[LitCTF 2023]enbase64
base 64

里面有一个换表的函数
写代码
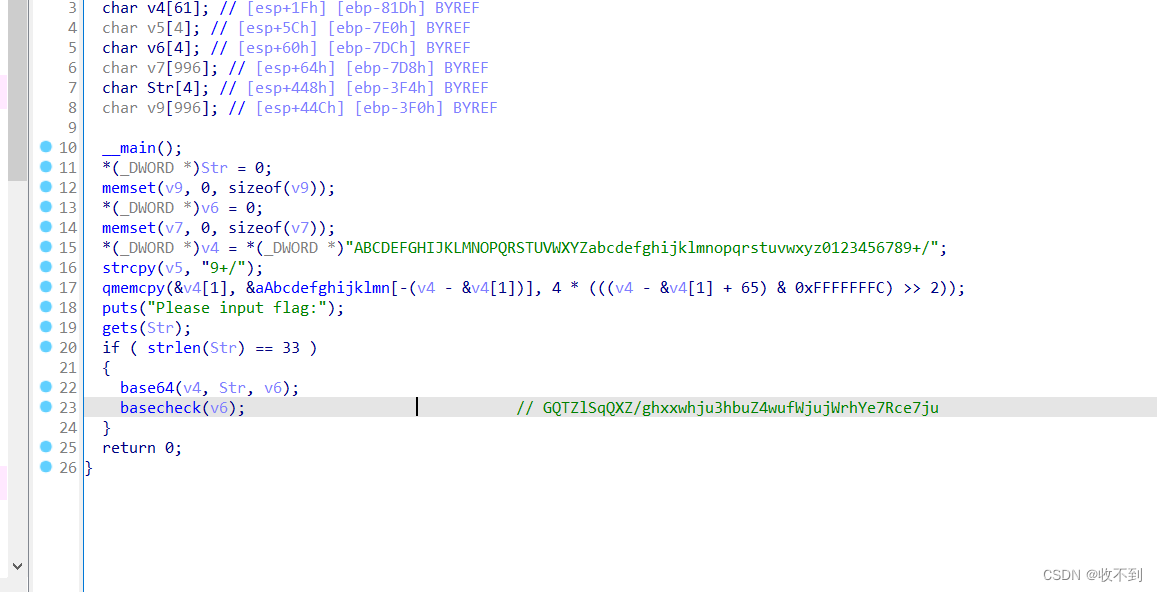
#include<stdio.h>
#include<string.h>
#include<stdlib.h>
int main()
{char *result; char Destination[65]; int v3[65];int j;int i; char Source[]="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";memset(v3, 0, sizeof(v3));v3[0] = 16;v3[1] = 34;v3[2] = 56;v3[3] = 7;v3[4] = 46;v3[5] = 2;v3[6] = 10;v3[7] = 44;v3[8] = 20;v3[9] = 41;v3[10] = 59;v3[11] = 31;v3[12] = 51;v3[13] = 60;v3[14] = 61;v3[15] = 26;v3[16] = 5;v3[17] = 40;v3[18] = 21;v3[19] = 38;v3[20] = 4;v3[21] = 54;v3[22] = 52;v3[23] = 47;v3[24] = 3;v3[25] = 11;v3[26] = 58;v3[27] = 48;v3[28] = 32;v3[29] = 15;v3[30] = 49;v3[31] = 14;v3[32] = 37;v3[34] = 55;v3[35] = 53;v3[36] = 24;v3[37] = 35;v3[38] = 18;v3[39] = 25;v3[40] = 33;v3[41] = 43;v3[42] = 50;v3[43] = 39;v3[44] = 12;v3[45] = 19;v3[46] = 13;v3[47] = 42;v3[48] = 9;v3[49] = 17;v3[50] = 28;v3[51] = 30;v3[52] = 23;v3[53] = 36;v3[54] = 1;v3[55] = 22;v3[56] = 57;v3[57] = 63;v3[58] = 8;v3[59] = 27;v3[60] = 6;v3[61] = 62;v3[62] = 45;v3[63] = 29;result = strcpy(Destination, Source);for ( i = 0; i <= 47; ++i ){for ( j = 0; j <= 63; ++j )Source[j] = Destination[v3[j]];result = strcpy(Destination, Source);}puts(Destination);//gJ1BRjQie/FIWhEslq7GxbnL26M4+HXUtcpmVTKaydOP38of5v90ZSwrkYzCAuNDreturn 0;}得到
gJ1BRjQie/FIWhEslq7GxbnL26M4+HXUtcpmVTKaydOP38of5v90ZSwrkYzCAuND
得到换的表以后,套了一个脚本就出来了
import base64
import stringstr1 = "GQTZlSqQXZ/ghxxwhju3hbuZ4wufWjujWrhYe7Rce7ju"string1 = "gJ1BRjQie/FIWhEslq7GxbnL26M4+HXUtcpmVTKaydOP38of5v90ZSwrkYzCAuND"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"print(base64.b64decode(str1.translate(str.maketrans(string1, string2))))
#LitCTF{B@5E64_l5_tooo0_E3sy!!!!!}LitCTF{B@5E64_l5_tooo0_E3sy!!!!!}
[LitCTF 2023]snake
.pyc
010 打开,第一行是空的,需要补齐,
提示了python3.7版本
Python 2.7: \x03\xf3\x0d\x0a\0\0\0\0Python 3.0: \x3b\x0c\x0d\x0a\0\0\0\0Python 3.1: \x4f\x0c\x0d\x0a\0\0\0\0Python 3.2: \x6c\x0c\x0d\x0a\0\0\0\0Python 3.3: \x9e\x0c\x0d\x0a\0\0\0\0\0\0\0\0Python 3.4: \xee\x0c\x0d\x0a\0\0\0\0\0\0\0\0Python 3.5: \x17\x0d\x0d\x0a\0\0\0\0\0\0\0\0Python 3.6: \x33\x0d\x0d\x0a\0\0\0\0\0\0\0\0Python 3.7: \x42\x0d\x0d\x0a\0\0\0\0\0\0\0\0\0\0\0\0Python 3.8: \x55\x0d\x0d\x0a\0\0\0\0\0\0\0\0\0\0\0\0Python 3.9: \x61\x0d\x0d\x0a\0\0\0\0\0\0\0\0\0\0\0\0Python 3.10: \x6f\x0d\x0d\x0a\0\0\0\0\0\0\0\0\0\0\0\0转py
关键代码
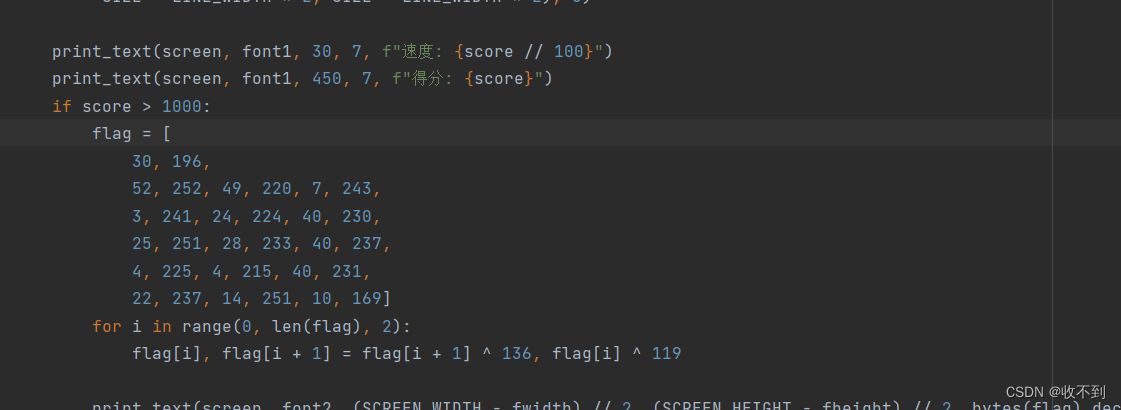
下面那个逗号,写的很迷,然后AI转了一下,emmm,人工智障,,。
找了一个别的,要加一个中间变量
脚本
#include<stdio.h>
#include<string.h>
int main()
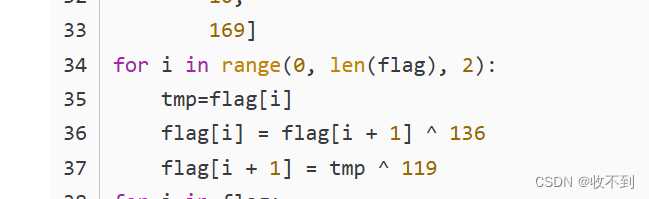
{char flag[] = {30, 196, 52, 252, 49, 220, 7, 243, 3, 241, 24, 224, 40, 230, 25, 251, 28, 233, 40, 237, 4, 225, 4, 215, 40, 231, 22, 237, 14, 251, 10, 169};int len;int i;char tmp;len=strlen(flag);for(i=0;i<len;i=i+2){tmp=flag[i];flag[i] = flag[i+1 ] ^ 136;flag[i+1] = tmp ^ 119;} puts(flag);//LitCTF{python_snake_is_so_easy!}return 0;
}[LitCTF 2023]程序和人有一个能跑就行了--wait
题目提示动态调试
找到主函数
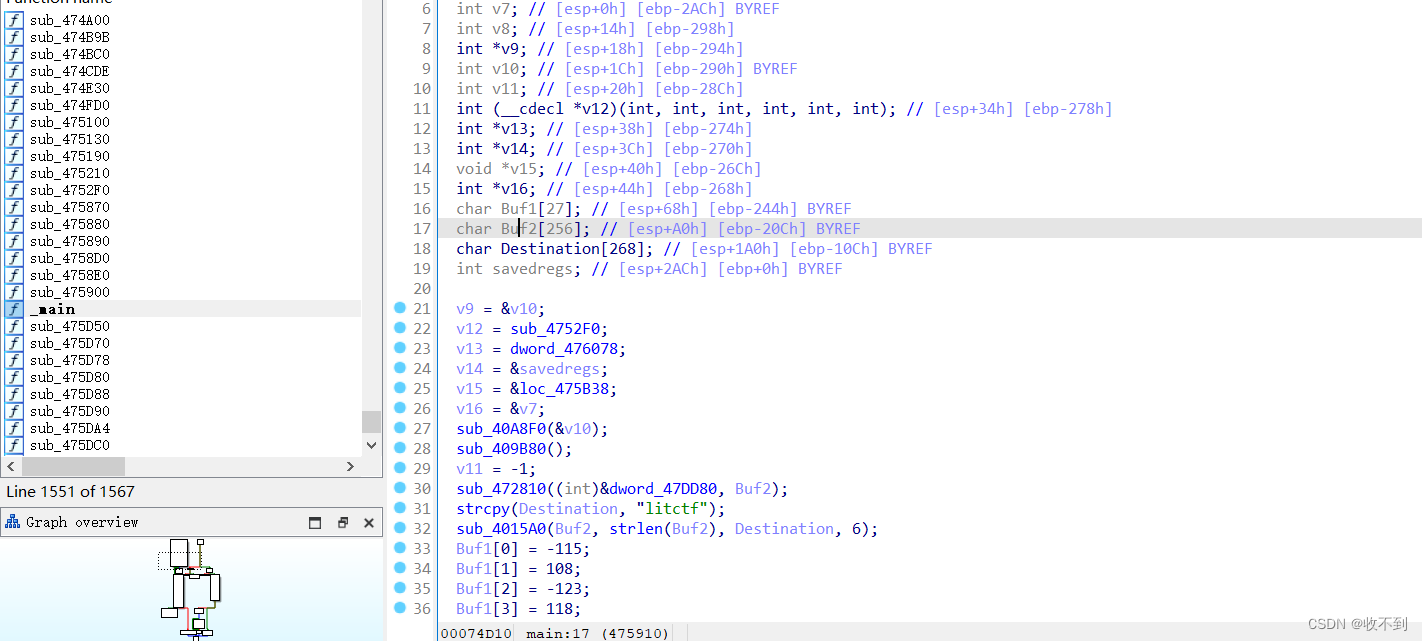
rc4加密,buf2是一个256字节的s盒,密钥是litctf
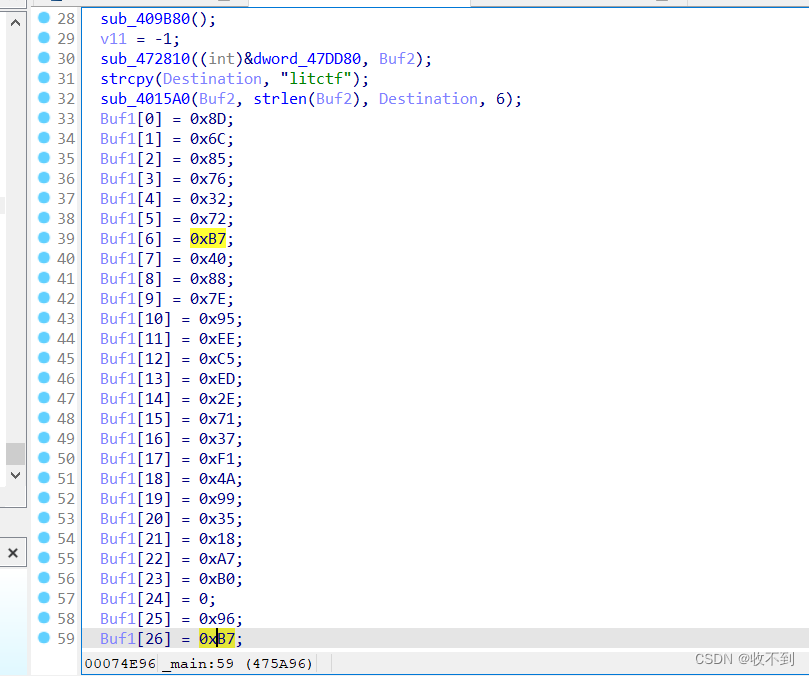
把那个buf1转为十六进制
进入下面那个4015A0

rc4脚本
def rc4_decrypt(ciphertext, key):# 初始化 S-boxS = list(range(256))j = 0for i in range(256):j = (j + S[i] + key[i % len(key)]) % 256S[i], S[j] = S[j], S[i]# 初始化变量i = j = 0plaintext = []# 解密过程for byte in ciphertext:i = (i + 1) % 256j = (j + S[i]) % 256S[i], S[j] = S[j], S[i]k = S[(S[i] + S[j]) % 256]plaintext.append(byte ^ k)return bytes(plaintext)# 示例用法
encrypted_data = [0x8D, 0x6C, 0x85, 0x76, 0x32, 0x72, 0xB7, 0x40, 0x88, 0x7E, 0x95, 0xEE, 0xC5, 0xED, 0x2E, 0x71, 0x37, 0xF1, 0x4A,0x99, 0x35, 0x18, 0xA7, 0xB0, 0, 0x96, 0xB7] # 替换成你的密文
encryption_key = b'litctf' # 替换成你的密钥decrypted_data = rc4_decrypt(encrypted_data, encryption_key)
print("Decrypted Data:", decrypted_data.decode('utf-8'))# Decrypted Data: LitCTF{this_is_a_fake_flag}
一个假的flag,再分析别的
five five
[LitCTF 2023]debase64--wait
参考:http://t.csdnimg.cn/mPUBT
32位,盲猜有SMC,猜错了,用不到,阿巴阿巴
4015220函数进入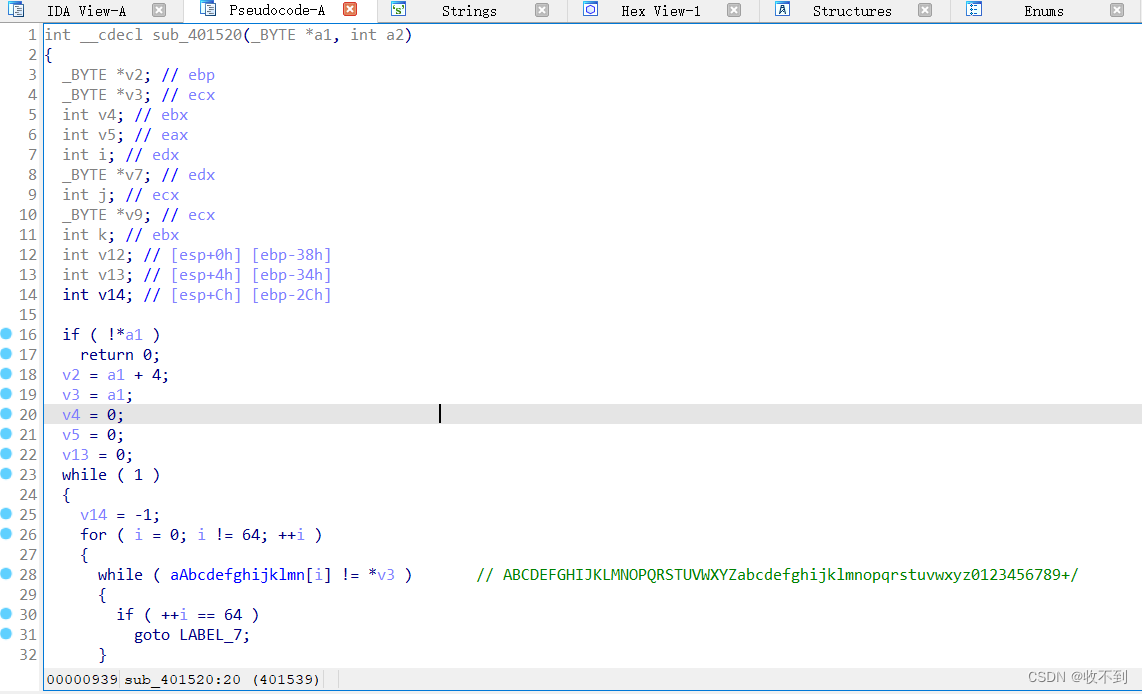
学习
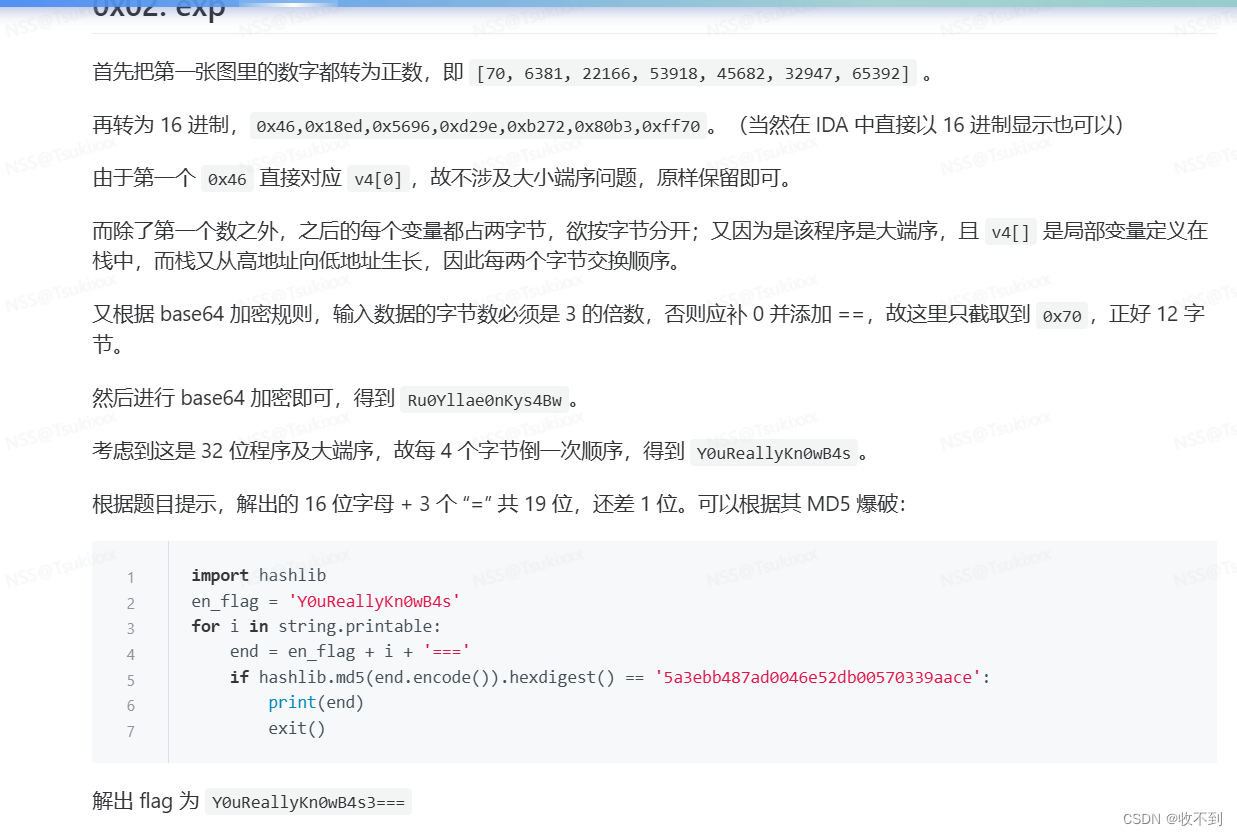







)








)


