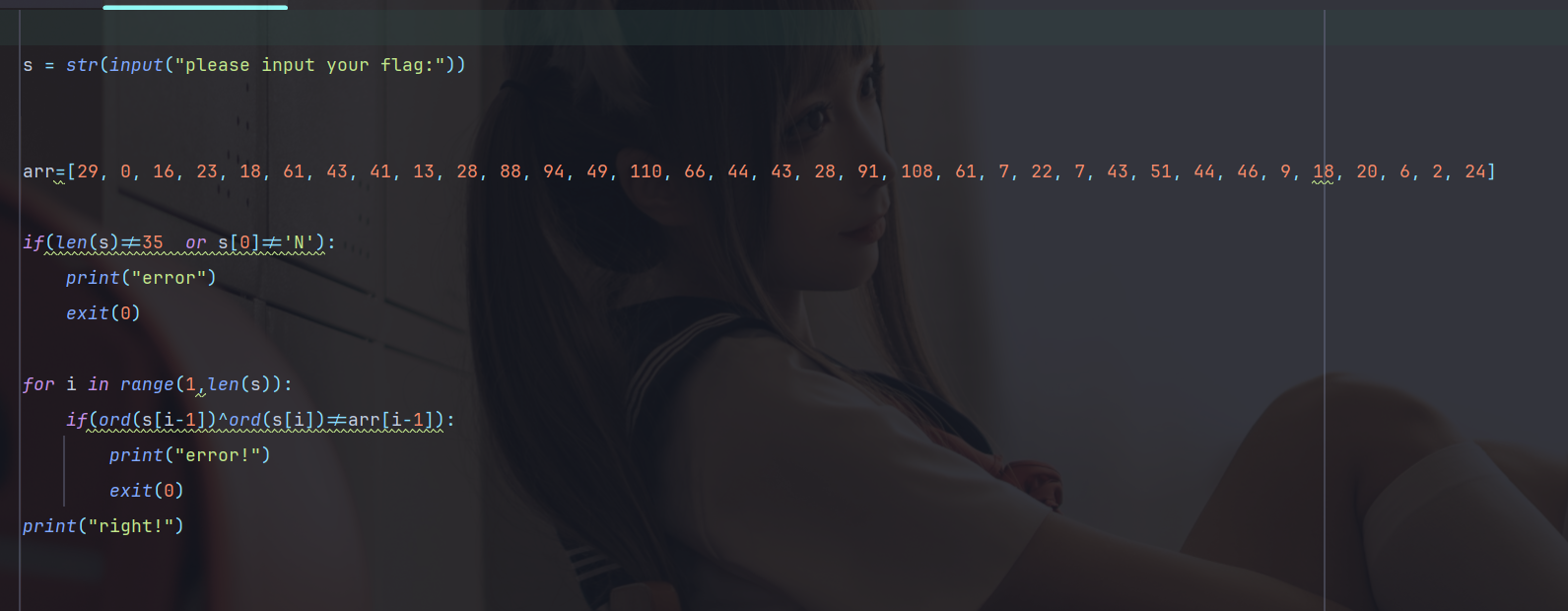
给出了S[0],再依次异或
EXP:
arr=[29, 0, 16, 23, 18, 61, 43, 41, 13, 28, 88, 94, 49, 110, 66, 44, 43, 28, 91, 108, 61, 7, 22, 7, 43, 51, 44, 46, 9, 18, 20, 6, 2, 24]
flag = ['N']
for i in range(len(arr)):flag.append(chr(ord(flag[i])^arr[i]))
print(''.join(flag))
# NSSCTF{Pyth0n_1s_th3_best_l@nguage}
[HNCTF 2022 Week1]CrackMe
ida也可以做,打开后搜索字符串,(先运行程序观察程序大致运行情况)
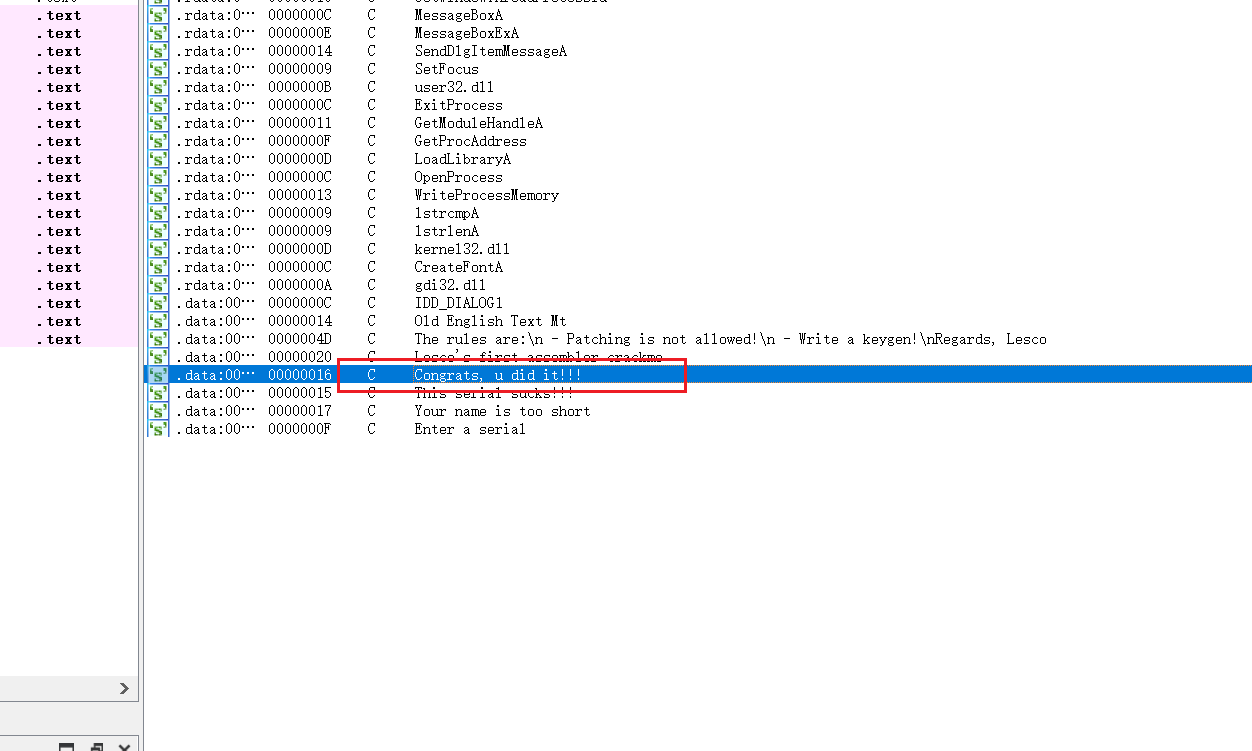
发现之前调试得到的错误信息和正确信息。跟进
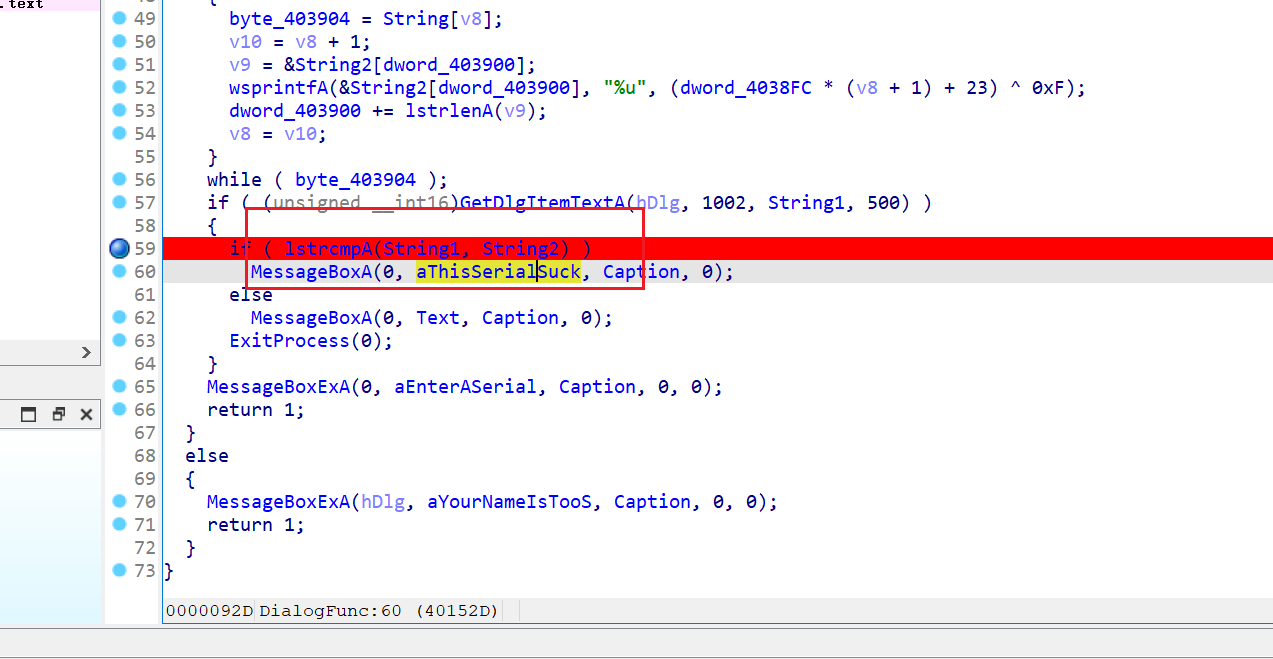
一个lstrcmp比较,String2应该就是正确的serial了。下断点调试

在比较处,最初的String2是错误的,需要再运行程序直到弹出错误信息后才会出现真正的String2。
这题得到的4e.40程序运行成功,但是提交flag失败,查看了不少wp,有的一样有的不同。有点争议的,
[HNCTF 2022 Week1]给阿姨倒一杯Jvav
直接用jadx打开。
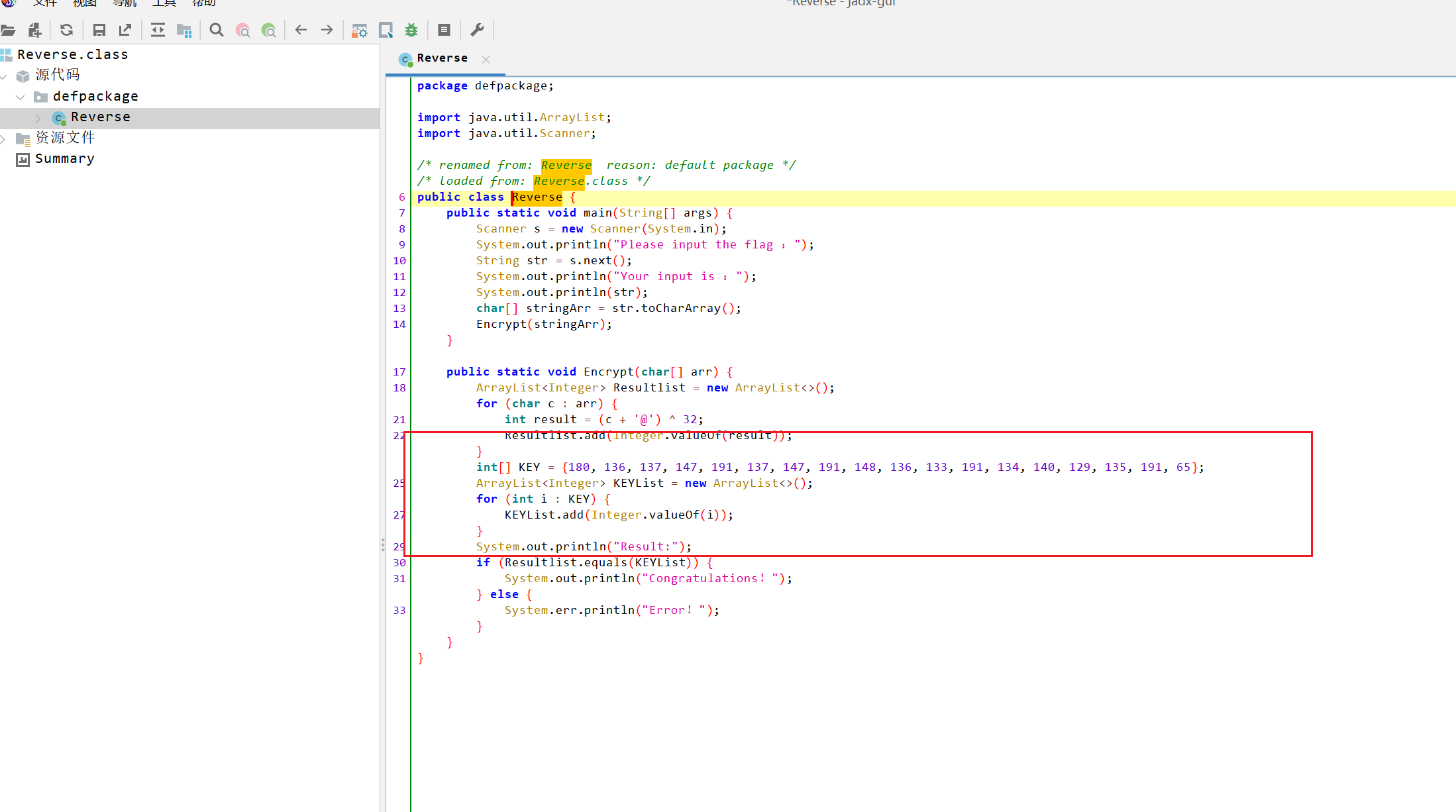
然后根据加密过程逆向
EXP:
enc = [180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65]
flag = [chr((enc[i] ^ 32) - ord('@')) for i in range(len(enc))]
print(''.join(flag))
# This_is_the_flag_!
[HNCTF 2022 Week1]Little Endian
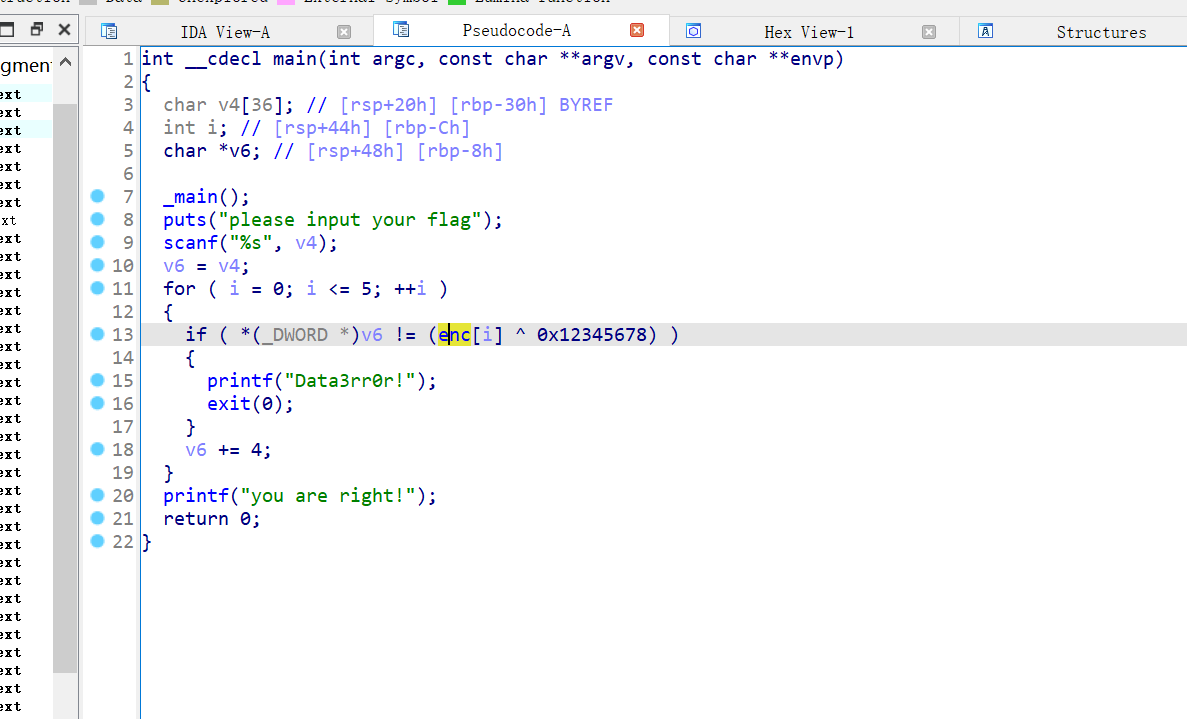
异或后得到的十六进制,需要逆序一下;
EXP:
enc = [0x51670536, 0x5E4F102C, 0x7E402211, 0x7C71094B, 0x7C553F1C, 0x6F5A3816,]
key = [(enc[i] ^ 0x12345678) for i in range(len(enc))]
print(key)
# key = [1129534286, 1283147348, 1819571305, 1850040115, 1851877732, 2104389230]
flag = []
for i in range(len(key)):key[i] = hex(key[i])[2:][::-1]key[i] = ''.join(key[i][j:j+2][::-1]for j in range(0,8,2))
for x in key:hex_num = [x[i:i+2]for i in range(0,8,2)]flagn = [chr(int(xx,16))for xx in hex_num]flag.append(''.join(flagn))
print(''.join(flag))# NSSCTF{Littl3_Endiannnn}
range(0,8,2)]
flagn = [chr(int(xx,16))for xx in hex_num]
flag.append(‘’.join(flagn))
print(‘’.join(flag))
NSSCTF{Littl3_Endiannnn}
---








:数据架构演变)









